Principle of Least Privilege (PoLP): Definition, Benefits & Implementation

In today's age of threat-laden cyberspace, one of the strongest security controls isn't putting more tools into the solution, it's about taking away the unnecessary. The Principle of Least Privilege (PoLP) ensures that each user, system, and application is given no more and no less than the bare minimum level of access needed. This simple yet potent concept reduces the attack surface, prevents abuse, and creates a more robust cybersecurity stance.
Whether you're managing cloud infrastructures, hybrid IT setups, or preparing for compliance audits, implementing PoLP can lower your risk and operational complexity dramatically. In this blog, we'll demystify what PoLP is, why it's important, and how to utilize it effectively through practical steps and real-world scenarios.
What Is the Principle of Least Privilege?
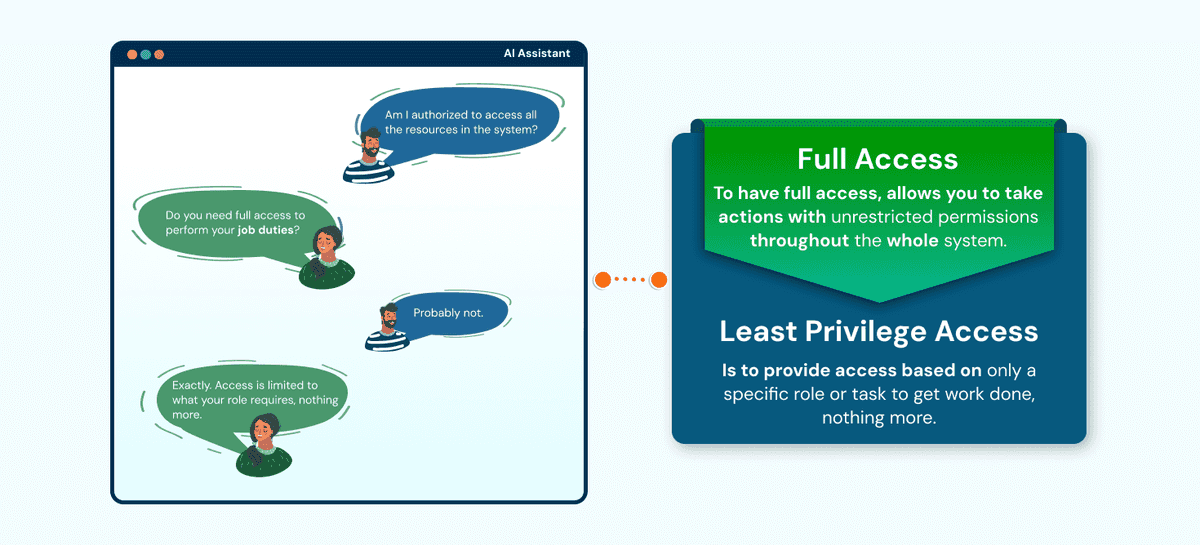
The Principle of Least Privilege (PoLP) is the practice of granting users, applications, or systems no more than the minimum privileges they need to accomplish their work, no less. This access control technique minimizes the risk of unintentional mistakes, insider threat, or system compromise by forcing each entity to run under a narrowly defined set of privileges.
Let us understand this concept of PoLP with simple example. Think of access as a set of keys to a locked building. A receptionist may need a key to the front reception but not the server room. If all have a master key, then one mistake or worse, an ill intent, can compromise the whole system. That is why limiting access by role or responsibility is necessary in reducing risk.
Why Is Least Privilege Important?
The Principle of Least Privilege (PoLP) is a key consideration in reducing cybersecurity risk and enhancing operational control. By limiting access to only what is necessary for a specific role or activity, organizations can significantly reduce the attack surface. This reduces the chances of internal abuse and external attacks.
Adopting PoLP prevents privilege abuse, limits malware propagation, and yields better system stability. It also satisfies audit and compliance needs through traceable and authorized access across the board. Lastly, PoLP supports a proactive paradigm of cybersecurity protecting data, systems, and people by upholding access need-to-know.
Least privilege secures your company's systems and information in significant ways by putting it into practice. It minimizes the threat of unauthorized access, prevents malware from propagating, and avoids internal errors that cause massive outages or loss of data. It's a cornerstone of any contemporary cybersecurity plan.
According to a report by BeyondTrust, 80% of breaches involve privileged credential misuse. Implementing PoLP directly deals with this by limiting the number of users with higher access rights.
When used properly, PoLP not only offers protection but also maximizes overall operational efficiency and audit readiness. Here's a peek at how organizations gain from it on a day-to-day basis:
Key Principles Underlying the Principle of Least Privilege (PoLP)
Knowing the basis of PoLP makes it easier to understand why it's critical to security. Below is a breakdown of its fundamental purpose and meaning:
What does "least privilege" mean?
The "Least privilege" is the cybersecurity principle whereby users, programs, or systems only receive the explicit access needed to carry out their role, and not one inch more. Least privilege also becomes apparent in the permissions assigned to view, edit, or execute data and system functions based solely upon the user's job role. By limiting access to a strictly role-appropriate basis, organizations can minimize the risks of data exposure, misadventures, and breaches directed at internal and external contexts.
Why is it used?
PoLP allows for better cybersecurity by reducing the potential for malicious or accidental misuse. It avoids data leakage, unauthorized access, and insider threats by granting only the required permissions. It also facilitates audits and compliance by making it easy to monitor who accessed what and when. Lastly, PoLP establishes a better-controlled, manageable, and secure access environment.
Real-World Examples of Least Privilege
To understand PoLP clearly, imagine a data center with multiple access levels:
Scenario | Minimum Required Access | Risk If Over-Privileged |
|---|---|---|
Software Developer | Access to specific code repositories | Access to production servers could lead to accidental outages |
External Auditor | Read-only access to audit logs | Write access could compromise data integrity |
Customer Support Rep | Access to customer profiles | Access to billing systems could expose sensitive data |
These are genuine risks. In big companies, overly privileged users have indeed caused system downtime, data loss, and compliance issues all due to lack of granular access control.
A well-known breach at a large financial services firm was due to an over-privileged developer account being exploited by an attacker to access customer financial records. This incident can highlight the essential need for privilege boundaries and ongoing access reviews.
The moral: security is not achieved by trusting others less but trusting systems more by defining what each role must be capable of accessing and implementing it exactly.
Before we go into how PoLP is the same or dissimilar to Zero Trust, let's establish where they intersect.
Both approaches attempt to achieve minimal risk through access control, but they accomplish it in different ways.
How Is Least Privilege Different from Zero Trust?
While both PoLP and Zero Trust aim to reduce cybersecurity risks, they approach the challenge from different angles. Here are five key differences that help distinguish them:
- Objective: Where PoLP grants access to only what is necessary for an action, Zero Trust is about validating every access request, no matter if it's inside or outside the network.
- Scope: The scope of PoLP focuses on users, apps, and systems ensuring they are granted only the minimal acceptance needed. Zero Trust goes broader in scope by including laptops, network traffic, and validating identity.
- Enforcement: Least privilege is enforced via models such as RBAC or ABAC to create roles and limit permissions. ZT employs ongoing authentication processes through multi-factor authentication (MFA) as a means to authenticate the session.
- Assumption: When PoLP operates on the premise that restricting access limits risk, Zero Trust operates on the assumptions that breaches will happen and that ongoing surveillance and validation are necessary.
- Integration: PoLP provides a simple path to start with Zero Trust, but Zero Trust includes PoLP and expands the opportunity to evaluate as a comprehensive security framework that continuously validates all access points - before and after entry.
Together, PoLP and Zero Trust create a layered defense approach, where access is both minimized and continuously verified.
Feature | Minimum Least Privilege | Risk If Zero Trust |
|---|---|---|
Goal | Minimize access | Continuously verify access |
Applies to | Users, apps, systems | Users, devices, network traffic |
Work together? | Yes, PoLP is part of Zero Trust | Yes, they often support each other |
How to Use the Principle of Least Privilege in Your Company
We've covered what the Principle of Least Privilege (POLP) is, how it functions, and its core concepts, and now we're ready to get into how you can implement it, and probably more importantly, how it can benefit your organization.
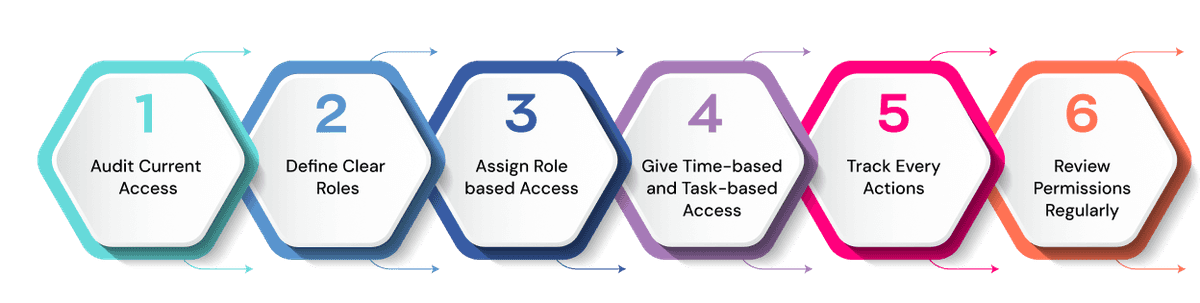
Applying PoLP starts with visibility. Begin by auditing who currently has access to what systems and tools. Often, you’ll find outdated permissions or blanket access that no longer align with roles.
Once that baseline is established, define clear access roles using the principle of "need to know." Group similar access requirements under Role-Based Access Control (RBAC), so that permissions are assigned by responsibility, not person.
In fast-changing environments, Just-In-Time (JIT) access makes a difference. Temporary access can be granted for specific tasks or projects, then automatically revoked. This keeps access clean without slowing anyone down.
Finally, log all access events and conduct regular reviews. Automated tools can flag anomalies, reduce manual workload, and ensure the right people always have the right access, nothing more.
Common Challenges and How to Overcome Them
Implementing least privilege in an organization isn’t always straightforward. Legacy systems often weren’t built with fine-grained access control in mind, making integration difficult. In environments with dozens of applications and platforms, mapping out the exact access needs of each role can quickly become overwhelming.
There’s also human resistance. Teams accustomed to broad access may push back against perceived limitations. Without strong communication and clear policies, these transitions can feel like a step backward.
To address these challenges, organizations should combine policy updates with training, use automation tools to simplify access reviews and take a phased approach to implementation.
- Old systems: Hard to limit access if the tools don’t support it.
- Too many tools: Complex setups make access harder to manage.
- People push back: Some may resist change if they’re used to open access.
Benefits of Least Privilege in an Enterprise Environment
Applying the Principle of Least Privilege doesn't just reduce risk; it improves the overall health and efficiency of your organization. By minimizing unnecessary access, companies can stop malware from spreading across systems if a breach occurs. Limiting permissions also reduces the chances of human error or insider threats causing major disruptions.
From a compliance standpoint, least privilege makes audit preparation much smoother. When access is well-documented and clearly justified, audits become less stressful and more transparent. Additionally, it prevents privilege creep, the gradual build-up of access rights over time which is often a hidden source of security gaps.
For the IT team, PoLP translates into fewer support tickets, cleaner access logs, and more time to focus on strategic tasks. In essence, applying least privilege helps businesses work smarter, stay compliant, and build more resilient digital operations.
- Controls the spread of malware by identifying the potential threat footprint and restricting its actions.
- Limits insider threat potential by limiting the potential for accidental or malicious misuse of information.
- Streamlines audit readiness by providing traceable, role-based access and use controls.
- Increases productivity by reducing risk and IT overhead associated with access.
- Strengthens governance and decreases security exceptions across the board.
Principle of Least Privilege in Cloud and Modern IT Environments
Today’s IT environments are complex, with users operating across cloud platforms, SaaS tools, and hybrid infrastructures. Least privilege plays a foundational role in this context.
In cloud-native systems, PoLP works through identity-based access controls that integrate with platforms like AWS, Azure, and GCP. These platforms allow policies to be applied dynamically, depending on the user’s role, time of access, or even location.
Automation and alerts further support the model, enabling real-time responses to abnormal access behavior. For DevOps teams, limiting access to container configurations or deployment pipelines prevents costly errors or malicious changes.
In essence, PoLP scales with modern infrastructure when supported by the right identity governance and monitoring tools.
- Works with identity-based access
- Pairs well with automation and alerts
- Used in cloud, DevOps, and SaaS environments.
PoLP and Compliance
Organizations in regulated industries must adhere to strict compliance standards and PoLP directly supports these requirements by ensuring access is both minimal and auditable.
HIPAA: The Health Insurance Portability and Accountability Act mandates that healthcare data access is strictly limited to authorized individuals. PoLP helps organizations implement role-based access for patient records, reducing the risk of unauthorized exposure.
SOX: Under the Sarbanes-Oxley Act, organizations must maintain detailed logs showing who accessed financial systems and when. PoLP ensures access to financial data is tightly controlled and traceable, supporting both integrity and accountability.
GDPR: The General Data Protection Regulation enforces strict guidelines on data minimization and access control. PoLP aligns with GDPR by limiting access to personal data based on role and need, ensuring that only authorized personnel can handle sensitive information.
By embedding least privilege principles into access control policies, companies not only improve security but also simplify their path to regulatory compliance.
Conclusion | Simplify User Access with Identity Confluence
The Principle of Least Privilege isn’t just a technical best practice, it’s a mindset shift toward smarter, safer access. By giving people only what they need, when they need it, organizations can reduce risk, simplify audits, and build a stronger foundation for long-term security and compliance.
If your team is still managing access manually or using outdated controls, now’s the time to rethink your approach.
Identity Governance and Administration (IGA) solutions like Tech Prescient’s Identity Confluence offer automated access control, RBAC, and just-in-time provisioning.
Frequently Asked Questions (FAQs)
Q: What is privilege creep and why is it risky?
A: It happens when users gradually accumulate access permissions they no longer need. Over time, this can create serious security vulnerabilities, as excessive privileges increase the likelihood of data breaches or internal misuse. Regular access reviews help reduce this risk.Q: How often should access privileges be reviewed?
A: Access rights should be reviewed on a quarterly basis or when there are major changes to their role. Regular reviews are important to validate that users only have the access they require at the moment, and to deter privilege creep.Q: Can PoLP slow down productivity?
A: Not if implemented correctly. Policy of least privilege (PoLP), with automation and role-based access control, not only allows users to get what they need in a timely manner, but does so by mitigating the risks associated with open-ended access.Q: Why does PoLP matter in today’s cybersecurity landscape?
A: PoLP is important because many modern attacks start with someone having too many rights. By ensuring that users have the rights they need and nothing more, organizations are minimizing the chance of internal misuse and external compromise. PoLP is a first line of defense in cloud, hybrid, and remote-first enterprises.Q: Can PoLP be applied to both people and systems?
A: Absolutely. PoLP is not only for users, it applies to applications, scripts, APIs, and service accounts too. Every digital identity in your environment should follow least privilege principles to help limit unintended consequences.Q: What’s the biggest mistake companies make when applying PoLP?
A: The most common mistake is treating it as a one-time setup. In reality, PoLP is a continuous monitoring, review, and updating process to account for changes in user roles, applications and risk levels.Q: How is PoLP enforced in a dynamic environment like the cloud?
A: The principle of least privilege (PoLP) is often implemented in cloud environments through identity-based access or authentication control, policy automation and real-time monitoring capabilities. Role-Based Access Control (RBAC), Attribute-Based Access Control (ABAC), and Just-in-Time (JIT) access are all core components of effective cloud-based PoLP implementation.Q: What’s a simple way to get started with PoLP?
A: Start by auditing your current access permissions. Map those permissions to job functions, and get rid of the excess access based on that data, and define permissions that are role-based. This helps eliminate over-privileged user issues, and tools like Tech Prescient's Identity Confluence, provide automated help with governance workflows.