
Top Cybersecurity Challenges in 2026

The cybersecurity landscape of 2025 grows more complex and multidimensional than at any previous point in history as digital transformation accelerates, while adversaries employ increasingly sophisticated methods. Organizations now find themselves facing multiple cybersecurity challenges at once: ever-more complex IT spaces with more attack vectors, critical shortages of skills in security teams, and an expanding labyrinth of compliance requirements. These challenges are making traditional security approaches less effective. Traditional security relied on strong network boundaries, but those boundaries are disappearing. As a result, ensuring the identity of the user has become the main focus of security, as we can no longer trust a user simply based on their network connection. With a continuous acceleration of cyber threats in scale, organizations must prepare for significant costs associated with breach recovery, damages to brand reputation and consumer trust, and potentially regulatory fines and consumer privacy lawsuits.
Key takeaways:
- Discover the top 4 emerging threats: AI-powered attacks, ransomware evolution, supply chain vulneraxbilities, and zero-day exploits
- Learn why human factors cause 82% of breaches and how to address skills gaps and insider threats
- Understand technological risks from IoT devices, cloud misconfigurations, and future quantum computing threats
- Navigate complex compliance requirements and shadow IT challenges
- Implement practical solutions: Zero Trust, security awareness training, and identity governance
Why Cybersecurity Challenges Are Growing
Cybersecurity challenges consist of the multifaceted and changing challenges organizations encounter when trying to secure their digital assets from unauthorized intrusion or attack. Cybersecurity challenges include technological threats, human behaviour, resource constraints, and compliance. Cyber adversaries continually adapt their tactics to gain access to computers to compromise organizational and personal systems, adapting more quickly than organizations can respond to their changes. The cybersecurity environment has changed considerably as the pace of digital acceleration has outstripped security achievements. According to the World Economic Forum's Global Risks Report 2024, cybersecurity failures now rank among the top five global risks by likelihood.
Three factors have combined to create this high-risk environment:
-
Infrastructure complexity: Modern enterprises operate across interconnected environments, including on-premises systems, multiple cloud providers, and remote work setups. This hybrid reality creates security blind spots at transition points between systems.
-
Sophisticated Threat Actors: Cybercriminals have become more organized and more efficient in conducting their attacks, taking advantage of automation and artificial intelligence to scale their activities. Through techniques such as Advanced Persistent Threats (APTs), the attacker or attacker group breaks into a network and may not be discovered until months or years have passed. In that time, they collect harvested data or disrupt responsibilities upstream or downstream. Criminal organizations have also adopted a specialization approach, where group members specialize in distinct phases of the attack. Bad actors have advanced beyond just encrypting files to now also threatening to expose sensitive information if demands are not met. These types of multistage phishing campaigns use the initial information to make subsequent and even higher-consequence attacks later on, which are further complicated by their timing and advanced threat vectors.
-
Shortage of Skilled Cybersecurity Professionals: Overall, the worldwide shortage of skilled, global cybersecurity professionals is an obstacle. As cyber threats are becoming more frequent and complex, there has been a greater need for cybersecurity professionals than ever before, but that demand has not and will not be satisfied by a corresponding supply of qualified professionals that can assist in mitigating the quality and ease with which attackers increase vulnerability towards organizations. This skills shortage is one reason that organizations have been struggling to have capability detection, response, and mitigation of cyber threats, because they may not be effectively able to manage the advanced security tools and strategies necessary for it.
This shift has changed identity governance, which is the method of managing appropriate access to resources, from an administrative function to a strategic security priority. With the disappearance of perimeters, determining who is accessing systems and whether that person should have access is now the key security question for organizations to answer.
Top Emerging Cybersecurity Threats in 2025
1. AI-Powered Attacks
AI-driven attacks leverage artificial intelligence technologies to increase the risk of cyber threats. They offer targeting, evasion, and automation potential. Such advanced attacks rely on machine learning to evaluate defence patterns, tailor scams to users' needs, and react in real time to security events.
AI has been used in defence in the security industry for a long time; however, 2025 marks an inflection point where offensive AI has fundamentally altered the threat landscape. The MIT Technology Review's State of AI 2024 report includes realization that AI-powered attacks (i.e., offensive AI) have increased 300% since 2023, and in particular, there are three significant types of threat:
- Context-aware phishing: While phishing in the past leveraged volume, the new AI-led phishing is based on precision. Language models can even 'understand' the behaviours and generate highly convincing messages related to real events of the organization, and can match the typical writing of known associated individuals and know when to send it for the greatest impact.
- Voice and video deepfakes: These attacks are moving on from a technical demonstration to the new weapon of choice for attackers. New AI allows rapid creation of realistic voice replicas, to the extent that they require very few samples to work with. This has meant that attackers can impersonate executives on calls to activate transfers or acquire either sensitive phishing campaigns involving synthesised video or impersonate previously approved requests to spoof the system's biometric input (i.e., the typical security features). Deepfakes can also hijack automated classification systems where the AI bases its detection power and ability on its learning through identifying patterns from previous observation.
- Autonomous malware: Self-adapting malware learns how a defence will respond to it and adapts the attack strategy in real time. In other words, unlike traditional malware that has an "attack signature", the AI threat can identify flaws that it can exploit, and then alter attack characteristics to defeat detection/evasion. Ultimately, this creates an arms race where attackers continually evolve their code faster than the defender can respond.
Tech Prescient's Identity Confluence helps address these challenges through its behavioural analytics capabilities that establish baseline access patterns for users. The platform can detect anomalous access requests that might indicate AI impersonation, providing an additional security layer beyond traditional authentication.
2. Ransomware & RaaS
Ransomware is malware that will lock you out of your computer or encrypt the files so you cannot use them unless you pay a ransom. The cybercriminals behind these attacks want you to send them the agreed-upon ransom so they will send you the keys to decrypt your files. The ransom is usually demanded in an anonymous email or web address in the form of cryptocurrency, so it is anonymous when they receive their funds. It can spread across networks and infect many systems, as was the case with the WannaCry attack that impacted the UK National Health Service in 2017. Once infiltrated, the attackers will ask you to pay them (using cryptocurrency) to gain back access, but even after paying, you are not guaranteed restoration of access to your data. This threat has recently evolved to a model called Ransomware-as-a-Service (RaaS), where criminals interested in attacking make malicious code and then rent it out to others to carry out the campaign, such that using the RaaS model promotes ransomware events as a dark version of a legitimate software service. This process and business model have enabled crime to be executed by criminals more regularly in sophisticated business models and without the technical expertise.
Despite years of defensive advances, ransomware remains the most financially devastating cyber threat. According to Coveware's Q1 2024 Ransomware Report, the average ransom payment reached $740,144, while recovery costs often exceed ten times that amount when including business disruption.
The shift in ransomware operations reveals three alarming trends:
- Threat service-based models: Ransomware-as-a-service (RaaS) platforms now offer victims negotiation teams, payment processing, and general technical assistance. This trend toward professionalizing ransomware groups has lowered the bar for those who do not have technical expertise while increasing the sophistication of the attacks.
- Multi-stage extortion: Attacks have progressed past encryption for ransom purposes to threaten additional attacks from data theft before encrypting data, threatened public release of sensitive information such as healthcare information, and a distributed denial-of-service attack as leverage.
- Critical infrastructure targeting threats: Ransomware groups are increasingly targeting health, energy, and transportation services.
3. Supply Chain Attacks
In a supply chain attack, threat actors focus on the weakest links, like a target vendor or service provider within your trusted network, to compromise your organization. Instead of attacking a well-protected endpoint directly, cybercriminals will target a lower-defended third party, such as a software vendor, hardware manufacturer, or managed service provider, with legitimate access to your environment. The noted SolarWinds incident demonstrated how an attacker could inject malicious code as part of a software update and compromise security controls to access thousands of customer networks at the same time. Supply chain attacks are most dangerous, as established trust relationships are compromised, and the adversary can remain in the environment undetected for long periods of time, moving laterally through multiple connected systems.
The SolarWinds breach, in its implications, was a prominent demonstration of how supply chain weaknesses could be exploited across thousands of organisations, across multiple verticals, at the same time. Today, supply chain attacks follow several sophisticated patterns:
- Software supply chain compromise: attacking legitimate software updates or legitimate software development pipelines by injecting malicious code.
- Vendor remote access exploitation: launching an attack through either privileged connections maintained by service providers or contractor access.
- Open-source poisoning: infiltration of open source vulnerabilities into open source components, which eventually become integrated into a commercial software product.
4. Zero-Day Exploits
A zero-day attack is an attack that exploits a security vulnerability that developers do not even know exists. They have zero days to develop a defence against it. Zero-day vulnerabilities can occur in software or hardware and often go undetected until a researcher discovers them or the attackers actively exploit them. We call it a zero-day attack because the organization had zero days of warning before the attack took place.
The attack lifecycle typically follows four distinct stages:
- Discovery: Attackers discover a previously unknown security vulnerability in commonly used software or hardware, and there is no patch for the vulnerability.
- Weaponization: The attackers create specific code (the exploit) that is designed to exploit this vulnerability.
- Deployment: The attackers execute their attack against the target systems before defenders know the vulnerability exists and bypass traditional security tools that use known threat signatures.
- Exploitation window: A dangerous time period exists between the attack and the time the vendors discover, create, and publish patches, creating a period of time where all users are vulnerable.
The risk of zero-days has been heightened because:
- Financial motivations: Black-market brokers pay millions for high-impact zero-days, which influences researchers to sell findings in the market instead of responsibly disclosing them.
- Prolonged exposure: Although patches are released, organizations take weeks to deploy patches, creating lengthy periods of vulnerability.
- Utilization by nation states: State-sponsored threat actors leverage additional zero-days for advanced directedness of attacks against high-value targets.
These attacks are especially risky because they escape traditional detection, as security controls are focused on protecting against recognized threats, as opposed to unencountered attacks.
Human & Operational Challenges
1. Skills Gap
The lack of cybersecurity professionals relates to an inadequate number of security professionals to meet the demand for their skills in the marketplace. There is a disparity between the skills required and the skills that are available, and the lack of qualified professionals means there is not enough expertise present to effectively deploy, manage, and respond to security threats, which increases the organization's risk profile despite spending money on security technologies.
This gap has reached crisis levels in 2025, with the the (ISC)² Cybersecurity Workforce Study reporting 3.7 million unfilled cybersecurity positions globally. This shortage creates several critical vulnerabilities:
- Alert fatigue: Security teams face alert fatigue due to the sheer volume of potential indicators of threats, resulting in potential blind spots, because the team cannot investigate all alerts.
- Specialized skill gaps: The skill gaps are especially acute in the areas of cloud security, identity governance, and security architecture.
- Retention issues: Security teams experience high rates of turnover, which leads to the understaffing of critical functions.
2. Human Error
Human error in cybersecurity constitutes the mistakes, oversights, or poor decisions made by people that introduce security vulnerabilities or even contribute directly to an incident. Examples of human error include falling for social engineering, mishandling credentials, misconfiguring systems, or bypassing security policies for convenience.
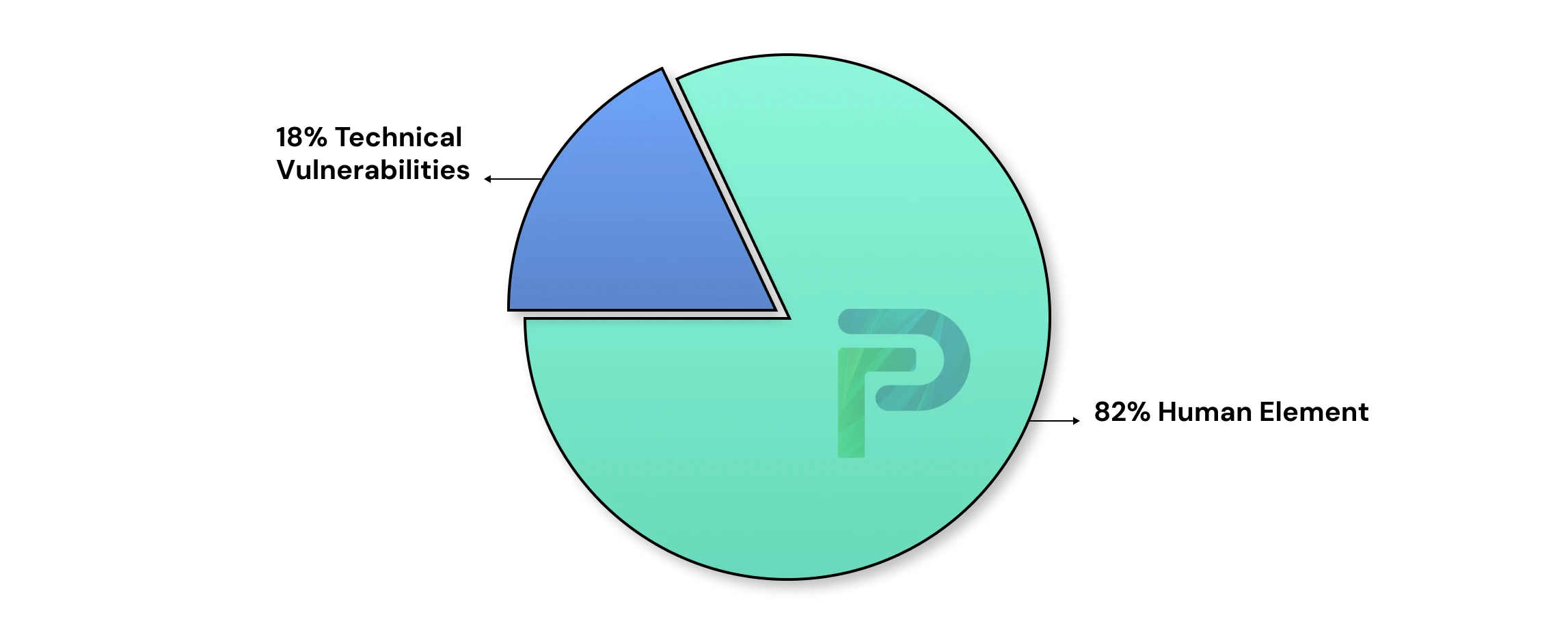
According to Verizon's Data Breach Investigations Report, 82% of breaches involve the "human element" in some form. This vulnerability persists for several reasons:
- Social engineering progression: Phishing moved from obvious spam to targeted efforts that contextualize breaches.
- Credential complication: Even with security awareness training, writing down passwords continues to cause issues, as do using and reusing credentials.
- Configuration complexity: Nowadays, systems require configurations to be much more complex, and misconfiguration is the cause of most cloud security incidents
3. Insider Threats
Insider threats are risks to security that still come from someone who has authorized access to an organization’s systems or data. Insider threats generally can fit into one of three categories:
- Negligent insiders: Employees or contractors who inadvertently create security vulnerabilities due to negligence, lack of training, or disregard for policy. A negligent insider may share login credentials, click on links in phishing emails, improperly configure sensitive systems, or transfer sensitive data to unsecure personal devices. While not malicious, negligent insiders can create significant exposure to security forums.
- Malicious insiders: Employees who purposely misuse their authorized access to steal intellectual property, sabotage systems, or disclose sensitive information. A malicious insider exploits their authorized access, as well as their organizational knowledge, to perpetrate attacks that are difficult to detect, as the attacks often occur in the normal course of work.
- Credential theft victim: Occurrences where an external actor gains access to a legitimate user's credentials and poses as the impacted user. Credential theft victims, otherwise known as pseudo-insiders, are particularly dangerous because they have malicious intent from outside the organization, but combine it with the privileges of an established user inside the organization. The compromised insider often allows for lateral movement through networks to evade detection.
Identity Confluence helps detect and mitigate insider threats through its Identity Analytics & Risk Insights component, which uses login pattern analysis to establish baseline activities for each user and flag anomalous behaviors. The platform also enforces separation of duties to prevent single-user control of critical processes, limiting the damage potential from any individual insider.
Technological Vulnerabilities
1. IoT & Endpoint Security
IoT devices (smart cameras, sensors, industrial controls) typically lack the robust security features found in traditional computing assets. Unlike corporate laptops or servers with regular updates and monitoring, these connected devices often run with basic security, creating significant vulnerabilities across networks.
This security gap creates three major challenges:
- Weak device protection: Many IoT devices ship with default passwords, unencrypted communications, and minimal security testing. Attackers exploit these weaknesses to access sensitive systems and data. For example, hackers can target vulnerabilities in building automation systems to manipulate temperature controls and gain deeper network access.
- Update limitations: Unlike standard computers, many IoT devices run proprietary operating systems that cannot be easily patched when vulnerabilities are discovered. Some devices lack any update mechanism at all, leaving security flaws permanently exposed.
- Extended attack surface: Remote work has expanded corporate networks to include home environments where consumer-grade IoT devices (smart speakers, home automation) share networks with corporate assets, creating countless new entry points with minimal security oversight.
2. Cloud Misconfigurations
Cloud misconfigurations are security vulnerabilities resulting from improperly set up cloud resources, often leading to data exposure or system compromise. These errors occur in various forms including overly permissive access controls, disabled encryption, and inadequate monitoring settings.
This persistent vulnerability stems from several factors:
-
Multi-cloud complexity: Organizations typically use multiple public cloud providers. Each environment has different security models and interfaces, creating natural security gaps as teams work across platforms.
-
Excessive permissions: Most cloud identities use only a small fraction of their assigned permissions, indicating widespread violation of least-privilege principles.
-
Visibility challenges: Even security-focused organizations struggle to maintain visibility across hybrid infrastructures.
3. Quantum Computing (future risk)
Quantum computing employs the principles discovered in quantum physics to address complex problems at a velocity that is impossible for conventional computers to match. While conventional computers process information in bits (0's and 1's), quantum computers use quantum bits, or "qubits", which represent data that can exist in multiple states simultaneously, allowing certain calculations to be performed exponentially quicker than with traditional processors.
This new technology will usher in advances in medicine, materials science, and artificial intelligence, but will also provide significant new security issues. The security of the modern internet is provided by the use of encryption that a conventional computer would take thousands of years to break. A quantum computer would be able to solve the same problems in minutes or mere hours.
Though it may take years to achieve the realization of fully capable quantum computers, there are three immediate security concerns that organizations must consider:
- "Harvest now, decrypt later" attacks: Adversaries are collecting sensitive data that has been encrypted now and intend to decrypt it later when the use of quantum computing is viable. Data that has long-term value (trade secrets, personal information, and national security material) will still have long-term vulnerability regardless of current encryption standards.
- Susceptibility of cryptography: For digital security to exist, there must be some problem in mathematics that the cyber adversary could not use a conventional computer to solve. Ethically, quantum algorithms, such as Shor's algorithm, could resolve the mathematical problems that support most digital security, including secure transactions and secure communications.
- Slow transition: The process of developing and implementing quantum resistant encryption will take a considerable amount of time and money. With most organizations not planning to start the transition, the security landscape faces a perilous implementation gap whenever quantum computing appears.
Organizational & Compliance Pressures
Regulatory Challenges
Regulatory cyber issues refer to the difficult and occasionally conflicting requirements faced by organizations when complying with laws, regulations, and operational standards related to data protection, privacy, and security across jurisdictions. Similarly, the regulatory environment is changing rapidly, resulting in a complicated compliance framework. By 2025, more than 150 countries will have passed data protection regulations based on the European Union General Data Protection Regulation (GDPR).
A few important regulatory trends create challenges for security teams:
- Jurisdictional fragmentation. In the United States, the absence of federal privacy legislation has led to a patchwork of state laws.
- Additional reporting requirements. Publicly held companies face shorter time frames for incident reporting and greater requirements for disclosures.
- Increased enforcement. Regulatory authorities have increased both the frequency and severity of enforcement action.
Shadow IT
Shadow IT refers to technology resources used within an organization without the knowledge or approval of the central IT department. This includes unauthorized cloud services, applications, devices, or software that employees use to enhance productivity or circumvent perceived IT limitations. While often implemented with good intentions, these unsanctioned technologies bypass official security measures and create significant vulnerabilities. While often used with good intentions, unmanaged technology creates serious security problems because it bypasses the security controls or limitations set by the organization through the IT department.
Over the last decade, the ease of use of cloud services and Software-as-a-Service (SaaS) applications has transformed this into a major issue for organizations and creating three main security threats:
- Visibility: Security teams can't protect what they don't know exists. IT departments often find that they only know a small fraction of cloud services that are being used within their organizations, while almost all of the cloud services go unmonitored and unprotected.
- Data protection: Employees often take sensitive company information and use unauthorized services that lack the right level of protection. This could possibly expose regulated personally identifiable data or intellectual property to a data breach.
- AI exposure: The use of generative AI tools could be considered the latest frontier of shadow IT. Employees may paste sensitive company information into AI services without thinking about privacy and terms when using the service that enables them to use, retain, and to learn from all submitted data.
How to Overcome Cybersecurity Challenges
Adopt Zero Trust Architecture
Zero Trust Architecture eliminates implicit trust within an organization's network and requires continuous verification of every user, device, and application attempting to access resources, regardless of location. This approach assumes breach as a default state and verifies each access request individually rather than trusting users based on network location.
Effective implementation includes:
-
Identity-centric security: Replace network-based trust with identity-based verification.
-
Micro-segmentation: Divide networks into secure zones with separate access requirements to contain lateral movement if breaches occur.
-
Continuous validation: Implement systems that verify trust continuously rather than at login only, adapting access rights based on risk factors.
Continuous Employee Awareness Training
Continuous awareness training transforms security education from annual compliance exercises to an ongoing process that builds security knowledge through regular, relevant learning opportunities integrated into employees' workflows. This approach recognizes that security awareness must be reinforced continuously to address evolving threats.
Effective programs incorporate:
-
Microlearning modules: Short, focused training delivered at the point of risk rather than lengthy annual sessions.
-
Personalized content: Training customized to each employee's role, access privileges, and past security behavior.
-
Simulated attacks: Controlled tests that mimic real threats targeting specific organizational vulnerabilities, providing practical learning experiences.
Invest in AI-Driven Defense Tools
AI-driven defense tools leverage artificial intelligence and machine learning to detect threats, automate responses, and enhance security operations beyond what human analysts could accomplish alone. These tools analyze patterns across vast datasets to identify anomalies, predict potential attacks, and accelerate incident response.
AI security tools provide advantages in:
-
Anomaly detection: Identifying unusual patterns across massive datasets that would be impossible for human analysts to process manually.
-
Automated response: Taking immediate action against known threat patterns, reducing the time between detection and containment.
-
Predictive analysis: Forecasting potential vulnerabilities before exploitation by analyzing threat intelligence and system characteristics.
Regular Patching & Vulnerability Scanning
Vulnerability management encompasses the cyclical practice of identifying, classifying, remediating, and mitigating security weaknesses in systems and software. This process includes discovering vulnerabilities through scanning, prioritizing them based on risk, applying patches or mitigations, and verifying remediation effectiveness.
A comprehensive approach includes:
-
Automated discovery and scanning: Continuous monitoring for vulnerabilities across all environments.
-
Risk-based prioritization: Focusing remediation efforts on vulnerabilities with the highest business impact.
-
Defined patching SLAs: Establishing time frames for remediation based on severity.
Strengthen Supply Chain Security Assessments
Supply chain security assessments systematically evaluate the security postures of vendors, partners, and service providers to identify and remediate risks before they impact the organization. These assessments examine third-party security practices, access requirements, and incident response capabilities.
Effective third-party security governance includes:
-
Pre-access security evaluation: Comprehensive assessment before granting system access.
-
Continuous monitoring: Ongoing validation of vendor security posture.
-
Limited access enforcement: Ensuring vendors can access only essential systems and data.
Final Thoughts
The cybersecurity challenges anticipated in 2025 are numerous and rapidly changing. Managing these challenges will require a thoughtful approach across technology, people, and process change. Although sophistication in threats will continue to rise, organizations deploying layered defences with identity at the core will significantly limit their risk.
Identity Governance and Administration (IGA) is an integral element of security because it is ultimately the question of who has access to what and whether that access is appropriate. As traditional perimeters diminish, identity has become the only control point for all systems on-premise, in the cloud, and third-party services.
Tech Prescient's Identity Confluence product consolidates identity governance at the same time as automating the enforcement of access policies. Through deploying automated life cycle management, risk-based analytics, and continuous policy enforcement, organizations can shift identity from an often burdensome administrative task to a strategic security-related opportunity.
The future of cybersecurity is not about building taller walls but about knowing who is at the gate and what they should be able to access once they get through the gate.
Frequently Asked Questions (FAQs)
1. What are the main cybersecurity challenges in 2025?
AI-driven attacks, ransomware, supply chain vulnerabilities, skills gaps, and compliance risks. These challenges are interconnected, as attackers leverage AI to create more sophisticated threats while organizations struggle with resource constraints and expanding regulatory requirements.2. What is the biggest cybersecurity issue today?
Ransomware remains the most financially damaging cyber threat. Its evolution into a service model has lowered barriers to entry for criminals, while multi-stage extortion tactics have increased potential damages. The average incident now costs organizations millions in direct payments, recovery expenses, and business disruption.3. What are the top 5 threats to cybersecurity?
AI attacks, ransomware, IoT vulnerabilities, insider threats, and zero-day exploits. These threats have evolved to bypass traditional security controls, exploiting the expanded attack surface created by digital transformation and remote work. Identity-based security has become essential for detecting and mitigating these advanced threats.4. How can organizations prepare for cybersecurity challenges?
By implementing Zero Trust, automating defences, training staff, and enforcing compliance monitoring. Organizations should focus on identity governance as the foundation of their security strategy, ensuring that all access is appropriate, regularly reviewed, and automatically adjusted as roles change.5. Why is the cybersecurity skills gap a major risk?
Without skilled staff, organizations can't detect, prevent, or respond to sophisticated threats. The talent shortage forces security teams to focus on immediate threats rather than strategic improvements, creating a reactive security posture. Automation and managed services have become essential for augmenting internal capabilities in this constrained talent environment.



