
Identity Security Posture Management (ISPM): A Complete Guide


Identity Security Posture Management signifies a change from reactive identity protection to proactive identity risk intelligence. During a time when the majority of data breaches are linked to human error and the ISPM market is growing exponentially, there has never been a more pressing need for complete identity security. With cloud and SaaS applications continuously proliferating, legacy security is unable to keep up with the outpouring of attack surface. The inability to manage access across multiple environments has shown that traditional identity solutions (SSO, IAM, IGA) cannot solve for identity security. This is why more organizations are looking to ISPM: to employ a full-spectrum strategy for reducing and ameliorating the attack surface related to all identity access in the enterprise. In today's complex, digital ecosystem, understanding and acting upon ISPM is not optional; it is critical to resiliency to identity threats.
Key Takeaways:
- Continuous identity risk assessment transforms periodic reviews into real-time security intelligence
- Automated remediation capabilities reduce mean time to response from days to minutes
- Zero Trust architecture foundation through identity-centric security controls
- Measurable compliance automation with a reduction in audit preparation time
What Is Identity Security Posture Management (ISPM)?
Identity Security Posture Management (ISPM) involves securing an organization's data access for all digital identities. ISPM encompasses the processes, technologies, and policies used to manage identities across administrators, IT systems, and applications. The purpose of ISPM is to mitigate the risk posed by identity access to the entire enterprise while still allowing the business to function.
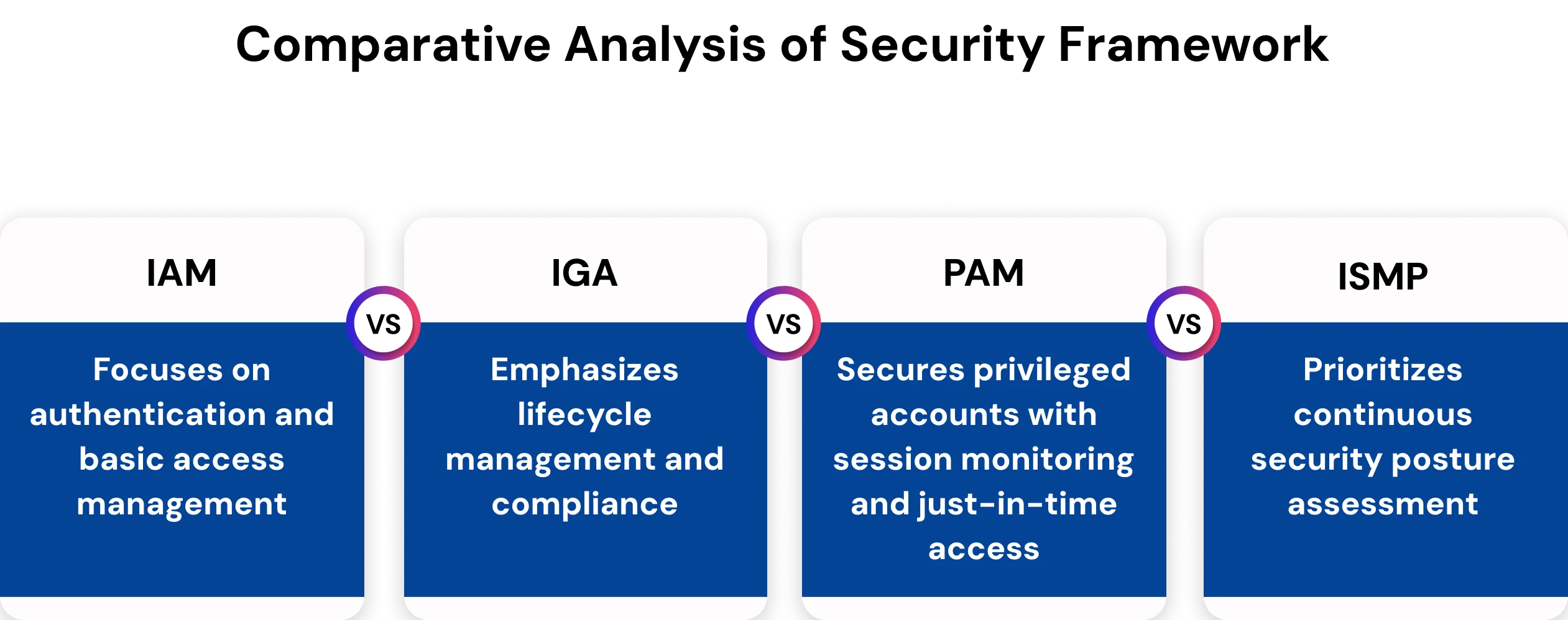
ISPM fundamentally changes organizational approaches to identity security by transforming identity security from a periodic, reactive assessment to a continuous, proactive risk management framework. Traditional Identity and Access Management (IAM) systems assess and manage identity access, focusing on authentication and basic access provisioning. Identity Governance and Administration (IGA) solutions expand on IAM's capabilities with lifecycle management and periodic assessments of compliance. ISPM goes beyond IGA solutions to provide organizations with informed security intelligence across the entire identity ecosystem and in real time.
Core Principles Defining Modern ISPM
- Continuous Risk Assessment: ISPM continues on the premise that identification-related risk typically changes on a continuous basis, so rather than having review cycles quarterly like most companies, the ISMP platforms give real-time visibility through behavioural analytics, machine learning algorithms, and policy monitoring.
- Using Intelligence to Inform Access Decisions: Contemporary ISPM solutions apply artificial intelligence to sift through massive identities, identifying PDF patterns that human reviewers will miss. This opens the door to decisions on appropriate access levels and risk remediation before an incident occurs.
- Automated Remediation Beyond Detection: Traditional identity protection tools focus on alerts about suspicious activity, whereas ISPM platforms give operators the ability to automatically remediate the risk through policy enforcement, access modification, or workflow orchestration.
Business Context for ISPM Evolution
The rise of ISPM indicates profound shifts in enterprise operations. Digital transformation has caused most breaches to involve data stored in cloud environments, while stolen credentials are responsible for a substantial portion of all breaches and often take hundreds of days to identify and contain.
| Traditional IAM | IGA | PAM | ISPM |
|---|---|---|---|
| "Who gets access?" | "What access do they have?" | "How do we secure privileged access?" | "What risks do they pose?" |
| Reactive | Periodic reviews | Session-based protection | Continuous monitoring |
| Basic provisioning | Lifecycle management | Privileged account management | Behavioral analytics |
| Authentication focus | Compliance focus | Privileged security focus | Risk-centric approach |
How ISPM Works
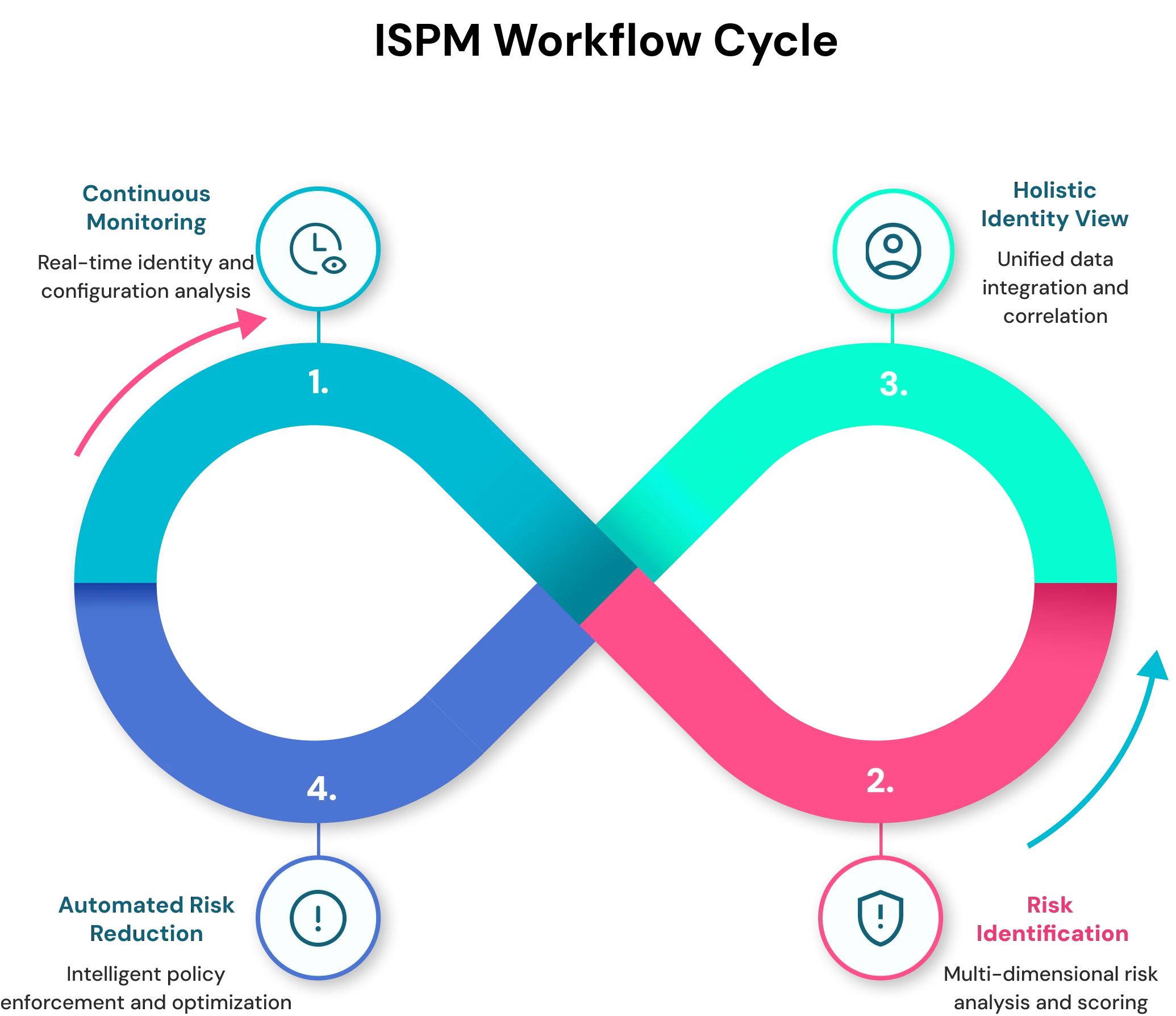
ISPM functions through an integrated framework of continuous discovery, real time risk assessment, behavioural analytics, automated policy enforcement and intelligent remediation that sustains an optimal identity security posture across dynamic enterprise environments.
1. Continuous Monitoring & Assessment
Continuous monitoring and assessment in ISPM employs real-time collection, analysis and evaluation of identity data across all systems for maintaining current knowledge of security posture and actionable intelligence.
- Comprehensive Identity Discovery: Modern ISPM begins with automated discovery of all types of identity across the enterprise ecosystem that is continuously working to identify new accounts, systems and access relationships.
- Human Identity Discovery: ISPM platforms connect to corporate directories (Active Directory, LDAP), cloud security providers (Azure AD, Okta, Google Workspace), and application-specific user stores to identify all human accounts, INCLUDING federated systems and dormant accounts for terminated employees.
- Service Account Identification: The platform systematically discovers service accounts used for application communication, database connections, API integrations, and automated processes, including certificate-based authentication and batch processing accounts with high privileges.
- Real-Time Activity Monitoring: Beyond static discovery, ISPM platforms continuously monitor identity activities, including real-time authentication pattern analysis, authorization decisions, and configuration changes that affect access controls.
2. Risk Identification & Scoring
The ISPM risk identification and scoring process incorporates systematic review of identity-related data, using machine learning algorithms, behavioural analysis and threat intelligence, to scope security risks and prioritize remediation tasks.
- Multi-Dimensional Risk Analysis: ISPM platforms assess identity risks across multiple dimensions, developing overall risk profiles that include technical, behavioural, and business considerations.
- Permission Risk Assessment: The platform provides assessment of whether each identity has unnecessary access using role-based assessments, evaluating usage data and checking policy misalignment.
- Behavioural Risk Analysis: Advanced ISPM platforms use machine learning and have the ability to review patterns of user behaviour, detect and identify anomalies that may point to compromised accounts or insider threats through the creation of baseline behaviour, and then detect deviations from that baseline behaviour through anomaly detection.
3. Holistic Identity View
A full view of identity in ISPM gives consolidated visibility of all identity data for the entire enterprise ecosystem, leveraging correlated information from a variety of sources, leading to an overall view and thoughtful decision-making.
- Unified Data Integration: Building a holistic view requires integration with identity data from corporate directories, cloud storage identity providers, application databases, and human resources (HR) data to provide context for organization and employment status.
- Cross-System Correlation: A holistic view allows an understanding of relationships that progress across multiple systems, in some cases allowing the tracking of identities in their complete lifecycle and analyzing risks across identity relationships.
4. Automated Risk Reduction
Automated risk reduction in ISPM includes technology-fuelled proceedings that autonomously discover, evaluate, and remediate identity-related security risks in real time without any manual input.
- Intelligent Policy Enforcement: Modern ISPM solutions enforce security policies utilizing automated controls to avert risks from occurring, including the ability to block policy-violating access requests and making dynamic access adjustments based on a risk evaluation process.
- Machine Learning-Driven Optimization: Advanced ISPM platforms rely on machine learning that fashion effectiveness through pattern-recognition, predictive risk assessments, and ongoing learning from security incidents.
Why ISPM Matters for Modern Enterprises
The strategic relevance of ISPM is tied to various factors, including the increasing attack surfaces of the digital stream, increasingly sophisticated identity-based threats, the increased pressure to comply with regulatory requirements, and the need to accommodate a Zero Trust architecture. All of which have invalidated traditional approaches to identity protection that exhibit reactive behaviour.
1. Growing Attack Surface in Hybrid Environments
Increasing attack surfaces in hybrid models means all potential points of entry across on-premise environments, multiple clouds and cloud service providers, SaaS applications, and connected partner ecosystems.
- Infrastructure Complexity: Modern enterprises typically operate within complex technology environments, which contributes to rapid growth of the ISPM market; there is a clear urgency for overall identity security and resilient timeout processes, especially in complex environments.
- Multi-Cloud Identity Challenges: Organizations implementing multi-cloud strategies will continue to face unique complexities related to identity protection, as each platform has its identity model, cross-cloud resource access requirements, and varying permissions inheritance traits.
- SaaS Application Proliferation: The global growth of the ISPM market adoption correlates with the worldwide challenge of managing identities across thousands of SaaS applications.
2. Identity as the Most Exploited Entry Point
Identity-based attacks encompass threat actors compromising legitimate user credentials or exploiting weaknesses in identity protections to gain unauthorized access to systems, data, documentation, etc., while bypassing traditional perimeter security controls.
- Statistical Evidence: The current objective threat intelligence shows that cybercriminals are focusing their intent on identity-based attacks. Stolen credentials are responsible for a large portion of all breach vectors, while it is shown that users are clicking on phishing emails within minutes.
- Business Impact: The global average cost of data breaches continues to increase year over year. Organizations are incurring direct incident response costs and long-term reputation risks.
3. Enabling Zero Trust Architecture
Zero Trust architecture is based on "Never trust, always verify" principles, which require continuous authentication and authorization in which identity is the primary trust anchor.
Zero Trust architecture is wholly dependent on the comprehensiveness of ISPM. Research indicates that the vast majority of account compromise-type attacks can be blocked with multi-factor authentication, highlighting the critical importance of identity controls in ZTA implementations.
4. Proactive Threat Prevention
The goal of preventing threats before they happen is to discover and address security threats before they are exploited by a threat actor rather than just responding to an incident that has occurred. This means taking a proactive approach to identity security and moving from reactive incident response to predictive risk management to prevent the identity breach or attack altogether.
- Early Threat Detection: ISPM platforms provide early threat detection capabilities based on behavioural anomaly detection that utilize machine learning algorithms, constructive risk modelling that uses historical data analytics, and automated preventive controls supported by a policy-enforced prevention capability.
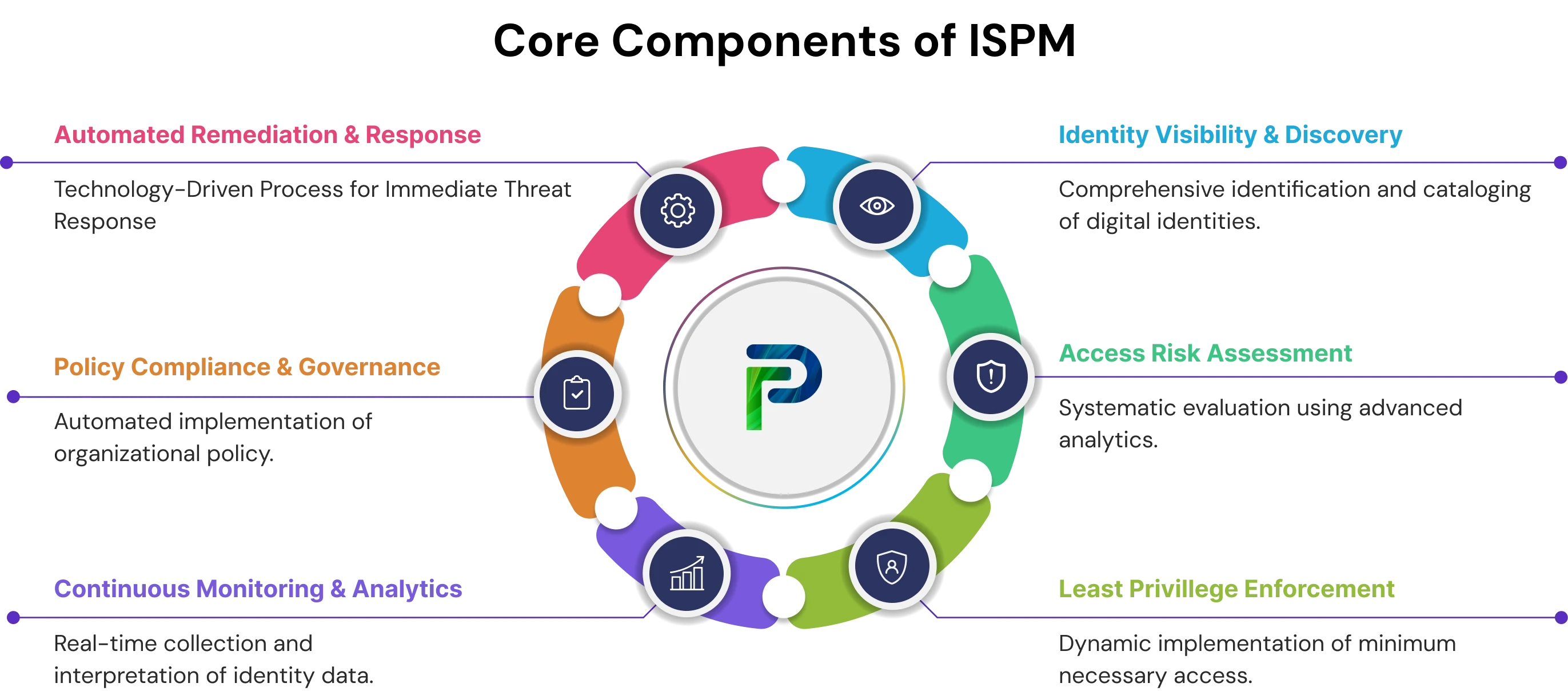
Core Components of ISPM
The core capabilities of the ISPM process represent the foundational capabilities that organizations should develop to properly manage identity security risk management within their organization. This encompasses identity discovery, risk assessment, policy enforcement, monitoring, compliance management, and automated remediation.
1. Identity Visibility & Discovery
Identification and discovery of identities encompasses comprehensive identification, cataloguing, mapping, and continuous monitoring of every digital identity and access relationship in all related cloud security environments, which provides the baseline intelligence for effective identity protection.
Effective identity discovery means scanning and identifying identity across the boundaries of business before a breach occurs. This involves systematic identification across the organizational ecosystem, including human identity discovery through the corporate directory and supported by cloud security providers, non-human identity identification for service accounts and machine identities, as well as privileged account discovery and management.
- Access Relationship Mapping: To understand the ties between identity and resources, complete analysis needs to include direct permission analysis, inherited access assessment based on group memberships, and cross-system access affiliation analysis and federation and synchronization.
2. Access Risk Assessment
Access risk assessments are structured assessments of identity provision, permissions, and behaviours that leverage advanced analytics to identify security weaknesses and compliance violations.
- Permission Risk Analysis: ISPM platforms analyze the adequacy of access rights for the population by exploiting excessive privilege identification, segregation of duties violations, and account hygiene reports to identify orphaned accounts and weak authentication.
- Behavioural Risk Analysis: Great ISPM platforms use advanced machine learning capabilities for abnormality detection and risk score day-to-day behaviour of users by including quantitative and qualitative evaluations.
3. Least Privilege Enforcement
The enforcement of least privilege is the operationalization of access controls to ensure that each identity only has the minimum permissions to perform legitimate business purposes for users.
- Dynamic Access Control Implementation: Modern ISPM platforms implement intelligent, adaptive access controls, including both risk-based access decisions and just-in-time access, to give users access that is by design or set to automatically expire.
4. Continuous Monitoring & Analytics
Ongoing tracking and analytics involve real-time gathering and assessment of identity data using sophisticated analytics for continued awareness of security posture to identify new potential threats.
- Real-Time Activity Surveillance: ISPM platforms will monitor identities' activities, such as monitoring logins, maintaining patterns, multi-factor authentication compliance, and tracking authorization decisions to evaluate the effectiveness of access control and usage of permissions.
5. Policy Compliance & Governance
Policy compliance and governance involve the orderly implementation and enforcement of organizational policy and regulatory standards through automated controls, regulatory oversight, and ongoing evaluation.
Regulatory Compliance Management: ISPM platforms regardless of integrating compliance with an identity and access management strategy. Various regulatory compliance requirements address compliance across industries, such as financial industry oversight regulations, including SOX and PCI DSS; compliance with healthcare industry regulations, such as HIPAA; and various privacy regulations, including GDPR and the California legislation, such as CCPA.
6. Automated Remediation & Response
- Automated remediation includes technology-enabled processes which automatically recognize, evaluate, and resolve identity-related security risks in real time, shrinking the time from threat identification to neutralization.
- Immediate Threat Response: ISPM (identity and security posture management) platforms automatically respond to security events through account compromise response and policy violation remediation using intelligent decision-making based on the risk severity and the business context.
Benefits of Implementing ISPM
The benefits of implementing ISPM include measurable enhancements in security risk reduction, operational efficiencies, regulatory compliance, business agility, and cost efficiencies, providing a quantifiable return on investment.
1. Reduced Security Risk & Attack Surface
When we measure security enhancements, we can reduce risk through ISPM by employing a systematic process of identifying and remediating identity-related risks and threats – and behavioural anomalies that a threat actor could exploit. ISPM provides the ability to continually monitor and evaluate access controls, identity vulnerabilities, and enterprise misuse and overprivilege. In doing so, ISPM reduces the chances of breaches and reduces the impact or damage severity if a breach does occur by limiting accessible data to compromised identities.
- Quantifiable Risk Reduction: Organizations that have implemented a multi-layered ISPM programme have experienced measurable improvements in their overall security posture. Organizations employing extensive use of AI in security have realized a more significant cost advantage than organizations that do not utilize AI. Furthermore, research has shown that MFA can contain the vast majority of compromised accounts.
- Faster Threat Detection: Modern ISPM platforms can facilitate a significantly faster response. Organizations have demonstrated a significantly reduced incident lifecycle from identification to containment.
2. Improved Operational Efficiency
Organizations that implement comprehensive ISPM programmes realize measurable "less" security costs. Organizations that rely on AI for security yield substantial cost savings compared to organizations that do not rely on AI, and research indicates that MFA can inhibit the overwhelming majority of compromised accounts.
- Access Management Process Automation: ISPM automates traditionally manual processes, including user lifecycle management automation, access review process optimization with a 60-80% reduction in manual review requirements, and IT resource optimization enabling strategic focus.
3. Stronger Compliance & Audit Readiness
Improved compliance and audit readiness through ISPM means systematically applying automated controls, continuously collecting evidence, and documenting compliance performance as you go. ISPM helps governance and risk teams identify areas where they may not be compliant with regulations such as GDPR, HIPAA, or PCI-DSS. ISPM helps to enable these teams to continuously monitor employee and contractor access and intervene when policies have been broken. Many industries are also required to implement ISPM strategies due to industry-specific regulations around sensitive data handling and privacy.
- Continuous Compliance Monitoring: ISPM changes compliance from an event-based to an ongoing event validating compliance. It also enables automated policy enforcement processes and allows for all evidence to be collected in advance of auditing for easy evaluation to prepare for audit.
4. Enhanced Business Agility
Improved business agility through ISPM means being able to change the identity protection for a business' needs quickly and supporting technology adoption and change while having strong controls and security in place.
- Technology Adoption Enablement: SPM enables a security posture for new technologies such as cloud security migration, multi-cloud identity protection, and API security for cloud-native applications.
Top ISPM Tools and Vendors in 2025
The ISPM vendor landscape consists of standardized platforms and integrated solutions that provide full identity security posture management capabilities.
The ISPM market is growing rapidly, as progress has been made to normalize ISPM into mainstream security platforms.
1. Enterprise ISPM Platforms
Tech Prescient Identity Confluence: A Comprehensive ISPM Platform
Identity Confluence provides enterprise-grade ISPM on a unified platform with integrated identity governance and risk management capabilities. The platform combines automatic user lifecycle management with behavioural analytics to provide continuous assessment of identity security posture across hybrid environments.
Core ISPM Capabilities:
- Risk Analytics in Real-time: Algorithms powered by machine learning examine user behavior patterns and access relationships identifying anomalies and excessive privilege across 50+ integrated systems
- Automated Policy Enforcement: Visual RBAC/ABAC policy builders deliver dynamic access controls with just-in-time provisioning and automated deprovisioning workflows
- Continuous Compliance Monitoring: Built-in support for SOX, GDPR, HIPAA, and PCI DSS with automated evidence collection and one-click audit reporting
- Hybrid Architecture Support: You can to deploy as SaaS, on the premise, or hybrid with native connectors for cloud platforms (Azure AD, Google Workspace, Salesforce) and legacy systems.
2. Leading Market Competitors
CrowdStrike Falcon Identity Protection provides integrated ISPM as part of a holistic cybersecurity platform. This platform additionally includes: integrated security platform with ISPM for endpoint protection; identity security threat detection and response capabilities; or the cloud security infrastructure entitlement management. Saviynt emphasizes AI-driven identity security capabilities, which support a cloud security native architecture, such as intelligent identity analytics features; comprehensive IGA (Identity governance and administration) and PAM (privileged access management) platform integration; and natural language interface functionality.
Best Practices for Identity Security Posture Management
ISPM best practices entail the established techniques, implementations, and operational procedures those operating within the organization should use to be as effective, appropriate, and valuable as possible in achieving security goals, regulatory obligations, and value to the business.
1. Establish Comprehensive Identity Visibility
Identity visibility entails systematic discovery, continuous inventorying, and continuous monitoring of all digital identities and access relationships in place, which will provide the foundational intelligence necessary to successfully protect identities.
- Systematic Identity Discovery: Comprehensive discovery connects to every system within your organization, including primary identity repositories, secondary system integrations, specialized identity types, and external identity management for partners and vendors.
2. Implement Risk-Based Access Controls
Risk-based access controls entail determining access based on the comprehensive assessment of risk, taking into consideration user behaviour, sensitivity of resources, environmental context, and requirements of the business.
- Comprehensive Risk Assessment Framework: Effective risk assessment begins with an evaluation of risk from many dimensions, including user risk factors, environmental risk assessment, resource sensitivity risk assessment, and integration of threat intelligence.
3. Enforce Least Privilege Systematically
Consistent least privilege implementation establishes structured policy controls, ensuring each identity has only the minimal permissions necessary to accomplish legitimate responsibilities.
- Dynamic Access Control Implementation: Current ISPM platforms apply intelligent, adaptive policy controls by implementing risk-based access decisions and just-in-time provisioning with automatic expiration.
4. Integrate ISPM with Zero Trust Strategy
Aligning ISPM to a Zero Trust strategy means positioning the identity security capabilities to comply with the "never trust, always verify" approach while using identity as the basis of your security decisions.
- Identity-Centric Zero Trust Foundation: ISPM critical Zero Trust capabilities through continuous verification of identity, contextual access decisions based on real-time risk evaluation, and visibility into all identity activities across your enterprise ecosystem.
5. Ensure Continuous Compliance
Continuous compliance in ISPM is when you have established structured automated policies that are implemented and provide real-time awareness and the right evidence to provide continuous compliance.
- Automated Compliance Management: ISPM platforms enable compliance to be streamlined through the automated enforcement of policies, the automatic detection of violations and remediation in real time, and the generation of a complete audit trail for regulatory requirements.
Future of ISPM: AI, Zero Trust, and Beyond
The future of ISPM revolves around emerging technologies, reconceptualized architectural frameworks, and shifting business drivers that will transform identity security via the implementation of artificial intelligence, the evolution of Zero Trust, and cloud security frameworks.
1. Role of AI and Machine Learning in Identity Security
Using AI & machine learning in identity security makes use of artificial intelligence to improve threat detection, automate decisions, and anticipate security risks through malleable learning.
Advanced Behavioural Analytics: AI systems can comprehend complex patterns, utilizing multi-dimensional modelling, context-based anomaly detection, and predictive risk analysis.
2. ISPM as Foundation for Zero Trust Architecture
ISPM, as the Zero Trust foundational architecture, is using identity security posture management as the robust foundational principle of "never trust, always verify".
3. Integration with Cloud-Native and DevSecOps
Cloud-natively, through the integration of security capabilities, a development security operations model (DevSecOps) entails reshaping ISPM capabilities to support modern software development and deployment practices while ensuring security.
The future lies in ISPM solutions that offer governance, analytics, and automated remediation in integrated platforms built for today's enterprises.
Tech Prescient has positioned Identity Confluence at the forefront of this evolution by combining comprehensive identity governance expertise with next-generation ISPM capabilities to assist organizations in managing expected and unforeseen identity security challenges.
Ready to implement the ISPM strategies outlined in this guide?
Discover how our smart solution, Identity Confluence, can strengthen your organization's identity security posture with comprehensive risk assessment, automated remediation, and continuous compliance monitoring.
Frequently Asked Questions (FAQs)
1. What is Identity Security Posture Management (ISPM)?
Identity Security Posture Management (ISPM) is a comprehensive cybersecurity discipline that continuously monitors, assesses, and optimizes an organization's identity security posture through automated risk identification, behavioral analytics, policy enforcement, and intelligent remediation across all digital identities.ISPM represents fundamental evolution from traditional identity protection approaches. While conventional IAM systems focus on authentication and IGA solutions add lifecycle management, ISPM provides continuous, real-time security intelligence encompassing all identity types.
2. Why is ISPM important for modern enterprises?
ISPM importance stems from convergence of expanding digital attack surfaces, sophisticated identity-based threats, and Zero Trust architecture adoption. The rapid global ISPM market growth reflects urgent market need.3. How does ISPM differ from traditional IAM and IGA solutions?
ISPM differs by providing continuous security-focused assessment, behavioral analytics, and automated remediation while traditional IAM and IGA approaches focus on authentication, lifecycle management, and periodic compliance activities.4. What are the main components of effective ISPM solution?
Main components include Identity Visibility and Discovery, Access Risk Assessment, Least Privilege Enforcement, Continuous Monitoring and Analytics, Policy Compliance and Governance, and Automated Remediation and Response working together for comprehensive identity security.5. How long does it take to implement ISPM in enterprise?
ISPM implementation typically ranges several months for comprehensive deployment, with organizations achieving immediate value within weeks through identity discovery and initial risk assessment capabilities.6. What ROI can organizations expect from ISPM implementation?
Organizations typically realize significant ROI within 18-24 months through security risk reduction, operational efficiency gains, compliance cost savings, and business enablement benefits.7. Can ISPM integrate with existing security tools?
Modern ISPM solutions provide extensive integration capabilities with existing identity security infrastructure, business applications, cloud security platforms, and security tools through native connectors and APIs.8. How does ISPM support Zero Trust architecture?
ISPM supports Zero Trust by providing identity-centric foundation through continuous identity verification, risk-based access control, comprehensive monitoring, and automated policy enforcement making identity the primary trust anchor.