Manual Monitoring Misses Risky Behavior
Security teams struggle to detect insider threats or misuse until it’s too late. Static rules and delayed reviews leave blind spots.
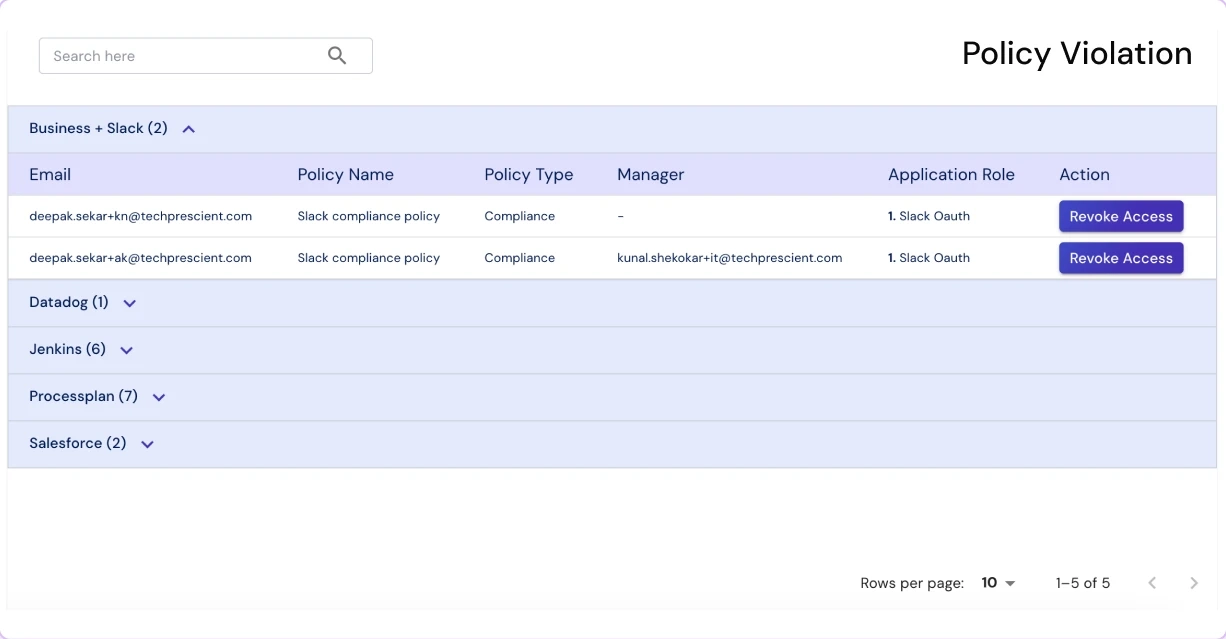
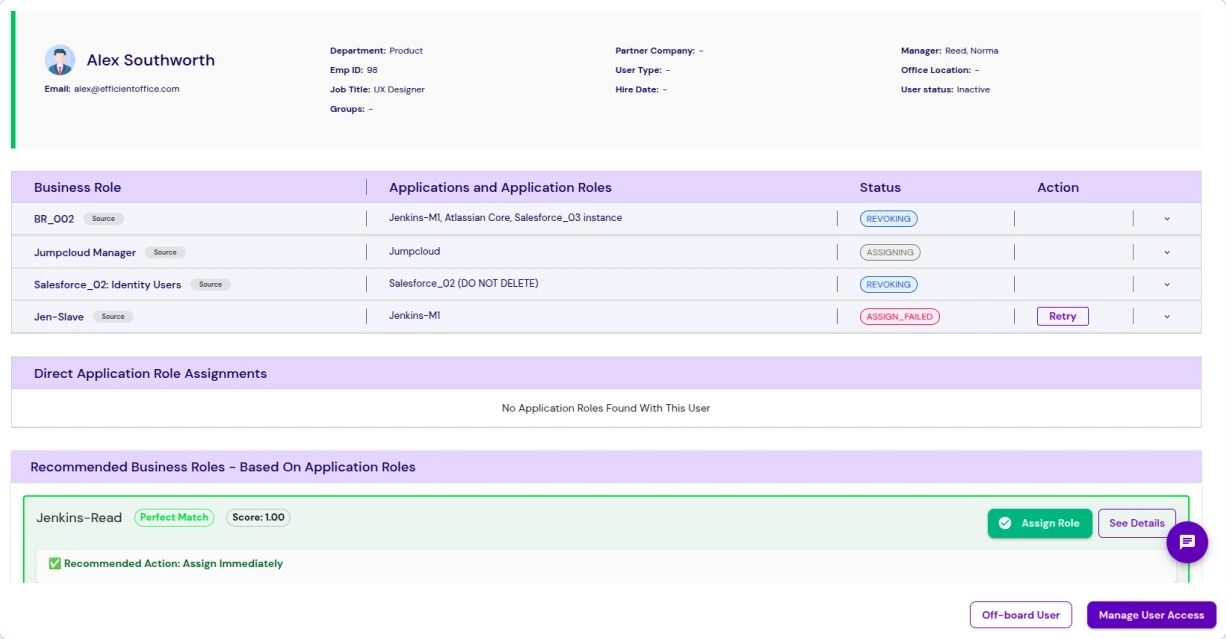
Identity Confluence addresses this challenge with behavioral risk scoring and real-time user activity monitoring. It proactively identifies unusual or high-risk behavior, prioritizes threats, triggers automated alerts, and initiates swift remediation workflows, closing the gap between detection and response.
Behavioral Risk Scoring Built for Identity Security
Proactively detect identity threats and prioritize response with context-aware risk scores and real-time alerts.
Anomaly Detection
Detects unusual login times, access patterns, and behavior deviations.
Risk Scoring
Assign dynamic risk scores based on context, frequency, and severity.
Automated Alerts
Trigger real-time notifications for high-risk actions or access anomalies.
Actionable Insights
Prioritize investigations with clear, time-stamped activity trails.
Identity Confluence Risk Monitoring Across the Lifecycle
From provisioning to de-provisioning, Identity Confluence continuously evaluates user behavior and flags risks. Integrated scoring helps security and compliance teams detect threats earlier, reduce false positives, and act decisively.