Uncover Access Risk Before It Becomes a Breach
Most organizations struggle to track and manage user access across fragmented systems. This creates hidden risks, audit fatigue, and non-compliance.
Identity Confluence solves this
with powerful User Access Mining, providing real-time visibility into all entitlements, helping you flag violations, reduce privilege sprawl, and generate audit-ready reports with just a click.
How Identity Confluence Simplifies Access Visibility and Audit Readiness
Gain centralized control, detect hidden risks, and generate audit-ready reports—all from one unified platform.

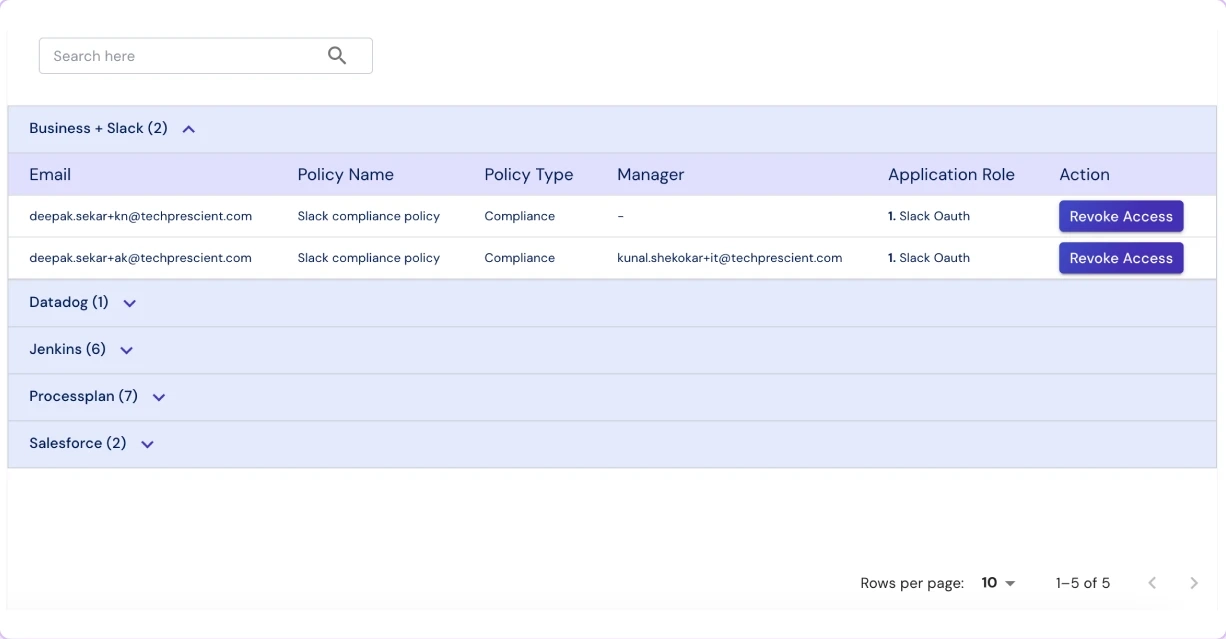
Unified Access Inventory
Get a single source of truth for access across applications, roles, and entitlements — updated in real time.

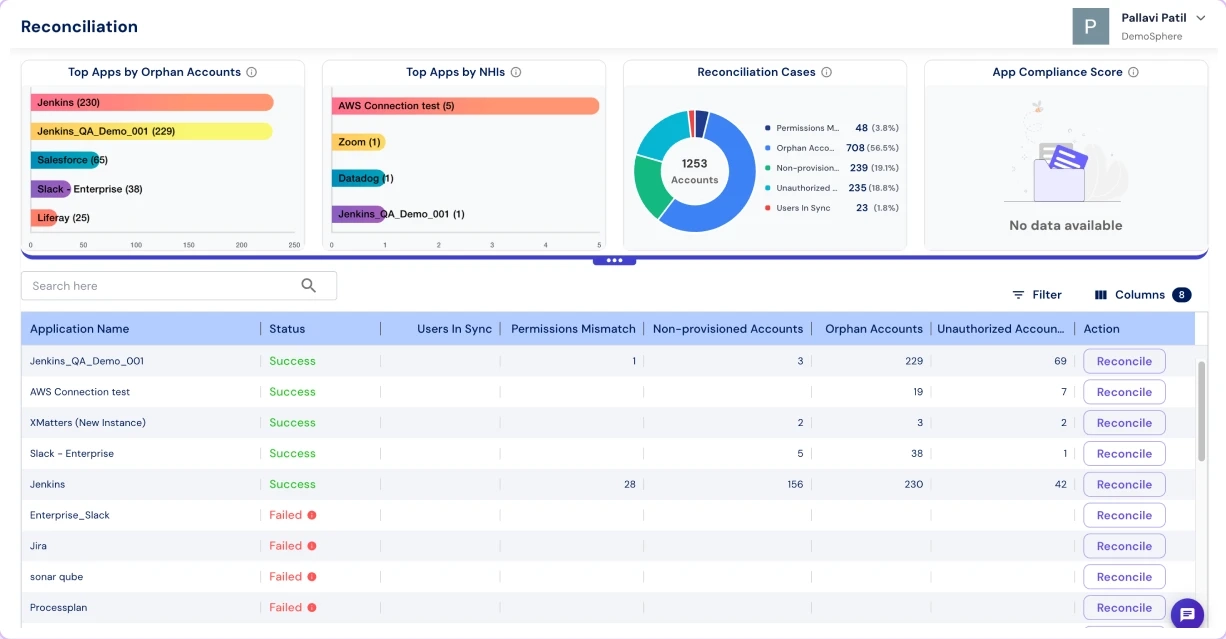
Access Risk & Anomaly Detection
Identify orphaned accounts, toxic access combinations, and excessive privileges in one dashboard.

Audit-Ready Reports
Export detailed access reports instantly for internal and external audits — in CSV, JSON, or custom formats.
Take Control of Access, Risk, and Compliance
Automate audits, detect SoD conflicts, and eliminate risky access—before it impacts your business
Audit Preparation
Generate certified, on-demand access reports for regulatory reviews.
SoD Violation Detection
Detect users with conflicting access in shared systems.
Risk Mitigation
Spot and remediate stale, orphaned, or misconfigured accounts across environments.
Boost Efficiency & Compliance Across Teams
Automate access workflows, ensure policy enforcement, and stay audit-ready—effortlessly and at scale
For IT Teams:
Eliminate manual tracking and access mapping
Integrate with existing identity, HR, and ticketing systems
Automate reporting and reduce overhead
For Security & Compliance Teams:
Detect and respond to SoD violations and policy breaches
Maintain continuous compliance with GDPR, HIPAA, SOX
Cut audit prep time by over 70%
70%
Enforce Consistent Role-Based Access (RBAC)
50%
reduction in manual reporting tasks
2x
improvement in compliance response accuracy
Why Identity
Confluence?
Unlike siloed tools, Identity Confluence provides real-time access intelligence across your entire identity ecosystem. Fully integrated into your IGA workflows, it enables context-aware decisions with zero guesswork.
Unlock deeper insights into your access landscape
Take the first step toward intelligent, risk-free access governance.
Trusted By The Industry's Best Organizations