
What is GDPR? Meaning, Compliance & Security Explained


The General Data Protection Regulation, also known as GDPR, is a landmark (EU) European Union data privacy law that became effective from 25th May, 2018. It sets the standards for collecting, processing, storing, and transferring personal data in an organization. It also ensures that the personal data collected is handled securely and grants individuals the right to control their information.
GDPR is applied globally. It means that any organization offering goods, services, or tracking the behavior of EU residents must comply with GDPR, regardless of whether your company is located within the borders of the EU or outside. By having equal data protection rules all across the EU, it will be easy for businesses to follow the law and ensure people’s personal data stays safe.
According to Vinciworks' 2024 study, the total fines issued under the GDPR have reached €5.88 billion, highlighting the regulation's strict enforcement and the enormous financial consequences connected with noncompliance.
In this article, we will go over GDPR standards, clarify what constitutes personal data, detail data subject rights, examine the relationship between GDPR and cybersecurity, and present a step-by-step compliance strategy for 2025. By the conclusion, you'll understand both the legal duties and the practical procedures required to make your company GDPR compliant.
Key Takeaways
- Understand what GDPR is, who it applies to, and why it matters for businesses handling EU citizen data
- Learn the key personal data protections, user rights, and organizational obligations under GDPR
- See what GDPR compliance means for businesses, including consent management, cross-border data handling, and penalties for violations
- Discover how strong security practices like encryption, MFA, and breach monitoring support GDPR compliance
- Follow a practical 2025 roadmap from mapping data flows to updating notices, securing systems, appointing DPOs, and training staff
What Does GDPR Stand For and Why It Matters
GDPR, or General Data Protection Regulation, is a European Union regulation that safeguards individuals' personal data and privacy. It provides a comprehensive framework for the collection, processing, storage, and transfer of personal data, setting clear rules for how organizations must handle such data. The regulation ensures that all personal data is processed securely and transparently, promoting accountability. Additionally, GDPR enforces strict penalties and fines for businesses that fail to comply with its requirements.
The regulation defines three main types of data parties: data subjects, controllers, and processors. A “data subject” is any person whose data is being collected. A “controller” is an organization that decides the purpose, conditions, and methods for processing that data. A “processor,” on the other hand, is an organization that processes personal data on behalf of the controller.
What makes GDPR significant is that controllers and processors don’t have to be located in the European Union. They can be based anywhere in the world, even in the United States. This is a major shift from older EU rules, making GDPR much more far-reaching.
Another key concept under GDPR is personal data. Not all data is protected; only information that can identify an individual. For instance, age by itself would not fall under GDPR, but age combined with a name would, because together they can identify someone.
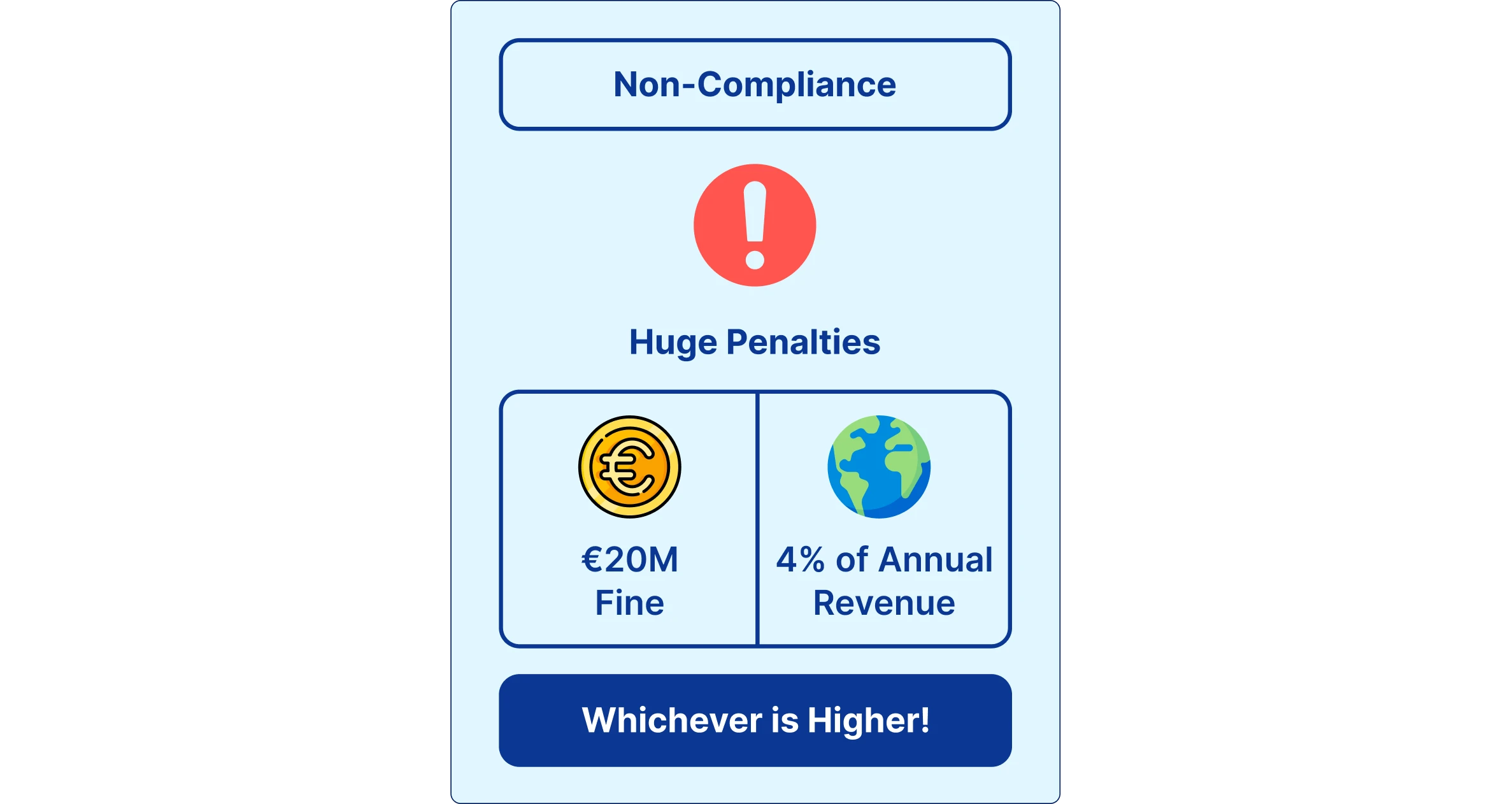
GDPR also comes with strict consequences for non-compliance. The fines are much higher than before, with the data protection supervisory authority able to impose penalties of up to 4% of a company’s annual revenue or EUR 20 million, whichever is greater. This is why GDPR truly matters. It’s not just about avoiding rules and penalties, it’s about keeping data safe, protecting privacy, and building trust between individuals and organizations.
GDPR Requirements Explained
To comply with GDPR, organizations must follow a clear set of rules that define how personal data is collected, stored, and used. These requirements cover everything from understanding what qualifies as personal data to ensuring that individuals have control over their information. They also establish strict expectations for security, accountability, and governance, making data protection an ongoing responsibility rather than a one-time task.
What Counts as “Personal Data”?
Under the GDPR, personal data refers to any information that can directly or indirectly identify an individual. This covers a wide range of data types, not limited to just names or email addresses. Here are key categories of personal data:
- Direct Identifiers: These are clear, straightforward identifiers such as a person’s name, home address, email address, and identification numbers. Without proper protection, this information can easily be exploited for identity theft or fraud.
- Indirect Identifiers: Data like IP addresses, cookie IDs, and location data fall into this category. While not directly revealing a person’s identity on their own, they can be combined or analyzed to track and profile individuals.
- Specific Factors: Information related to a person’s physical, genetic, mental, economic, cultural, or social identity is considered especially sensitive under GDPR. Examples include biometrics, ethnicity, religion, political opinions, health records, or economic status, which reveal intimate aspects of someone’s identity.
- Online Identifiers: Data such as advertising identifiers of a phone or online usernames are included. These identifiers help online services personalize experiences, but can also be used to track and profile individuals without their knowledge.
- Combined Information: Even seemingly harmless data points, when collected together, may lead to the identification of an individual. For example, combining browsing history, device information, and app usage patterns can effectively create a detailed profile of a person.
Importantly, GDPR covers both data collected after its enforcement and any personal data gathered before it came into effect, ensuring ongoing protection of individual privacy.
Data Subject Rights
Under the GDPR, individuals, referred to as data subjects, are given strong rights to control how their personal data is used. These rights ensure transparency, fairness, and accountability in data handling. Key rights include:
- Right of access: Individuals can request a copy of their personal data held by an organization. This gives them visibility into what data is stored, why it is processed, and who it is shared with.
- Right to be informed: Data subjects must receive clear, accessible explanations about how their personal data is collected, used, and managed by organizations, helping them understand the purpose and scope of data processing.
- Right to rectification: If personal data is incomplete or inaccurate, individuals can demand corrections. This ensures that decisions made on the basis of their data are fair and reliable.
- Right to object: Data subjects can oppose the use of their personal data for specific purposes. In certain situations, organizations must honor this objection and stop processing the data, unless there are compelling legitimate grounds to continue.
- Right to data portability: Individuals can request their personal data in a structured, commonly used, and machine-readable format. This empowers them to transfer information easily between service providers, such as switching banks or telecom operators.
Beyond these, GDPR also grants rights like restricting processing, objecting to data use, and contesting automated decisions. Together, these provisions give individuals greater control and hold organizations accountable for protecting privacy.
Security Measures & Accountability
The GDPR places strong emphasis on both prevention and accountability when it comes to data security. Organizations are expected to implement appropriate safeguards, such as encryption, access controls, and regular monitoring, to minimize the risk of unauthorized access or misuse of personal data.
In addition, GDPR has strict rules for handling breaches. If a data breach occurs, organizations must detect, assess, and report it to the relevant supervisory authority within 72 hours of becoming aware of it. Failure to do so can lead to heavy penalties and reputational damage. This requirement ensures that organizations remain accountable and transparent in how they respond to security incidents.
Role of Data Protection Officers (DPOs)
Under the GDPR, appointing a Data Protection Officer (DPO) is mandatory only for specific types of organizations, not every data controller or processor. The requirement applies in the following situations:
- The organization is a public authority or body, except when acting in a judicial capacity.
- The organization’s core operations involve systematic and regular monitoring of individuals on a large scale, for example, companies like Google that track user behavior across services.
- The organization conducts large-scale processing of sensitive personal data, such as health records, biometric data, or information about criminal convictions, as outlined in Articles 9 and 10 of the GDPR, typical of medical practices or criminal justice entities.
Even when not mandatory, organizations may choose to appoint a DPO to benefit from specialized expertise in data protection. The DPO’s key duties include guiding the organization on GDPR requirements, advising teams on their responsibilities, conducting training and audits, monitoring compliance, and acting as a liaison with regulatory authorities.
What Does GDPR Compliance Mean for Businesses?
For businesses, GDPR compliance goes far beyond just ticking legal boxes. It requires embedding privacy into daily operations, from how consent is managed to how data is transferred and secured across borders. Non-compliance isn’t just costly in terms of fines; it can also erode customer trust.
Consent Management
Under GDPR, consent is one of the cornerstones of lawful data processing, and the rules around it are stricter than ever. Organizations must ensure that:
- Consent is explicit and informed: It must be freely given, specific, and unambiguous. This means no vague terms, bundled permissions, or hidden clauses.
- Requests are clear and transparent: Consent forms must be written in plain, straightforward language and presented separately from other terms and conditions.
- Opt-in only, never opt-out: Pre-checked boxes or default consent are not allowed. Users must take a deliberate action, like ticking a box, to agree.
- Easy withdrawal: Individuals must be able to withdraw consent at any time, and organizations must respect that choice without shifting to another legal justification.
- Special rules for children: For users under 13 years of age, parental permission is required before processing their personal data.
- Proof of consent: Businesses must keep records demonstrating when and how consent was obtained, ensuring accountability if challenged.
Cross-Border Data Handling
GDPR extends beyond Europe’s borders, requiring that personal data transferred outside the EU/EEA is protected to the same high standard as within the EU. Organizations must use authorized transfer methods to ensure compliance. These include Adequacy Decisions (where the European Commission confirms a country provides sufficient data protection), Standard Contractual Clauses (SCCs), or Binding Corporate Rules (BCRs).
If no Adequacy Decision exists for a country, such as the US, businesses must implement strong legal and technical safeguards before transferring data. Additionally, data controllers are required to inform individuals about cross-border transfers and share details of the protection measures applied.
Key terms to understand in this context:
- Personal Data: Any information relating to an identified or identifiable person.
- Data Controller: The organization that decides how and why personal data is processed.
- Third Country: Any nation outside the EU or European Economic Area (EEA).
Penalties & Fines (up to €20M or 4% of Global Turnover)
GDPR has some of the strictest penalty structures in the world, designed to hold businesses accountable for protecting personal data. Non-compliance can result in significant financial and reputational damage.
There are two tiers of fines under GDPR:
- First tier: For less severe violations, such as poor record-keeping or failing to notify of a breach, organizations can face fines of up to €10 million or 2% of global annual turnover, whichever is higher.
- Second tier: For more serious violations, like unlawful data processing, lack of user consent, or ignoring data subject rights, the fines increase to €20 million or 4% of global annual turnover, whichever is higher.
Beyond these financial penalties, data subjects also have the right to seek compensation for damages if their personal data has been mishandled. This makes compliance not only a legal obligation but also a crucial trust factor between businesses and their customers.
GDPR and Cybersecurity: How They Connect
GDPR and cybersecurity go hand in hand; strong data protection is impossible without strong security. The regulation makes it clear that safeguarding personal data isn’t just a compliance task but a continuous responsibility. From building secure systems by design to preventing and responding to breaches, organizations must align their cybersecurity practices with GDPR’s principles.
Security by Design & Default
GDPR requires organizations to build privacy and security into their systems from the ground up, not as an afterthought. This principle, known as security by design and by default, ensures that protection is embedded in every step of data handling.
In practice, this means any new product, service, or process must integrate data protection principles at every stage of development. For example, if you’re launching a new mobile app, you need to carefully assess what personal data it will collect, limit collection to what’s truly necessary, and ensure that security measures such as encryption, access controls, and data minimization are in place from the start.
“By default” also means privacy-friendly settings must be turned on automatically. Users shouldn’t have to opt out of unnecessary data collection; the system should protect their privacy without extra effort on their part. This proactive approach ensures that compliance isn’t just about ticking a box but about embedding security and accountability into the organization’s DNA.
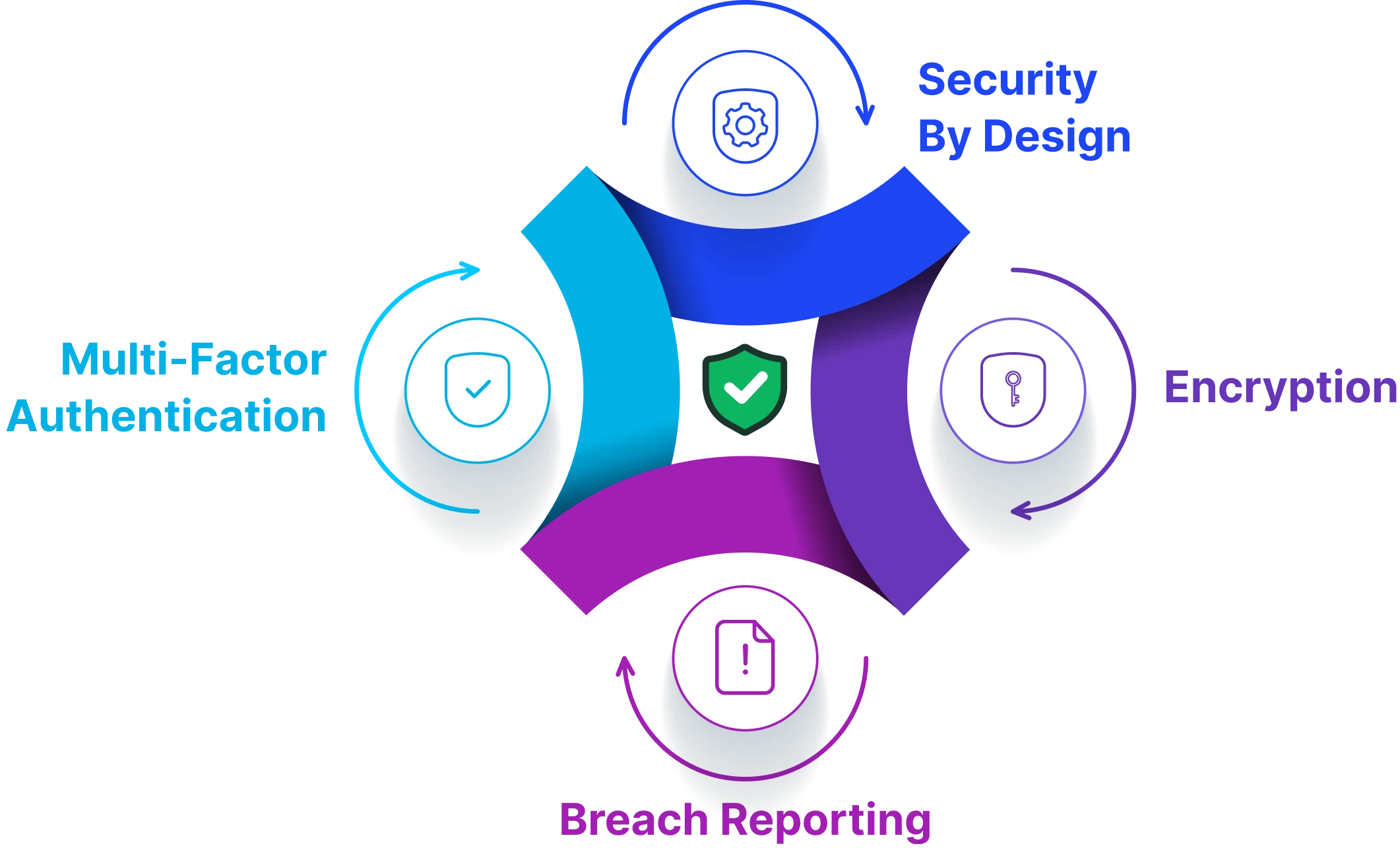
Protecting Against Breaches (MFA, Encryption, Monitoring)
One of the strongest connections between GDPR and cybersecurity lies in breach prevention. To remain compliant, businesses must proactively secure personal data with both technical defenses and organizational safeguards.
- Multi-Factor Authentication (MFA): Strong authentication reduces the risk of unauthorized access to accounts holding sensitive data. By requiring multiple verification steps, MFA makes it significantly harder for attackers to break in using stolen credentials.
- Encryption: Encrypting personal data, whether in storage or during transmission, ensures that even if information is intercepted or stolen, it remains unreadable and useless to cybercriminals.
- Monitoring & detection: Continuous system monitoring, logging, and alerting help organizations quickly detect suspicious activity. Early detection means faster response and less damage in case of a breach.
Despite best efforts, if a breach occurs, GDPR requires notification to supervisory authorities within 72 hours. However, if safeguards like encryption render the data inaccessible, the regulatory burden may be reduced. By combining MFA, encryption, and proactive monitoring, businesses not only strengthen cybersecurity but also demonstrate accountability under GDPR.
GDPR Cybersecurity Checklist
To ensure effective cybersecurity under GDPR, organizations should integrate the following essentials into their compliance strategy:
Step 1. Establish Legal Foundations for Data Processing
- Before collecting any data, verify that your organization has valid legal grounds for processing under GDPR. This includes obtaining explicit consent from data subjects, fulfilling contractual obligations, complying with legal requirements, protecting vital interests, performing public interest tasks, or demonstrating legitimate business interests that don't override individual rights and freedoms.
- Start with a clear data audit: identify what personal data you collect, where it resides, who accesses it, and how long it's stored. This foundational step reinforces accountability and enables risk management. Clearly articulate the legal basis for all processing activities, such as consent or legitimate interest, and reflect this explicitly in your privacy policy for transparency.
Step 2. Comprehensive Data Mapping and Classification
- Map and Document Your Data Processing by conducting a thorough inventory of all personal data your organization handles. Classify data into standard categories and special categories (including biometric data, genetic data, political or religious beliefs, health information, racial or ethnic origins, and sexual orientation) to ensure appropriate protective measures are implemented for each data type.
- Document retention periods for each data category and maintain detailed records of data controllers, processing purposes, and data recipients as required under Article 30 of GDPR.
Step 3. Embed Privacy and Security by Design
- Integrate strong technical safeguards like encryption, pseudonymization, and data minimization at every development phase. This ensures risks are mitigated from the point of inception. Implement robust physical security controls, including restricted access to servers, databases, and critical infrastructure components.
- Prepare for high-risk processes using Data Protection Impact Assessments (DPIAs) to proactively identify and reduce potential privacy risks. DPIAs are mandatory when using new technologies for large-scale processing, handling substantial volumes of special category data, conducting systematic monitoring, or when processing activities may significantly impact individual rights.
Step 4. Implement Strong Organizational Controls
- Assign clear ownership and responsibility, designate someone responsible for GDPR oversight, and, if applicable, appoint a Data Protection Officer (DPO). A DPO appointment is required for public authorities, organizations conducting regular systematic monitoring on a large scale, or those processing large volumes of special category data or criminal conviction information. Ensure the DPO operates with sufficient autonomy and reports directly to senior management.
- Foster a culture of awareness: train staff on GDPR requirements, deploy internal data protection policies, and ensure third-party processors are bound by Data Processing Agreements (DPAs).
Step 5. Develop Comprehensive Privacy Policies
- Create both internal and public-facing privacy policies that govern all aspects of data collection and processing. Internal policies should cover data flows, employee access controls, and data sharing practices. Public-facing policies must be easily accessible on your website, clearly explaining how and why data is collected, how it will be used, and how individuals can exercise their rights. Update and notify customers whenever policy changes occur.
Step 6. Prepare for Breach Management
- Establish formal procedures to detect, respond to, and report data breaches. GDPR mandates notifying supervisory authorities, and in some cases data subjects, within 72 hours of awareness. Your breach response plan should include communication channels for timely reporting, specify the nature of breaches, affected data categories and volumes, DPO contact information, likely consequences, and planned remediation measures. Notify data subjects directly when breaches pose a high risk to their rights and freedoms.
Step 7. Establish Data Processing Records
- Create and maintain a comprehensive data register (Record of Processing Activities - ROPA) that documents all data processing activities. This register should answer key questions: data sources, content types, collection purposes, legal bases, special category classifications, usage intentions, data sharing arrangements, and implemented safeguards. This documentation is essential for demonstrating compliance during audits.
Step 8. Determine EU/UK Representative Requirements
- If your organization operates outside the EU or UK but processes personal data of individuals in these regions, assess whether you need an EU or UK-based representative. This requirement applies unless you process data occasionally on a small scale, don't handle special categories of data, conduct low-risk processing, or operate as a public authority.
Step 9. Continuous Monitoring & Vendor Oversight
- Regularly test and evaluate your controls, both internally and across third-party services. Use audits, assessments, and incident simulations to ensure effectiveness. Maintain vigilance over your vendors: ensure they uphold GDPR-aligned security standards, conduct risk assessments, and establish compliant data agreements.
- Update vendor contracts and Data Protection Addendums to include clear data privacy and security provisions, breach reporting obligations, and defined roles between data controllers and processors. Implement comprehensive third-party risk management to safeguard customer data handled by SaaS providers and other vendors.
Step 10. Implement Cybersecurity Frameworks and Standards
- Deploy established cybersecurity frameworks such as the NIST Cybersecurity Framework to maintain your security posture. Ensure systems process only necessary data by default, implement strong encryption for all GDPR-governed data, and maintain robust security practices, including access controls and data management policies. Consider using compliance management software to automate evidence collection and reduce compliance costs.
How to Comply with GDPR in 2025 (Step-by-Step)
Staying compliant with GDPR isn’t just about avoiding fines; it’s about building trust with customers by safeguarding their personal data. Here’s a simple step-by-step roadmap for businesses in 2025:
Step 1: Map data flows
Start by conducting a data audit to understand what personal data you collect, where it’s stored, who has access, and whether it leaves the EU. Documenting these flows is essential for accountability and identifying potential risks.
Step 2: Update privacy notices
Your privacy policy must be clear, transparent, and written in plain language. Explain what data you collect, why you collect it, how long you keep it, and how individuals can exercise their GDPR rights (like access, rectification, or deletion).
Step 3: Implement security controls Adopt both technical and organizational safeguards. Use tools like encryption, multi-factor authentication (MFA), and monitoring systems to secure personal data. Pair these with policies like access restrictions and regular employee awareness programs.
Step 4: Appoint a DPO if required If your business processes large-scale personal or sensitive data, GDPR requires you to appoint a Data Protection Officer (DPO). This person oversees compliance efforts, serves as the point of contact with regulators, and ensures privacy is embedded across operations.
Step 5: Train employees Employees are often the weakest link in security. Regular training on phishing, data handling, and GDPR requirements ensures that everyone, from HR to IT, knows their responsibilities and helps prevent breaches.
Final Thoughts
GDPR is no longer just a European regulation; it’s a global benchmark for privacy and data protection. In an era where personal data fuels business growth, compliance is not optional; it’s the foundation of trust, transparency, and long-term resilience.
At Tech Prescient, we simplify GDPR compliance while strengthening cybersecurity. From data mapping and consent management to strong security controls and accountability, we ensure your business stays compliant without slowing innovation.
Now is the time to rethink data protection. Embrace GDPR compliance with Tech Prescient to safeguard your customers, reputation, and growth against rising regulatory and cyber risks.
Frequently Asked Questions (FAQs)
1. What does GDPR mean in simple terms?
GDPR, or the General Data Protection Regulation, is an EU law designed to protect personal data. It gives individuals more control over how their information, like names, emails, or IP addresses, is collected, stored, and used. For businesses, it sets clear rules on handling data responsibly.2. Does GDPR apply to US companies?
Yes. GDPR doesn’t stop at EU borders; it applies to any company, including those in the US, that processes or stores data of EU citizens. If a US business offers products, services, or even tracks the online behavior of people in the EU, GDPR rules apply.3. What are the 4 main rules of GDPR?
GDPR is built on four key principles: lawfulness, fairness & transparency (being clear about data use); purpose limitation (collecting data only for specific reasons); data minimization (using only what’s necessary); and integrity & security (protecting data from loss or misuse).4. What happens if a company is not GDPR compliant?
Non-compliance isn’t just risky, it’s costly. Regulators can issue fines up to €20 million or 4% of the company’s annual global turnover, whichever is higher. Beyond fines, businesses risk reputational damage and losing customer trust.5. How does GDPR impact cybersecurity?
GDPR makes strong cybersecurity practices a must. Organizations need to implement safeguards like encryption, multi-factor authentication (MFA), and continuous monitoring. Plus, they must report data breaches within 72 hours, ensuring accountability and faster response to threats.