
What Is HIPAA Compliance? Definition & Key Requirements


What Is HIPAA Compliance? Definition & Key Requirements
Compliance with HIPAA refers to the compulsory adherence to the Health Insurance Portability and Accountability Act of 1996 and its Privacy, Security, and Breach Notification Rules, which dictate how protected health information (PHI) is handled in the United States. PHI is any individually identifiable health information, in any form, that is held or transmitted by a covered entity or business associate that pertains to health-care related condition(s), provision, and/or payment for health care.
Organizations that deal with protected health information (PHI) are subject to the U.S. HIPAA regulations. Organizations are required to implement and maintain safeguards, which can be categorized as physical safeguards (access controls at the facility), technical safeguards (secured transmission of data), and administrative safeguards (policies, workforce training, and audits) to ensure the protection of protected health information (PHI) against unauthorized access, use, or disclosure.
The Act set national standards to ensure the protection of patient privacy and ensure access to secure electronic health information while enabling the proper sharing of health-care information for treatment, payment, and health-care operations. For the healthcare organizations, HIPAA compliance requires a formal plan and implementation of administrative, physical, and technical safeguards to protect the confidentiality, integrity, and availability of protected health information (PHI).
Key takeaways:
- HIPAA compliance ensures patient data protection (PHI) through standardized safeguards
- Applies to covered entities and business associates handling any form of health information
- Requires administrative, physical, and technical safeguards with documented implementation
- Non-compliance can lead to significant civil penalties and criminal charges
Who Must Be HIPAA Compliant?
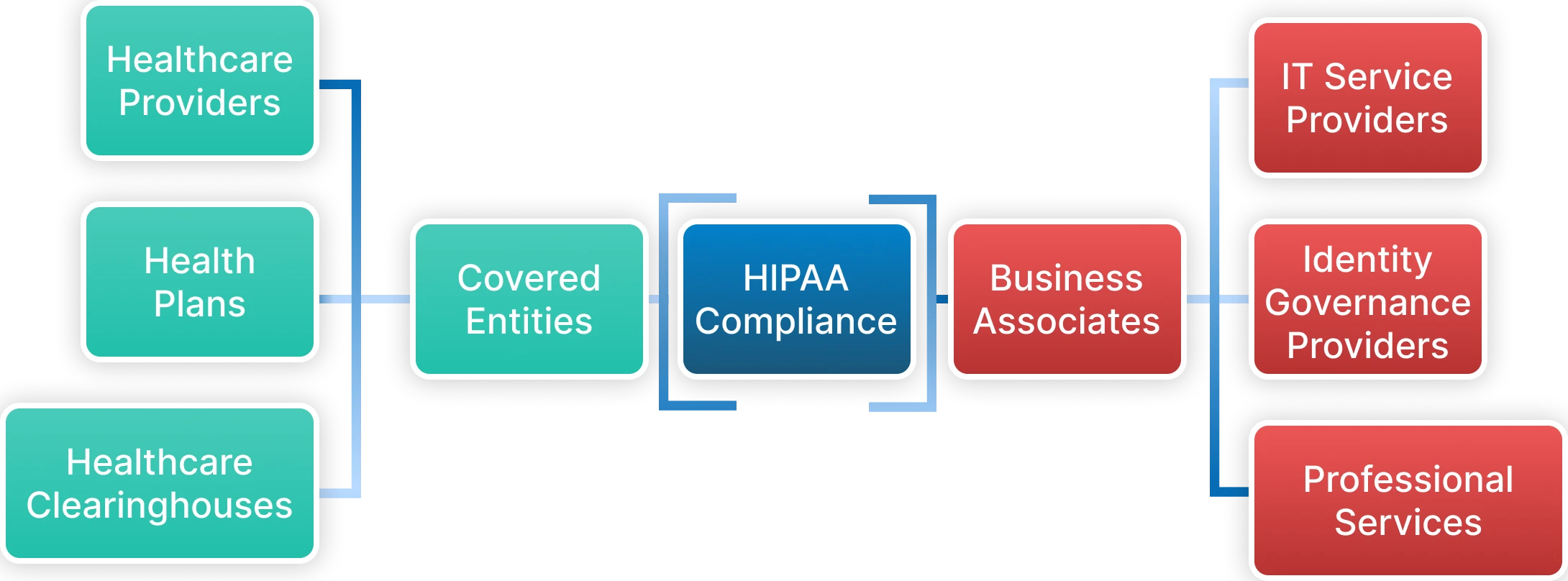
The reach of HIPAA goes beyond just health care providers. It broadly applies to any organization that creates, receives, maintains, or transmits PHI in any form. HIPAA categorizes organizations within its scope into two primary classifications with separate but overlapping responsibilities—both are directly liable for violations of HIPAA.
- Covered Entities:
A covered entity is any organization that collects, creates, or transmits PHI electronically in connection with standard healthcare transactions. Covered entities are comprised of healthcare organizations that fall into the categories of healthcare provider, healthcare clearinghouse, or health insurance provider. Covered entities have the responsibility of protecting PHI. Covered entities must develop comprehensive compliance programs that will govern all aspects of handling patients' information during each point of contact from collection to disposal of PHI. - Business Associates:
A business associate is any organization that comes into contact with PHI while performing work that has been contracted on behalf of a covered entity. The definition of a business associate is far-reaching due to the number of service providers that have the potential to come in contact with, handle, transmit, or process PHI. Examples include billing companies, practice management services, third-party consulting firms, EHR companies, managed service providers (MSPs), IT providers, document faxing companies, shredding companies, physical storage companies, cloud storage solutions, email hosting services, attorneys, accountants, and numerous service providers that assist healthcare operations.Modern healthcare delivery involves complex ecosystems where patient data flows through multiple systems, cloud platforms, and third-party services. Each touchpoint requires sophisticated identity governance and access management capabilities to ensure comprehensive PHI protection.
1. Covered Entities
Covered entities are organizations that directly engage in healthcare activities and electronically transmit health information for HIPAA-covered transactions.
These entities have primary responsibility for PHI protection and must implement comprehensive compliance programs. Covered entities fall into three main categories:
Healthcare Providers:
- Hospitals, physician practices, dentists, pharmacies, nursing homes
- Mental health professionals, physical therapists, chiropractors
- Any provider who submits electronic claims or conducts eligibility inquiries
- Organizations performing standard HIPAA transactions electronically
Health Plans:
- Insurance companies, HMOs, Medicare, Medicaid programs
- Employer-sponsored health plans and government health programs
- Organizations processing PHI for coverage determinations
- Entities handling claims processing and quality assurance activities
Healthcare Clearinghouses:
- Organizations processing health information between healthcare providers and health plans
- Entities converting non-standard data formats into standard electronic formats
- Intermediaries handling HIPAA transactions and data transformation
- Third-party processors facilitating healthcare payment systems
2. Business Associates
Business associates perform activities involving PHI use or disclosure on behalf of covered entities. The 2013 HIPAA Omnibus Rule made business associates directly liable for HIPAA compliance, eliminating previous indirect liability models.
IT Service Providers represent the largest category, including cloud storage providers, software vendors, system integrators, and identity governance platform providers like Tech Prescient. These organizations often have extensive access to PHI through their technology services, requiring comprehensive security controls and compliance programs.
Identity governance providers like Identity Confluence must implement technical safeguards that protect PHI during user authentication, authorization, and access management processes, including encrypting PHI in transit and at rest, maintaining detailed audit logs, and implementing role-based access controls.
Professional Services include legal firms, accounting services, consultants, and other providers who may access PHI during their work and must implement appropriate safeguards and sign Business Associate Agreements (BAAs).
What is Protected Health Information (PHI)?
Protected Health Information (PHI) is any individually identifiable health information that relates to healthcare provision, payment, or operations and is created, received, stored, or transmitted by covered entities and business associates. PHI represents a specific subset of personally identifiable information (PII) that gains special protection under HIPAA when handled by healthcare organizations and their partners.
PHI encompasses a broad range of data elements that can identify an individual when associated with healthcare services. Common data fields that constitute PHI when processed by covered entities or business associates include:
Personal Identifiers:
- Names, addresses, and contact information
- Social Security numbers and government-issued ID numbers
- Date of birth and demographic information
- Fingerprints and facial recognition data
Healthcare-Specific Information:
- Medical record numbers and patient identifiers
- Health insurance information and policy details
- Account numbers and billing information
- Treatment records and clinical documentation
Digital Identifiers:
- IP addresses and device identifiers
- Online activity logs related to healthcare
- Electronic health record access logs
- Digital communication records
Important Consideration: PHI exists in multiple formats including written documents, oral communications, and electronic data. All forms receive equal protection under HIPAA regardless of the medium used to store or transmit the information.
Practical Example: Consider a patient named Sarah who schedules her first appointment with a cardiology practice. When Sarah arrives, the office staff records her name and address, collects her health insurance information, and verbally requests her medical history from a previous provider. All of this written and oral information constitutes PHI and must be protected according to HIPAA standards.
The following week, Sarah participates in a telehealth consultation with the same cardiologist. Her online activities during this virtual appointment, including login credentials, session data, and any digital communications, also qualify as PHI because they contain identifiable information related to her healthcare services. This demonstrates how PHI protection extends across all healthcare delivery methods, whether traditional in-person visits or modern digital health platforms.
The 5 HIPAA Rules Explained
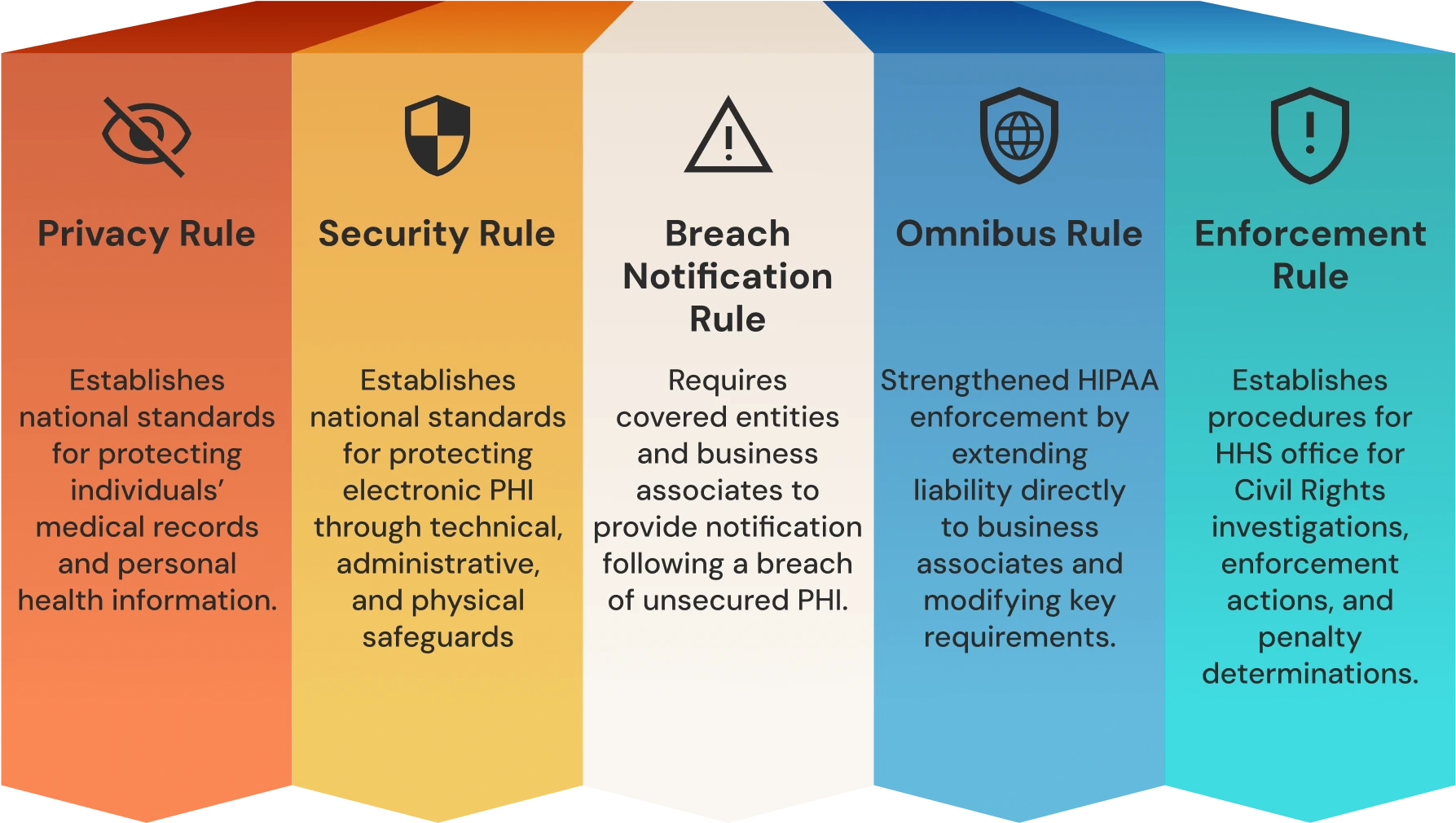
HIPAA consists of five interconnected rules that establish comprehensive requirements for protecting patient health information. Each rule addresses specific aspects of healthcare data protection, from individual privacy rights to technical security requirements and enforcement mechanisms. These rules work together to create a framework that protects patient privacy while enabling appropriate healthcare information sharing.
1. Privacy Rule
The Privacy Rule establishes national standards for protecting individuals' medical records and personal health information. PHI under this rule includes any information in a medical record that can be used to identify an individual and relates to healthcare services, including obvious identifiers like names and Social Security numbers, as well as dates and geographic data.
The Privacy Rule sets comprehensive national standards for patients' rights to PHI and applies specifically to covered entities, not business associates. Key standards established by the Privacy Rule include:
- Patients' rights to access their own PHI and request copies
- Healthcare providers' rights to deny access under specific circumstances
- Rights to request amendments to medical records
- Rights to receive accounting of disclosures of their PHI
Disclosure and Notice Requirements:
- Contents and requirements for Use and Disclosure release forms
- Notices of Privacy Practices that must be provided to patients
- Standards for obtaining patient authorization for PHI use
- Requirements for minimum necessary disclosure practices
The rule requires covered entities to implement administrative, physical, and technical safeguards to protect PHI confidentiality. Key components include appointing a privacy officer, conducting workforce training, and establishing policies for PHI access and disclosure.
From an identity governance perspective, the Privacy Rule's minimum necessary standard is particularly important. This standard requires covered entities to limit PHI access, use, and disclosure to the minimum necessary to accomplish the intended purpose. Identity governance platforms must enforce role-based access controls that automatically limit users to only the PHI needed for their specific job functions.
2. Security Rule
The Security Rule establishes national standards for protecting electronic PHI (ePHI) through technical, administrative, and physical safeguards. Unlike the Privacy Rule, the Security Rule specifically addresses electronic health information, requiring covered entities and business associates to implement specific security measures.
Administrative Safeguards include appointing a security officer, conducting workforce training, implementing access management procedures, and establishing incident response protocols. Physical Safeguards protect systems, equipment, and facilities housing ePHI from unauthorized access. Technical Safeguards include unique user identification, automatic logoff, encryption capabilities, and audit controls.
Identity governance platforms like Identity Confluence address multiple Security Rule requirements by providing centralized user authentication, role-based access controls, automated audit logging, and integration capabilities that ensure consistent security controls across healthcare applications.
3. Breach Notification Rule
The Breach Notification Rule requires covered entities and business associates to provide notification following a breach of unsecured PHI. A breach is defined as unauthorized acquisition, access, use, or disclosure of PHI that compromises the security or privacy of the information.
Organizations must conduct risk assessments to determine whether incidents constitute reportable breaches. Notification requirements include notifying affected individuals within 60 days, the Department of Health and Human Services within 60 days for breaches affecting fewer than 500 individuals, and immediately for larger breaches. Media notification is required for breaches affecting 500 or more individuals.
4. Omnibus Rule
The 2013 Omnibus Rule significantly strengthened HIPAA enforcement by extending liability directly to business associates and modifying several key requirements. Business associates now face direct responsibility for implementing HIPAA compliance programs, conducting risk assessments, implementing safeguards, and providing breach notifications.
The rule also strengthened patient rights, prohibited PHI sale without individual authorization, and modified breach notification requirements by eliminating the harm standard and replacing it with a risk assessment approach.
5. Enforcement Rule
The Enforcement Rule establishes procedures for HHS Office for Civil Rights (OCR) investigations, enforcement actions, and penalty determinations. This rule provides the regulatory framework for HIPAA compliance oversight, including complaint processing, audit procedures, and corrective action requirements.
Penalty Structure includes four tiers based on culpability levels, with penalties ranging from $100 to $50,000 per violation and annual maximums reaching $1.5 million per violation category. OCR enforcement data shows that investigators have resolved over 31,000 cases through corrective actions and technical assistance.
HIPAA Compliance Checklist (Step-by-Step)
A HIPAA compliance checklist is a systematic framework for implementing and maintaining adherence to HIPAA requirements across all organizational processes involving PHI. Effective checklists address each HIPAA rule's specific requirements while creating integrated processes that ensure ongoing compliance rather than one-time implementation.
1. Conduct a Risk Assessment
Risk assessment is the foundation of HIPAA compliance, requiring systematic evaluation of how PHI is created, stored, transmitted, and disposed of throughout your organization. HIPAA requires covered entities to conduct accurate and thorough assessments of potential risks and vulnerabilities to the confidentiality, integrity, and availability of ePHI.
The risk assessment process begins with PHI inventory, identifying all locations where health information is created, received, maintained, or transmitted. This includes electronic systems, paper records, backup media, mobile devices, and cloud storage locations. Organizations must document data flows showing how PHI moves between systems, departments, and external entities.
Identity governance platforms like Identity Confluence streamline risk assessment by providing automated discovery of user access patterns, identifying privileged accounts with extensive PHI access, and mapping data flows across interconnected healthcare systems.
2. Assign Responsibility
Designate key HIPAA compliance leadership roles to ensure clear accountability and oversight. Organizations must appoint a HIPAA Compliance Officer or separate HIPAA Privacy Officer and HIPAA Security Officer depending on organizational size and complexity. These designated officials bear responsibility for developing, implementing, and maintaining HIPAA compliance programs, conducting workforce training, managing incident response, and serving as primary contacts for regulatory inquiries.
3. Develop Policies and Procedures
HIPAA compliance requires written policies and procedures that address each applicable requirement of the Privacy, Security, and Breach Notification Rules. These policies must be tailored to the organization's specific operations, technology environment, and business processes rather than relying on generic templates.
Privacy Rule policies must address PHI use and disclosure limitations, individual rights procedures, minimum necessary standards, workforce training requirements, and business associate management. Security Rule policies require documentation of administrative, physical, and technical safeguards appropriate to the organization's size and complexity.
4. Implement Safeguards (Technical, Physical, Administrative)
HIPAA safeguards represent the operational controls that protect PHI from unauthorized access, use, and disclosure. These safeguards must be implemented systematically across all organizational processes and technology systems that handle PHI.
Administrative Safeguards establish the management processes and assigned responsibilities for protecting ePHI, including appointing a security officer and implementing access management procedures. Physical Safeguards protect the electronic systems, equipment, and facilities that house ePHI from unauthorized physical access. Technical Safeguards are the technology controls that protect ePHI and control access to computer systems containing health information.
Modern identity governance solutions like Identity Confluence automate many technical safeguards through centralized user authentication, role-based access controls that enforce minimum necessary access, and comprehensive audit logging that tracks all PHI access activities across multiple systems.
5. Train Employees
HIPAA training is mandatory for all workforce members who have access to PHI or work in areas where PHI might be encountered. Training must be comprehensive, role-specific, and ongoing, addressing both general HIPAA principles and specific organizational policies and procedures.
Research shows that human error contributes to 95% of data breaches, making workforce training the most critical component of any HIPAA compliance program.
Role-specific training must address each employee's actual job responsibilities and PHI access requirements. Training content must cover HIPAA basics including the definition of PHI, permitted uses and disclosures, individual rights, and organizational policies and procedures.
6. Sign BAAs with Vendors
Business Associate Agreements (BAAs) are legally required contracts between covered entities and business associates that establish how PHI will be protected when shared with third-party organizations. The 2013 Omnibus Rule significantly strengthened BAA requirements and made business associates directly liable for HIPAA compliance.
BAA requirements must include specific language required by HIPAA regulations, clearly defining permitted and required uses and disclosures of PHI, establishing safeguard requirements that business associates must implement, and specifying procedures for reporting breaches and other security incidents.
7. Monitor, Audit, and Review Compliance
Ongoing compliance monitoring is essential for maintaining HIPAA compliance and demonstrating good faith efforts to protect PHI. Monitoring activities must be systematic, documented, and integrated into regular organizational operations.
Continuous monitoring involves implementing automated controls and regular review procedures that provide ongoing visibility into compliance status. This includes monitoring access logs for unauthorized PHI access attempts, reviewing user access rights to ensure they align with job responsibilities, and tracking policy compliance through regular audits.
Identity governance solutions provide automated compliance monitoring capabilities that simplify ongoing oversight requirements. Identity Confluence can generate compliance reports showing user access patterns, identify users with excessive privileges, track access review completion, and provide audit trails that demonstrate appropriate PHI access controls.
HIPAA Compliance Training & Certification
HIPAA compliance training represents a mandatory risk management strategy that transforms regulatory requirements into practical workforce behaviors that protect patient privacy and organizational reputation. Training extends beyond simple awareness to build competency in applying HIPAA principles to daily work activities, recognizing potential violations, and responding appropriately to privacy and security incidents.
1. Why Employee Training is Essential
Employee training creates measurable risk reduction by establishing consistent privacy and security behaviors across diverse organizational functions. Well-trained employees can identify phishing attempts targeting patient data, recognize when colleague behavior may violate privacy policies, and understand the appropriate procedures for handling patient requests regarding their health information.
Legal and regulatory requirements mandate that covered entities and business associates provide HIPAA training to all workforce members with PHI access. The Security Rule specifically requires that organizations conduct training in security awareness and provide appropriate access to electronic PHI based on job responsibilities.
2. Online vs In-Person HIPAA Compliance Training
Training delivery methods must balance cost-effectiveness, consistency, and engagement while accommodating diverse workforce schedules and learning preferences. Most healthcare organizations implement hybrid approaches that combine online modules for foundational knowledge with in-person sessions for role-specific applications and interactive discussions.
Online training advantages include consistency of content delivery, automated tracking and reporting capabilities, cost-effectiveness for large organizations, and flexibility that accommodates varying work schedules. In-person training benefits include interactive discussions that address organization-specific policies and procedures, real-time clarification of complex requirements, and scenario-based training.
3. Certification Process for Compliance Officers
Healthcare compliance officers benefit from professional certification programs that provide comprehensive regulatory knowledge and practical implementation skills. Organizations like the Health Care Compliance Association (HCCA) offer the Certified in Healthcare Compliance (CHC) credential, and the American Health Information Management Association (AHIMA) provides specialized privacy and security certifications.
Common HIPAA Violations & Penalties
HIPAA violations represent serious regulatory infractions that can result in significant financial penalties, criminal prosecution, and reputational damage that affects organizational competitiveness and patient trust. Understanding common violation patterns helps healthcare organizations focus prevention efforts on high-risk areas while implementing appropriate controls.
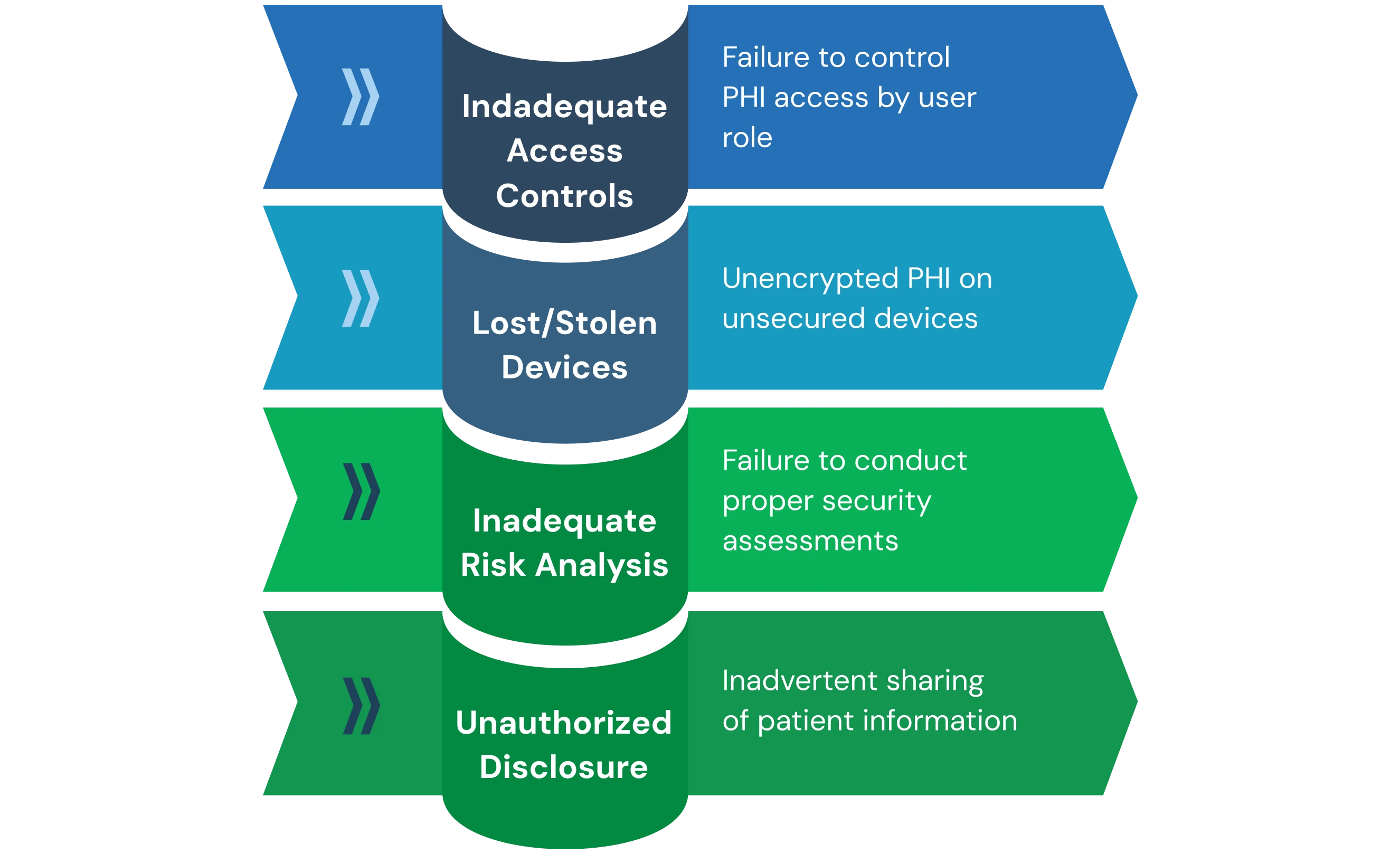
1. Examples of Common Violations:
- Unauthorized PHI Disclosures represent the most frequent category of HIPAA violations, encompassing both intentional and inadvertent sharing of patient information without proper authorization. These violations include discussing patient cases in public areas where conversations can be overheard, sending PHI to incorrect email recipients, posting patient information on social media, and accessing patient records without legitimate business justification.
- Inadequate Risk Analysis has become a primary enforcement focus through OCR's Risk Analysis Initiative, which targets organizations that fail to conduct proper security risk assessments. This enforcement demonstrates the importance of comprehensive risk analysis as the foundation of HIPAA compliance.
- Lost or Stolen Devices containing unencrypted PHI continue to generate significant violations despite years of regulatory guidance regarding mobile device security. Healthcare workers increasingly use laptops, tablets, and smartphones to access patient information, creating risks when devices are lost, stolen, or inadequately secured.
- Inadequate Access Controls violations occur when organizations fail to implement appropriate technical safeguards that control PHI access based on user roles and responsibilities. These violations include sharing user credentials, failing to implement unique user identification, inadequate password policies, and systems that allow users to access PHI beyond their job requirements.
2. Penalty Structure:
Penalty Structure:
Civil penalties are assessed using a four-tier structure based on culpability levels. The Office for Civil Rights (OCR) categorizes HIPAA violations based on severity and wilful neglect:
- Tier 1: Unaware of Violation The entity is unaware of its noncompliance with HIPAA regulations, and penalties range from $100 to $50,000 per violation, with the maximum penalty at $25,000 annually.
- Tier 2: Reasonable Cause The entity did not act with wilful neglect. Penalties for Tier 2 violations range from $1,000 to $50,000 per violation, with a maximum penalty of $100,000 annually.
- Tier 3: Wilful Neglect That Is Corrected Within 30 Days of Discovery. The penalties can range from $10,000 to $50,000 per violation and can reach up to a maximum of $250,000 annually.
- Tier 4: Wilful Neglect That Is Not Corrected Within 30 Days. As the most severe tier, penalties for Tier 4 violations can reach up to $1.5 million per violation category annually.
Criminal Penalties may be pursued by the Department of Justice for knowing violations that involve wrongful conduct. Criminal penalties can include fines up to $250,000 and imprisonment up to 10 years for violations involving intent to sell, transfer, or use PHI for commercial advantage, personal gain, or malicious harm.
HIPAA Compliance Software & Services
HIPAA compliance software encompasses technology solutions that automate, monitor, and manage the complex requirements of healthcare privacy and security regulations. These solutions range from comprehensive compliance management platforms to specialized tools that address specific HIPAA requirements like risk assessment, audit logging, or encryption.
1. Benefits of Automation
Automated compliance management reduces human error while providing real-time visibility into compliance status across complex healthcare environments. Automation enables healthcare organizations to scale compliance programs efficiently without proportional increases in compliance staff, while ensuring consistent policy enforcement across multiple locations, departments, and systems.
- Risk Assessment Automation streamlines the complex process of identifying and evaluating privacy and security risks throughout healthcare organizations. Automated tools can scan network infrastructure to identify systems containing PHI, evaluate security controls against HIPAA requirements, and generate risk reports that prioritize remediation efforts.
- Tracking and Reporting capabilities provide comprehensive documentation of compliance activities that support regulatory audits and internal oversight. Automated systems maintain detailed audit trails of user access, policy compliance, training completion, and incident response activities that demonstrate ongoing compliance efforts.
2. Identity Governance for HIPAA Compliance
Identity governance represents a specialized category of compliance software that addresses core HIPAA requirements through comprehensive user access management and automated compliance controls.
Tech Prescient's Identity Confluence provides centralized visibility into user access across healthcare systems while enforcing policy-driven access controls that support HIPAA's minimum necessary standard.
- Centralized Access Management enables healthcare organizations to implement consistent access controls across diverse technology environments, including electronic health records, financial systems, and administrative applications. Centralized management ensures that access policies are enforced consistently, regardless of the underlying technology platform or vendor.
- Identity governance platforms integrate with HR systems to automate user provisioning and deprovisioning based on employment status changes, ensuring that former employees lose access immediately upon termination. This automation addresses a common HIPAA violation where terminated employees retain system access due to inadequate account management procedures.
- Role-Based Access Controls support HIPAA's minimum necessary standard by automatically limiting user access to only the PHI required for specific job functions. Identity governance platforms maintain role definitions that specify appropriate access levels for different job functions, automatically adjusting user access when job responsibilities change.
3. Cloud Platform Compliance:
AWS HIPAA Compliance is supported through Amazon Web Services' comprehensive HIPAA-eligible services program that includes infrastructure-level security controls, encryption services, and audit logging capabilities. AWS offers a Business Associate Agreement for customers who want to use AWS services to store, process, or transmit PHI.
Azure HIPAA Compliance is delivered through Microsoft Azure's comprehensive compliance program that includes HIPAA/HITECH certifications, specialized healthcare cloud services, and integrated security features. Azure provides Business Associate Agreements and specialized compliance documentation.
4. Choosing Consultants vs Software Solutions
Healthcare organizations must evaluate whether to engage compliance consultants, implement software solutions, or combine both approaches based on their specific needs, resources, and risk profiles.
Compliance consultants bring specialized expertise and industry experience that can accelerate compliance program development while providing objective perspectives on organizational practices. Software solutions provide automation, consistency, and ongoing monitoring capabilities at predictable costs that scale efficiently with organizational growth.
Combined approaches often provide optimal compliance coverage by leveraging consultant expertise for initial program development and software platforms for ongoing compliance management and automation.
Final Thoughts
HIPAA compliance represents an ongoing operational requirement, not a one-time implementation project. Healthcare organizations must maintain continuous vigilance through regular risk assessments, policy updates, and training programs that adapt to evolving threats and technologies.
Modern healthcare operates in complex technology environments where patient data flows through multiple systems, cloud platforms, and business partner networks. This complexity requires sophisticated approaches extending beyond traditional processes to address electronic health records, telehealth platforms, and AI systems processing patient data.
Technology integration plays a critical role in sustainable compliance programs. Identity governance platforms like:
Tech Prescient's Identity Confluence enables healthcare organizations to automate core HIPAA requirements while providing visibility and user access controls needed for complex technology environments.
Organizations investing in comprehensive compliance programs not only avoid penalties but also build competitive advantages through enhanced security postures and patient trust.
Transform Your HIPAA Compliance with Identity Confluence
Ready to automate your HIPAA compliance and strengthen your healthcare identity governance? Tech Prescient's Identity Confluence provides comprehensive identity and access management specifically designed for healthcare organizations. Our platform automates user provisioning, enforces role-based access controls, and maintains detailed audit trails that satisfy HIPAA requirements while reducing administrative burden.
Frequently Asked Questions (FAQs)
1. What is HIPAA compliance in simple terms?
HIPAA compliance means following U.S. laws that protect patient health information (PHI). It ensures healthcare data stays private, secure, and only shared when authorized through specific administrative, physical, and technical safeguards.2. What are the three main rules of HIPAA?
The three main HIPAA rules are:- Privacy Rule: Protects patient health records and gives patients control
- Security Rule: Secures electronic health data with safeguards
- Breach Notification Rule: Requires reporting when PHI is leaked or stolen
3. Who is required to be HIPAA compliant?
Covered entities (healthcare providers, health plans, clearinghouses) and business associates (IT vendors, billing services, cloud providers, consultants) must follow HIPAA. Business associates face direct liability since the 2013 Omnibus Rule.4. What happens if you are not HIPAA compliant?
Non-compliance leads to civil fines from $100 to $50,000 per violation, with annual maximums reaching $1.5 million per category. Criminal penalties can include fines up to $250,000 and imprisonment up to 10 years, depending on intent and severity.5. How do I create a HIPAA compliance checklist?
- Risk assessment of PHI handling processes
- Written policies and procedures for all HIPAA rules
- Technical, physical, and administrative safeguards
- Employee training programs with documentation
- Signed Business Associate Agreements (BAAs) with vendors
- Ongoing monitoring, auditing, and compliance review procedures