PCI DSS Compliance: Complete Guide for 2026


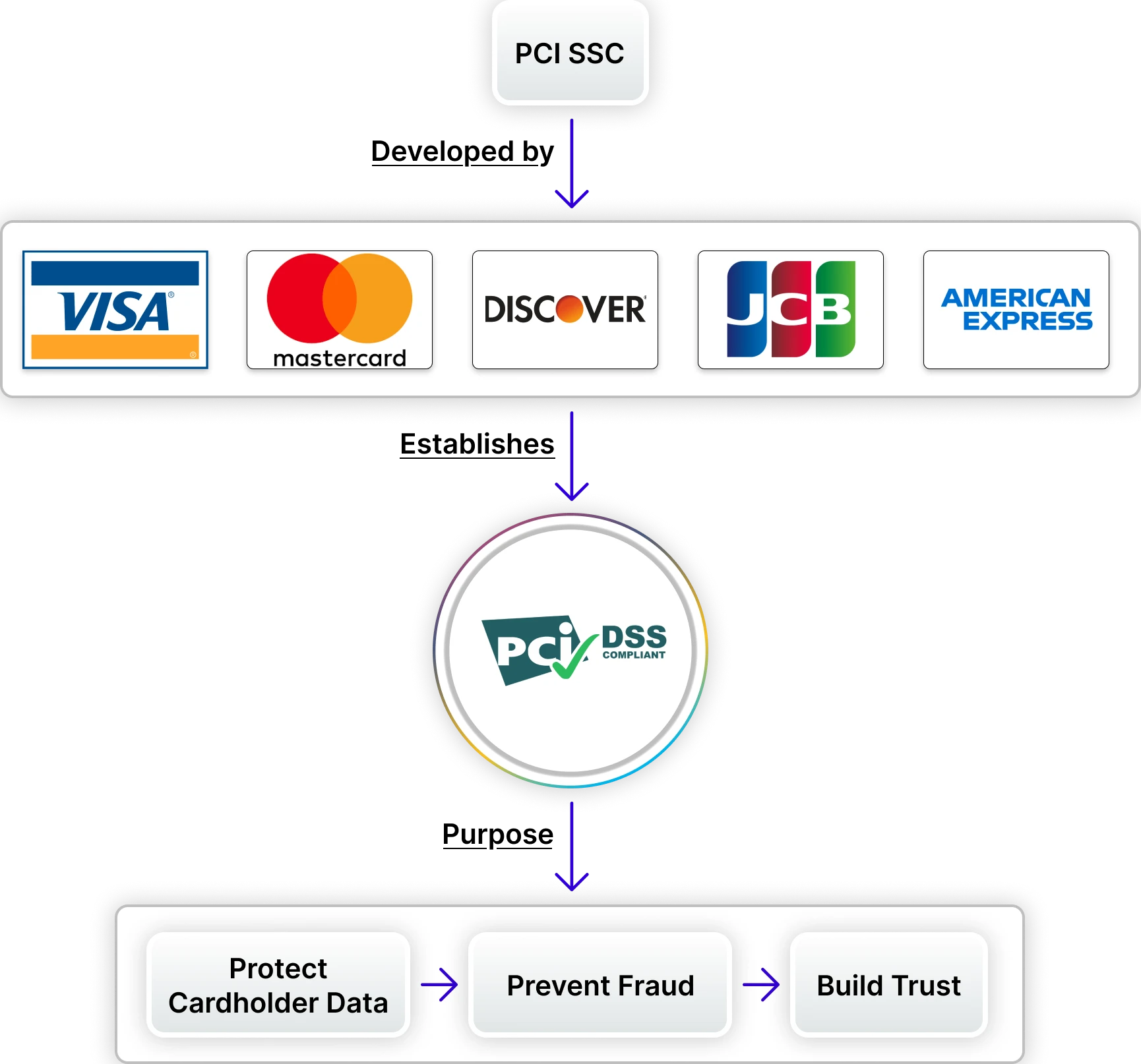
The Payment Card Industry Data Security Standard (PCI DSS) is an international security standard that protects credit and debit card information from theft and fraud. Created by the PCI Security Standards Council, a group made up of big card brands like Visa, Mastercard, American Express, JCB, and Discover, the standard sets forth a series of requirements that must be complied with by any business that processes card payments. To put it simply, PCI DSS is the playbook to help companies protect sensitive cardholder data to limit the likelihood of a breach and protect future customers' trust.
As an increasing share of transactions takes place online and payments are made using digital means today, safeguarding payment card data has never been more important. The IBM Costs of a Data Breach Report 2025 informs us that the global average cost of a data breach has reached USD 4.88 million, representing a 10% increase over the preceding year. No company handling credit or debit card data wants the legal implications, loss of card brand or organization payment processing rights, expensive incident remediation costs, or the damage to reputation that follows if it becomes non-compliant with PCI DSS.
As PCI DSS version 4.0 has moved into required compliance by March 2025, the new standard includes enhanced controls, additional requirements, and a greater focus on ongoing monitoring. In this blog, we are going to explain what PCI DSS is, why it is important for a business in 2025, detail the 12 requirements and control objectives, describe compliance levels and certification processes, describe what is new in PCI DSS 4.0, discuss common issues, and provide best practices for ongoing steady compliance.
Key Takeaways
- PCI DSS is the global standard for protecting payment card data, and it applies to all businesses, regardless of size, that store, process, or transmit cardholder information.
- The framework consists of 12 security requirements that are categorized into 6 control objectives, and organizations are classified into 4 compliance levels according to transaction volume.
- With version 4.0, PCI DSS has shifted from point-in-time compliance toward continuous monitoring and risk-based validation.
- In addition to reducing fraud and monetary penalties, compliance improves the organization's overall cybersecurity posture while establishing long-term trust with customers.
What is PCI DSS?
The Payment Card Industry Data Security Standard (PCI DSS) is a globally recognized framework to protect payment card information from theft, fraud, and misuse. It is relevant to any organization that stores, processes, or transmits cardholder data, whether it is a global bank, e-commerce company, or small retailer, service provider, or anywhere a credit card or debit card is swiped. It all comes down to this: if you take credit or debit as a form of payment from your customers or clients for goods or services, you are required to be PCI DSS compliant.
The Payment Card Industry Security Standards Council (PCI SSC) established PCI DSS in 2004. The PCI SSC is an independent organization founded by the five largest card brands - Visa, Mastercard, American Express, JCB, and Discover. These card brands realized that the lack of security best practices resulted in exposed cardholder data and, eventually, created a single global standard for payment security. Although PCI SSC does not have the legal authority to mandate compliance, card brands and acquiring banks require compliance to do business with them, and compliance is believed to be the best method for organizations to protect sensitive information and maintain customer trust in a mutually beneficial manner.
PCI DSS is rather simple in its purpose and mission: to protect cardholder data anywhere it resides - whether it's stored, processed, or transmitted. Requirements around encryption, access controls, network monitoring, and vulnerability management are some of the definitions of the PCI DSS standard. Over the last number of years, PCI DSS has grown in conjunction with increased information security threats, changes in technology, and has become the foundation of a modern payment security strategy.
Why PCI DSS Matters for Business
PCI DSS is not merely a regulatory box to check but a shield for businesses in an increasingly hostile digital environment. The standard’s main aim is to ensure that cardholder data is secure across every stage of its lifecycle to reduce the likelihood of fraud use, data breaches, and unauthorized use. Operations that align with PCI DSS requirements reinforce their defenses against new forms of attack while demonstrating to customers and partners that security is a priority.
Key Benefits of Being PCI DSS Compliant
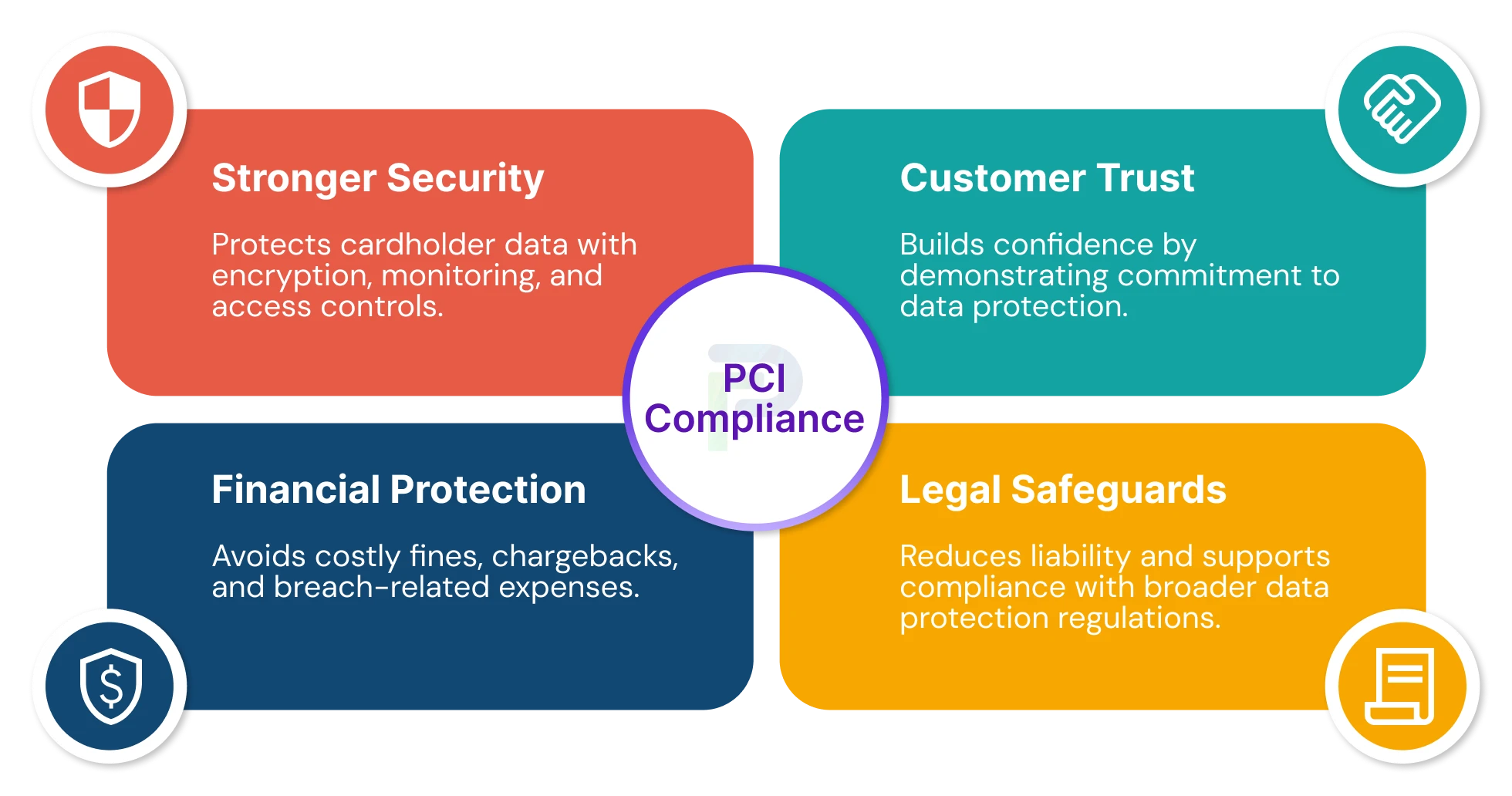
1. Enhanced Security
PCI DSS safeguards cardholder data by obligating organizations to comply with a set of proven security practices. This practice will not only defend against data breaches but will foster trust and confidence with customers resulting in stronger relationships with those customers, repeat business, and ultimately lasting brand loyalty.
2. Trust with Existing and New Customers
Consumers want to do business with organizations that take a proactive approach to data protection. When organizations show compliance with PCI DSS, it demonstrates that an organization is making every effort to earn and maintain trust with its customers. This is especially important in retail, e-commerce, and financial sectors - trust is a key driver of customer loyalty.
3. Mitigating legal risk
Compliance can protect you from some legal risk in the event of a security incident. Complying with PCI DSS, in addition to taking some precautions, can help ensure greater regulatory compliance and avoid litigation and liability in the event of a breach.
4. Financial Protection
PCI DSS compliance can help avoid significant costs, like penalties from card networks and banks if PCI DSS is not complied with, as well as repair costs associated with a breach, including remediation and brand damage. Compliance is a financial shield that protects the overall revenue, SCC, and business continuity.
PCI DSS Requirements Explained
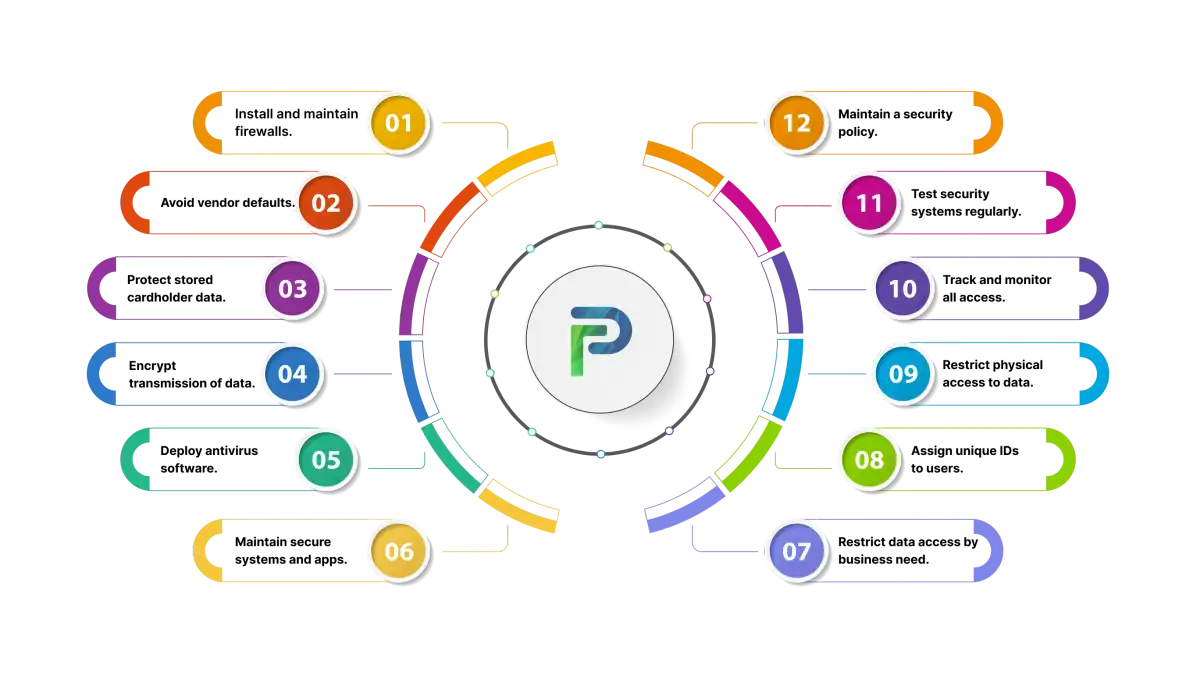
The PCI DSS framework consists of 12 primary requirements that are organized into six control objectives. All together, they offer a robust strategy for protecting customer cardholder data from unauthorized access, theft, or misuse. Below is a summary of each of the objectives, with each of the requirements:
Objective 1: Build and Maintain a Secure Network
The first objective addresses the need for organizations to establish a solid foundation for payment security.
- Requirement 1: Install and maintain a firewall configuration to protect cardholder data. Firewalls serve as a barrier between trusted and untrusted networks and stop unauthorized access.
- Requirement 2: Do not use vendor-supplied defaults for system passwords and other security settings. Attackers will often seek out and exploit weak or unchanged defaults.
Objective 2: Protect Cardholder Data
The second objective focuses on protecting sensitive payment data while it is both at rest and in transit.
- Requirement 3: Stored cardholder data must be protected via strong encryption, truncation, masking, or hashing methods. Businesses should only store cardholder data when it is necessary.
- Requirement 4: Cardholder data must be encrypted during transmission across open, public networks. This helps prevent attackers from stealing cardholder data during transmission.
Objective 3: Vulnerability Management
This objective deals with protecting systems from malware and managing timely patches.
- Requirement 5: Use and regularly update anti-virus software or programs, including end-user devices, server devices, and all other system components that may store, transmit, or process cardholder data to protect against malicious software.
- Requirement 6: Develop and maintain secure systems and applications (including applying patches on time and following secure coding guidelines) to create secure systems and applications.
Objective 4: Access Control
Robust access controls ensure that only approved individuals can interact with sensitive cardholder information.
- Requirement 7: Access to cardholder data must be restricted to only those individuals who need access to perform their job responsibilities. Access is to be based on the principle of least privilege.
- Requirement 8: Each individual with access to computers must be assigned a unique identification (ID). This will ensure accountability and tracking of individual activity.
- Requirement 9: Physical access to a computer system accessing cardholder data, including servers and storage, must be restricted to only individuals who need access. Physical security must include data centers and POS systems, including backups.
Objective 5: Monitor & Test Networks
Ongoing monitoring and testing are essential to finding problems before they happen.
- Requirement 10: Organizations must track and monitor all access to network resources and cardholder data with logging and audit trails. Visibility of access to data can assist in identifying suspicious activity.
- Requirement 11: Organizations must regularly test security systems and processes, including vulnerability scans, penetration tests, and incident detection.
Objective 6: Maintain Security Policies
To sum up, the PCI DSS mandates that entities formalize their security practices through policies and training.
Requirement 12: Keep an information security policy that includes employees, contractors, and third parties. Include providing ongoing security awareness training and updating security policies regularly.
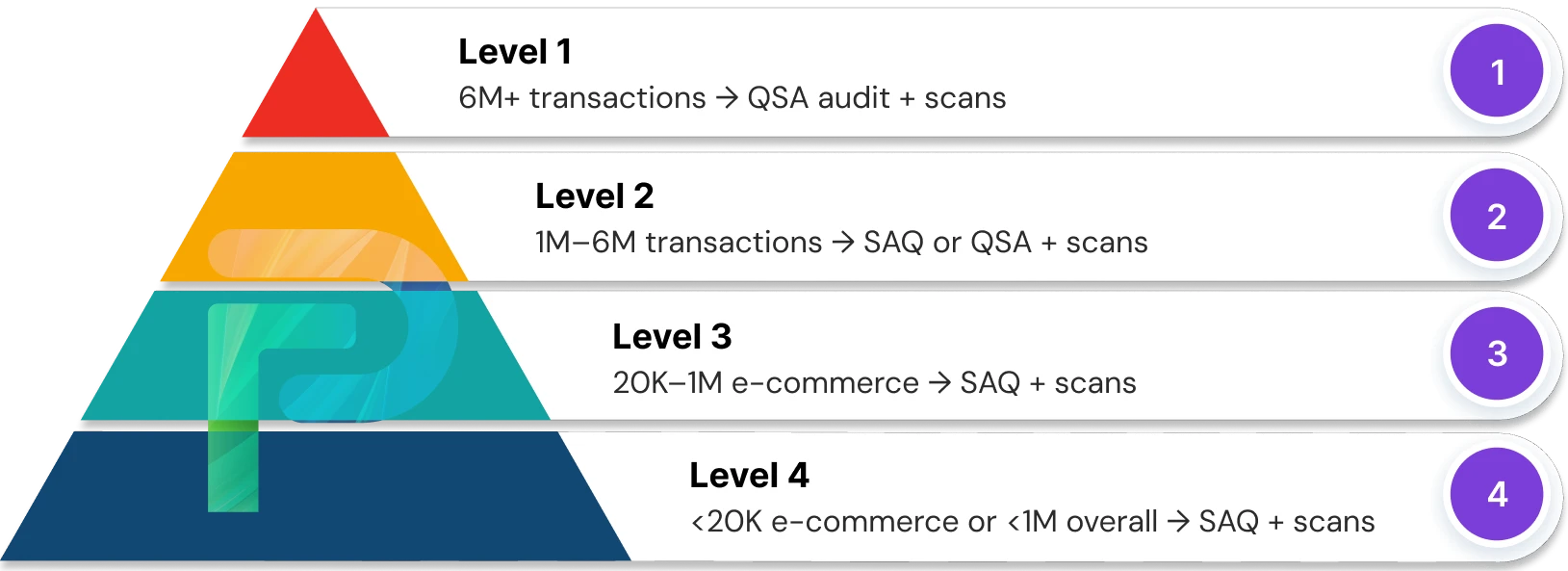
PCI DSS Compliance Levels
Not all businesses process the same volume of card transactions, so PCI DSS employs a tiered model of compliance levels. The level at which an organization is placed depends on how many annual transactions it processes, and in particular, at what level of transactions it expects its compliance validation. Every level sets forth its own validation methodology that can be anywhere from a self-assessment to formally being reviewed via an on-site audit by a Qualified Security Assessor (QSA).
The framework applies to all types of entities that store, process, or transmit cardholder data, no matter if you are a global retailer processing tens of millions of transactions annually, or a small business processing just a few thousand annually.
PCI DSS Compliance Process (How to Get Certified)
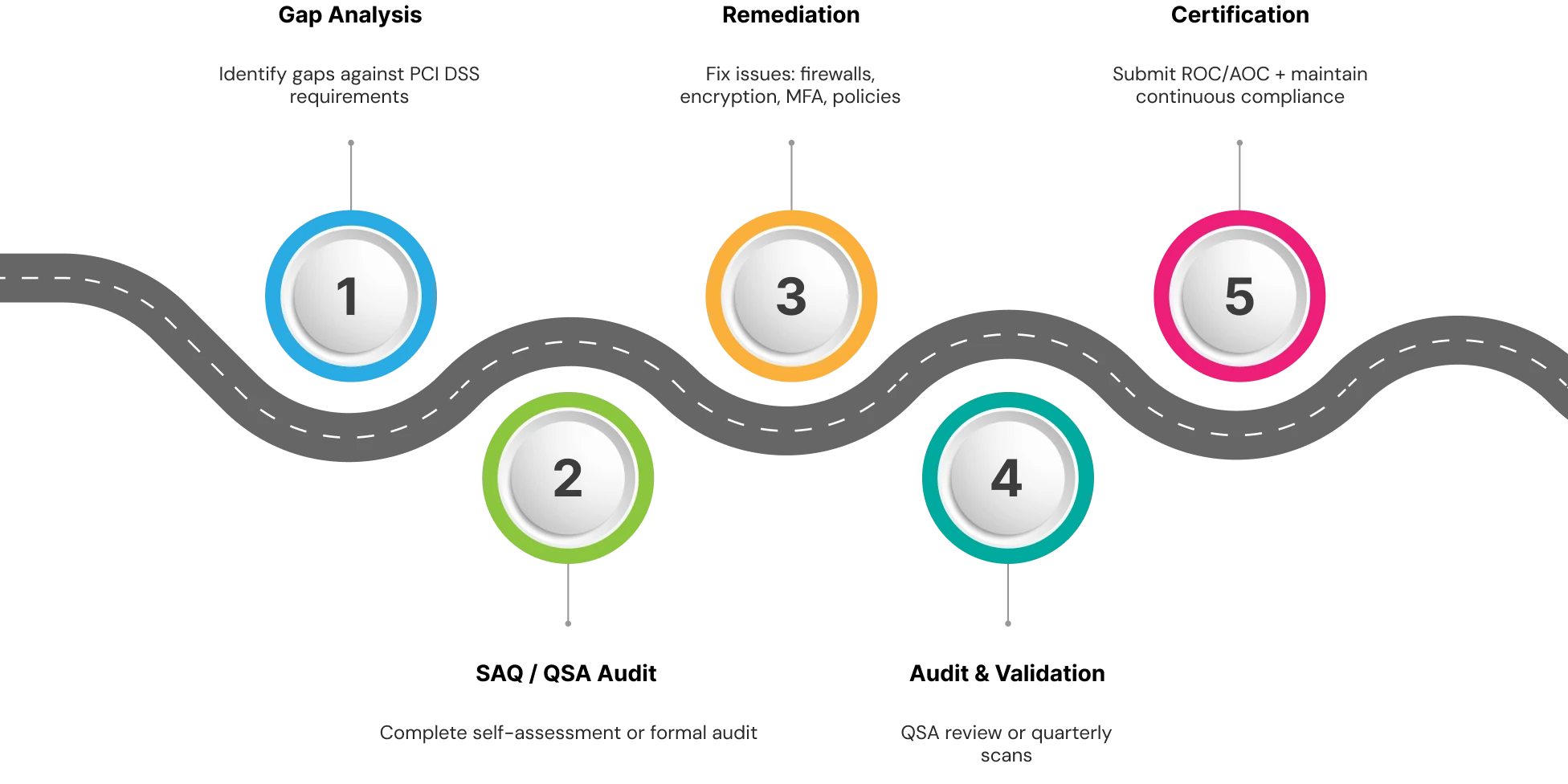
Achieving compliance with PCI DSS is not a one-time endeavor; it is an organized, comprehensive, and deliberate approach that requires preparation, validation, and continuous engagement. From an engagement perspective, the journey towards becoming certified generally follows five steps:
Step 1: Gap Analysis
The first step is to assess your current environment against the PCI DSS security requirements. This assessment will identify where your company's security controls, documentation, or processes are not sufficient. Many companies will use a qualified security assessor (QSA) or internal security assessor (ISA) to conduct the assessment and develop a prioritized remediation plan.
Step 2: Self Assessment Questionnaire (SAQ) or QSA Audit
Depending on the level of compliance, you will either complete a Self Assessment Questionnaire (SAQ) or identify an auditor for a full on-site assessment. For organizations with smaller merchants and service providers that are PCI DSS compliant, an SAQ is a structured checklist that they can use to document compliance. For larger organizations to become PCI compliant, they will undergo a full on-site independent audit.
Step 3: Remediation
Once the gaps have been identified, businesses need to remediate the gaps prior to receiving certification. This may be in the form of tightening policies around firewall rules, encrypting sensitive data, upgrading aging systems, facilitating multi-factor authentication (MFA), or improving access control policy. Ideally, remediation closes gaps for PCI DSS but also provides an overall cybersecurity resilience boost.
Step 4: Audit and Validation
After remediation is completed, the environment is formally validated. For Level 1 merchants and service providers, validation occurs once per year via an on-site audit completed by a QSA, as well as quarterly vulnerability scans completed by an Approved Scanning Vendor (ASV). All other lower-level merchants validate their compliance via an SAQ and an external scan, although a recommendation on the review by a QSA is still possible.
Step 5: Certification and Ongoing Compliance
After a successful validation, the organization then submits its attestation of compliance (AOC) and report of compliance (ROC) to the acquiring bank, or brand, according to PCI guidelines. Compliance is an ongoing process where guidance indicates the organization should conduct quarterly vulnerability scans, annual reevaluations, and maintenance of sound monitoring of its security controls for the foreseeable future.
PCI DSS 4.0 Transition
As PCI DSS 4.0 has been fully enforced by March 2025, organizations have to fulfill additional requirements for stronger authentication, broader scoping, and continuous monitoring. Businesses that currently hold a PCI DSS 3.2.1 certification will need to revise their controls and policies to comply with PCI DSS version 4.0 before the deadline to maintain compliance.
Common Challenges and Risks of Non-Compliance
Not adhering to PCI DSS means more than just missing a checkbox; it puts organizations at risk of extremely serious financial, operational, and reputational consequences. This risk is serious enough that even a single error can threaten customer trust and the long-term viability of the organization. What follows are the most critical issues for organizations that fail to meet PCI DSS requirements.
1. High Cost of Breaches and Fines
Compliance breaches leave organizations more exposed to data breaches to steal sensitive cardholder information. The financial costs are exorbitant and as alarming as you can imagine. In addition to the immediate losses of fraud, a business may also incur hefty fines from card brands and acquiring banks. These fines typically vary between thousands and millions of dollars, depending on the non-compliance's degree and length. The average cost of a data breach has risen globally year-on-year, which includes remediation, legal fees, and, in many cases, customer compensation. If you are a small business, even a portion of this cost would be crippling.
2. Operational Disruption
When non-compliance with regulations results in a security event, it can, in turn, result in business disruption well beyond IT. An organization may have to take its systems offline during investigations, creating downtime in payment processing or e-commerce transactions. A business may also face restrictions from payment providers, including higher fees, more audits, or being banned from processing credit card payments entirely. Disruption goes beyond the day-to-day operations and can create far-reaching effects through supply chains and customer service.
3. Loss of Reputation
By far, the most harmful effect of PCI DSS non-compliance is the loss of customer trust. People expect companies to safeguard their payment details. With customer loyalty and trust gone, it can be extremely challenging to rebuild that relationship. Research shows that consumers tend to cease conducting business with an organization that has experienced a breach of payment information. Once a reputation is damaged, it takes a significant investment in public relations, marketing, and more security measures to recover. For many organizations affected by a breach, the pain of a lost reputation continues beyond the financial impact and penalties they face.
PCI DSS 4.0: What’s New?
PCI DSS 4.0, which debuted in March of 2022 with a full transition deadline of March 31, 2025, is the most recent edition of the standard in more than a decade. It is intended to address modern payment security threats, provide organizations with more flexibility to achieve compliance, and emphasize a continuous practice of security as opposed to checkbox compliance with sporadic checks.
-
Customized Validation Methods
Perhaps the most significant change is the addition of customized validation methods, which help organizations demonstrate security outcomes through alternative controls if traditional methods don’t suit the entity’s environment. This is particularly helpful for complex environments that may be cloud-native or supported by non-hosted services. At the same time, the standard increases expectations for stricter authentication, now requiring multi-factor authentication (MFA) for all access into cardholder data environments, not just for administrative access. -
Continuous Monitoring and Testing
A second significant change addresses the emphasis on continuous monitoring and testing. PCI DSS 4.0 demonstrates this shift by requiring organizations to use continuous practices such as automated log reviews, vulnerability scans, and threat detection in place of the annual or semi-annual reviews of the past. As a result, compliance becomes more relevant to real-time security needs than simply a snapshot in time.
In summary, PCI DSS 4.0 emphasizes flexibility and accountability; organizations have more discretion in securing cardholder data, but at the same time, they are held to a higher standard in demonstrating that their security is effective at all times.
PCI DSS Best Practices in 2025
Now that the deadline for moving to PCI DSS 4.0 has passed in March 2025, compliance is no longer simply optional; it’s a base expectation. For organizations handling cardholder data, the situation in late 2025 becomes not merely getting certified, but sustaining the certification through additional cyber threats and regulatory expectations. The following best practices provide assistance to organizations that are engaging in compliance on a continuous basis while providing them with long-term resiliency.
1. Automate Compliance Monitoring
Manual monitoring can be slow, imprecise, and hard to scale. By incorporating automation tools, organizations can reliably monitor ongoing requirements for things like vulnerability management, access reviews, and encryption. Automation makes compliance audit readiness easier, faster, and reduces last-minute anxiety prior to all assessments.
2. Continuous Monitoring and Logging
PCI DSS 4.0 focuses on real-time visibility, making continuous monitoring increasingly important. Organizations should centralize logging capabilities, employ a SIEM tool, and generate automated alerts to detect and respond to anomalies, including unusual access attempts or suspicious data transfers. With the right monitoring technology in place, the regular log reviews, now required in PCI DSS 4.0, become much more effective.
3. Zero Trust Alignment
Zero Trust is a concept quickly becoming an industry standard as a security model. It aligns closely with PCI compliance principles. Enforcing least privilege, requiring strong authentication for every access attempt, and segmenting networks all help mitigate the risk of lateral movement and unauthorized access. Zero Trust not only strengthens compliance but also enhances the overall security posture of the organization.
4. Reduce Data Storage
Organizations should only keep cardholder data that is needed for business to run. Reducing cardholder data of sensitive nature reduces the attack surface you have to support risk analysis and compliance.
5. Creating Strong Policies and Accountability
PCI compliance is accomplished best with strong policies and assigned accountability. Organizations can enforce strong password policies, clearly define roles, and outline goals for compliance. Continuous training on policies and standards establishes awareness to protect cardholder data.
6. Oversight of Third-Party Vendors
In addition to onboarding their employee security standards, all service providers and vendors with access to cardholder data must comply with PCI. Organizations should implement ongoing oversight of their vendors to avoid opening third-party risk in their environment.
7. Security Awareness and Incident Response
Human error and social engineering is still the root cause of breaches. Having continuous training to strengthen employee awareness of phishing, scareware, social-engineering, etc. is necessary. The organization should also maintain an incident response plan that addresses any failures or breaches through detection, containment, and remediation.
8. Continuous Improvement
PCI DSS compliance is not a destination. Organizations should periodically reassess and update their programs, use risk-based methods to focus on the highest priority risks, and in the event of conditions in their industry or environment that demand higher standards, exceed the PCI DSS controls. If an organization has a QSA (a Qualified Security Assessor) or ASV (an Approved Scanning Vendor) partner, they can provide valuable guidance on long-term compliance.
Final Thoughts
Today, PCI DSS is not just a regulatory requirement but a competitive advantage for organizations that consider compliance part of their security DNA. Organizations that treat compliance as part of their security DNA enjoy more than just avoiding fines; they generate customer confidence while standing apart from competitive organizations, paving the way to establishing strong reputations around trust. By treating PCI DSS as a micro-form of everyday operations, businesses receive both protection and trust, with them as secure partners in the digital economy, which they consider above all other factors.
NEXT STEPS
Strengthening PCI DSS compliance isn’t just about passing audits; it’s about building lasting trust and resilience. Take the next step toward simplifying and sustaining compliance for your organization:
- Get started faster → Explore now
- See it in action.
Frequently Asked Questions (FAQs)
1. What does PCI DSS stand for?
PCI DSS stands for Payment Card Industry Data Security Standard. It is a global set of security requirements created to protect cardholder data and reduce payment fraud. It was developed by the PCI Security Standards Council (PCI SSC) and applies to any organization that accepts, transmits, or stores payment card transactions.2. Who needs to comply with PCI DSS?
Any business that stores, processes, or transmits cardholder data must comply with PCI DSS. This includes retail merchants, online e-commerce sites, financial institutions, service providers, and even small businesses that accept card payments. There are no exceptions related to the size of the business or the average volume of transactions.3. What are the 12 requirements of PCI DSS?
The twelve requirements of PCI DSS fall into six different security objectives. These objectives include building and maintaining secure networks, protecting stored and transmitted cardholder data, maintaining a vulnerability management program, implementing robust access controls, monitoring and testing computer networks, and maintaining a security policy. The requirements include practical functions such as firewalls, encryption, anti-virus software, access restrictions, logging activity, and employee training.4. What are the 4 PCI DSS compliance levels?
There are four PCI DSS compliance levels determined by the number of transactions a business processes every year. Level 1 is for large companies processing over six million transactions a year, whereas Level 4 is for smaller merchants processing less than 20,000 transactions. Each of the four levels has requirements for validation, from an on-site assessment by a Qualified Security Assessor (QSA) to Self-assessment Questionnaires (SAQ).5. Is PCI DSS compliance mandatory by law?
PCI DSS compliance is not a government regulation by itself. It is a contractual requirement of major card brands like Visa, Mastercard, and American Express. Although there is no legal requirement, you will face financial penalties, increased transaction fees, restrictions on your ability to process payments or, in some cases, lose the ability to accept card payments completely. The financial impact is only one aspect of the consequences of not complying with PCI DSS, as a breach can be reputational damage and legal challenges.In practice, this essentially makes complying with PCI DSS mandatory for any business that accepts cardholder data.