
What is Identity and Access Management (IAM)?


Identity and access management (IAM) is the backbone of cybersecurity. IAM is fundamentally a framework of processes, policies, and technologies that helps organizations manage digital identities and resource access. IAM becomes crucial for organizations to understand who has access to systems and sensitive information. It restricts access to only verified individuals, whether those individuals are employees, contractors, or partner organizations.
IAM solutions leverage methods for authentication such as single sign-on (SSO), multi-factor authentication (MFA), and privileged access management (PAM) to authenticate individuals, maintain access policies, and restrict and revoke access. Beyond authentication, IAM provides identity life cycle functions (provisioning, de-provisioning, and establishing authenticator reliability) to make it easier for IT administrators to know who has access to what, and why. In fact, a 2025 security study found that 91% of organizations now consider identity security a top-five priority, underscoring just how essential IAM has become to protecting sensitive data, meeting compliance requirements, and enabling a smooth user experience with controlled risk.
As organizations undertake cloud adoption, remote work, and digital transformation, the traditional security perimeter no longer applies, and with it the concept of perimeter-based controls. In this context, identity is the new security perimeter. When we talk about Identity and Access Management, it supports the protection of sensitive data, compliance regulations, and a positive user experience while managing security risk.
This blog provides an overview of IAM’s essential components, the benefits and challenges of IAM, and IAM trends in the future to illustrate why IAM is an essential requirement for every organization, rather than just an option.
Key Takeaways
- IAM ensures that only authorized individuals, devices, and applications have access to the necessary resources at the correct time.
- The core functions of IAM include identity creation, authentication, authorization, and ongoing access monitoring.
- IAM enhances security by minimizing unauthorized access and mitigating insider or external threat scenarios.
- Strong IAM practices allow organizations to demonstrate compliance with industry or regulatory standards.
- IAM increases productivity and user experience by simplifying the login process and automating access management.
Identity and Access Management Definition
Identity and Access Management (IAM) is a cybersecurity framework of policy, process, and technology that allows the right person and/or entity to access the right resources at the right time. It includes both identity management, that is, creating, storing, and verifying digital identities, and access management, which includes identifying, defining, and enforcing access to specific systems, applications, and data.
IAM solutions allow organizations to manage employee access centrally, avoiding user logins to each application one at a time. This makes management easy and strengthens security, which applies to all access to the applications. For example, single sign-on (SSO) allows a user to log on once, and the user can securely access multiple applications, whereas layered controls, such as MFA, add a layer of security for sensitive systems such as financial or medical data.
Modern IAM goes beyond human users; IAM is managing a broader set of identities: applications, software agents, IoT devices, and robotics; ensuring every identity, human, and machine, is authenticated and authorized.
Core Components of IAM
At its core, Identity and Access Management (IAM) collates several building blocks to understand, protect, and control digital identities, allowing for access control. Each of these components has distinct purposes in allowing only the correct users/entities to access the correct systems and data.
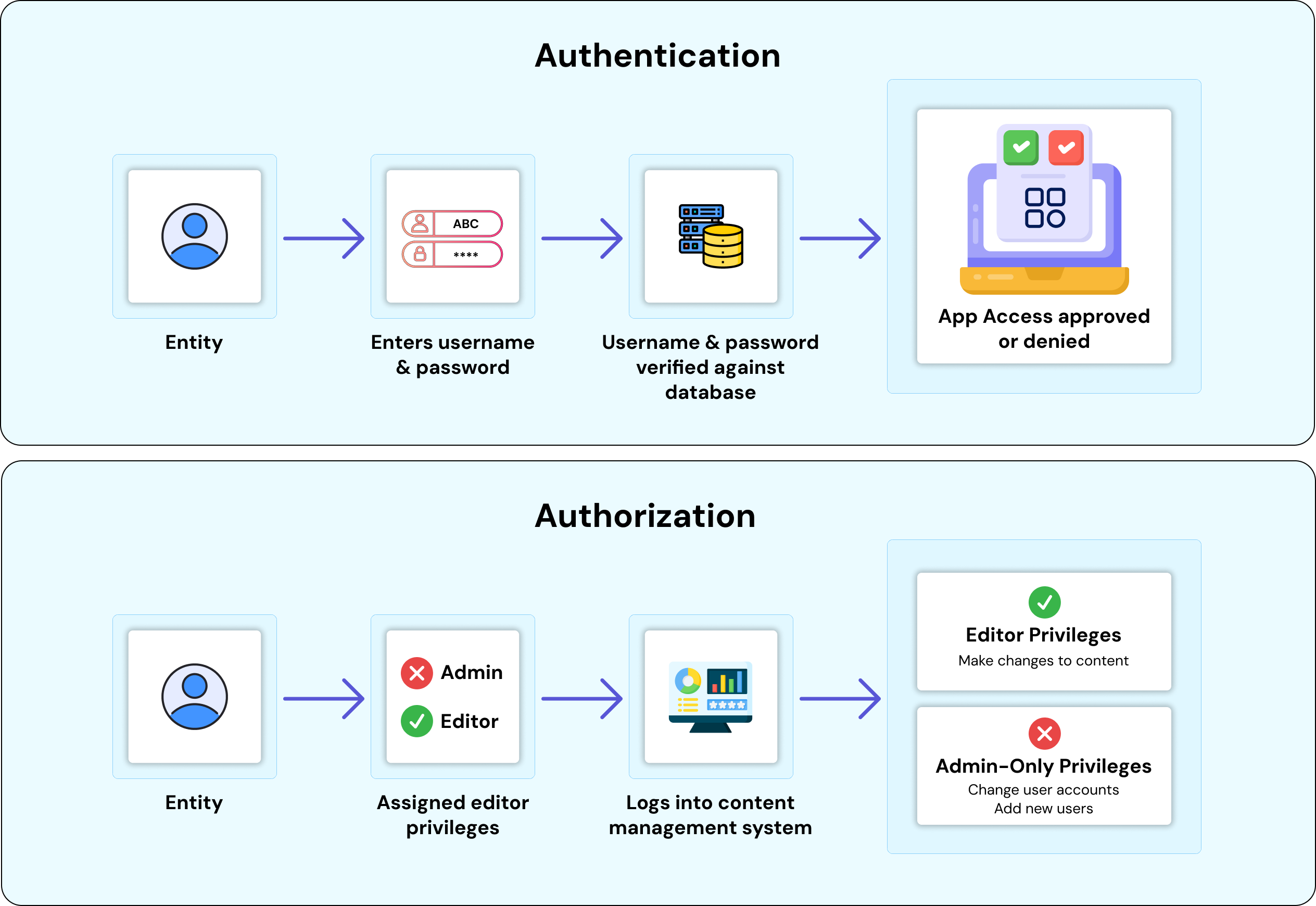
1. Digital Identities
A digital identity is a set of information about people, organizations, or devices that are resident within a digital system. Digital identities are built from attributes that are unique combinations, such as usernames, email addresses and corporate email, job titles, department or location, or device IDs. For example, a digital identity could represent an employee’s corporate email, assigned role, and which apps the employee has access to, while a device’s identity may be associated with an IP address and a security certificate. IAM solutions manage these digital identities so that organizations can track and control all entities, human or otherwise, who interact with their systems.
2. Authentication
Authentication is the act of verifying that a digital identity is real and actually belongs to the person or system presenting the identity. Authentication methods can be as simple as providing a password or as advanced as using multi-factor authentication (MFA) with a combination of passwords, biometrics (e.g., fingerprint recognition, facial recognition), or adaptive authentication, which is becoming more common in IAM. Adaptive authentication uses risk factors (e.g., where the user logs in from or what device the user logs in from) to determine whether or not to grant access. This is a useful and scalable way to ensure that if one of your authentication factors is compromised, the attacker cannot easily use other factors and gain access.
3. Authorization
After authentication is established, authorization determines the meaning of the identity; what the identity is allowed to do. Authorization determines access rights to applications, systems, or data, typically with ABAC (Attribute-Based Access Control) or RBAC (Role-Based Access Control) models, where access rights are determined by context, with ABAC, or by role, with RBAC, and the context may include: time of day, location, and project status. A finance manager may be authorized to view payroll systems, while a contractor may have temporary access to a project management tool. This fine-grained authorization helps drive the principle of least privilege.
4. Administration
Administration manages the identity lifecycle from provisioning (creation of accounts and assignment of roles) through to deprovisioning (revoking access when no longer necessary). Automating management is important to reduce human error and to prevent security gaps, for instance, accounts that remain active after an individual leaves the organization. Administration includes the management of passwords, resets, escalations of privilege, and approval workflows, making it one of the most pivotal daily functions of IAM.
5. Auditing & Reporting
IAM systems also have auditing and reporting capabilities that give organizations true visibility into access activities (who accessed what, when, and how). These logs are necessary for compliance and meeting regulatory requirements such as GDPR, HIPAA, and SOX. But these logs can also be a good indicator of insider threats or unusual behavior. For instance, if a contractor in your organization suddenly attempts to download a large amount of data outside of business hours, the IAM platform can alert you. Continuous monitoring and reporting strengthen your security posture and significantly ease audit readiness for compliance teams.
Why is Identity and Access Management Important?
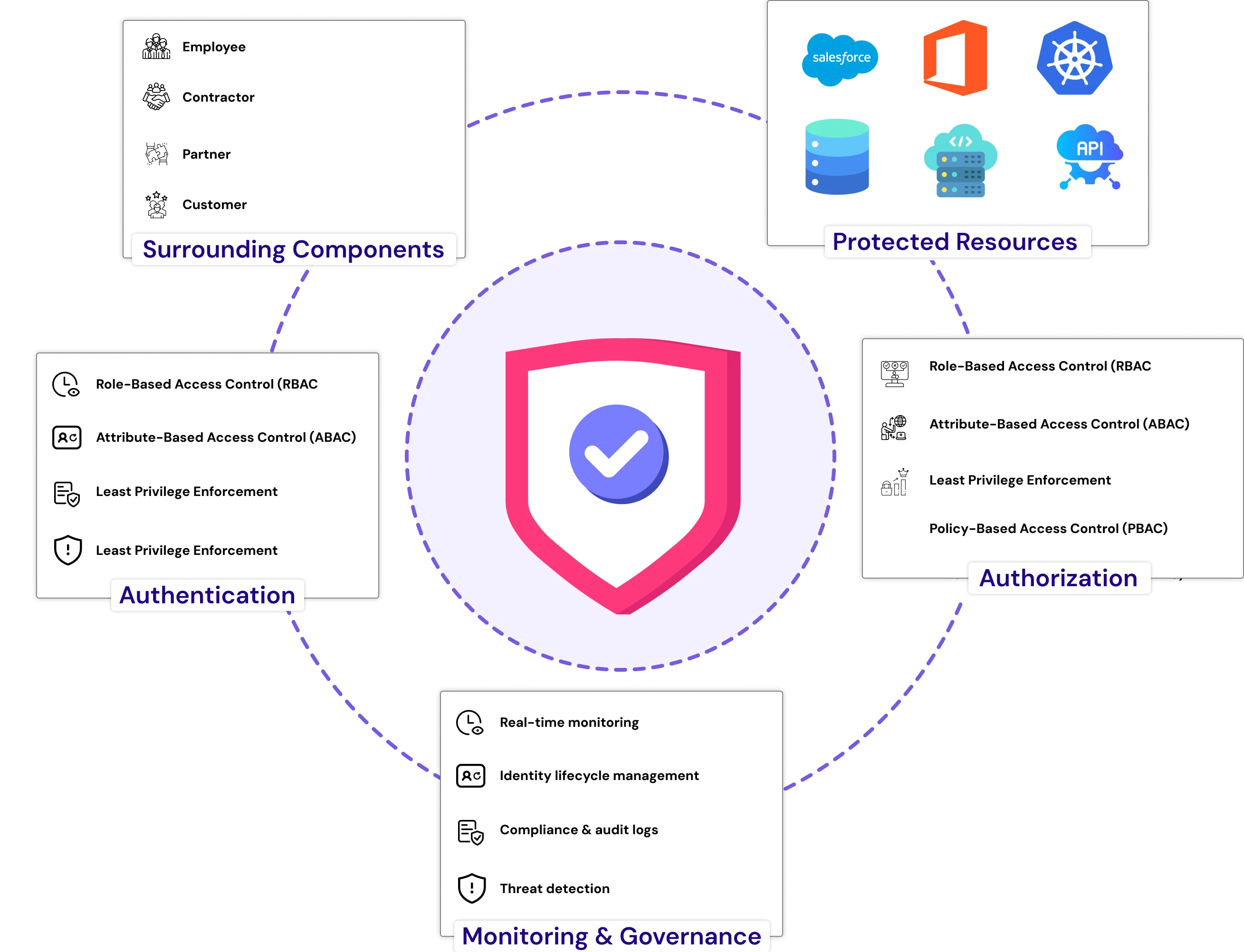
As organizations transition to more hybrid and cloud-focused environments, access control can also evolve, and the evolution of access control starts with Identity and Access Management (IAM). Cybersecurity developments today go well beyond static firewalls; now the threats are around the identities themselves. The evidence indicates that 59% of all cyber incidents can now be classified as identity-based attacks, increasing 156% since 2023.
IAM identifies the solutions to those issues by managing who or what can access your systems, especially as many applications, devices, and users are accessing the enterprise beyond its historical network perimeter. It continuously validates access using multi-factor access control (MFA), role- or attribute-based access control, and centralized user provisioning. This marries well with Zero Trust, as zero trust dictates that there is no safe request and that every access event must be validated, and users should be given as little access as possible (least privilege).
When it comes to managing insider risk, compliance, and usability, IAM is very effective. For example, when employees leave or change roles, IAM systems automatically adjust users' attributes to revoke access and remove lingering permissions - eliminating one option for internal attack. Similarly, when approval to access resources originates from new locations or devices, context-based IAM policies can ask for additional verification.
With the increase of cyber threats and complexity of IT infrastructure, Identity and access management has evolved from 'nice to have' to 'must have.' IAM is closing the gap between Zero Trust theory and Zero Trust practice with continuous validation and least privilege. IAM keeps risk at bay while enabling secure and scalable access to resources.
Benefits of Identity and Access Management
The primary benefits of identity access management (IAM) are security, compliance, and efficiency. IAM consolidates identity processes and provides accessibility to the right people with the least amount of risk while providing efficiencies for operations.
The following are the benefits:
1. Stronger Security
IAM reduces the risk of data breaches by enforcing least privilege access and requiring robust authentication methods like biometrics and MFA, combined with adaptive authentication. Adaptive authentication includes contextual data both for determining the legitimacy of a login attempt and providing additional verification for both the user and the company. And with the ability to monitor access from a centralized place to identify unusual patterns of access and respond accordingly, IAM allows organizations to identify threats to their online security quickly. As compromised credentials are still one of the leading causes of cyberattacks, IAM offers an important security layer.
2. Regulatory Compliance
Compliance with regulations is always a challenge for organizations, particularly in highly regulated industries such as healthcare, finance, and government. IAM solutions facilitate compliance by providing detailed audit logs, enforcing access policies, and creating automatic reports. This information can provide the necessary documentation for accountability during audits and reduce the risk of possibly costly complications from continued non-compliance.
3. Enhanced User Experience
Security and usability can work independently without being at odds. Using Single Sign-On (SSO) allows users to log in once and access multiple applications, limiting password fatigue. Self-service capabilities like Self-Service Password Reset (SSPR) also allow users to solve issues themselves without requiring time from IT, all while ensuring stringent security standards are still applied.
4. Enhanced Productivity
By automating IAM into onboarding and offboarding, employees have access to the applications they need from day one, and access is removed upon exit/termination. This ensures there are minimal delays going into these phases and helps to protect sensitive systems by not leaving them exposed via inaction.
5. Reduced Risk Exposure
Organizations face significant risks if users maintain unused accounts, privilege creep, and lose unused accounts to shadow IT. IAM takes care of this continuously by identifying and removing those risks through maintenance of access rights that align with changes in business roles. This not only reduces the opportunity for insider misuse it also decreases the chances that an attacker can exploit forgotten active credentials.
6. Supporting Zero Trust Security
IAM is an important contributor to Zero Trust security models because it enables least privilege and mandates continuous verification. Every access request is authenticated and authorized at the time of access, so there is no implicit trust of any user or device.
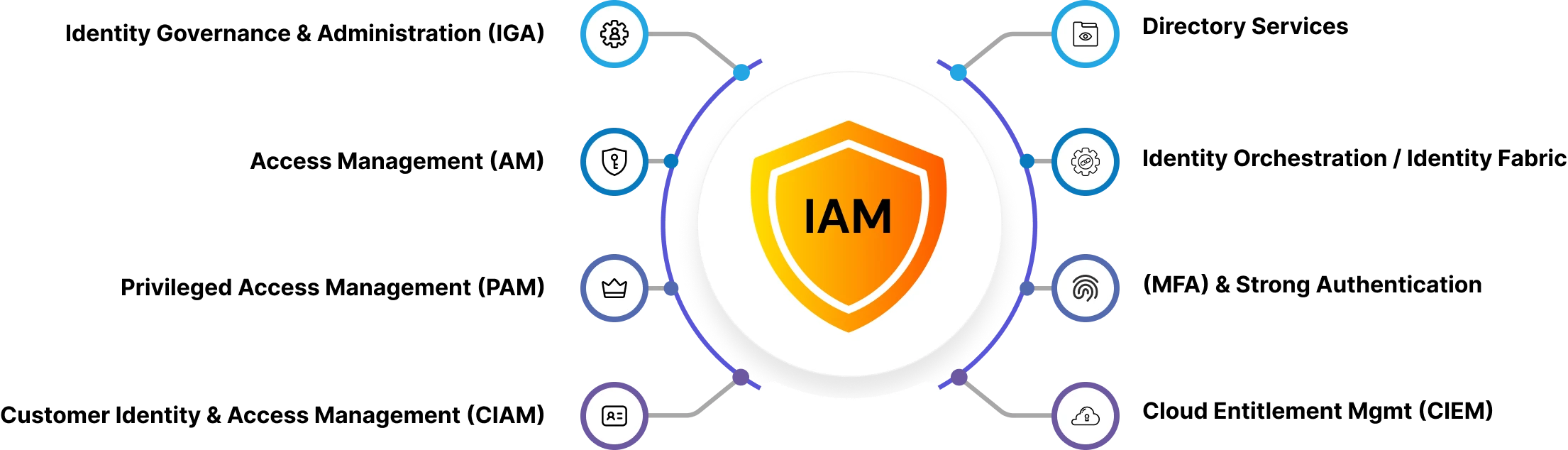
IAM Tools and Solutions
Modern organizations seldom build their own IAM frameworks from scratch. They instead rely on IAM platform vendors to assist them in centralizing IAM for identity management. Specialized IAM vendor platforms, such as Okta, Microsoft Entra ID, provide many different types of IAM solutions, enabling organizations to manage digital identities, enforce access policies, and integrate with thousands of applications.
📌Note: IAM is powerful, but on its own, it isn’t enough. To truly strengthen identity security, enterprises need Identity Governance and Administration (IGA) on top of IAM. That’s where Tech Prescient comes in, with Identity Confluence, we help organizations unify IAM and IGA, making access not just managed, but governed, compliant, and secure across hybrid and multi-cloud environments.
The IAM tools often have a variety of categories that can be organized in a way that aligns explicitly with a particular aspect of identity security and user access:
-
Single Sign-On (SSO) – SSO allows a user to authenticate once and access numerous applications without authenticating again. SSO reduces password fatigue and, most importantly, enhances security by reducing the potential number of login points (and therefore points of attack) from which attackers can attempt to log in to each account one at a time.
-
Multi-Factor Authentication (MFA) - MFA mandates users to authenticate their identity using two or more factors: something you know (password), something you have (token, mobile device), or something you are (fingerprint, face scan). The likelihood of a bad actor gaining access is substantially reduced, as they will require more than stolen credentials to log in. In many use cases, SSO (Single Sign-On) can also be used in conjunction with MFA, allowing users to log in once while still being subject to verification with multiple applications. Modern IAM systems are also using adaptive MFA, which looks at the context of the login attempt (where, with what device, network, and when) to determine whether more verification is needed. This allows for stronger security to be implemented without burdening the user unnecessarily.
-
Privileged Access Management (PAM) - PAM is a tool focused on control and monitoring of access to key systems and accounts with elevated access. PAM prevents misuse of admin accounts, whether intentional or unintentional, through session monitoring and recording, credential vaulting, privilege elevation & delegation, and just-in-time access to privileged entities.
-
Cloud IAM - With organizations moving towards hybrid and multi-cloud environments, Cloud IAM provides secure identity management across platforms such as AWS, Azure, and Google Cloud. The solutions extend centralized policies to cloud resources, which allows security organizations to maintain governance and access control beyond an organization's on-premises resources.
Together, these tools create a layered IAM ecosystem that balances security, compliance, and usability, while giving organizations the flexibility to scale with new applications and infrastructures.
IAM in Cybersecurity
The identity and access management (IAM) function is more than just an IT function; it is the modern perimeter of security, establishing security at the identity level. With increased enterprise adoption of cloud technologies and remote work realities, traditional perimeter firewalls have become less relevant. IAM plays a fundamental role in the modern security posture, verifying every identity before granting access to any resource.
IAM is a critical piece of security, considering modern cybersecurity requirements, including cloud environments, increased insider threats, hybrid consumption of organizations, and distributed business models, have completely eroded the static network perimeter. IAM is the “new perimeter”; the trust and authorization for each access transaction are tied to a trusted identity, not location or device.
Why Identity is the Perimeter, not the Network?
IAM systems adopt Zero Trust principles, such as “never trust, always verify” and least privileged access. Every user, regardless of the industry they are from, is required to verify their identity and authorized status, regardless of where they connect from or which device they are using.
IAM Use Cases:
- Finance: IAM enables only authorized analysts to access financial customer data through role-based controls and detailed logging, which allows organizations to comply with SOX requirements (and Certification Regulatory Compliance) and PCI-DSS requirements with reduced risk of fraud or insider misuse.
- Healthcare: IAM enables nurses, doctors, and third-party partners seamless access to Electronic Health Records (EHRs) as defined by their role and responsibility. IAM ensures compliance with privacy mandates, such as HIPAA, while protecting sensitive patient data from being unnecessarily exposed.
- SaaS companies: IAM consolidates identity management for dozens of cloud apps for organizations to access seamlessly and securely, whether that's through secure login methods (SSO) or adaptive authentication methods. IAM is a controlled way to balance organizational security practices with user and system convenience by limiting the chance of credential misuse in fast-growing SaaS organizations.
Identity and Access Management is shifting the guard and ensuring distributed environments no longer rely solely on outdated network-based security. IAM brings the guard to the identity validation level per user or system, applies the least amount of access, and continuously monitors for behavior. By adopting this identity validation stance, IAM supports security, productivity, and the practice of Zero Trust as cybersecurity techniques evolve and improve.
IAM Implementation and Best Practices
Strong IAM is more than just deploying tools; it involves creating processes that can assure long-term effectiveness, scalability, and resilience. The following are proven best practices that organizations should adhere to when putting IAM into action.
1. Clearly Define Policies and Roles
Without distinct policies, an IAM system suffers from redundancy and duplication, as well as "shadow access" granted to users. An organization should start out by linking business activities to various roles, such as the role of HR manager, sales associate, or contractor, and documenting the resources required in each role. This not only maintains easier access requests, but also makes access reviews and audits more lucid. A role-based approach simplifies provisioning, eliminating human error by automatically granting the appropriate access to a new user when they are added to the system.
2. Use the Principle of Least Privilege
IAM works best when you embrace the principle of least privilege (PoLP), that is, giving users only the least amount of permissions they absolutely need to do their jobs. Doing so reduces the potential blast radius of a compromise or an insider threat. For example, an employee in the financial department should have access to financial systems but not to HR databases or cloud infrastructure consoles. Zero Trust frameworks build upon PoLP by verifying identity continuously at the start and during access and limiting lateral movement. Least privilege isn’t just cutting back on access; it’s dynamically shaping access based on contextual factors like device, location, and risk signals.
3. Automate Provisioning and Deprovisioning
When you create or delete accounts manually, there is always room for error, and it takes time to do so. If you automate the provisioning and deprovisioning of accounts, you can ensure that employees, contractors, and partners have access on day zero and lose it immediately when they leave. This is even more important in hybrid workplaces with a lot of workforce churn. Platforms like Okta and Microsoft Entra ID provide automated workflows that link your HR system. That way, when HR takes action to offboard an employee, for example, IAM takes action to rescind that user's access immediately. This also reduces orphaned accounts, which are one of the leading vectors for unauthorized access.
4. Conduct Regular Access Reviews
IAM is not something you can just “set and forget.” Performing access reviews regularly helps make sure the user's entitlements remain valid as their roles change. Compliance frameworks like SOX, HIPAA, and GDPR dictate periodic access reviews, but they provide a strategic security benefit as well, helping identify over-privileged accounts that can be exploited. Some authorization and access management tools support access reviews and certifications at scale, often with AI recommendations to speed up the decision-making, which strengthens security and streamlines compliance audits.
5. Integrate IAM with SIEM for Monitoring
Finally, IAM must be integrated with Security Information and Event Management (SIEM) systems to provide continuous monitoring capabilities. Examples of account compromises include attempts to log in from unusual hours, spikes in the number of privilege escalation requests, and multiple failed MFA inputs. By correlating IAM data with other security telemetry stored in the SIEM, security organizations can get a complete picture of suspicious events. This integration effectively creates a cycle: IAM enforces policies, SIEM detects anomalies, and IAM and SIEM create a feedback loop that improves threat detection and response.
IAM Challenges and Risks
While IAM brings many security and compliance benefits, it also comes with challenges. Organizations that do not address those risks will likely find their IAM programs are not meeting expectations. Below are some of the most common challenges organizations will face.
1. Over-permissioning Users
One of the most common IAM mistakes is over-permissioning users. This is often a result of organizations leveraging large groups of users, not actually deprovisioning permissions that aren't being used, or a "better safe than sorry" mentality, whether someone needs access to a resource or not. Over time, this creates "permission creep," and a single user may have permissions across multiple roles that are useless. Ultimately, this extends the attack surface; in the event of a single compromised account, the intruder now has access to far more systems and data than is needed. Regular review of access, along with the principle of least privilege, is an effective way to reduce this danger.
2. Complex integrations with legacy systems
IAM systems are powerful, but integrating those solutions with legacy systems and applications can be a challenge. Many legacy systems were built without consideration of modern identity standards and therefore do not support protocols like SAML, OAuth, or OpenID Connect. Today’s IAM platforms support these standards with ease, but connecting to legacy systems often necessitates custom connectors, proxies, or manual workflows. Such workarounds can be inefficient and even create security holes. To successfully deploy IAM, organizations need solutions that work with both cloud-native and legacy ecosystems, managing security and access control from a singular location.
3. Insider threats and credential misuse
Internally, threats exist in the form of insider threats regardless of the intended action. While we often think attackers are accessing resources illegally, there is a significant potential for a valid credential to be misused. These credential misuse instances could be employees or contractors acting maliciously, but they can also be completely accidental. We can't forget the opportunity for breaches through stolen or weak passwords.
IAM tools help provide a layer of protection through strong authentication and MFA, which, when you couple that with user behavior monitoring as well as SIEM product integrations, to help detect questionable activity can help slow down potential misuse. But without proper policies and oversight, even advanced IAM technologies cannot fully prevent credential misuse.
4. Regulatory compliance gaps
Regulations such as GDPR, HIPAA, Sarbanes-Oxley (SOX), and PCI DSS introduce strict requirements for how organizations address identity and access. Organizations investing the time and effort into IAM should be aware of the penalties when something goes wrong; fines, publicly classified misconduct for being non-compliant, and work stoppages all make compliance important. The challenge is that organizations generally just do not align their IAM work properly with the requirements; incomplete audit history and audit trails, lack of deprovisioning processes and auditing for time durations or periods of when and how access is provisioned and deprovisioned, as well as how often access is reviewed, are just examples of compliance gaps, like when particular implementations are required.
Many of the established IAM technology vendors do have built-in compliance reporting, audit reporting and templates, and automation workflows to reduce the effort involved with the ongoing governance, but you need to have good governance processes and maintain documentation for good compliance.
Future of IAM: Cloud and AI
Identity and Access Management (IAM) is evolving quickly as enterprises move more into the cloud and adopt AI-based security models. As organizations modernize and refine how people access applications and sensitive data, they must navigate IAM development in the context of a hybrid world and multi-cloud infrastructures. The original IAM framework applied to on-premise environments was designed to restrict access to a single perimeter. Now that organizations are in hybrid cloud environments and adopt a multi-cloud approach to applications and data, the maturity of IAM must adapt. There are three major trends that we are seeing emerge in the field of IAM.
-
Cloud IAM as Foundation
Cloud IAM is a foundational requirement for identity and access management. Enterprises have thousands of applications (mostly SaaS) with sensitive data, located in private clouds and with public cloud providers. Organizations need IAM systems that allow them to write and enforce unified access policies across all environments. Cloud IAM provides scalability, API-driven integrations, and continuous visibility of access to users. Cloud IAM has the foundational capabilities of identity and access management that traditional perimeter-based IAM systems did not have. -
AI/ML Driven Security
AI and machine learning (ML) are creating a fundamental shift in identity security. Instead of depending on static rules to establish identity security, users will be evaluated based on their behavior and actions. User behavior across systems, datasets, and locations will be monitored and evaluated by AI-based IAM tools. If an employee logs into an application from a location he/she is not familiar with, or is downloading large volumes of sensitive data suddenly, AI-driven analytics will notify security teams so that they can further investigate. This creates a proactive protection layer against intrusions. IAM is changing from a reactive control or protection layer to become a proactive security layer. -
Identity Fabrics and Contextual Access
Identity fabrics and contextual access controls are becoming more widespread. An identity fabric serves as an orchestration layer that connects multiple identity sources and enforcement points to create an identity architecture. As a next step, contextual access, where access decisions are made based on context beyond just identity, such as device attributes, location, and risk signals, these two innovations are bringing IAM provisioning to the zero-trust world. IAM is moving towards "never trust, always verify," instead of "trust but verify," and ensuring that every access request can be verified contextually.
Together, these trends are reshaping IAM as a cloud-native, AI-enabled security fabric. Organizations that adopt these capabilities will improve their ability to meet the nexus of a new workforce, regulatory complexity, and ever-evolving threats to cybersecurity.
Final Thoughts
Identity and Access Management (IAM) has become an essential pillar of modern cybersecurity, assuring that the right people can access the right asset at the right level, at the right time, in today's cloud, mobile, and hybrid environments. Without IAM in place, organizations would be hard-pressed to balance usability with security.
That said, IAM alone is not enough. IAM governs access, but without ongoing validation, IAM cannot ensure that access remains appropriate and compliant over time. This is where Identity Governance and Administration comes into play. IGA is an oversight layer - it connects the dots between entitlement reviews, least privilege enforcement, segregation of duties, and regulatory compliance. In other words, IAM provides access, whereas IGA provides governance.
When IAM and IGA merge together, they provide a cohesive identity security framework that enhances compliance, reduces insider risk, and promotes secure workforce productivity. At Tech Prescient, our Identity Confluence platform accommodates this exact framework, empowering organizations to manage their access while embedding governance within the process.
IAM gives you the foundation, but pairing it with governance takes your program further.
With TechPrescient’s Identity Confluence, you can unify access management with governance, automate reviews, and stay audit-ready—all from a single platform.
Get started faster → Learn more about Identity Confluence
Frequently Asked Questions (FAQs)
1. What are the 4 pillars of IAM?
The 4 pillars of IAM are Administration, Authentication, Authorization, and Auditing. In conjunction, these pillars allow for identities to be "created and managed" appropriately, that users are "authenticated/notified" before system access, that entitlements align with job duties, and that all actions are "logged for responsibility and compliance2. What is an example of IAM?
For simplification, a general example of IAM is perhaps user access to corporate applications via Single-Sign-On (SSO) plus Multi-Factor Authentication (MFA). In this scenario, users can access several systems with one set of credentials, and MFA provides an additional layer of protection against credential theft during authentication.3. What is the difference between IAM and IGA?
IAM is about managing user identities and controlling user access, meaning you want to make sure the right people have access to the right things. IGA (Identity Governance and Administration) is about providing the same functions as IAM, but also adds aspects of compliance, oversight, and governance controls, such as access certifications, policy enforcement, and audit reporting. (Read our full comparison here → refer to IGA vs IAM blog).4. What are some benefits of IAM?
IAM can increase security by limiting unauthorized access, ensuring your organization is compliant with regulations, and improving productivity by enabling streamlined logins and faster provisioning. It can also create an improved user experience by eliminating login fatigue and making sure access bottlenecks won’t slow individuals down.5. How does IAM enforce Zero Trust?
IAM is a foundation of the Zero Trust model, where the owner does not have any trust in the user and devices by default. IAM utilizes least privilege access, continuously verifies user(s) and sessions, and contextualizes access based on role, device, and risk.