Understanding Zero Trust Security: Key Principles, Benefits & How It Works

Ayushi Tiwari
15 min read
In today’s times traditional security is no longer enough. With the ever evolving remote work, cloud adoption, and cyber threats sharply on rise, companies need a security model that assumes nothing and verifies everything. Zero Trust security does exactly that. It’s a modern cybersecurity framework that marks every user, device, and application as untrusted until proven otherwise. Instead of relying on network boundaries, Zero Trust puts on strict identity checks, ensure very limited privilege, and continuous validation of all devices, roles and individual accounts. All of this helps businesses stay secure in a dynamic, and digitally connected world.
Key Takeaways
- Zero Trust means never trust by default always verify user, device, and access.
- It limits lateral movement and minimizes the attack surface.
- Core principles include least privilege, continuous monitoring, and microsegmentation.
- Ideal for securing remote work, cloud apps, and third-party access.
- Scalable for businesses of all sizes not just large enterprises.
What Is Zero Trust Security?
Zero Trust security is a modern cybersecurity model that works on - Trust nothing. Verify everything. It basically nullifies the outdated approach of trusting every individual, resource or accounts inside the network. Whether a user is inside the office or logging in remotely, access is never granted automatically, without proper checks and authentication.
In traditional models, of organization where users inside the network were trusted by default, but on now Zero Trust assumes that threats can exist both outside and inside the network. This is crucial as once an attacker gets access of the system, traditional models often allowed them to move freely within the network and resources. Zero Trust changes that by requiring strict identity checks and access controls at every step.
Zero Trust Network Access, or ZTNA, ensures that users can only access specific applications and data they are authorized for, sometimes with some policies and boundations. This combined with techniques like microsegmentation, continuous authentication, and identity-based access, Zero Trust offers a more adaptive way to secure systems. It is not just a tool but a complete security framework that helps organizations stay protected in a constantly evolving digital environment.
Why Zero Trust Matters in 2025
A Zero Trust architecture is built on foundational principles that redefine how access is granted, monitored, and secured across modern IT environments. Unlike traditional security models that focus on protecting the perimeter, Zero Trust operates under the belief that no user or device should be trusted by default. Every interaction must be verified, controlled, and monitored to reduce risk and maintain strict security posture.
Below are the five key principles that define a robust Zero Trust framework.
- Cyber threats are smarter. Attackers are using AI-driven methods, phishing, and ransomware that bypass outdated defenses. Zero Trust helps stop threats early by verifying every request in real time.
- Cloud and hybrid environments are growing. Businesses now run across multiple platforms. Zero Trust creates consistent rules for access, no matter where the data lives.
- Protecting sensitive data is critical. With growing privacy regulations, companies need better controls. Zero Trust supports least privilege access and detailed monitoring to protect information.
- It limits the blast radius. Even if one part of your system is compromised, Zero Trust ensures the attacker cannot move freely within your network.
- Improved detection and response. Constant monitoring allows security teams to respond faster and more accurately to any suspicious activity.
- User experience gets better. Once identity and device trust are established, users can access what they need quickly without unnecessary barriers.
- Supports digital innovation. Zero Trust helps teams adopt new technologies while keeping security in place.
- Prepares your business for what’s next. As threats and technologies continue to evolve, Zero Trust offers a flexible and forward-looking way to stay secure.
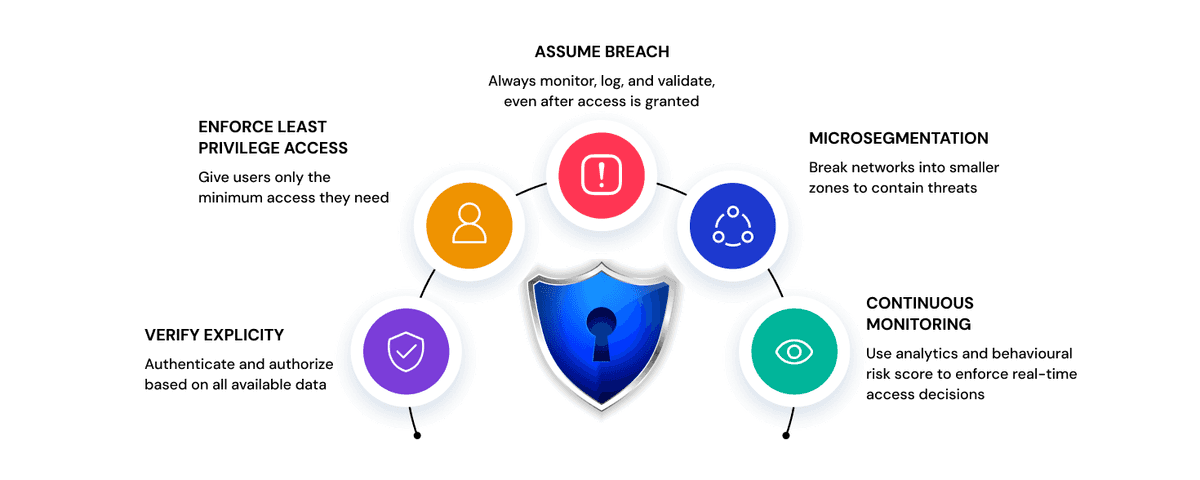
Core Principles of Zero Trust Architecture
Let’s break down the five core principles that make up a successful zero trust strategy.
1. Verify Explicitly
Every access request must be authenticated and authorized based on real-time data. This includes user identity, location, device health, and even behavioral context. Zero Trust replaces blind trust with data-backed decisions. To implement this, organizations should use tools like multi-factor authentication (MFA), single sign-on (SSO), and robust identity and access management (IAM) systems. These solutions help validate both human and non-human identities, ensuring that access is never based on assumptions.
2. Enforce Least Privilege Access
No user should have more access than they actually need. This is known as the least privilege principle, and it plays a critical role in limiting the potential damage from a compromised account. Whether it's a senior executive or a temporary contractor, access should be tailored to their specific role and responsibilities. Fine-grained access control ensures that users can only reach the applications or data required to do their job nothing more.
3. Assume Breach
Zero Trust assumes that breaches are inevitable, so it is built to contain and minimize their impact. Even after access is granted, systems should log activity, validate user behavior, and monitor for any signs of malicious intent. By shifting from a reactive to a proactive security posture, organizations can detect unusual patterns early and respond faster to threats. This principle aligns closely with continuous authentication and real-time risk assessment.
4. Microsegmentation
Microsegmentation involves dividing the network into smaller zones so that even if a threat actor gets in, they cannot move freely across systems. Each zone has its own set of access rules, making lateral movement significantly harder for attackers. By isolating workloads and applications, microsegmentation adds a powerful layer of defense and limits the exposure of critical assets.
5. Continuous Monitoring
Security in a Zero Trust environment is not a one-time check. It requires continuous monitoring of user activity, device posture, and network traffic. This includes using tools for behavioral analytics, risk scoring, and real-time alerting. With a strong monitoring system in place, organizations can adapt access controls instantly and block suspicious activity before it becomes a threat.
Zero Trust vs Traditional Security Models
The shift from perimeter-based security to Zero Trust architecture marks a major change in how organizations approach cybersecurity. While traditional models focus on building a strong outer defense, they often fail once that perimeter is breached. Zero Trust, on the other hand, is built on the assumption that threats can come from anywhere inside or outside the network.
Feature | Traditional Perimeter Security | Zero Trust Security Model |
|---|---|---|
Trust Model | Trust is granted to users inside the network | No implicit trust. Every request must be verified |
Network Perimeter | Strong focus on securing the outer boundary | Perimeter is irrelevant. Focus is on identity and context |
Access Control | Broad access within the network once a user is inside | Strict identity-based access for each application or resource |
User Verification | One-time authentication at login | Continuous verification of identity, device, and context |
Lateral Movement Risk | High. Once inside, attackers can move across systems | Minimal. Microsegmentation and access control limit lateral movement |
Response to Breach | Reactive. Focus on detecting after the breach | Proactive. Designed to limit breach impact from the start |
Visibility and Monitoring | Limited visibility across all users and devices | Continuous monitoring and behavioral analytics |
Device Trust | Often not verified after initial login | Ongoing checks for device health and posture |
Data Protection | Data is protected primarily at the perimeter | Data is protected at every access point and user interaction |
Scalability in Cloud Environments | Struggles to adapt to hybrid and multi-cloud setups | Built to support cloud-native, hybrid, and remote environments |
Zero Trust Use Cases
As organizations continue to adapt to hybrid work models, cloud-first strategies, and growing digital ecosystems, Zero Trust security offers practical solutions to some of the most pressing cybersecurity challenges. Its flexible design allows it to be implemented across multiple environments and industries, making it an essential part of a modern security framework.
Here are some of the most impactful use cases where Zero Trust helps organizations strengthen their security posture:
- Remote Workforce Access to Sensitive Applications With employees working from various locations and devices, traditional perimeter security fails to offer adequate protection. Zero Trust network access (ZTNA) ensures that only verified users and trusted devices can access specific business applications, regardless of where they are connecting from. This reduces unauthorized access risks and secures corporate data across distributed teams.
- Privileged Access Control Accounts with elevated access are prime targets for cyber attackers. Zero Trust enforces strict verification for all privileged actions, ensuring that even admin-level users are granted access only after continuous identity and context checks. By applying the least privilege principle, it limits what users can access and what actions they can take, reducing the blast radius in case of compromise.
- Securing Cloud Environments As workloads and data shift to the cloud, consistent and adaptive access controls become essential. Zero Trust architecture provides protection across multi-cloud and hybrid environments by verifying every access request and enforcing identity-based policies. This prevents unauthorized lateral movement and keeps cloud resources secure at all times.
- Protection from Ransomware and Insider Threats Zero Trust helps mitigate the risk of ransomware attacks by restricting access paths and monitoring user behavior in real time. It also reduces the potential for insider threats by ensuring users can only interact with the data and systems necessary for their roles. Microsegmentation and continuous authentication add extra layers of control, helping detect and block suspicious activity before it escalates.
- Third-Party and Vendor Access Management Vendors, contractors, and third-party collaborators often need temporary or limited access to internal systems. Zero Trust enables organizations to manage these connections securely by creating time-bound, role-specific access policies. Every access attempt is logged and monitored, providing transparency and control without sacrificing productivity.
Steps to Implement Zero Trust in Your Organization
Adopting a Zero Trust security model requires more than just new tools—it demands a shift in how access, users, and data are managed across the enterprise. The process is not one-size-fits-all, but following a structured roadmap can help organizations implement Zero Trust effectively and efficiently.
Here are the key steps to guide your Zero Trust implementation:
1. Identify Critical Assets and Users
Start by creating an inventory of all digital assets, including cloud applications, on-premise systems, user groups, and data repositories. Determine which assets are most sensitive or business-critical and identify the users who interact with them. Understanding what needs to be protected is the foundation of a Zero Trust approach.
2. Map Current Access Flows
Analyze how users, devices, and applications currently interact with systems and data. This includes identifying who accesses what, under what conditions, and from which locations or devices. Mapping these access flows helps detect risky patterns, gaps in control, and potential areas for policy refinement.
3. Deploy Identity-Based Authentication (MFA, SSO)
Implement robust identity and access management (IAM) controls that verify users and devices before granting access. Use multi-factor authentication (MFA) to add another layer of security, and integrate single sign-on (SSO) to streamline and secure user access across applications. This ensures only verified identities gain access, based on contextual factors like device health and user behavior.
4. Segment Networks and Isolate Resources
Use microsegmentation to divide your network into smaller, isolated zones with distinct access rules. By doing so, even if a threat actor breaches one segment, they are restricted from moving across the environment. Isolating high-value assets and applying specific security controls to each segment significantly limits the impact of any intrusion.
5. Monitor Continuously with Risk-Based Analytics
Real-time visibility is key in a Zero Trust environment. Continuously monitor user activity, device posture, and network traffic using behavioral analytics and risk scoring. This allows for adaptive access decisions and fast response to unusual behavior. Constant monitoring helps detect potential threats early and strengthens the security posture over time.
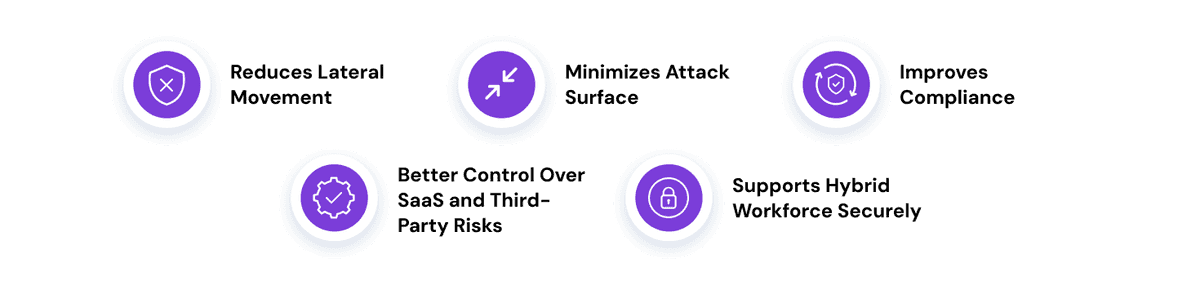
Benefits of a Zero Trust Security Model
Implementing a Zero Trust security model offers far more than just improved threat protection. It brings measurable advantages across security, operations, and user experience making it a strategic investment for modern organizations.
Here are the key benefits of adopting Zero Trust:
- Reduces Lateral Movement
Zero Trust assumes that threats can exist anywhere, even inside the network. By enforcing identity-based access and isolating workloads, it limits how far an attacker can move if they gain entry. This containment significantly reduces the risk of a widespread breach. - Minimizes the Attack Surface
By granting access based on strict verification and least privilege, Zero Trust minimizes the number of entry points exposed to attackers. Microsegmentation and continuous validation help ensure that only the right users access the right resources at the right time—nothing more, nothing less. - Improves Compliance
Whether it’s GDPR, HIPAA, SOX, or PCI DSS, regulatory frameworks demand strong access control and data protection. Zero Trust aligns with these requirements by offering granular visibility, access logs, and automated policy enforcement. This simplifies audit readiness and supports long-term compliance. - Better Control Over SaaS and Third-Party Risks
Organizations rely heavily on third-party vendors and cloud applications. Zero Trust helps manage this complexity by enabling strict access controls for external users and ensuring that SaaS applications are only accessible to verified identities. This reduces the risk posed by unmanaged or loosely governed connections. - Supports Hybrid Workforce Securely
With employees working across locations, devices, and networks, consistent security is essential. Zero Trust makes it possible to secure hybrid work environments by verifying every access request in real time no matter where the user is. It improves the end-user experience while maintaining high levels of control and visibility.
Our Approach to Zero Trust: Why Tech Prescient Solutions Work
At Tech Prescient, we don’t just talk about Zero Trust we help you implement it where it matters most. Our solution is built on the core principles of Zero Trust architecture and tailored to meet your unique business needs. Whether you're looking to secure remote workforces, reduce third-party access risk, or simplify cloud security, our platform gives you the control and visibility you need.
We combine identity-based access, risk-aware authentication, microsegmentation, and continuous monitoring to ensure that your environment remains secure, compliant, and agile. With Tech Prescient, Zero Trust is not just a framework it becomes a practical, scalable part of your cybersecurity strategy.
Book a Live Demo
See how Zero Trust looks in action
Experience firsthand how our platform delivers secure, real-time access control and visibility across users, apps, and data no matter where they are.
Frequently Asked Questions (FAQs)
- What is Zero Trust in simple terms?
Zero Trust is a security model that assumes no user or device should be trusted automatically. Every access request is verified based on identity, context, and device posture before access is granted.
- How is Zero Trust different from VPN or firewall-based models?
VPNs and firewalls protect the perimeter, assuming everything inside is safe. Zero Trust eliminates this assumption by verifying every access request continuously, even from within the network.
- Is Zero Trust only for large enterprises?
No. While larger organizations often lead adoption, Zero Trust principles can benefit businesses of all sizes by improving access control, reducing risk, and simplifying compliance.
- How long does it take to implement Zero Trust?
Implementation timelines vary depending on your current infrastructure and goals. Many organizations begin with core use cases like identity and access management, then expand over time.
- What tools are required for Zero Trust?
Key tools include identity and access management (IAM), multi-factor authentication (MFA), single sign-on (SSO), endpoint detection, ZTNA solutions, and continuous monitoring platforms.