
What Is Identity Governance Framework: Guide For 2026

In today's digitally connected world, data is a great business asset. From sensitive financial records to employee credentials, nearly every piece of digital information is valuable. As per Verizon’s Data Breach Investigations Report , 61% of data breaches involve stolen or misused credentials.
This is the very reason why organizations are investing on identity and access governance solutions. In fact, the Identity Governance and Administration (IGA) market is expected to reach $24 billion by 2027.
But here’s an interesting aspect: securing access isn't just about technology, it’s about structure. That’s where an effective identity governance framework comes into play. You could be dealing with hundreds or even millions of users. This framework offers a structured, policy-driven approach to managing who gets access to what, when, and why.
What Is an Identity Governance Framework?
Identity Governance and Administration (IGA) is a structured set of standards that helps enterprises manage user identities, enforce access policies, and maintain compliance. But when we are referring to an identity governance framework we are talking about a strategic blueprint that guides how those governance policies are implemented across an organization.
So, what is an identity governance framework in simple terms?
It is a policy-driven model that enables IT teams to define, manage, monitor, and control digital identities and their access privileges across various applications, systems, and environments. This includes setting role-based access controls (RBAC), ensuring access certification, automating user provisioning and deprovisioning, and aligning with compliance and audit requirements.
To understand this better, let’s take an example: Imagine a financial institution XYZ Bank. Its critical data like customer IDs, transaction records, and card information is stored across various internal systems and third-party SaaS platforms. The finance team needs full access to this data, but marketing or HR should have no visibility into it.
With an appropriate identity governance framework in place, XYZ Bank can implement role-based access control (RBAC) policies that allow only finance team members to access these systems nothing more, nothing less. This approach eliminates unauthorized access, reduces the risk of insider threats, and ensures compliance with regulatory standards like GDPR and SOX.
Now, you might ask: “Isn’t this what Identity and Access Management (IAM) does?” It's a valid question. While IAM handles the ‘who logs in’ part, IGA goes deeper governing why they have access, what level of access they have, and whether that access is still valid.
Why Does Identity Governance Matter in 2025?
In 2025, the digital threat landscape is more complex than ever before. With the explosion of cloud apps, hybrid work environments, and an increase in third-party integrations, organizations face growing challenges in managing access effectively. This leads to a dangerous phenomenon known as cloud sprawl, where identities and permissions multiply across disconnected systems creating the perfect opportunity for attackers.
Add to that the rise of insider risks, and the need for an effective identity governance framework becomes non-negotiable. According to the 2023 Verizon Data Breach Investigations Report, 74% of data breaches involved human elements, including errors, misuse of privileges, and stolen credentials. These breaches could have been prevented with better access governance best practices and automated access reviews in place.
Identity governance isn’t just about security it’s about resilience and accountability. With increasing pressure from regulations like GDPR, HIPAA, and SOX, organizations must prove they have tight control over user provisioning and deprovisioning, access certification, and segregation of duties (SoD).
By adopting a robust IGA framework, companies can:
- Prevent excessive or outdated access.
- Enforce role-based access control (RBAC).
- Meet evolving compliance and audit demands.
- Reduce the risk of data breaches by addressing identity-related vulnerabilities.
In 2025, identity governance solutions are no longer optional they're essential for sustaining trust, ensuring agility, and maintaining competitive edge.
Identity Governance vs. Identity & Access Management (IAM)
What’s the difference between IGA and IAM? identity governance and identity and identity and access management (IAM) serve distinct purposes. Here’s a quick comparison:
Aspect | Identity Governance (IGA) | Identity and Access Management (IAM) |
|---|---|---|
Core Focus | Governance, policy enforcement, lifecycle management | Authentication and authorization |
| Scope | Monitors who should have access and why | Manages who can access systems |
| Functions | Access reviews, role assignments, access recertification, compliance tracking | Login management, password policies, session handling |
| Lifecycle Coverage | End-to-end user lifecycle: provisioning, modification, deprovisioning | Mainly login and real-time access control |
| Use Case | Ensuring least-privilege access across systems | Verifying user credentials and granting access |
| Governance Layer | Strategic—aligns with compliance and audit standards | Operational focused on system access enforcement |
Example: IAM verifies if User A can access a system. IGA evaluates whether they should continue to have access, especially after a role change or department shift.
By integrating both, businesses achieve a powerful identity and access governance strategy that secures the entire identity lifecycle management process.
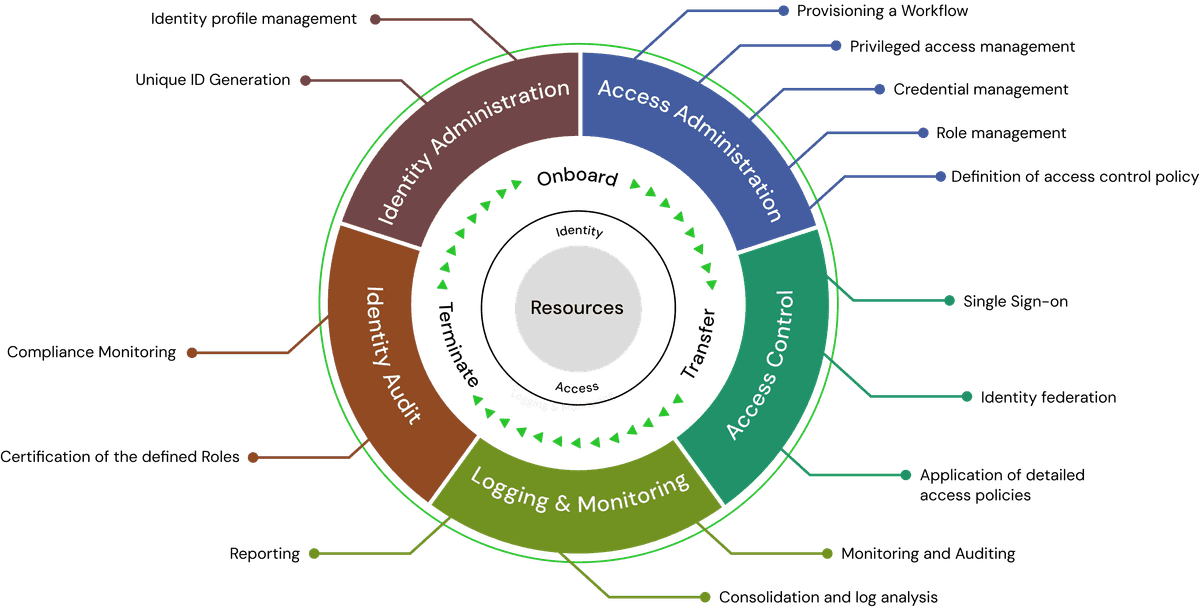
Key Components of an Identity Governance Framework
An effective identity governance framework consists of several foundational components that help organizations manage digital identities, enforce access policies, and maintain regulatory compliance. These elements ensure that every identity is governed consistently across its entire lifecycle, minimizing risk and supporting business operations securely.
Identity Lifecycle Management
Identity lifecycle management forms the foundation of any IGA framework. It covers every stage of a user’s journey within an organization, including onboarding, role transitions, and offboarding. The goal is to ensure that access is provisioned promptly, adjusted as roles evolve, and revoked when it is no longer needed.
Automating user provisioning and de-provisioning helps eliminate the risk of unauthorized access and reduces administrative overhead. This not only strengthens security but also ensures that access rights always align with business needs.
Role-Based Access Control (RBAC)
Role-based access control, or RBAC, allows organizations to grant access permissions based on job roles rather than individual requests. This streamlines the process of assigning and managing access and helps enforce the principle of least privilege across departments.
By using RBAC as part of an identity governance solution, businesses can prevent privilege creep, reduce manual errors, and improve scalability across teams and systems.
Segregation of Duties (SoD)
Segregation of duties is essential for mitigating internal threats and ensuring proper checks and balances. It ensures that no individual has enough control to execute conflicting functions, such as both initiating and approving a financial transaction.
Incorporating SoD policies into your identity governance framework strengthens compliance posture, reduces fraud risk, and enhances transparency within business operations.
Access Review and Certification
Access reviews and certifications help verify that users have the correct level of access based on their roles. This process involves reviewing and validating access rights on a regular basis to eliminate excessive or outdated permissions.
Automated access reviews are a core capability of identity governance tools. They help identify risks early, enforce access policies, and ensure that access entitlements remain aligned with business and compliance requirements.
Audit and Compliance
Audit and compliance capabilities are crucial in highly regulated industries. Your identity governance solution should provide a clear record of who accessed what, when, and why, along with policy enforcement and violation alerts.
Complete audit trails and real-time reporting make it easier to demonstrate compliance with frameworks like GDPR, HIPAA, and SOX. They also improve incident response and build trust with stakeholders.
Risk Analytics
Risk analytics adds a predictive layer to identity governance. It allows organizations to monitor user behavior, identify anomalies, and respond to threats proactively.
By integrating risk scoring and behavior analysis, organizations can focus on high-risk access patterns and take timely corrective action. This enhances security across the identity lifecycle and supports a more adaptive access governance strategy.
3 Business Benefits of Implementing an IGA Framework
Implementing an identity governance framework offers more than just security. It strengthens compliance, boosts operational efficiency, and ensures access is always aligned with business needs. Let’s break down the top three benefits.
1. Improved Security
An IGA framework continuously monitors and adjusts access based on user roles and their behavior. Through automated access reviews, RBAC, and identity lifecycle management it is ensured that users only have access to what they need. This reduces the risk of unauthorized access, insider threats, and credential misuse, making your organization far less vulnerable to breaches.
2. Regulatory Compliance
Identity governance solutions help enforce policies such as least privilege and segregation of duties, aligning with regulations like GDPR, HIPAA, and SOX. They also maintain audit-ready logs and reports, making compliance easier and reducing the risk of fines during regulatory audits.
3. Operational Efficiency
By automating user provisioning, access updates, and de-provisioning, an IGA framework reduces manual workload for IT teams. This leads to faster onboarding, fewer errors, and consistent enforcement of access policies, improving both productivity and scalability.
How to Implement an Identity Governance Framework
Implementation of an identity governance framework requires a blend of policy, technology, and collaboration. Let us have a look at five essential steps to get started.
1. Understand Business Requirements
Start by aligning your identity governance goals with overall business objectives. Identify key systems, critical data, user roles, and compliance mandates specific to your industry.
This step ensures your IGA framework is tailored as per your organization’s risk profile, operational needs, and regulatory responsibilities, whether you're in finance, healthcare, or a SaaS-driven enterprise.
2. Define Access Policies
Establish access policies based on role-based access control (RBAC) and the principle of least privilege. Clearly define who should have access to what, under what conditions, and for how long. Include rules around user provisioning and deprovisioning, segregation of duties (SoD), and access certification to prevent excessive or conflicting privileges.
3. Choose IGA Tools
Select the right identity governance tools that offer centralized visibility, policy enforcement automated access reviews, and reporting capabilities. Modern tools should integrate easily with your existing identity and access management (IAM) infrastructure, support compliance tracking, and offer built-in workflows for access governance.
4. Automate with Workflows
Use automation to handle routine identity tasks like granting access on role changes, revoking access upon termination, or triggering certification reviews. Automated workflows not only improve operational efficiency but also reduce the risk of human error, which is often the root cause of security gaps.
5. Review and Optimize Regularly
Identity governance isn’t a one-time effort. Conduct regular audits, access reviews, and policy evaluations to ensure continued alignment with business changes and evolving compliance standards. Track metrics, assess risk scores through risk analytics, and update your framework as needed to maintain a strong security posture.
Best Practices for Identity Governance
To establish a robust and scalable identity governance framework, organizations must go beyond basic implementation. A combination of leadership support, smart access models, and automation helps ensure long-term success in managing digital identities and access.
Every effective Identity Governance solution needs support from executive leadership. Gaining buy-in ensures the initiative receives proper funding, visibility, and collaboration across departments. Leadership backing also reinforces the importance of identity governance as a core component of enterprise security and compliance.
Adopting a Zero Trust approach strengthens identity and access governance by removing any assumption of trust. Every user, device, and system is continuously validated before access is granted. When aligned with your IGA framework, Zero Trust ensures strict access controls and better protection against insider threats and credential misuse.
Access recertificationinvolves periodic review of user entitlements to ensure they still align with job roles. This step helps prevent privilege creep and supports policies like segregation of duties (SoD). With automated access reviews, teams can quickly identify and revoke outdated or unnecessary permissions to stay audit-ready and secure.
Just-in-time access provides temporary access to resources only when needed. It eliminates standing privileges and limits access exposure to a predefined duration. This model supports least privilege access, reduces risk, and helps manage sensitive data more securely within the identity governance framework.
Automation improves accuracy and efficiency across identity governance processes. It simplifies tasks like user provisioning, access requests, deprovisioning, and policy enforcement. By leveraging identity governance tools with built-in workflows and analytics, teams can streamline operations and reduce the burden of manual oversight.
Why Our IGA Solution Stands Out Among Leading Tools
In an ever-expanding market of cybersecurity solutions and identity governance tools, what sets a solution apart is not just featured checklists but how well it aligns with real-world needs, adapts to business change, and scales with confidence. That’s where our IGA framework at Tech Prescient excels.
We’ve designed our platform from the ground up with a deep understanding of the challenges modern enterprises face whether it’s managing cloud sprawl, meeting stringent compliance demands, or enforcing precise role-based access control (RBAC) across dynamic user environments.
Here’s why our identity governance solution goes beyond the ordinary:
-
Automate provisioning and de-provisioning across all systems with precision and speed.Unified Identity Lifecycle Management
-
Built-in risk analytics to detect and respond to high-risk access patterns in real-time.Risk-Aware Governance
-
Architected to support just-in-time access and least privilege models out-of-the-box.Zero Trust Ready
-
Works smoothly with your existing IAM, HR, ITSM, and compliance tools.Seamless Integrations
-
Real-time access certification, reporting, and audit trails for stress-free regulatory reviews.Audit-First by Design
-
Whether you’re managing 500 or 50,000 identities, our platform adapts to your growth.Built for Scale
Why Tech Prescient IGA vs Others
Ready to see the difference for yourself? Choose Tech Prescient’s IGA platform for smarter, scalable, and risk-aware identity governance—built for enterprises that demand more from their access management.Frequently Asked Questions (FAQs)
- What is the purpose of an Identity Governance Framework?
The main purpose of an identity governance framework is to ensure that the right people have the right level of access to the right systems at the right time. It helps organizations manage user identities and access privileges securely, reduce the risk of unauthorized access, and stay compliant with industry regulations like GDPR or HIPAA. In short, it’s a blueprint for controlling digital access in a safe, scalable, and policy-driven way. - What industries benefit most from implementing identity governance?
Industries that deal with sensitive data or strict compliance regulations benefit the most from identity governance. This includes finance, healthcare, government, manufacturing, and large-scale enterprises. If your business needs to protect confidential data, prove compliance, or manage access across hundreds or thousands of users, implementing an IGA framework is not just helpful, it’s essential. - Can identity governance be automated?
Yes, identity governance can absolutely be automated—and it should be. With the right identity governance tools, you can automate tasks like user provisioning and deprovisioning, access reviews, and policy enforcement. Automation reduces manual errors, speeds up onboarding and offboarding, and ensures access rights are always aligned with user roles and business rules.