Top 10 Role-Based Access Control Best Practices for 2026

Role-Based Access Control (RBAC) has a central position in today's dynamic business environment in mapping job duties to access privileges within organizations. By organizing users according to their roles within the organization as full-time employees, third-party vendors, or contractors, RBAC provides a simplified, scale-out mechanism for managing access across systems and applications. With 94.7% of organizations having used RBAC at some time and 86.6% viewing it as their top access control model currently, knowing role-based access control best practices is now critical to the enterprise security landscape.
The relevance of RBAC extends beyond the convenience of operations since it resolves fundamental challenges such as delayed onboarding, over-provisioned accounts that are breaches of the principle of least privilege, and stale access upon role transition or employee termination that poses security risks. Without an organized RBAC model supported by automation, organizations put themselves at risk of operational inefficiency and critical security loopholes resulting in data breaches and compliance infractions.
Based on our deep experience across digital-first businesses with Identity Confluence deployments, we've seen firsthand how rbac implementation best practices succeed in harnessing order out of sheer access chaos to become efficient, audit-quality governance. Whether you're governing cloud-native applications, hybrids, or sophisticated enterprise systems, these tried-and-tested role-based access control best practices form a platform for secure, compliant access control that leverages least privilege, enhances compliance, and facilitates secure, role-aligned access at scale.
Key Takeaways
- Define roles based on real job responsibilities and business functions rather than individual user requests
- Avoid excessive roles or conflicting privileges that create security gaps and administrative complexity
- Automate role assignments and access reviews to reduce manual errors and operational overhead
- Monitor permissions continuously and elevate access only temporarily, following just-in-time principles
- Integrate with IAM and Zero Trust models for comprehensive security architecture alignment
What Is Role-Based Access Control?
Role-Based Access Control (RBAC) is a way to control access to a system by assigning a user to a specific role that has permissions rather than assigning permissions to the user directly. The security model of RBAC protects resources (e.g., data, applications, systems) from unauthorized access, modification, and deletion by allowing access based on an individual's Organizational roles and responsibilities. RBAC is a simple and efficient approach to achieve compliance (e.g., SOX, GDPR, HIPAA) that reduces administrative burden, while also increasing the overall security posture.
RBAC = Roles + Permissions + Users
The three fundamental components of the RBAC framework are users, roles, and permissions. Any user can only be assigned to a role, where each role has its own set of permissions that outline what users are allowed to do in systems. This abstraction between user and permissions creates a mechanism that allows easier access management while still maintaining security controls around access.
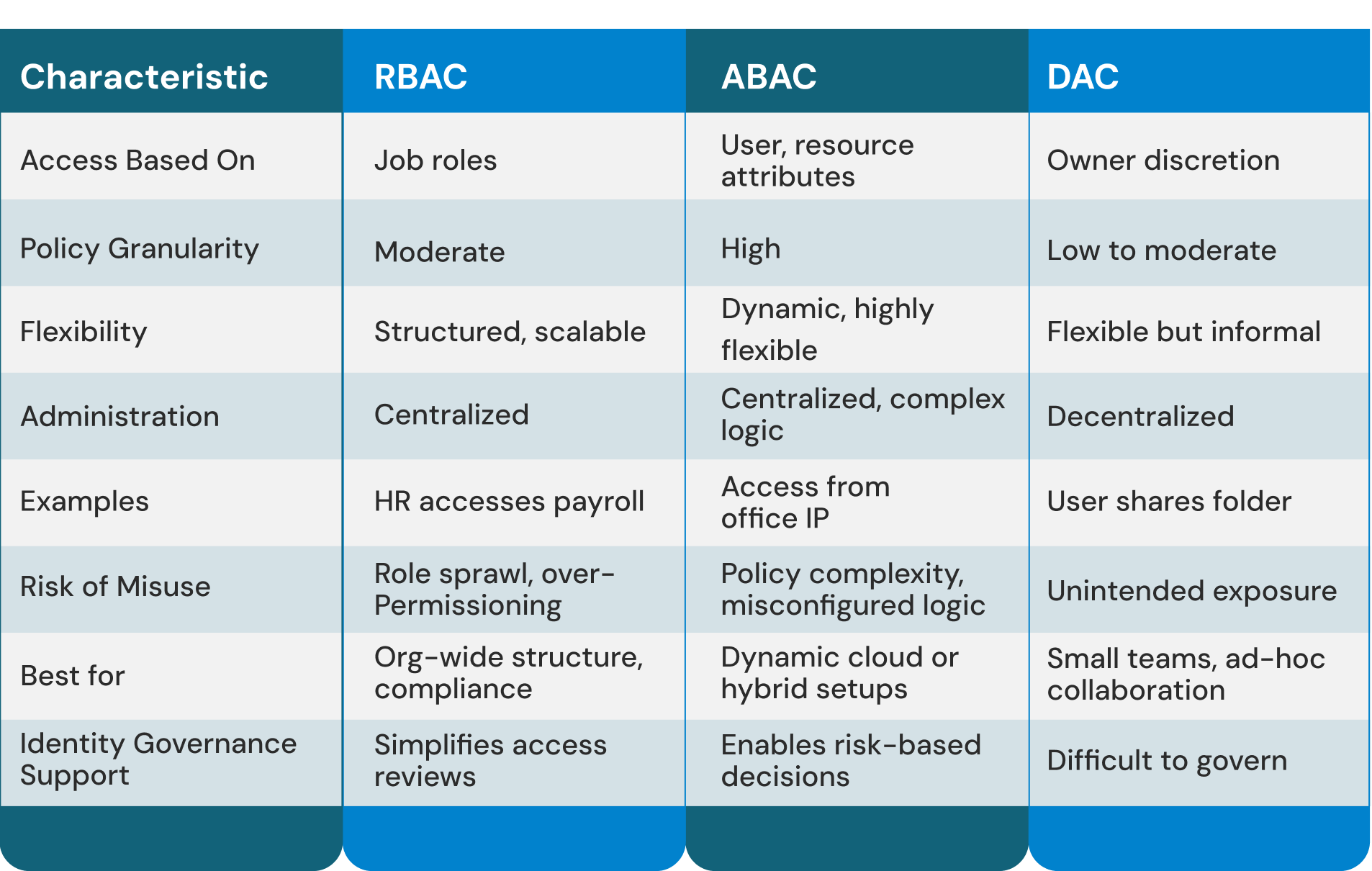
RBAC vs Other Access Control Models:
RBAC provides a structured access governance approach, assigning permissions to roles that align with job functions. This provides an advantage over Attribute-Based Access Control (ABAC) (which considers dynamic attributes such as time, location, and contextual elements) or Discretionary Access Control (DAC) (which relies on data owners to make access decisions based on a variable context). In contrast to Access Control Lists (ACLs) (where a user can only be granted access by the owner who controls whether to provide a user with individual permission), RBAC assigns permissions to logical role containers defined by the organization.
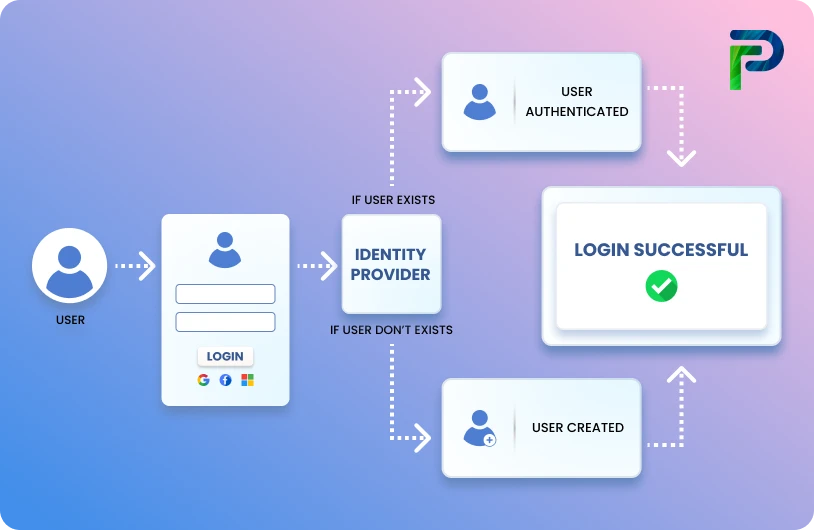
Modern RBAC implementations are integrated with cloud platforms, identity providers, and enterprise applications as part of an overall identity governance approach. The model solves the fundamental problem of managing access rights associated with multi-user, multi-application systems that emerged in the 1970s when online systems were starting to support multiple concurrent users.
The Top 10 RBAC Implementation Best Practices
These battle-tested RBAC implementation best practices have supported enterprises across sectors in implementing secure, scalable role-based access control systems that are able to grow with business objectives while still adhering to strict security provisions.
1. Define Roles with Business Context
Effective role-based access control needs roles that can apply to actual job functions and business workflows rather than personal preferences of users or historical accumulation of access patterns. A business-related approach to mapping roles as opposed to a personal user-focused mapping of roles will allow roles to be defined to stay relevant and have limited relevance as organizational structure may be constantly changing, and avoid making roles in reference to how legacy systems were developed, or in reference to one specific user request.
- Conduct top-down and bottom-up role analysis: Start with organizational charts, formal job descriptions, and departmental responsibilities to establish natural role boundaries and patterns of inheritance. This hierarchical method will illustrate where permissions should flow through organizational hierarchies and also examine actual usage patterns, application logs, and current permission assignments, which will provide a perspective on how actual work is completed as opposed to outlined process flows.
- Avoid over-granular or redundant roles: The best role granularity will normally align with distinct job functions or project responsibilities instead of the requirements for each employee. Doing individual roles, like "Senior Developer Project Alpha" and "Senior Developer Project Beta," would be improper; you will want a single role called "Senior Developer" and then control project-specific access through additional mechanisms.
- Involve business stakeholders: Use structured role definition workshops with department heads and process owners, as well as compliance teams. These stakeholders have a far deeper sense of the requirements for business function and can validate proposed roles to support actual operational needs.
Pro Tip: When rolling out Identity Confluence, Tech Prescient applies sophisticated algorithms for role mining to review current patterns of access throughout related systems. This reveals duplicate or oversized roles and suggests ideal role consolidation. Actually, most organizations find that they have 40–60% more roles than they need, many being temporary roles that became permanent or were created by copy-pasting user rights without checking real access requirements. Sanitizing this is a big step toward better security and simplified identity governance.
2. Enforce Least Privilege and SoD
The principle of least privilege refers to assigning users only the permissions associated with their given roles, specific to their functions as well as nothing greater than those. When combined with Separation of Duties (SoD) controls that limit any one individual from having total authority over key business processes, this serves to create a very effective protection against insider threats and external compromise.
- Prevent fraud via Separation of Duties (SoD): Develop SoD rules that align with both risk tolerance and regulatory obligations established by the organization. Common SoD models include: create requester and approver roles in procurement-based systems; the same user cannot create and approve journal entries in financial-based systems; IT administrators cannot create access and approve their own access permissions.
- Avoid privilege accumulation over time: Establish continuous monitoring for privilege violations, unusual access patterns, and likely SoD violations. Sophisticated analytics can detect when users have accumulated privileges that approach SoD violations, or when users access to systems exceeds the expected behavior of their assigned role within the organization.
- Document role constraints: Set up complete documentation practices that encompass MOUs for role purposes, approvals for role permissions, business owner identification, change history, and use cases. Develop role catalogs that describe what users and admins have with each role, how to request the proper level of access, and limits on the use of roles.
Pro Tip: Organizations leveraging Identity Confluence's automated policy enforcement and ML-based risk scoring capabilities have experienced a 70 percent reduction in over-privileged accounts in the first quarter of implementation. The platform's continuous monitoring surfaces potential privilege violations before they become security incidents.
3. Automate Role Assignment and Deprovisioning
Manual role management introduces delays, mistakes, and security gaps that can continue for months or years when employees change positions or leave organizations. Connecting RBAC to automated user lifecycle events will provide timely, appropriate access provision, consistency, full audit trails, and remove the human error factors that make manual processes vulnerable.
- Use IAM platforms for automated provisioning: Set up real-time data feeds from the authoritative HR systems, such as Workday, SAP SuccessFactors, BambooHR, and other human capital management systems, that will trigger automatic role assignments based on employee action upon lifecycle events. Ensure that role assignments imbue appropriate access provisioning that occurs simultaneously across all connected systems, be they cloud platforms, on-prem applications, network resources, or physical access systems.
- Integrate with HR systems: The integration should encompass not only hiring and termination events, but role changes, department transfers, temporary assignment placement, leave of absence situations, and contractor vs. employee designations. Create the integration logic to be able to accommodate organizational structures that are complex in nature, with matrix reporting relationships, multiple job codes, and international employment structures.
- Include Just-in-Time (JIT) permissions: Utilise Just-in-Time (JIT) access methods for elevated privileges that you require only in sporadic circumstances; when performing a specific time-limit task listed below; when creating a 'break-glass' emergency access procedure; when granting temporary access privileges as part of a project; or, when granting administrative privileges that are time limited. JIT access should interface with approval workflows, expire elevated access after a pre-determined period automatically, and maintain sufficient session detail to allow for compliance and utilization reviews.
Identity Confluence's pre-built connectors provide automated provisioning to cloud and on-premise systems for more than 50 platforms, which can provide Day 1 access provisioning that is able to complete all access grant actions within minutes from the HR system is updated. A common finding for organisations using an integrated system for provisioning is a reduction in provisioning time from days to minutes, while reducing orphaned accounts.
4. Maintain and Review Roles Regularly
RBAC systems need to be maintained over time in order to remain current with changes to business needs, new applications, and changes in the organizational structure. Periodic reviews help ensure roles align with current business needs while identifying and terminating unnecessary permissions before they turn into security risks or compliance failures.
- Perform quarterly access reviews: Develop comprehensive quarterly review cycles to assess both role definitions and individual role assignment, using automated data gathering on role usage patterns, permission usage rates, and irregular access patterns. Construct review workflows to provide managers with a clear and actionable representation of their team members' permissions.
- Retire unused roles: Use the analytics tools designed for you to look at role usage patterns, permission usage rates, and access rates across all operational systems to identify opportunities for optimization. This information reveals opportunities to consolidate roles, identifies inactive permissions we can eliminate, and identifies roles that may have been decommissioned due to changes in both processes or the retirement of associated applications.
- Use logging and monitoring for audit trails: Employ automated systems that facilitate review processes using access data from the current system. Automated systems can pre-populate review forms with current information and make it easier to identify changes since the last review cycle, including identifying possible issues needing manager review. Tie-in workflow systems can send reviews of access data to appropriate personnel and keep track of who, when, and how the reviews were executed, vastly improving a large organization's efficiency regarding complex hierarchies.
5. Implement Policy-Driven RBAC Controls
By establishing formal RBAC policies that scale with your architecture, you create cohesion for access control across all systems and environments while accommodating the complex business scenarios present in today's enterprises. Ideally, these policies will be scalable for iterations on business requirements, while having well-defined security boundaries that accommodate automated decision-making.
- Include inheritance, role groups, and dynamic conditions: Your policy hierarchy should mirror your organizational hierarchy and business relationships, with parent policies that define security baselines for the organization and child policies that extend additional specific requirements (e.g., by department, project, or geography). Create complex condition logic for evaluating multiple factors for access decisions to occur in real time.
- Combine with ABAC for flexibility: You can use the straightforward administrative model of role-based permissions with the flexibility of attribute-based controls for scenarios requiring dynamic access decisions. You can use RBAC for core job function permissions and ABAC to define access attributes for document resources to grant context media access to a small number of staff or to escalate privileges.
- Align with Zero Trust frameworks: If your RBAC policies support Zero Trust frameworks, you do not assume any implicit trust of a user to make the initial authentication request, regardless of location or authentication status. You need to actually implement continuous verification of re-evaluating access decisions based on changing conditions during the user session.
- Identity Confluence's visual policy builder allows business stakeholders to understand and validate complex access control logic without a strong security systems technical background. Policy simulation capabilities let an organization validate and preview changes before implementing them, greatly reducing the risk of unintended access disruption.
6. Avoid Common RBAC Pitfalls
Even well-meaning implementations of RBAC can end poorly without sufficient governance, which can result in security holes, administrative overhead, or compliance breaches that will take an investment of time and money to remediate. Understanding how to avoid common pitfalls of using RBAC will keep your organization secure and will improve your security posture (as it should), as opposed to complicating it.
- Avoid role explosion: Role explosion is when an organization creates too many specific roles to approach the number of users to be managed in a system, and even exceeds the number of users in the system. Have governance procedures on the creation of roles that require substantial business justification for a new role, and regular reviews for opportunities to consolidate. Focus on making roles that relate to job functions and organizational business processes.
- Eliminate wildcards or catch-all permissions: While wildcard permissions like "admin" or "full access" may be an attractive way to quickly deploy, they provide much more access than is necessary, nearly always violating the principles of least privilege. Eliminate the wild card and replace it with a list of permissions that require intentional decision-making for each capability permitted.
- Limit high-privilege roles: Unlimited high-privilege roles seem to impose significant security risks that would benefit from a higher degree of control and oversight. Consider implementing just-in-time activation for administrative access privileges, requiring multi-factor authentication for eligibility to elevated privilege scenarios, and maintaining audit logging of all high-privileged activity in a detailed manner.
We have seen organizations with more than 2,000 roles for fewer than 500 employees, creating an administrative burden rather than any meaningful security. Organizations that deploy full RBAC governance normally experience a reduction of role counts between 50 and 70 percent and a more secure posture.
7. Industry-Specific RBAC Best Practices
Various platforms, industries, and regulatory environments will need different approaches to RBAC that exploit platform-specific capabilities and variations, while complying with different unique compliance and security requirements. Recognizing these variances will allow for optimal implementation, following established best practices, and maximizing the built-in capabilities of the native platform.
- Azure: Use built-in roles, avoid custom unless needed: Azure's RBAC model utilizes role definitions, scope assignments, and resource hierarchy to effectively impose access to subscriptions, resource groups, and individual resources with precision. If possible, leverage built-in roles, since they are maintained and will be automatically updated with new service capabilities as Microsoft adds them. If custom roles are required, then make sure that their permissions are defined tightly, and their scope is clearly defined.
- Kubernetes: Use RBAC rules per namespace: Kubernetes RBAC is at the API level and controls access to cluster resources via role definitions and role bindings that provide the necessary fine-grained control an organization may require for container orchestration. To ensure sufficient workload isolation and to prevent cross-namespace access unless required, use RBAC rules per namespace. Use ClusterRoles sparingly and for truly cluster-wide administrative functions only.
- Snowflake: Grant least privilege via roles + masking policies: Snowflake, like an RBAC model, supports hierarchical role inheritance, which makes it great for more complex data access scenarios where an organization desires broad access across its datasets but specific restrictions to specific data domains. Design role hierarchies that reflect your data governance structure, where data steward roles can inherit appropriate access to multiple data domains. If using RBAC with Snowflake, also use dynamic data masking policies to help ensure sensitive data is not exposed.
Identity Confluence supports industry-specific templates and policy frameworks that address the common regulatory requirements in the healthcare, financial services, and critical infrastructure industries, while still requiring minimal customization.
8. Assign Roles to Groups, Not Individuals
Using security groups to manage access privileges instead of assigning them to individual users results in a simplified process, achieves more consistent enterprise access, improves the onboarding and off-boarding processes, and reduces the risk of human error. In this way, access management transforms from a reactive process of assigning access privileges user-by-user to a proactive process based on policies that manage access privileges in an intentional, structured manner.
- Create security groups by department, project, or function: Develop group structures based on characteristics of the organization, such as functional departments, project teams, locations, security clearance levels, and temporary assignments, all of which could potentially affect access. Establish nested group hierarchies to enable a complex organization, but with clear inheritance.
- Assign roles to these groups in your IAM or directory service: Automate group memberships using trustworthy HR data like job titles, department codes, project assignments, security clearances, and other credible organizational attributes. Create membership rules to deal with intricate case scenarios, including employees with multiple reporting structures and temporary assignments.
- Makes onboarding/offboarding faster and less error-prone: Organizations implementing group-based access management typically enjoy a 60 to 80 percent reduction in individual access assignment overhead, while increasing consistency and significantly reducing errors. The approach allows rapid access onboarding for new employees who can inherit all of their permissions through group membership in a matter of minutes.
9. Use Temporary Access and Role Expiry Controls
In addition to minimizing the attack surface, limiting standing privileges via temporal and project-based access helps organizations sustain operational efficiencies with legitimate business purposes with elevated access. This is based on the notion of just enough access for just enough time, which dramatically lessens the risks of a compromised account or an insider threat.
- Use Just-in-Time (JIT) access for admin roles: Use advanced JIT systems to dynamically provision elevated access based on validated business need and pre-defined approval criteria that meet technical risk thresholds. Build JIT workflows based entirely on business needs, keeping in mind the access requested, sensitivity of the resources being targeted, and current threat contexts.
- Set expiry dates for temporary permissions: Create the algorithms that recommend durations of access, based on historical access patterns, a complexity estimation of the task, and the unique business case of the request, to get access duration recommendations over a multitude of access requests. For general admin activity, set standards with a default duration that will require a business case to go beyond.
- Apply contextual conditions (e.g., location, device type): Establish temporary access solutions that assess contextual variables, such as user location, device trust level, prevailing threat state, and business hour restrictions, at the time of access decision making. Implement adaptive access capabilities that can modify or revoke temporary access, based on the changing state of risk. Identity Confluence's JIT capabilities provide automatic privilege elevation for approved scenarios with a full recorded session and full audit trail. Organizations typically achieve a 90 percent decline in standing administrative privileges while remaining operationally agile.
10. Document and Communicate RBAC Policies
Clear documentation allows security teams, auditors, and end users to comprehend role definitions, permission limits, and approval workflows clearly. This clarity fosters organizational trust while allowing for effective governance and minimizing support overhead through self-service operations and effective communication of policies.
- Include each role's purpose, permissions, and SoD rules: Complete each role document with its purpose statement that encompasses why each role was created, what business function it serves, and why organizations should maintain separation of duties in the role. Complete each role document with the specific permissions that each role has, what capabilities were explicitly included in the role, the capacity the role can perform, and what it can’t do. Ensure that you maintain complete documentation where policies, SoD rules, security constraints, compliance requirements, and policies align.
- Maintain a change log for audits: Create a formalized change control process that documents all changes made to each role, including timestamps, approvers, business justification, and assessments of impact for future reference. Maintain detailed documentation and version history to document role attributes and for rollback capabilities, all to manage detailed audit needs for compliance with regulatory and other obligations.
- Make policies accessible in onboarding or security training materials: Create user-friendly guides that explain and describe how to request access, understand role permissions, and use the policies for each role, without needing to have a technical background when making requests. Include RBAC policy documentation in each organization's security awareness training programmes and as a part of onboarding for new employees.
Frequently Asked Questions (FAQs)
1. What are the best practices for implementing role-based access control?
Initially, conduct a top-down assessment of the organizational structure, alongside a bottom-up assessment of actual system usage. Include least privilege with separation of duties, preferably automated role provisioning, especially through HR integrations (Workday, SAP, etc.). Follow with quarterly access reviews committees with usage visibility and metrics to keep roles clean. Promote role testing in a staging environment, formal declaration and to set up a governance structure through a role review board. Implementing RBAC in phases, versus all at once, is a smart approach for tangible adoption2. How does RBAC relate to IAM and Zero Trust?
RBAC is an essential access control model that aligns with Zero Trust by defining permissions after continuous identity verification is completed. Newer forms of RBAC have evolved to support dynamic, contextual and risk-based decisions that account for behaviour, device trust, and environmental conditions, thereby enabling “never trust, always verify” while still making admin simple. It works as part of a layered, policy-based trustless security solution with foundational security (like MFA), monitoring, and risk-based policies.3. What is the principle of least privilege in RBAC?
The principle of least privilege means assigning only the permissions absolutely necessary for a role to function effectively while preventing access to resources beyond legitimate business requirements. This approach requires starting with zero permissions and building up based on documented business needs rather than beginning with broad access and restricting it. Effective implementation includes regular permission audits to identify unused access, time-limited elevation for temporary privileges, and continuous monitoring to detect privilege creep. The principle extends beyond initial role design to include ongoing maintenance as business needs evolve. Organizations should avoid broad administrative roles and instead create specific functional roles that align with actual job responsibilities, reducing the risk if accounts become compromised.4. How can I avoid role explosion in my RBAC system?
o counter role explosion design roles based on business functions, not outliers. Leverage templates and inheritance to deal with complexity and establish requirements for creating and/or changing roles. Regularly audit roles and consolidate where possible to avoid a duplication of function. Require justification at the business level for new roles and be active to prevent 'temporary' roles from becoming permanent. Research indicates that most orgs unnecessarily carry a surplus of roles, typically between 40-60% due to la lack of discipline in their governance.5. What tools can help with RBAC best practices?
Contemporary IGA platforms such as Identity Confluence offer a streamlined approach to implementing RBAC by automating policy enforcement, continuous active monitoring and machine-learning based risk analytic. Key features include intelligent role mining, automated access reviews, visual policy builders, and integrated provisioning through more than 50 application connectors. When supporting SCIM for auto-provisioning HR integrations, with compliance reports built in, these tools can help you with secured, scalable, and auditable access governance.