
ITGC Audit: Process, Checklist & Best Practices

An ITGC audit assesses how well your organization’s IT controls are designed and functioning, focusing on areas such as access management, change control, and data integrity. It ensures your systems are not only compliant but also resilient in real-world scenarios, helping you identify and address vulnerabilities before they lead to a breach.
They are basically the foundation of IT governance. An IT general controls audit checks and verifies that these controls are in place and also functioning efficiently to manage risks and guarantee adherence. Consider this: even though you may have complicated change management procedures, strong password policies, or stringent access rules, how can you be sure they're secure? You get confidence from an ITGC audit, which highlights areas that are functioning properly and reveals any holes that might endanger your company.
A recent study by Cloudeagle found that about 39% (roughly 4 in 10) audits spot gaps or evidence issues in ITGC testing. It is a reminder that just having controls in place isn’t enough; you need to check them often, make sure they actually work, and fix them when they don’t. Curious what an ITGC audit looks at and how to run one right? Let’s walk through it step-by-step: the basics, the main things to check, handy checklists, audit types, and practical best practices.
Key Takeaways
- Understand what an ITGC audit is and why it protects system integrity and security.
- Learn why ITGC audits are critical for compliance, risk reduction, and stakeholder trust.
- Explore the main ITGC control areas: access, change, backup, and system security.
- Follow the ITGC audit step-by-step process from planning to continuous compliance.
- Discover best practices and differences between internal and external ITGC audits.
What Is an ITGC Audit?
Information technology general controls audit, also known as an ITGC audit, is the process of reviewing whether an organisation’s core IT controls are working as intended within its infrastructure. These controls, often referred to as ITGCs, form the foundation for managing risk, protecting systems, and supporting compliance.
They protect against data theft, unauthorized access, operational disruptions, and data breaches, influencing every layer of IT, from software deployment to user account management. ITGC also plays a key role in vendor management, ensuring that new applications and procurements comply with established control standards. With ITGC in place, your systems remain secure, properly tested, and correctly implemented, while security patches and network updates are carried out on schedule.
The audit typically examines areas like access management, change management, physical safeguards, and operational controls, all aimed at ensuring the confidentiality, integrity, and availability (the TSCs) of sensitive information. At a practical level, ITGC audits come in two forms: internal audits (proactive self-checks) and external audits (formal reviews, often for compliance like SOX). Which one applies depends on your organization’s needs and regulatory environment. We will break down the difference between the two next.
Types of ITGC Audits
IT General Control (ITGC) audits are typically divided into two categories: internal and external. Each serves a distinct purpose. Internal audits focus on proactive self-assessment to strengthen control effectiveness, while external audits provide independent validation and compliance certification.
1. Internal ITGC Audit – Proactive Self-Assessment
An internal IT general control (ITGC) audit acts as a deep-dive evaluation of your existing IT controls, conducted by your organization’s internal audit or risk management team.
-
When is an internal ITGC audit conducted?
Organizations usually perform internal ITGC audits to ensure that implemented controls are functioning as expected and to identify areas that need reconfiguration, modification, or optimization. Think of it as a proactive “health check” that helps detect issues early before they impact compliance or operational resilience.
-
Who performs it and how often?
An internal ITGC audit is conducted by the organization’s own internal audit team, but organizations without a dedicated team can also engage external experts to perform the review internally. Internal ITGC audits can be conducted quarterly, bi-annually, annually, or right after ITGC implementation, depending on business needs and control maturity.
2. External ITGC Audit – Third-Party, SOX-Driven
An external IT general control audit is an independent assessment carried out by a certified external auditor who is not affiliated with the organization.
-
When is an external ITGC audit conducted?
This type of audit is required when organizations seek to obtain or renew compliance certifications such as SOX, GDPR, or PCI DSS. These certifications serve as proof that the organization meets regulatory and data protection standards, helping establish trust with investors, partners, and clients while avoiding non-compliance penalties.
-
Can internal auditors issue these certifications?
No. An external ITGC audit is conducted by a certified independent auditor. During the audit, the external auditor thoroughly examines ITGC design and operational effectiveness, and based on the findings, issues a certificate of compliance confirming that the organization adheres to the required standards.
-
How often are external ITGC audits conducted?
External ITGC audits are typically performed once a year, as compliance certifications are valid for one year. To maintain compliance, organizations must undergo reassessment annually and renew their certification.
3. Comparison: Internal vs. External ITGC Audit
Both internal and external ITGC audits share a common goal: ensuring that IT controls are effective, reliable, and compliant. However, they differ in purpose, execution, and frequency.
Here’s a quick side-by-side comparison to highlight how they complement each other.
| Sr No | Parameters | Internal ITGC Audit | External ITGC Audit |
|---|---|---|---|
| 1 | Purpose of the Audit | To identify areas for improvement and strengthen IT general controls by ensuring they operate effectively. | To achieve formal compliance certification (SOX, GDPR, PCI DSS, etc.) and demonstrate adherence to legal and regulatory standards. |
| 2 | Conducted By Whom | Performed by the organization’s internal audit or risk management team. | Conducted by a certified, independent third-party auditor. |
| 3 | Audit Frequency | Can be scheduled quarterly, bi-annually, annually, or after ITGC implementation, depending on organizational needs. | Typically performed annually, since most compliance certifications are valid for one year. |

Why ITGC Audits Are Critical
IT General Control (ITGC) audits are not just about compliance checklists. They are essential for safeguarding data, maintaining operational resilience, and preserving stakeholder trust. In today’s high-risk digital landscape, strong ITGCs ensure that your IT systems are secure, compliant, and capable of supporting reliable business performance.
1. Compliance (SOX, ISO 27001)
Maintaining compliance with frameworks such as SOX and ISO 27001 is one of the core objectives of ITGC audits. These audits help ensure that your organization’s internal controls align with regulatory and industry standards. Without proper oversight, you risk non-compliance penalties, reputational harm, and loss of customer confidence. Routine ITGC audits validate that all controls are operating effectively, helping you meet mandatory requirements and maintain a credible compliance posture.
2. Risk Mitigation (Fraud, Downtime, Breaches)
ITGC audits play a critical role in reducing operational, financial, and cybersecurity risks.
- Operational Risks: Effective controls prevent system disruptions, data loss, or configuration errors that could impact day-to-day business continuity. Regular testing ensures your systems remain accurate, updated, and resilient.
- Financial Risks: Poor control environments can lead to data breaches or compliance failures that directly affect financial performance. Missed audits or incomplete records can delay reporting and impact investor confidence.
- Reputational Risks: A single control failure can undermine stakeholder trust. Strong ITGC frameworks demonstrate accountability and help preserve your brand reputation even during incidents.
3. Stakeholder Trust
Trust is the cornerstone of every business relationship. A well-audited IT control environment signals to customers, investors, and partners that your organization takes data protection and compliance seriously. Consistent ITGC audits reinforce transparency, proving that your business operates with integrity and adheres to recognized security standards.
By conducting ITGC audits regularly, organizations can stay compliant, reduce exposure to fraud and downtime, and strengthen confidence among stakeholders. In short, ITGC audits ensure your IT foundation remains secure, compliant, and trustworthy.
Key Areas Reviewed in ITGC Audits
Now that you understand why ITGC audits are important and what they typically involve, let’s explore the key control areas that auditors focus on. These controls form the foundation of your IT governance and are critical for maintaining compliance, security, and operational integrity.
1. Access Management Controls – User Provisioning, Password Policy
Access management controls govern who can access what within your systems and applications. They ensure that only authorized users can interact with critical data and IT resources.
During an audit, reviewers assess whether your user provisioning, de-provisioning, and access review processes are properly defined and enforced. They also evaluate password policies, multi-factor authentication, and least-privilege access models to confirm that accounts are adequately protected. Weak or outdated access management practices can expose organizations to insider threats and unauthorized data exposure.
2. Change Management – Testing, Approvals, Rollback
Your IT environment is constantly evolving, and every change, whether it’s a software update, configuration adjustment, or system upgrade, introduces potential risks. Change management controls ensure that all modifications are properly documented, authorized, tested, and approved before implementation.
Auditors typically review your change logs, testing procedures, and rollback plans to determine whether there is a consistent and traceable process for managing system updates. Effective change management minimizes disruption, prevents misconfigurations, and helps maintain operational stability.
3. Backup & Recovery – Disaster Readiness
Even the best systems can experience unexpected failures or attacks. That’s why backup and recovery controls are crucial for business continuity. These controls define how your organization backs up data, tests recovery processes, and ensures critical systems can be restored after incidents such as cyberattacks, natural disasters, or hardware failures.
During an ITGC audit, evaluators assess the frequency and scope of data backups, verify the presence of offsite or cloud-based backup solutions, and test the effectiveness of recovery procedures. A strong disaster recovery strategy helps minimize downtime and data loss when the unexpected happens.
4. System & Network Security – Patching, Monitoring, Intrusion Prevention
System and network security controls are designed to safeguard your IT infrastructure against cyber threats and ensure systems remain secure and reliable. These controls typically include patching, monitoring, and intrusion prevention, each playing a critical role in protecting organizational assets:
-
Patching refers to the process of regularly applying updates or fixes to software and systems to close security vulnerabilities. Without timely patching, attackers can exploit known weaknesses and gain unauthorized access.
-
Monitoring involves the continuous observation of networks, systems, and logs to detect anomalies or suspicious activities in real time. Effective monitoring ensures early identification of potential breaches or operational issues.
-
Intrusion Prevention Systems (IPS) are security tools that actively block malicious traffic and attempts to exploit vulnerabilities. Unlike passive monitoring, IPS solutions can automatically stop attacks before they compromise systems.
During an ITGC audit, reviewers evaluate whether your organization consistently applies security patches, maintains active monitoring practices, and implements effective intrusion prevention measures. They also examine incident response procedures and log management to confirm that threats can be detected, analyzed, and contained quickly.
By strengthening these controls, organizations not only reduce exposure to cyber risks but also build a resilient ITGC framework that supports compliance, security, and operational integrity. While IT General Controls form the foundation of compliance, they are part of a broader governance framework that also includes Identity Governance and Administration (IGA) solutions.
ITGC Audit Checklist (Step-by-Step)
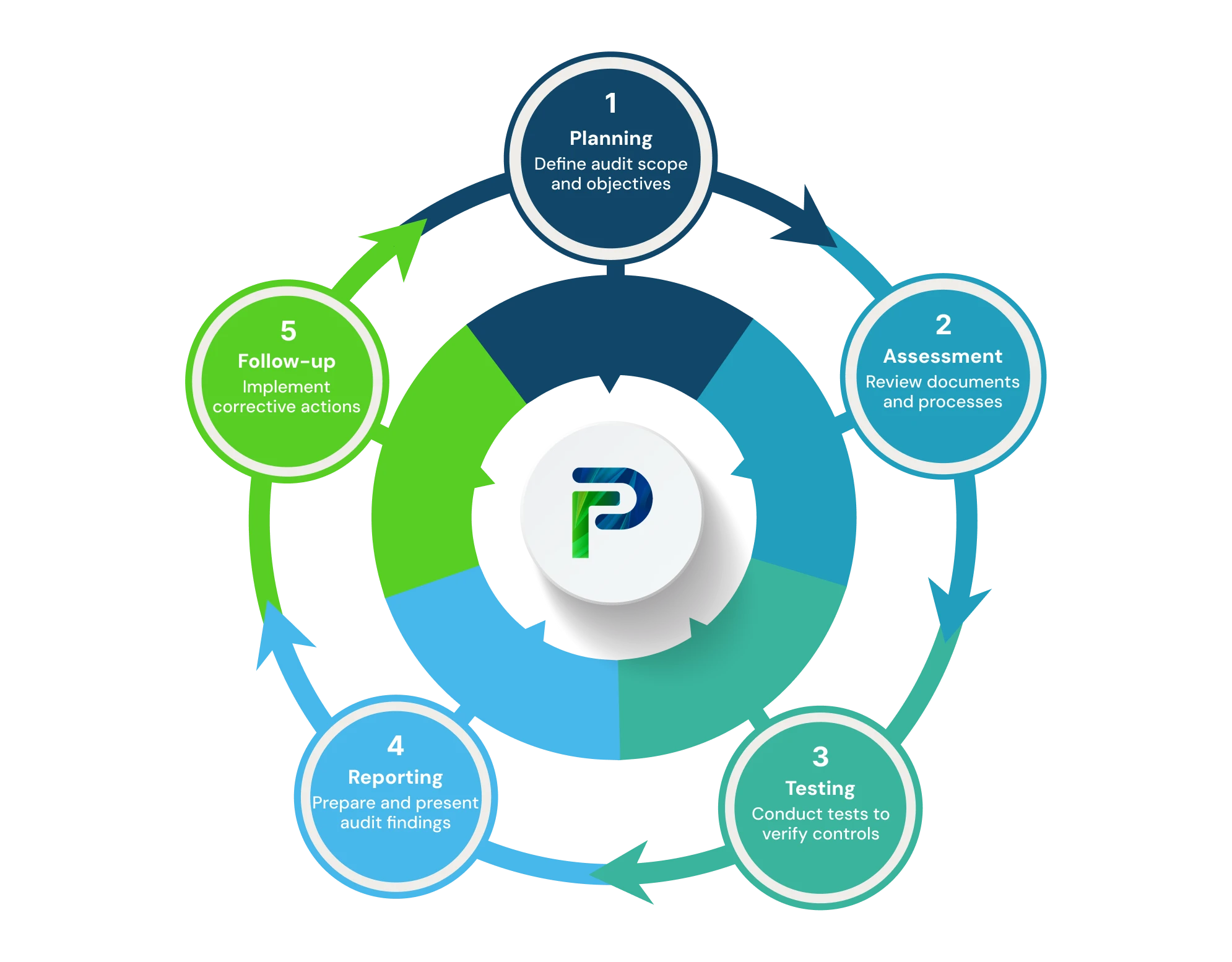
An ITGC audit follows a structured, multi-phase approach that helps auditors evaluate, test, and enhance the effectiveness of an organization’s IT general controls. Below is a step-by-step breakdown of the process that ensures your IT environment remains secure, compliant, and resilient.
1. Planning – Scope Definition
The first stage of any ITGC audit is planning, which involves defining the scope and objectives of the audit. Here, the audit team identifies which IT general controls are in place and which systems, applications, and processes fall under review.
Common control categories include:
-
Physical and Environmental Security Controls: Protecting physical entry points to sensitive areas such as data centers through biometric authentication, CCTVs, and motion sensors. These also include HVAC systems to protect stored assets from environmental risks like humidity or overheating.
-
Logical Security Controls: Restricting unauthorized access to applications and data using measures such as two-factor authentication, identity access management (IAM), and least-privilege access models.
-
Change Management Controls: Monitoring and authorizing system changes or configuration updates to ensure they do not disrupt business operations.
-
Incident Management Controls: Establishing an incident response framework to manage security events such as cyberattacks, breaches, or data loss.
-
Backup and Recovery Controls: Maintaining secure data backups and disaster recovery plans to restore operations quickly after an incident.
Once the audit scope and applicable control types are documented, auditors can prioritize which areas need deeper review first.
2. Assessment – Review Policies and Documentation
In this phase, auditors review documentation related to IT policies, standard operating procedures (SOPs), and prior audit results. The goal is to verify that written policies align with the implemented controls.
Auditors gather information such as:
-
Existing IT governance policies and compliance checklists.
-
Change request forms and approval workflows.
-
Incident logs, backup schedules, and recovery test reports.
This documentation review provides context for the testing phase and ensures the audit approach aligns with your organization’s compliance requirements and operational goals.
3. Testing – Verify Design and Operating Effectiveness
After reviewing documentation, auditors move into testing to evaluate whether ITGCs are designed effectively and operate as intended.
Two key methods are typically used:
-
Vulnerability Scanning: This process helps auditors detect weaknesses in the IT infrastructure, including unpatched systems, outdated security software, misconfigured applications, or open ports that may allow unauthorized access. The goal is to identify any potential entry points that attackers could exploit to compromise sensitive data or disrupt operations.
-
Penetration Testing (Pen Testing): In addition to scanning, auditors may perform or commission penetration tests to conduct a more in-depth analysis of IT general controls. This involves simulating cyberattacks, often with the help of ethical hackers (or internally if the audit team has the expertise), to actively exploit detected vulnerabilities. By mimicking real-world attack scenarios, pen testing provides valuable insights into whether existing controls can truly withstand advanced threats. This rigorous exercise helps organizations understand their resilience against actual attacks and highlights areas that require immediate strengthening.
If auditors find exploitable vulnerabilities or if a simulated breach is successful, it indicates that the current controls may not be performing effectively and need immediate remediation.
4. Reporting – Findings and Remediation
Once the testing is complete, auditors compile their findings into a comprehensive audit report. This report details which controls passed the assessment, which failed, and what corrective measures are needed to improve the overall control environment.
For example, if an intrusion detection system (IDS) fails to flag a penetration test attempt, the report must note the specific attack vector, affected port, and remediation recommendation. The report should also outline corrective actions and assign responsibilities for remediation. Many organizations establish a separate team to implement these recommendations before scheduling the follow-up audit.
5. Follow-Up – Continuous Compliance
After implementing the recommended changes, your audit team should perform a follow-up review to confirm that those fixes have been applied correctly and are working as expected. This step ensures that previously identified gaps are truly resolved and that IT controls remain reliable.
Note: If your organization is undergoing an external compliance audit, the follow-up will typically be conducted by external auditors. They will assess whether the recommended changes were properly executed and whether ITGCs are functioning as required. If everything is in place, the organization may be awarded a compliance certification.
Regular follow-up audits not only help validate remediation efforts but also strengthen overall IT governance and reduce the risk of recurring control gaps.
ITGC vs SOX vs ISO 27001 Controls
Organizations often confuse ITGC, SOX, and ISO 27001 since all three involve auditing, risk management, and compliance. However, their purpose and scope differ.
SOX (Sarbanes-Oxley Act) is a compliance requirement that mandates annual evaluations of how effectively an organization manages its IT controls. Its primary goal is to safeguard shareholders by ensuring that financial reporting and disclosures are accurate, consistent, and trustworthy.
It’s important to note that SOX is not the same as ITGC. Instead, ITGCs provide the foundation that organizations rely on to stay compliant with SOX requirements. Together, SOX and ITGC function as complementary mechanisms that protect businesses, shareholders, and customers from risks such as data breaches and cyberattacks.
1. How ITGC and SOX Work Together
IT General Controls (ITGCs) are the foundation of SOX compliance for IT systems and financial reporting. The Sarbanes-Oxley Act of 2002 (SOX) requires all publicly traded companies to establish and maintain effective internal controls over financial reporting in order to protect investors from fraudulent accounting practices. ITGCs support this by ensuring the confidentiality, integrity, and availability of the IT systems that process and manage financial data.
The interdependent relationship
SOX and ITGC work hand in hand to ensure the reliability of a company’s financial information. Under SOX Section 404, both management and independent auditors must assess the adequacy and effectiveness of internal controls over financial reporting. ITGCs provide the control objectives and governance framework needed to manage IT-related risks and safeguard the accuracy and integrity of financial reporting systems.
2. Who Is Responsible for ITGC Compliance Under SOX?
Under SOX, senior management, particularly the CEO and CFO, hold the ultimate responsibility for establishing and maintaining effective IT General Controls (ITGCs). They are required to certify both the accuracy of financial statements and the effectiveness of internal controls over financial reporting. This responsibility flows down through the organization, with managers and department heads ensuring that controls within their areas are properly implemented, monitored, and updated. To support this structure, teams across IT, finance, and audit work together on control design, documentation, and ongoing compliance, forming an integrated framework that safeguards operational integrity and meets regulatory obligations.
3. Where ISO 27001 Fits In?
While SOX focuses on financial reporting controls, ISO 27001 is an international standard for information security management systems (ISMS).
It provides a broader security framework that goes beyond financial systems, covering all aspects of data protection, risk management, and security governance. Organizations that align their ITGC practices with ISO 27001 gain a comprehensive, globally recognized approach to maintaining data confidentiality, integrity, and availability.
Best Practices for Successful ITGC Audits
Implementing ITGC (IT General Controls) is not a one-time effort. Success comes from embedding ongoing rigor, automation, governance, and collaboration. Below are key best practices that will help make your ITGC audits both effective and sustainable.
1. Automate Access Reviews & Monitoring
Automation is one of the strongest enablers of consistent ITGC compliance. By reducing manual oversight and enabling real-time monitoring, you can strengthen security while minimizing human error.
-
Use continuous monitoring tools
Instead of relying purely on periodic, manual checks, use automation to monitor user access, privilege changes, and unusual activity in real time. This helps identify issues such as excess privileges or inactive accounts quickly. -
Schedule regular user access certifications
Automate reminders and workflows so that reviews and approvals of user access rights happen at defined intervals, ensuring timely revocation or adjustments. -
Apply role-based and least privilege principles
Wherever possible, group access through roles and ensure users only have the minimum necessary rights. This reduces complexity and the risk of overprovisioning. -
Document every change and event
Maintain an audit trail for every access change, including who performed it, the reason, and the approval path.
2. Use Proven Frameworks (COBIT, NIST, ITIL, etc.)
A structured framework brings consistency, clarity, and credibility to your ITGC program. It helps standardize processes, align teams, and measure progress effectively across control environments.
-
Map your controls to established frameworks
Using a recognized framework like COBIT, NIST SP 800-53, ITIL, or ISO/IEC 27001 ensures completeness, standardization, and audit readiness. -
Leverage maturity models
Use framework maturity levels to assess where your control environment stands and what improvements are needed. -
Align control ownership and accountability
Frameworks help formalize ownership, define responsibilities, and assign oversight for every control. -
Periodically review and update frameworks
As your IT landscape evolves, revisit your framework mapping to ensure emerging risks and technologies are covered.
3. Regularly Test Disaster Recovery & Backup Procedures
Preparedness is at the heart of operational resilience. Regular testing ensures that your organization can respond swiftly and effectively when systems fail or cyber incidents occur.
-
Run formal drills and simulations
Conduct regular disaster recovery and business continuity drills to verify that your plans and controls work effectively during real scenarios. -
Maintain and test backup integrity
Check that backups are complete, uncorrupted, and restorable. Validate data consistency, especially for critical databases. -
Define RTO and RPO targets and validate compliance
Establish recovery time objectives (RTO) and recovery point objectives (RPO), and verify during tests that actual performance meets those targets. -
Document recovery steps clearly
Ensure your recovery plans include detailed, step-by-step procedures, assigned roles, and escalation paths. -
Include scenario-based variations
Test different scenarios like data center outages, ransomware attacks, or network failures instead of limiting to standard restore operations.
4. Foster Cross-Department Collaboration
Strong collaboration ensures that ITGC audits are embraced organization-wide, not just by the IT or compliance teams. When departments work together, controls are implemented more smoothly and sustainably.
-
Involve business, IT, security, and audit teams early
Since ITGC audits span multiple functions, involving all relevant teams ensures that controls are practical and aligned with business goals. -
Communicate audit goals and value
Position audits as tools for risk management and performance improvement rather than as compliance burdens. This helps improve cooperation. -
Train and sensitize stakeholders
Educate teams about the purpose and importance of controls such as segregation of duties, least privilege, and change management to encourage ownership. -
Use feedback loops
After each audit cycle, gather feedback from all involved teams to refine controls, improve coordination, and enhance efficiency.
To ensure ITGC audits are not just compliance exercises but drivers of resilience, focus on automation, align with trusted frameworks, test recovery processes regularly, and foster strong collaboration across teams.
Final Thoughts
ITGC audits are no longer just a compliance checkbox; they are a cornerstone of resilient IT governance, security, and risk management. By systematically reviewing access, change management, backups, and security operations, ITGC audits provide the assurance that critical systems and data remain secure, reliable, and compliant.
While frameworks like SOX and ISO 27001 define the “what” of compliance, ITGC audits deliver the “how” by validating that foundational controls are both designed effectively and operating as intended. In an era of increasing regulatory scrutiny and digital transformation, organizations that prioritize ITGC audits not only reduce risks but also strengthen stakeholder trust and operational continuity.
To see how Tech Prescient helps enterprises streamline ITGC audits with automation, proven frameworks, and deep compliance expertise -
Frequently Asked Questions (FAQs)
1. What does ITGC mean in audit?
ITGC stands for Information Technology General Controls. These are the foundational IT policies and procedures that organizations put in place to keep systems and data secure, reliable, and compliant during an audit. They form the baseline that ensures technology supports business operations without unnecessary risks.2. What are the 4 domains of ITGC?
ITGCs are usually grouped into four main domains:- Access Management: making sure only the right people have the right level of access to systems and data.
- Change Management: ensuring updates, patches, or new features are tested and approved before going live.
- IT Operations: covering day-to-day processes like backups, recovery, and job scheduling.
- Program Development and Security: focusing on secure system development practices and protecting infrastructure from threats.
Together, these domains keep IT environments controlled, consistent, and audit-ready.
3. What is the difference between ITGC and SOX controls?
ITGCs are broad IT controls that apply across an organization’s systems, covering areas like access, change, and operations. SOX controls, on the other hand, are specific requirements under the Sarbanes-Oxley Act that focus on ensuring accurate financial reporting. In simple terms, ITGC provides the overall IT governance foundation, while SOX builds on that foundation to protect financial integrity.4. What is the difference between ISO 27001 and ITGC?
ITGC and ISO 27001 overlap, but they serve different purposes. ITGC focuses specifically on IT systems and processes such as access, changes, and security operations. ISO 27001 is a global information security standard that goes much broader, covering risk management, governance, and continuous improvement of security practices. You can think of ITGC as one important piece within the wider ISO 27001 framework.5. What should be included in an ITGC audit checklist?
An effective ITGC audit checklist usually covers the following:- User access controls and password policies
- Change management workflows and approvals
- Backup and recovery procedures
- System and network security monitoring
- Physical and environmental safeguards
This checklist helps auditors verify that both policies and day-to-day practices are aligned, ensuring systems stay secure and compliant.




