What is Deprovisioning? Meaning, Process, and Benefits

Deprovisioning means revoking a user’s access to systems, applications, and data when it's no longer required, typically after an employee exits, a contractor’s term ends, or someone shifts roles internally. It’s a critical part of Identity and Access Management (IAM) that ensures no former users retain access to sensitive business assets.
This has become especially important in today’s enterprise environments, where organizations face challenges like hybrid workforces, increased reliance on SaaS tools, and growing cyber threats. With teams now using dozens (sometimes hundreds) of cloud-based applications, managing user access manually becomes nearly impossible. This increases the risk of leftover accounts, inconsistent permissions, and access blind spots that attackers can exploit.
Done right, deprovisioning not only prevents insider threats and ensures regulatory compliance, but also reduces IT overhead by eliminating unused licenses and accounts. But when handled manually or without clear policies, it can lead to data leaks, audit failures, and long-term vulnerabilities.
In this blog, we’ll break down what deprovisioning means, why it matters, and how you can automate it effectively as part of your identity lifecycle strategy.
Key Takeaways:
- Deprovisioning means removing access when roles change or the user leaves.
- Decreases the risk of insider threats, orphaned accounts, and compliance violations.
- Automated deprovisioning makes your data auditable and accurate while saving time.
- It is a fundamental aspect of implementing Zero Trust and Identity Governance strategies.
What is Deprovisioning?
Deprovisioning refers to the systematic removal of user access rights and deletion of associated accounts from an organization’s systems, applications, and data environments when those credentials are no longer needed. This process is typically initiated when an employee leaves, changes roles, or concludes a third-party contract.
As the final stage in the identity lifecycle, deprovisioning ensures that no unauthorized use of data and resources is permitted and access is denied to former users. Failing to execute deprovisioning promptly can result in “zombie accounts”—inactive or forgotten user accounts that retain access privileges. These orphaned credentials are a significant security risk and can be exploited by threat actors, leading to data breaches, leaks, or regulatory non-compliance.
This process includes:
- Removing access to email, cloud apps, internal tools, and systems
- Terminating directory accounts like Active Directory, etc
- Deactivating Single-Sign-On (SSO) sessions
- Archiving or deleting user data
- Reporting the event for audits
When done manually, this task can be slow, inconsistent, and prone to error, exposing the organization. Automated deprovisioning, based on HR or IT-initiated triggers and managed through predetermined identity policies, closes these loopholes. It guarantees that access is closed off instantly and thoroughly, leaving no lingering credentials to fall through the cracks.
Why Deprovisioning Matters for Identity Security?
Deprovisioning is critical to protecting the employee and contractor life cycle right from initial onboarding through ultimate offboarding. As an employee or contractor leaves the company or switches roles, their access to internal systems, applications, and information has to be shut down instantly to avoid residual access.
Not doing so can leave the organization at risk of serious threats like insider attacks, data breaches, and non-compliance. Many such threats usually arise from orphaned accounts or credentials that were never turned off.
As part of an organization's identity lifecycle management (ILM) strategy, deprovisioning isn't an action but a core control that protects enterprise security and enables operational governance at scale.
Risks of Not Deprovisioning
Neglecting timely deprovisioning can severely compromise your organization’s security and data integrity. These key risks include:
- Security Vulnerabilities: Attackers target inactive or orphaned accounts that haven’t been deprovisioned to get access to sensitive assets, leading to a compromised security posture.
- Data Breaches and Insider Threats: Accounts with active credentials that are no longer in use, also known as Zombie accounts, can be exploited by cybercriminals or discontented ex-employees. This can lead to security breaches, putting important data at risk and damaging the organizational reputation.
- Compliance Violations: When unused accounts are retained even after an employee’s lifecycle is complete, it becomes a compliance violation and risks fines, failed audits, and non-adherence to frameworks like GDPR, HIPAA, SOX, etc. This can also expose you to legal consequences.
- Resource Drain and License Waste: If timely deprovisioning is not performed, unused accounts consume IT resources, storage space, and licenses. This adds up as an unnecessary cost to organizations.
- Audit Complexity and Governance Gaps: Audits become complex when there are inconsistencies in access logs and no detailed audit trails, which can occur due to incomplete deprovisioning.
Benefits of Timely Deprovisioning
Proactive deprovisioning enhances efficiency and security at every level of an organization. Here’s how it’s done -
- Streamlined Offboarding: Deprovisioning eliminates the hassle of manual tracking of account access across tools. Access revocation is instead linked to pre-defined workflows, like HRMS triggers or role changes, that ensure prompt and consistent enforcement of security policies.
- Minimized Human Error: Manual processes often leave room for error, such as lost accounts, residual access, or partial deletions. Automation prevents unauthorized lingering access and misconfigurations, strengthening your security posture.
- Improved Execution: With automated triggers, deprovisioning happens in real-time across all integrated systems like cloud apps, VPNs, and file servers, drastically reducing delays that might otherwise be security blind spots.
- Centralized Visibility and Auditability: All deprovisioning actions are logged and timestamped. This helps generate comprehensive reports that support both internal and external audits as it provides clear traceability for user access lifecycle events.
- Compliance Assurance: Automated access removal helps enforce compliance regulations like HIPAA, GDPR, SOX, and other external regulations. Automatic deprovisioning applies these controls at scale, reducing the risk of breaches and corresponding penalties.
- Cost Savings: With automated deprovisioning, you can identify and remove inactive accounts, freeing up licenses and IT resources. This reduces administrative workload and lowers support costs, while optimizing IT budgets and enabling better resource allocation.
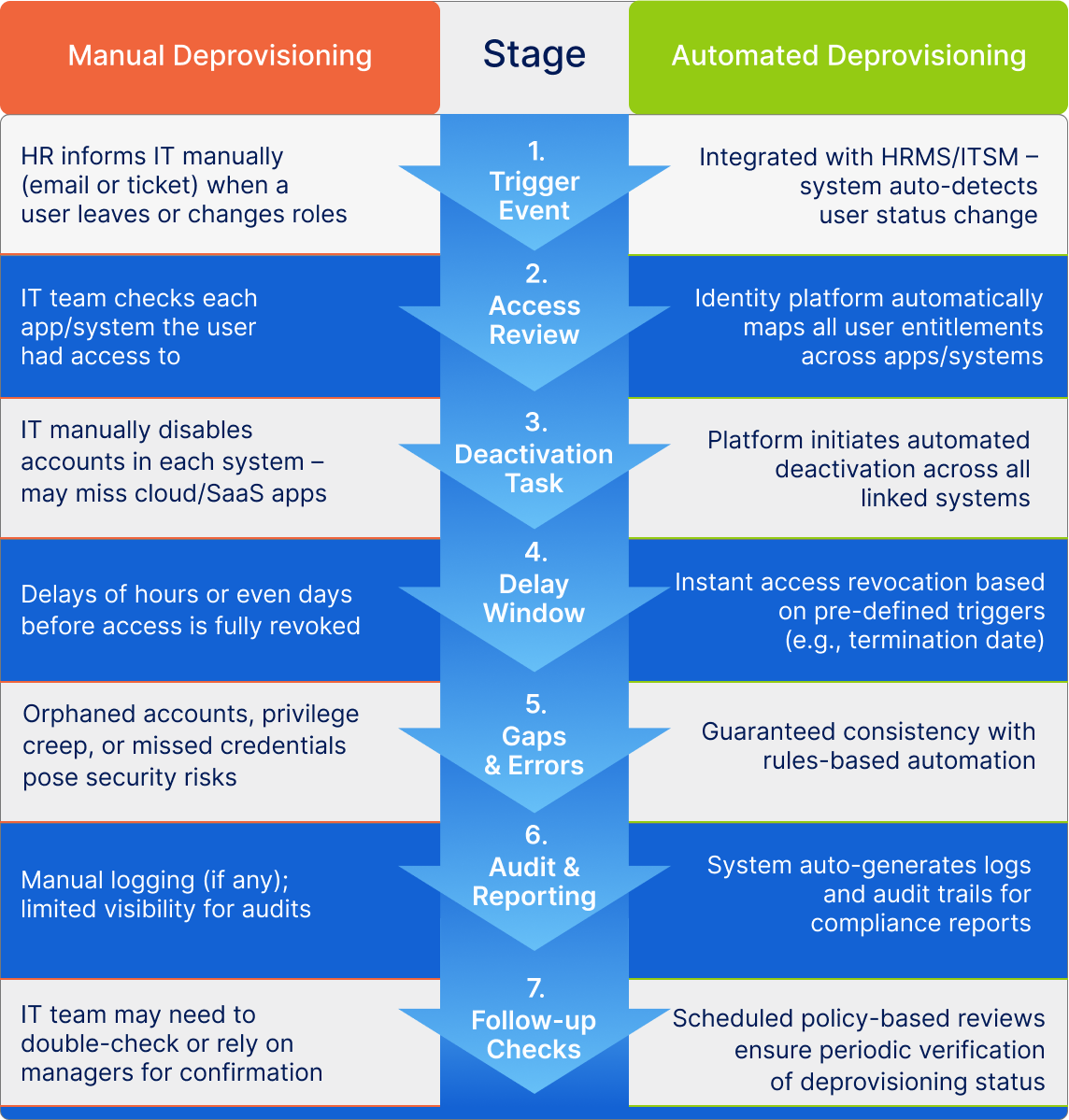
Manual vs. Automated Deprovisioning
Not all deprovisioning strategies are created equal when it comes to handling user exits. Manual processes often depend on human memory, spreadsheets, and IT tickets, all of which can be delayed, inconsistent, or overlooked. Automated deprovisioning, on the other hand, uses predefined rules, integration with HRMS and HCM systems, and identity governance tools to guarantee that access is removed safely and on time.
Manual Deprovisioning Challenges
- Human error and oversight: In a large organization, users are given access to multiple tools, systems, and resources. IT teams can forget to remove access to one or a few more systems, causing a lapse in security.
- Time-consuming and reactive: Manual deprovisioning often causes delays between the time taken for the employee to exit and access termination. This is because it requires tickets, approvals, and coordination between many departments.
- Inconsistent execution: Without a set process, some accounts may get deleted while others get overlooked. This increases the risk and lowers accountability.
- No audit trail: Manual work rarely leaves a clear, tamper-proof record of who had access, why, and when it was removed, as well as whether the process was fully completed.
- License and cost inefficiencies: Orphaned accounts may still access paid licenses, leading to higher IT costs that are unnecessary.
Advantages of Automated Deprovisioning
- Immediate access revocation: Automation tools work with HCM Systems, HRMS, or Directory services to remove an employee’s access in real-time as soon as they leave or switch roles.
- Policy-driven consistency: Every account, including email, VPN, SaaS apps, and cloud services, is deprovisioned according to pre-defined rules and workflows.
- Compliance and auditability: The detailed logs and audit trails ensure that internal rules and external policies like GDPR, SOX, and HIPAA are followed.
- Saving time and resources: As the system takes care of routine access revocation, IT teams don’t have to be occupied with repetitive tasks and actually focus on strategic initiatives.
- Insider threat mitigation: Automatic termination of access greatly reduces the chances of credentials being misused, which improves overall security.
- Reduced attack surface area: When accounts no longer in use are immediately disabled, automated deprovisioning ensures any entry points that can be exploited by attackers are eliminated.
- Consistent enforcement of the Principle of Least Privilege: Automated deprovisioning prevents privilege creep by ensuring access is retained by only those who need it and nothing more.
Self-Service Provisioning
Self-service provisioning gives users the ability to request and control access to IT resources such as applications, virtual machines, or internal tools automatically, using a secure, intuitive interface. Rather than having to wait for IT staff to manually provision access, users can trigger requests that are automatically fulfilled according to pre-established policies, approval processes, and role-based access controls.
This method uses automation and governance templates to provide the right resources to the right individuals without taking on undue risk.
Key components of self-service portals:
- Role-based access requests for all resources
- Triggers workflows automatically for policy checks and approvals
- Track all access requests in real-time
- Reduce IT helpdesk workload with self-service password resets and updates.
Integrating self-service provisioning with robust identity governance tools helps you as an organization find the right balance between control and agility. Employees get what they need faster, IT and security teams retain visibility and oversight, and implement least-privilege principles. When you combine self-service provisioning with automated deprovisioning, you get a system that is not just secure but also flexible.
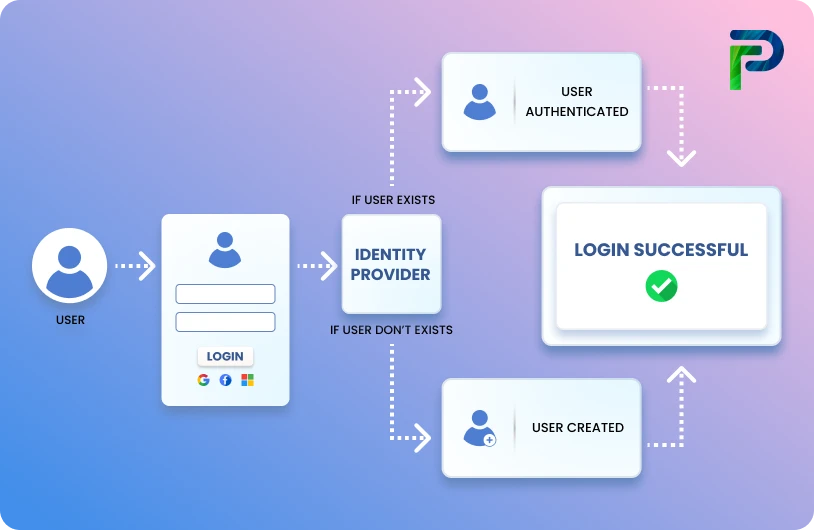
Provisioning and Deprovisioning in Identity Lifecycle
Managing who gets access to what, when, and why is not just a checkbox you tick, but it is a continuous and evolving process. It includes everything from onboarding, role/department changes, to offboarding. And at the core of these functions are two main components are provisioning and deprovisioning. Not having either one can cause security gaps, compliance issues, and loss of productivity.
What is Provisioning?
Provisioning means setting people up with the right access to systems, tools, and data based on their roles, needs, department, etc. This process is usually initiated when a new employee joins, someone switches roles, or access is given to a third-party vendor/contractor.
Key steps in provisioning:
- Setting up user profiles in directories like Active Directory or cloud identity platforms.
- Assigning access to the right SaaS or on-prem apps
- Applying role-based access controls and policy settings
- Integrating with systems like HRMS, HCM, and ITSM to show real-time status
With provisioning, you ensure:
- New hires are productive from day one and don’t have to wait for permissions
- The principle of least privilege is enforced
- Reduction in manual errors, especially if the entire process is automated
Role of Deprovisioning
If provisioning is handing out the keys, deprovisioning is changing the locks. Ensuring that accounts are disabled when they are no longer in use or removing access when it isn’t required.
Core deprovisioning actions:
- Deleting users from directories, apps, and systems
- Removing authentication tokens and access credentials
- Terminating their email, chat, and shared workspace access
- Track all these changes and log them for compliance and audits
Deprovisioning is a fundamental step in the identity lifecycle process to help you maintain security, compliance, and resource allocation. Without it, you can risk insider threats, zombie accounts, and failure to meet regulatory requirements.
A complete Identity Lifecycle Management ensures that provisioning and deprovisioning are automated and have pre-set triggers that enable real-time governance.

Best Practices for Secure Deprovisioning
Effective deprovisioning needs to be consistent, systematic, and tailored to your business needs. Here’s how you can do it right -
- Align deprovisioning with your use cases
Every user departure is different, and your deprovisioning process should align with that. Identify all the user lifecycle scenarios, like employee offboarding, internal transfers, or contractor offboarding. Every scenario requires distinct access removal steps, timelines, and approvals. Map out your workflows to prevent both overkill (revoking too much access, slowing down BAU work) and underkill (leaving a security gap). - Automate deprovisioning with IGA tools
Automation guarantees consistency, reduces IT workload, and removes any chance of human error in the process. Whereas manual processes are inconsistent and cause delays. You can automate deprovisioning with modern Identity Governance and Administration (IGA) platforms based on pre-set HR triggers and policies. - Implement role-based access control and automated policy triggers
Access should follow the role, not the individual. This simplifies deprovisioning and helps enforce least-privilege access. Incorporate this with policy-based triggers like 30-day inactivity thresholds, contract end dates, and HR status changes to disable access when predefined conditions are met. - Conduct regular access reviews and compliance reporting
Review user access lists periodically to identify any dormant, unutilized, or risky accounts. With periodic access certifications, you can verify that only authorized users retain access. Also, generate audit reports to check audit readiness and ensure compliance standards are followed.
Deprovisioning Use Cases
Deprovisioning is a business-critical process that supports integrity, compliance, and operational resilience. Here are some use cases where deprovisioning plays a critical role -
- Enterprise Offboarding
When an employee leaves, their access to all corporate data and systems should be disabled instantly. If not done, this can result in orphaned accounts, data leaks due to lingering access, and an elevated risk of insider threats. Automated deprovisioning ensures that access to all accounts, like VPN, email, and cloud, is disabled based on real-time HR updates. - SaaS Account Termination
There is a proliferation of SaaS apps like Slack, Salesforce, GitHub, etc, and without centralized visibility, users maintain access long after their work requires it. Deprovisioning workflows extend to third-party apps and remove access across the tech stack. This helps in cutting down License costs considerably by eliminating unutilized access. - Healthcare: HIPAA Compliance
Patient data is sensitive, and HIPAA ensures this information is secure with strict regulatory standards. Incomplete or delayed deprovisioning can cause HIPAA violations, unauthorized data exposure, and heavy fines. Healthcare organizations employ ILM solutions to implement least-privilege access and integrate with EHR systems to revoke access instantly when needed. - Financial Services: SOX and Access Controls
SOX has a strict mandate for financial institutions to protect important systems and data. Audits must prove that ex-employees, consultants, or contractors have no access to trading platforms, accounting systems, or customer data. Automated deprovisioning includes segregation of duties (SoD) and real-time compliance reporting. - Cloud Infrastructure and DevOps Environments
Cloud platforms like Azure, AWS, and GCP need strict access controls for developers, vendors, and service accounts. IAM roles, SSH keys, and API tokens often linger if not properly managed. They can be exploited if not disabled immediately.
Final Thoughts
Deprovisioning may be the final step in the Identity Lifecycle, but the impact it has on your organization’s security and compliance is anything but small. It acts as a fortification against all security threats, ensuring nobody can access what they are not allowed to. Automating deprovisioning is a simple yet significant step that can bring you structure and peace of mind.
Ready to close the gaps in your access management strategy?
Frequently Asked Questions (FAQs)
1. What does deprovisioned mean in IT?
In IT, deprovisioning means the process of revoking a user’s access to apps, systems, and data. This usually happens when an employee leaves an organization, switches roles, or no longer needs this specific access. This helps to maintain security and compliance, ensuring that no unauthorized user has access to critical data.2. What is the difference between provisioning and deprovisioning?
Provisioning means granting users access to systems, tools, apps, and data required by them to perform their role, usually at the time of onboarding or role change. Deprovisioning, on the other hand, is the revoking of that access when the user leaves or no longer needs those privileges anymore. Together, they form the core pillars of Identity Lifecycle Management.3. Why is automated deprovisioning important?
Automated deprovisioning removes access privileges in real-time, according to pre-defined triggers like HR updates or termination notifications. It rules out delays and human mistakes present in manual processes, lowering insider threats, audit failure, and orphaned accounts risks.4. How does deprovisioning improve cybersecurity?
Deprovisioning improves cybersecurity because it prevents stale credentials from accessing organizational systems except for active, authorized users. It averts data breaches due to stale credentials, reduces the attack surface, and enables Zero Trust principles through least privilege and role-based access.5. What happens if you don’t deprovision accounts?
Not deprovisioning accounts can cause "zombie accounts," which are inactive credentials left open and exposed. These can be exploited by attackers, resulting in non-compliance with regulations (such as GDPR, HIPAA, or SOX), which risks sensitive customer and organizational data, and leads to undue inflation of licensing and resource expenses.