
User Access Management (UAM): Guide & Best Practices 2026


User Access Management (UAM) is a key pillar of modern identity security. UAM is the discipline of defining, managing, monitoring, and revoking access, so that users, whether employees, contractors, or partners, have the appropriate permissions to do their job. Users' lifecycles should be managed from recruitment to offboarding. User Access Management plays a critical role in helping minimize the risk of over-permissioning, reducing the attack surface, and ensuring sensitive data, applications, and systems are tightly controlled.
The significance of UAM has never been more relevant. As per a report by Check Point, credential theft grew by 160% year-over-year, which led to credential theft now accounting for 20% of all data breaches. In a hybrid and multi-cloud context, where users would interact with hundreds of SaaS applications and infrastructure services, using static roles and passwords is no longer possible. Without frictionless User Access Management, organizations face potential encounters with privilege creep, orphan accounts, insider misuse, and expensive regulatory fines.
In this blog, we will walk you through everything about UAM, including: what UAM is, why it matters, important components, types of UAM, UAM best practices, and mistakes to avoid.
Key Takeaways:
- UAM controls permissions across all stages of the user lifecycle - onboarding to offboarding (and role changes in between).
- Addresses orphan accounts and privilege creep, greatly reducing the impact of insider breaches.
- Provides audit-ready controls to support compliance with frameworks such as ISO 27001, SOC 2, HIPAA, PCI DSS, and SOX.
- Automates provisioning, deprovisioning, and access reviews, creating some distance from manual efforts, which can introduce errors and delay.
- It fits into the bigger picture of IAM and balances security, compliance, and user experience.
What is User Access Management?
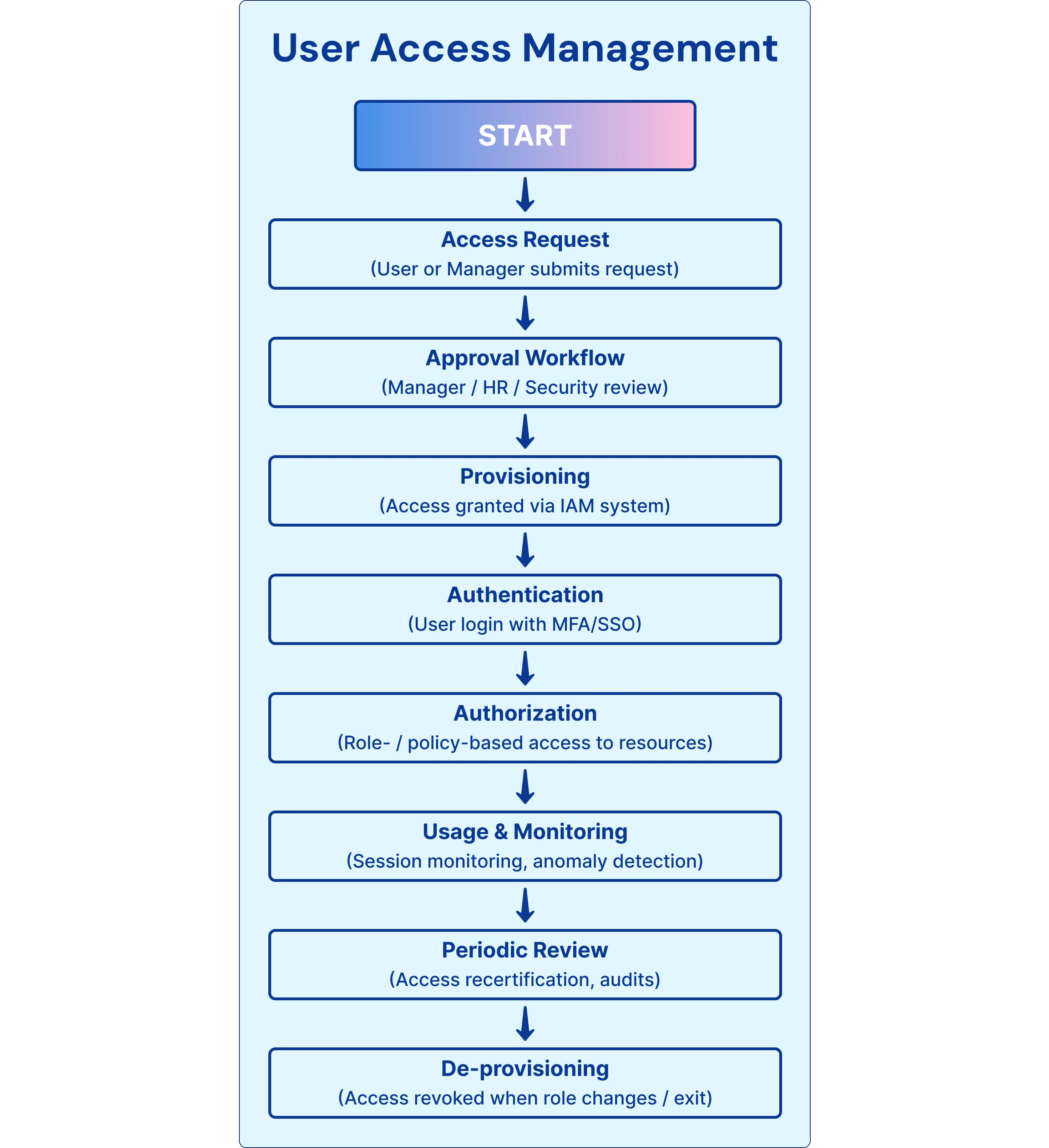
User Access Management (UAM) provides an extensive framework to regulate and govern access privileges of users across enterprise systems, applications, and data. It incorporates the entire access lifecycle, from authenticating access to ongoing authorization and permission management.. In general, UAM answers three main questions:
- Who is the user?
- What can they access?
- When, or under what circumstances, is access granted or denied?
UAM, unlike a one-time permission grant, considers the entire user lifecycle - who the user is, when the user starts, what position they fill, and when they leave the company. Each of these times has to be actively controlled so that access is correct, secure, and in compliance.
At its core, UAM combines two key identity security functions:
- Authentication → is the verification that the user is who they say they are (via password, MFA, or biometrics) before a user is permitted to access a system.
- Authorization → establishes what systems, files, or applications the authenticated user can access and what actions of those resources the user is authorized to perform.
Expanding on these functions, UAM also includes:
- Provisioning & Deprovisioning → The ability to assign access when a user is onboarded, and revoke it immediately upon separation.
- Ongoing Access Reviews → Routine checks to ensure users' access still supports their job responsibilities.
- Policies Enforcement → Applying the principles of least privilege and separation of duties to minimize risk.
- Auditing & Reporting → Keeping an accurate, auditable record of who had access to what, when, and why.
This makes UAM go beyond just technical control, but a governance framework to protect digital assets while allowing the business to be productive.
Why is User Access Management Important?
User Access Management is not just an IT function; it enables better business. If implemented properly, UAM reduces risks, guarantees compliance, and provides a privacy-versus-productivity balance. The following are the specific reasons why UAM is important in the year 2025:
1. Security:
The most significant and critical benefit of UAM is security. Organizations today maintain thousands of users-employees, contractors, vendors, and partners. Each type of user requires access to different systems. Without UAM, accounts can either be over-permissioned, remain active after employees have departed, or be prone to insider threats.
From a security perspective, unauthorized access is one of the primary causes for breaches. IBM’s Cost of a Data Breach Report 2025 states that stolen or compromised credentials were the first attack vector, with an average breach cost of $4.62 million.
UAM can help prevent this kind of behavior through strong authentication, privileged accounts monitoring, and revoking access in real-time. By identifying and closing these areas of their security, User Access Management would be able to mitigate the probability and severity of breaches.
2. Compliance:
All organizations are responsible for complying with frameworks like ISO 27001, SOC 2, HIPAA, PCI DSS, and SOX. As a general theme, all frameworks require some form of controlled, auditable access. For example-
- HIPAA requires healthcare organizations to have unique user IDs and logs to ensure that access was made.
- PCI DSS requires that only authorized users with a business reason can access cardholder data, and importantly, those actions are logged.
- SOX specifies strict control for financial systems access.
UAM provides the framework to be compliant, while it provides automated access reviews, with complete logs, and audit-ready evidence. UAM is a solution that can help avoid fines while establishing confidence with regulators, partners, and customers.
3. Least Privilege:
The principle of least privilege is fundamental to UAM, which involves providing users with only the necessary amount of access required to perform their duties. This leaves both users and organizations less risk of unauthorized access, privilege misuse, and further data breaches by minimizing erroneous permissions access, while still restricting access based on business needs.
- Avoiding UAM will create permission creep. A user goes from Sales to Human Resources (HR), and still has access to Sales unless reviewed.
- Privileged accounts have the potential to be dangerous if never reviewed, because they can bypass security controls.
UAM enforces least privilege, and to achieve it, removes or changes access as user role changes, removing any unnecessary access, and requests the highest level of access restrictions through Privileged Access Management (PAM).
4. Auditability:
When compliance auditors, or security investigators, ask "Who accessed this system; when; and why?", UAM delivers the evidence through reports and logs. By regularly conducting access reviews and audits, organizations can show that user permissions really map and align to business needs and security policies. Discrepancies or access violations can be identified and remediated, all while remaining compliant and secure.
- Centralized logs capture all user activities from login attempts to their access of files.
- Access reviews document whether users have permissions to carry out job responsibilities.
- Automated Reporting provides a clear chain of evidence, reducing auditors' efforts to pull information manually.
These properties of auditability produce accountability in the organization. Each action represents a verified identity milestone, deterring its misuse/abuse, and enables the organization to conduct any investigations quickly when incidents occur.
5. Operational Efficiency:
In addition to security and compliance benefits, UAM offers enhanced business productivity. Manual access processes are slow, prone to errors, and frustrating for employees.
- Automated provisioning ensures new hires have the right tools on Day 1.
- Self-service access requests reduce the burden on IT while the approval workflow still addresses the requirement of their approval.
- Automated deprovisioning ensures access is instantaneously revoked when users leave a company, and gaps are not left in the protection of the company.
By removing repetitive manual processes, UAM enables IT teams to spend resources on higher-value work and allows employees to obtain what they need sooner and more securely.
Key Components of User Access Management
User Access Management (UAM) is built around a set of foundational components that work together to secure access, enforce least privilege, and demonstrate compliance. All components focus on a different stage of the access lifecycle, ranging from authentication to auditing, which allows organizations to protect data while allowing for better operational efficiencies.
1. Authentication:
Authentication is the first line of defense in User Access Management (UAM) and allows organizations to verify that a user is who they say they are before granting access to systems or applications. The traditional approach to verification is a username and a password. However, with incidents of phishing and credential theft increasing, today increasingly incorporate multi-factor authentication (MFA) & adaptive MFA, biometrics (fingerprint and facial recognition), and hardware tokens. If organizations can fortify the first layer, they can prevent unauthorized actors from having the opportunity to enter the system in the first place.
2. Authorization:
After a user is authenticated, authorization determines what resources a user is authorized to access and what they are authorized to do. Authorization is accomplished through the principle of least privilege, allowing users only the rights required to do their job based on the user’s role, group membership, or specific permissions assigned to them. Authorization can either be accomplished through specific models, such as Role-Based Access Control (RBAC), which maps a permission set to job functions, or through Attribute-Based Access Control (ABAC), which considers many conditional aspects, such as location, device, or department. If an organization does not have a strong authorization process, privilege creep occurs and excessive access rights can accumulate, leading to security gaps.
3. Permissions Management:
Permissions management, which is closely related to authorization, specifies what operations a user is authorized to perform within a system or application, e.g., read, write, delete, and execute. Good permissions management practices enable organizations to enforce the fine-grained access control they need to limit unnecessary access while still allowing users to perform their jobs. Poor permissions management generally results in the user permissions being either inconsistent or overly permissive, often exposing sensitive resources.
4. Access Control Lists (ACLs)
Another core component of UAM is Access Control Lists (ACLs). ACLs are resource-specific permissions that explicitly outline which users/groups can access a system or dataset, and specifically, at what level. For example, in the financial database, the finance team may have permission to read and update records, but only the administration group may have permission to delete records. ACLs allow for very fine-grained permission specification; however, in large, diverse environments, ACLs can become very complex very quickly. ACLs work best when used with an overarching model such as RBAC or ABAC.
5. User Provisioning and Deprovisioning:
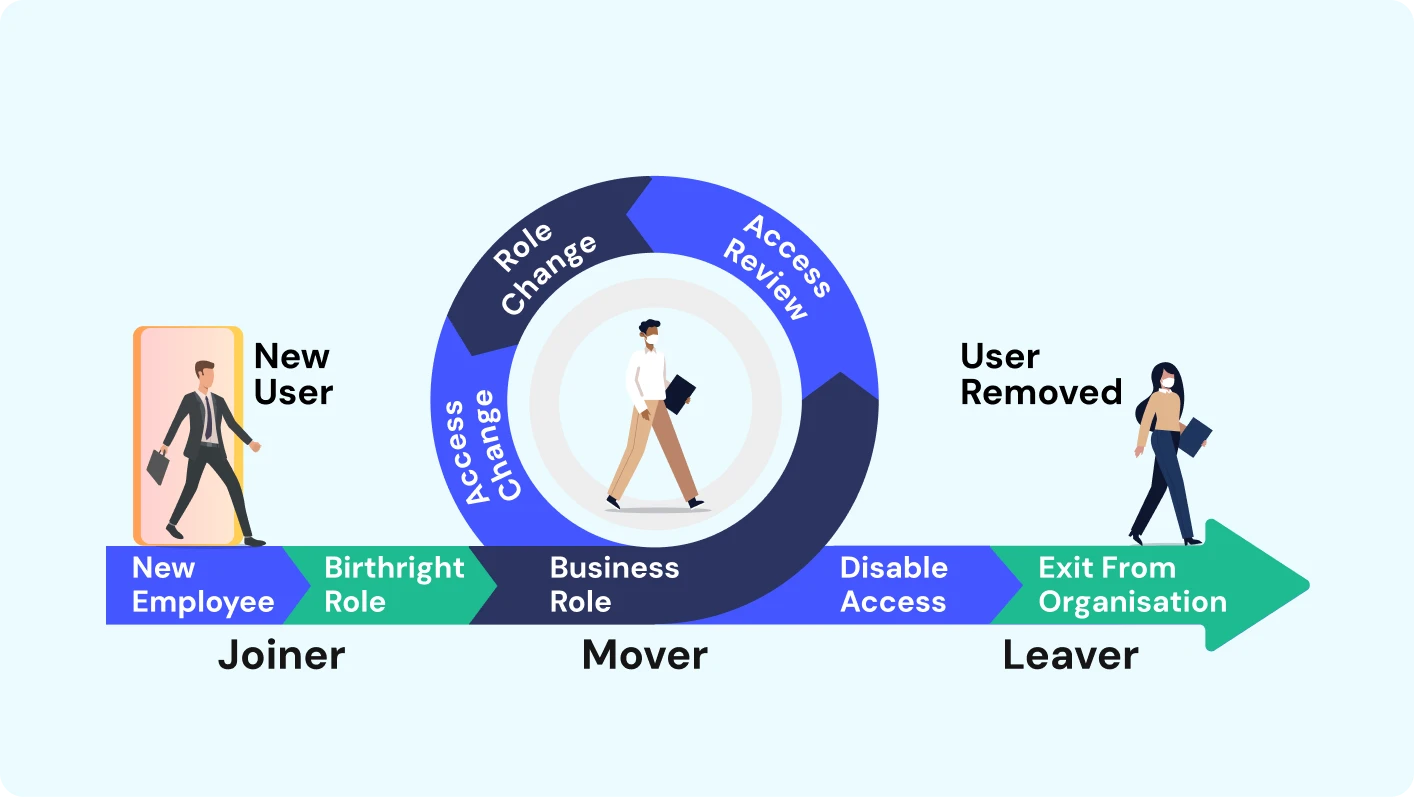
User provisioning and deprovisioning are equally important, controlling access throughout the Joiner-Mover-Leaver (JML) life cycle. This refers to the process of creating, modifying, and deleting user accounts and their associated access rights within an organization. Provisioning guarantees that when an employee joins or changes roles, they are given reasonable access without delay. Deprovisioning guarantees access is efficiently removed the moment someone leaves or no longer needs access to particular resources. Automating these processes helps to reduce errors, eliminate orphan accounts, and close the common backdoors exploited by attackers.
6. Single Sign-On:
To help with security and the user experience process, many organizations adopt Single Sign-On (SSO), which allows a user to authenticate once and then gain access to a number of applications and systems without needing to re-enter credentials. SSO also helps reduce password fatigue, eliminate credential reuse, and provide a simplified access management mechanism across hybrid and multi-cloud environments. When used with MFA, SSO offers convenience and security at the right level.
7. Auditing and Compliance:
No UAM framework is complete without auditing and compliance. Recording user activity, tracking permission changes, and recording a detailed audit trail are required to be able to identify suspicious activity and provide assurance of compliance standards like ISO 27001, SOC 2, PCI DSS, HIPAA, and SOX. These records will also help going through audits for compliance, incident response, and continuous improvement.
Types of User Access Management
User Access Management is not a one-size-fits-all practice. They are engaged with managing access appropriately, as either internal users from within the organization or external users outside the organization. Both internal and external users require a different approach and technology to manage access in a secure, efficient, and compliant manner.
Internal User Access Management
Internal access management refers to the monitoring of employee, administrator, and executive access from within the organization. The user roles mentioned above will often have various levels of access associated with their role. A junior employee will likely only require access to one SaaS tool, but an administrator can access any high-level critical infrastructure. Internal User Access Management incorporates accounts, privileges, access, password policies, Access Control Lists (ACLs), and Role-Based Access Control (Role-Based Access Control), which is considered the principle of least privilege.
For administrators and privileged users, additional protections like Privileged Access Management (PAM) will be important to effectively manage the threat of utilizing or compromising elevated qualified accounts. Internal User Access Management also provides monitoring and review of the access levels for all users regularly to minimize the risk of privilege creep, orphaned accounts, insider threats, etc.
Example: In hospitals, three groups of workers typically need access to various systems: clinicians, HR staff, and administrators. Clinicians need supervised access to EHRs but not to payroll, while HR staff need access to payroll but not patient records. Administrators who have responsibility for the hospital IT will have wide-ranging capabilities, but only with a monitored privileged account.
External User Access Management
External User Access Management enables access for individuals who are not part of the organization, e.g., customers using a digital platform, vendors connecting to enterprise systems, and business partners working on shared projects. Unlike internal users, the access assets requested by external users are typically finite and for a much more defined purpose.
External UAM utilizes technologies like Single Sign-On (SSO), Access Control Lists (ACLs), and role-based rules to facilitate secure and frictionless access. Strong identity verification, multi-factor authentication, and federation protocols (like SAML or OAuth) are often employed to minimize friction while enabling security. External UAM is especially important in industries that manage sensitive customer information, where security directly affects trust and brand reputation.
Example: A financial services company provides its customers with seamless access to secure online banking through a single sign-on portal, while vendors providing IT support will have a defined timeframe to use limited access on select systems. This provides a seamless experience for customers and restricts vendor access to only the limited resources needed to perform their role.
Setting Up User Access Management
Implementing User Access Management (UAM) effectively requires a structured approach that balances security, compliance, and usability. Following are the steps you can take to implement UAM:
Step 1: Policies and Procedures
The first step in developing a UAM framework is to develop policies and procedures. The policies should identify who has the authority to approve access, how access requests are submitted, and what conditions can be met before access is revoked. Identify ownership for IT, HR, and security matters to avoid ownership confusion. The procedures are the ‘rules of engagement’ for all actions related to access. Having a solid policy helps create consistency and, above all, limits the probability of ad-hoc access decisions that may pose a risk.
Step 2: Develop Access Levels
After the policies and procedures are developed, the next step is to create access levels based on the importance of the resources. Access levels are the authorities of a user (or device, program, or process) to access a particular resource. Access levels can vary for a resource depending on how sensitive the resource is. The access levels could range from read-only access, read-write access, or full access to modify or delete the resource. Systems have varying degrees of risk. Host sensitive databases, financial information, and patient information should be tightly controlled, while more general collaboration systems can probably be managed with fewer controls. Create controls that apply the principle of least privilege using techniques such as Access Control Lists (ACLS) or Role-Based Access Controls (RBAC) to ensure users are only accessing what they truly need, while minimizing the attack surface.
Step 3: Define User Roles
You can also set user roles instead of assigning permissions individually. Roles are used to group users according to their duties and authorizations in an organization. For example, position titles may say "sales" manager, "accounting" manager, or "IT" administrator. Each user role will have pre-defined access rights assigned in accordance with their job function. Having defined user roles streamlines user onboarding and privately assigns them a position for their entire career, so they won't accidentally violate policy when they switch departments. Defined user roles are also better prepared for audits and allow organisations to see where their access rights are, since they are assigned consistently.
Step 4: Automate Access
You can implement IAM/IGA platforms like Identity Confluence by Tech Prescient to automate provisioning and deprovisioning when employees are onboarded, compartmentalized into different roles, or exit the organization. Automation minimizes human error, prevents orphaned accounts, and enforces approvals. Moving access requests to self-service with approvals from managers improves efficiency without compromising governance. Also, integrating automation into an HR system means that access changes for role changes can be made immediately at the time of announcement.
Step 5: Monitor & Audit
You should implement continuous monitoring of login activities, privilege escalations, and dormant accounts. As a best practice, access reviews should be conducted regularly to determine whether employees, contractors, and vendors still require their access permissions. You should review audit processes regularly and tie compliance to an active compliance framework tonight, for example, ISO 27001, SOC 2, HIPAA, PCI DSS, so you have report-ready data for audits. A monitoring program is also used as an early warning system to detect unusual activity or user behavior that could signify suspicious, malicious, or risky activities are occurring.
Difference Between Identity Management and User Access Management
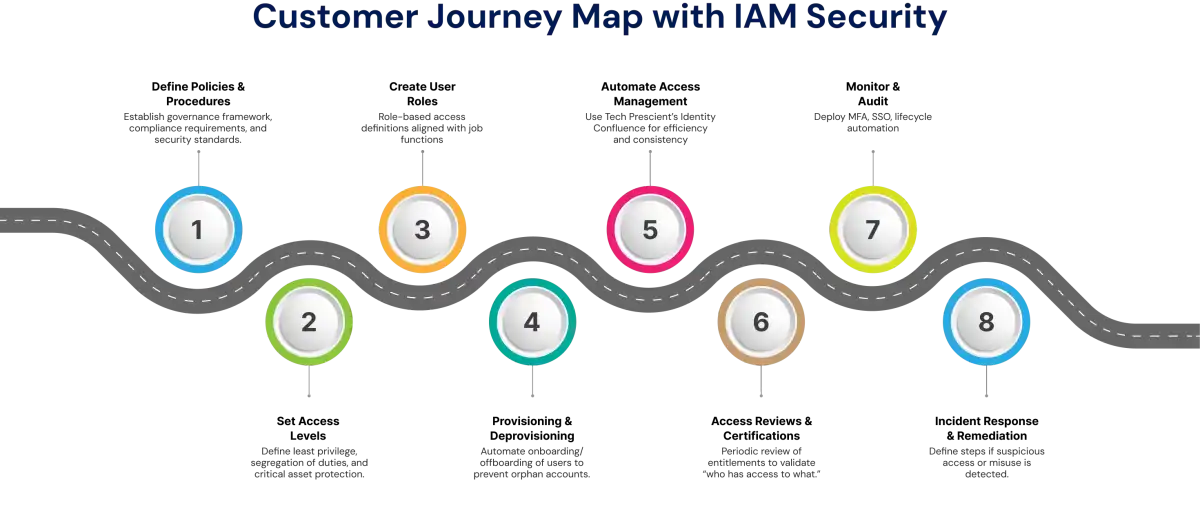
Identity Management (IDM) is very similar to User Access Management (UAM), but they are not the same. IDM deals with how to verify users and manage their identities, while UAM manages user access to information and resources based on those identities.
| Aspect | Identity Management (IDM) | User Access Management (UAM) |
|---|---|---|
| Scope | It's concerned with creating, maintaining, and validating digital identities for all users within an organization. | It governs what those users can do by assigning, controlling, and monitoring their permissions to resources. |
| Purpose | Confirm that a user is who they claim to be through authentication. | Decide what a verified user is allowed to access and under what conditions. |
| Focus | The focus is on user identity, authentication mechanisms, and secure credential management. | The focus is on authorization, access rights, role assignments, and lifecycle access governance. |
| Technologies | Common technologies include Single Sign-On (SSO), IAM platforms, and directory services like Active Directory or LDAP. | Common technologies include Role-Based Access Control (RBAC), Attribute-Based Access Control (ABAC), privileged access management (PAM), and access review tools. |
| Lifecycle Coverage | IDM primarily manages onboarding, authentication, and identity synchronization across systems. | UAM extends this by managing provisioning, role changes, periodic access reviews, and timely deprovisioning. |
| Compliance Role | IDM helps meet compliance by ensuring strong identity proofing and secure login processes. | UAM supports compliance by providing audit trails, enforcing least privilege, and validating access during audits. |
| Security Outcomes | Reduces risks like credential theft, identity spoofing, or account compromise. | Prevents privilege creep, insider threats, and misuse of sensitive data. |
Key Benefits of User Access Management
Many organizations receive value from a strong User Access Management (UAM) framework to mitigate security risks, although UAM provides much more. User Access Management is not just about security; it helps organizations find the right balance of protection, compliance, and operational flexibility. A few of the benefits of UAM are:
1. Improved Security and Least Privilege
The most beneficial part of UAM is that it can enforce least privilege. By only allowing users to have the exact level of access they need for their role, organizations lower the risk of company data being compromised or misused and reduce the risk of privilege creep over time. A finance employee does not need access to engineering tools or HR systems; if they only work within the accounting applications, that should be all the access they need. UAM frameworks can ensure that user permissions are continuously reviewed and adjusted as needed over time to ensure users do not have more access than necessary to take action against the organization.
2. Audit and Compliance Ready
We continue to see stricter regulatory requirements, with an auditor’s assessment of evidence of compliance very much depending on how access controls were implemented. UAM gives organizations the necessary visibility and control over their users to meet their auditors’ demands with an audit trail of who has access to what, the date user's permissions were granted, and the processes used to review access. Evidence of compliance is significantly offloaded via UAM capabilities, no matter what audit an organization is subject to, whether it be retroactive access for their annual ISO 27001 or SOC 2 audit, non-disclosures for HIPAA in the health industry, or protecting payment data pursuant to PCI DSS. UAM also greatly reduces the manual work required to prepare for audits each year and ensures compliance can be maintained consistently over time without doing so much manual work.
3. Efficiency through Automation
Without automation, managing user access between dozens of applications for hundreds (or thousands) of users becomes a resource-draining exercise. UAM tools automate the heavy-lifting of key processes like provisioning new users, changing permissions or access when roles change, and deprovisioning accounts when employees leave. Doing this reduces IT burden and human error, but it also ensures access changes happen in minutes or hours instead of weeks, and can speed up onboarding so new employees can contribute on their first day.
4. Improved User Experience with SSO and RBAC
Security is often achieved at the "cost" of user convenience. UAM helps to alleviate these tensions. For example, Single Sign-On (SSO) gives employees or external users access to multiple systems with one secure login. This mitigates the security risk of password fatigue and reduces the number of login-related IT support tickets. Role-based access control (RBAC) makes life a little easier, too: rather than having to request access every time you want to use a new (or different) tool that has permissions automatically assigned by RBAC, you receive them consistently. Overall, UAM helps to create a smoother, more secure journey for users.
5. Continuous Alignment with Joiner-Mover-Leaver Lifecycle
The Joiner → Mover → Leaver (JML) model is at the core of successful User Access Management by making sure access rights can change based on every user's journey within an organization. This is how it happens:
1. Joiner: When a new employee, contractor, or partner joins, UAM provisions accounts and assigns the right permissions at that time. With automated provisioning, onboarding time is reduced, so new users can access the right systems on day one, if not at that time.
2. Mover: As employees move from one role, department, or project to another, UAM updates access rights to reflect those new roles, departments, or projects. Privilege creep is avoided by removing permissions from the previous role while only granting the necessary access to the new role or project.
3. Leaver: When a user leaves the organization or is no longer entitled to use those accounts, UAM provides immediate deprovisioning. By deprovisioning those credentials, disabling the accounts, and removing access to all systems, organizations can remove the possibility of an orphan account being exploited.
Taking this lifecycle approach allows for access to be in line with the needs of the business while also removing security risk and administrative burden.
Best Practices for User Access Management
Successfully executing User Access Management requires more than the applications; it takes a level of discipline to maintain access appropriately secure, efficient, and compliant. Below are some best practices that we recommend all organizations take:
1. Enforce the Principle of Least Privilege
Always assign a user the least amount of access needed to perform their job role. This can minimize the attack surface, avoid privilege creep, and make sure no user is granted unnecessary rights that can be exploited. For example, no marketing employee should have access to financial reporting unless necessary.
2. Adopt Role-Based & Attribute-Based Access
Access management practices should take advantage of access models such as Role-Based Access Control (RBAC) or Attribute-Based Access Control (ABAC). RBAC groups users by job function, making it simple to assign common permissions, while ABAC provides fine-grained access decisions based on an attribute provided by the user, such as location, device type, or department. The two can be combined into a flexible and scalable method.
3. Automate Provisioning & Deprovisioning
Managing accounts manually can be tedious and error-prone. Automating provisioning allows new starters to access the tools they need immediately. Furthermore, automating deprovisioning ensures that leavers have their accounts revoked quickly. Orphan accounts are eliminated, and management overhead is reduced.
4. Conduct Regular Access Reviews
Regularly conduct access reviews to check that users still need the permissions assigned to them. This is particularly critical for privileged accounts. Reviews should involve a manager or system owners who can approve, change, or revoke access based on business changes. Having reviews documented improves audit readiness.
5. Use Strong Authentication
Password authentication is no longer enough. Consider enhancing your UAM framework with Multi-Factor Authentication (MFA) combined with adaptive authentication, passkeys, or biometric factors for additional security. Enforcing MFA across critical applications means that, even if the credentials are compromised, the attacker has an additional hurdle.
Common Challenges and How to Overcome Them
Despite having robust UAM policies in place, organizations routinely face recurring challenges that undermine security and efficiency. Below are the most frequently encountered problems and solutions to resolve them:
1. Privilege Creep
As employees transition from role to role or move to different job duties temporarily, they also accumulate additional permissions to access systems, software, and data. All this surplus access contributes to "privilege creep". Though it's extremely rare for an average employee to exploit their privileges intentionally, it opens the door for their unsuspecting involvement in a security or compliance incident (whether intentional or not) or contributes to an additional insider threat.
The Solution: Reiterate least privilege by assigning rights when needed. Regular access reviews enable you to remove outdated permissions from employees. You can also strengthen this process by implementing automated role-based access controls using Identity Confluence by Tech Prescient.
2. Orphan Accounts
When an employee or contractor leaves, their accounts are tied to their identities, but their accounts are often not terminated immediately, creating an "orphan" account. Orphan accounts can provide a pathway for a bad actor to perpetrate a significant incident against an organization.
The Solution: Automate provisioning/deprovisioning for all users to ensure accounts are created when users are onboarded, are updated and maintained when they switch from one role to another, and are immediately disabled when they leave. Integration with HR systems allows for automated deprovisioning.
3. Compliance Pressure
Trying to maintain regulations like ISO 27001, HIPAA, or PCI DSS can be difficult to manage when logs and audit evidence are scattered throughout multiple systems.
The Solution: Have monitored audit logs in a centralized location along with automated reports for compliance. UAM tools that include audit features can make collecting evidence easier and also make passing audits more achievable.
4. Poor User Experience
Strong security controls can frustrate employees, causing them to bypass official systems using shadow IT, which increases overall risk through weakened security, compliance, and productivity.
The Solution: Increase usability by introducing Single Sign-On (SSO) authentication, Multi-Factor Authentication (MFA), and self-service password restoration & access requests. This achieves high levels of user experience while effectively preserving strong security controls.
5. Hybrid/Cloud Complexity
Access management across hybrid/multi-cloud environments is complicated and cumbersome since each system often has its own identity framework, leading to inconsistent policies and significant visibility/monitoring gaps.
The Solution: Centralize access management with Identity Access Management (IAM) or User Access Management (UAM) solutions that can integrate with on-premises and cloud-defined resources entirely. An identity fabric approach can achieve consistent policies governing access and a unified visibility across the entire ecosystem.
Compliance Standards that Require UARs
User Access Reviews (UARs) are not only a best practice, but they are also an expectation of regulators mapped against several compliance frameworks. Each of these frameworks expects organizations to routinely validate who has access to sensitive systems and data; while each uses slightly different wording, they all hit some common concepts of security, accountability, and patient safety.
- ISO 27001 -
ISO 27001 has a lot written about access control policies to protect information assets. Ongoing and, therefore, regular UARs will confirm that only authorized personnel have or retain access and compliance with continual risk management processes to uphold the concept of least privilege. - SOC 2 -
SOC 2 monitors internal controls around security and availability. Documented and auditable access reviews show organizations are actively governing permissions and upholding appropriate security controls in the organization. - HIPAA -
For healthcare providers, HIPAA regulations include strict access to Protected Health Information (PHI), which all healthcare providers are required to enforce. UARs are a measure to validate that only authorized clinicians and staff have access to sensitive patient information, thereby reducing the risks of unauthorized breaches, non-compliance fines, or penalty fees. - PCI DSS –
The PCI DSS mandates strong access control for financial institutions and merchants within cardholder data environments. Regular User Access Reviews (UARs) will help ensure access is offered only to those individuals with a legitimate business need. - GDPR –
GDPR mandates organizations to apply and deploy the data minimization principle. User Access Reviews (UARs) can help accomplish this by ensuring employees only access data for which they have a legitimate business purpose and reducing exposure to personal data unnecessarily. - SOX –
SOX requires access governance to have tight control over access to financial reporting systems. UARs can provide confidence that only appropriate roles have access to sensitive financial data and, therefore, limit the possibility of fraud or tampering with financial data.
Final Thoughts
User Access Management (UAM) has transitioned from a purely technical protection measure to a strategic foundation of organizational security and efficiency. The trend toward hybrid work, cloud platforms, and complex partner ecosystems has made having knowledge of who has access to what, and for how long, a mandatory function. This area of security has ramifications for business agility, regulatory compliance, and customer trust.
At Tech Prescient, we believe that the ideal UAM is the right balance of security and usability. It should provide access frameworks that are scalable within hybrid and cloud environments, provide streamlined integration with identity governance, and scale with changing regulatory requirements, all of this without slowing down your organization. Our capabilities are designed to establish a UAM function for your organization that goes beyond simply "checking the box" for compliance and more towards being proactive and risk-aware with your access management.
Next Steps
Ready to strengthen your access management strategy?
With Tech Prescient’s Identity Confluence, you can automate provisioning and deprovisioning, enforce least privilege, and simplify compliance — all without adding complexity.
Frequently Asked Questions (FAQs)
1. What tools are used for UAM?
Common tools for User Access Management are Identity Confluence, SailPoint, Saviynt, Okta, Microsoft Entra, Ping Identity, AWS IAM, and Azure RBAC. User Access Management tools help organizations automate provisioning, enforce least privilege, support SSO/MFA, and provide audit-ready access reports. The right tools usually depend on your IT ecosystem, cloud, or on-premises, as well as regulatory requirements.2. How often should access be reviewed?
Access reviews should be based on the sensitivity of the account. Privileged accounts (like administrators or service accounts) should be reviewed quarterly due to the heightened risk of access. User accounts can be reviewed semi-annually or annually, depending on compliance needs. Some organizations have adopted continuous review methods, set up with alerts, in order to identify risk faster.3. What is the difference between RBAC and ABAC in UAM?
An example of Access Control models is Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC). In RBAC, access to an organization’s resources is dependent on job roles (e.g., HR manager, finance analyst). RBAC is easy to manage, but can be inflexible if the number of roles grows. ABAC relies on attribute data to make an access decision based on parameters related to department, device type, or location. ABAC generally provides more flexibility, such as dynamic permissions and more granularity, especially in hybrid or cloud-first environments.4. What is user access management in IAM?
User Access Management (UAM) is a subset of Identity and Access Management (IAM) that delivers a systematic approach to granting, reviewing, and revoking the authorizations of users. IAM defines who the user is and authenticates them; however, UAM determines if they have the right level of access during the entire lifecycle of the user - onboarding, role changes, and offboarding.5. How do you audit user access?
Auditing user access includes logging receipt, reviewing entitlements, and validating permissions against policies or compliance standards. Best practices for user access audits are to ensure that access reviews are scheduled on the calendar - periodic, whether quarterly, annually, etc., automate wherever you can for reporting, and always monitor your privileged accounts. Using automated compliance reporting for tools like SailPoint or Saviynt may lessen the audit fatigue, but also provide evidence and demonstration digitally for your regulator.