What Is User Provisioning and Deprovisioning? (Complete Guide for 2026)

Provisioning (assigning access) and deprovisioning (removing access) are often considered the two most fundamental tasks in identity and access management (IAM). Provisioning occurs when a user is onboarded (granted access to systems and data) or when a user is changing their role (changing the scope of access). Deprovisioning is removing access rights from users. Those users are either leaving the organization or changing their role, and they no longer need access.
These activities may seem like boring or mundane tasks, but they are critical to secure and compliant IT governance. With every grant of access, or removal of access, the organization is taking on risk and if these processes are not followed appropriately, this could lead to audit gaps, potential insider threats, and orphaned accounts that no one owns.
This guide will outline what user provisioning and deprovisioning mean, why they matter, and how modern cloud-based platforms, like Identity Confluence, are smartly automating the provisioning and deprovisioning process.
Key Takeaways
- Provisioning means giving users the right access to tools, systems, and data as soon as they join or change roles based on what they actually need to do their job.
- Deprovisioning means automatically taking away that access the moment it’s no longer needed when someone leaves the company or shifts departments.
- Manual processes (like spreadsheets or email tickets) often cause delays, leave access open longer than necessary, and increase security and compliance risk.
- Automating the identity lifecycle makes sure access is always up to date, secure, and fully auditable with less work for IT and faster results for the business.
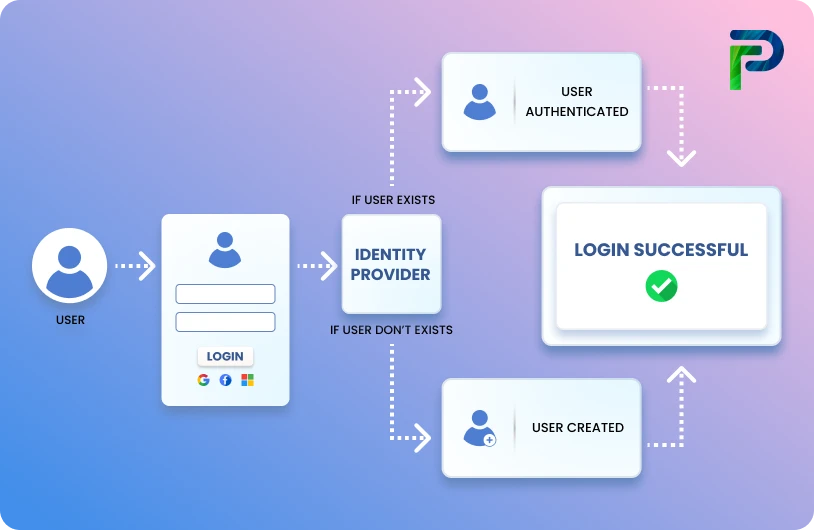
What Is User Provisioning and Deprovisioning?
User provisioning and deprovisioning are critical components of Identity and Access Management (IAM). Provisioning is the act of providing users with access to digital resources based on roles or business needs. Deprovisioning is removing that access when it is no longer needed. Provisioning and deprovisioning, together, comprise a critical piece of the Access Management Lifecycle, impacting organisational security, regulatory compliance, and operational efficiency. When automated, provisioning and deprovisioning can also help organizations improve accuracy, reduce manual work, and ensure decision point access is applied routinely and consistently.
Provisioning and deprovisioning are the lifecycle of operations that help identify who has access to what in your organization. Provisioning starts when a user is onboarded and ends when that user ends their relationship with the organization.
Provisioning generates digital identities and grants access based on job functions, roles, or attributes. Deprovisioning is the process of revoking those permissions when they are no longer needed. Importantly, these processes need to revoke access in such a way that authorization is never forgotten or left behind, a legacy of a departing employee. Provisioning and deprovisioning are at the core of Identity Lifecycle Management (ILM). User provisioning and deprovisioning processes typically begin with Human Resources or some type of identity system such as Workday, SAP SuccessFactors, or Active Directory.
What Does User Provisioning Involve?
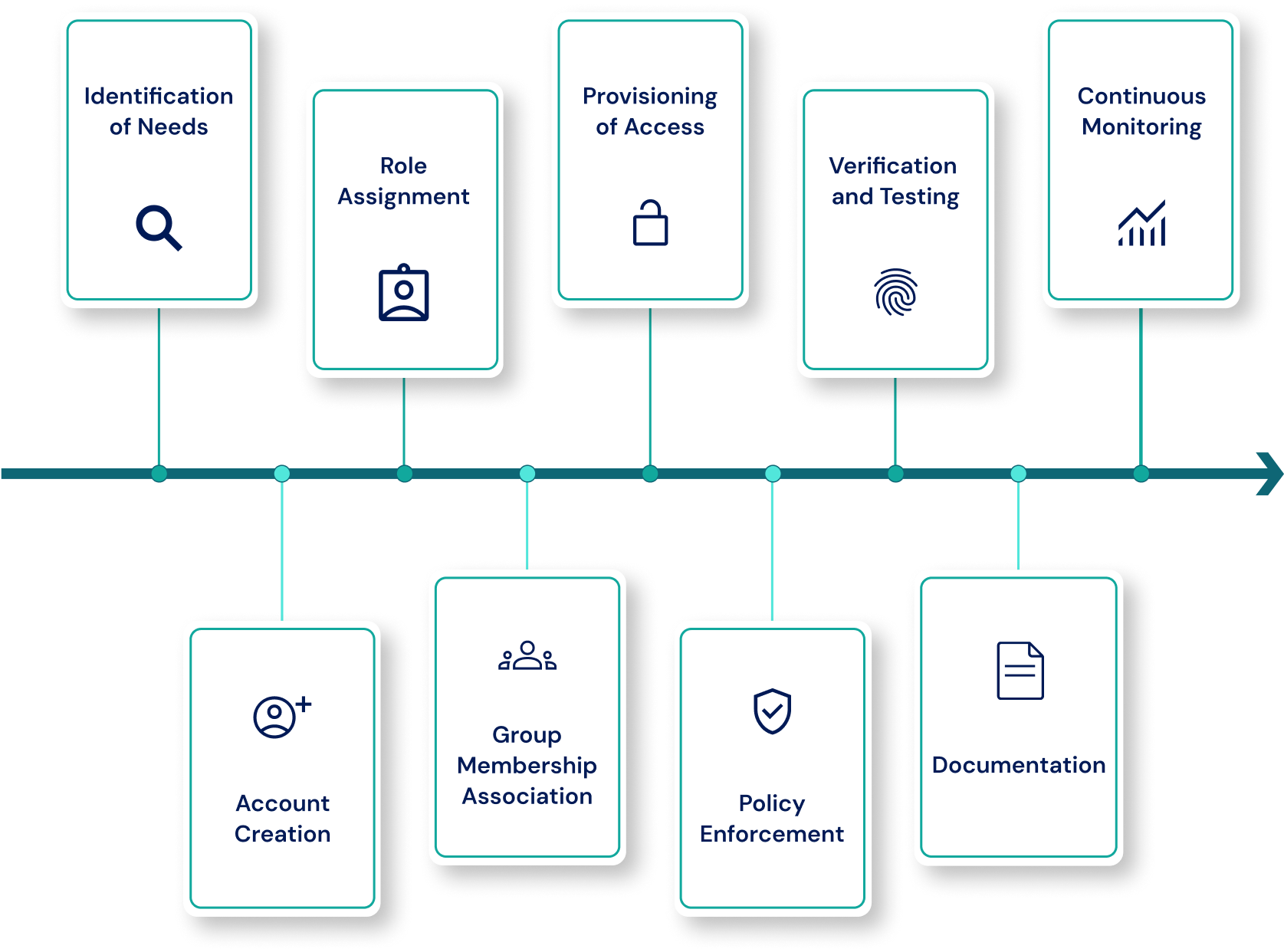
Provisioning enables users to receive appropriate access to apps and data based on their role, department, and business context. Provisioning is fundamental for enforcing security and compliance, enabling efficient onboarding, and ensuring scalable operations in modern hybrid and multi-cloud ecosystems.
Typical steps include:
- Account Creation and Configuration: For every user, a digital identity is created, typically derived from some entity in an HRMS system like Workday, SAP SuccessFactors, and BambooHR. Identity creation accounts for login credentials, authentication methods (like MFA), and syncing with identity directories (like Active Directory or Azure AD).
- Role and Permission Assignments: Access is not granted ad hoc; it is governed by policy. IC maps users to predefined business roles, based on title, department, location, or employment type. These business roles are linked to application-specific roles or access bundles and enforce least privilege by default.
- Integration with HR Systems for User Onboarding and Offboarding (Joiner-Mover-Leaver): Provisioning workflows are automatically triggered by user lifecycle events in the organization’s HR system (e.g., Workday, SAP SuccessFactors). When a new joiner is onboarded, a digital identity is created and associated application access is granted automatically depending on the role of the new joiner, access can be provisioned to relevant groups in real-time. When a user works on a different team after a departmental transfer, the process reviews their status, removes all previous entitlements, and provisions access to the new entitlements based on new responsibilities. If a user leaves, all access - regardless of whether application access is across cloud, on-prem, and hybrid - is removed in real time to avoid orphaned accounts and security vulnerabilities. This maintains a clean user access footprint, removing access totally, not just disabling it in one system.
With Identity Confluence, your actions are executed automatically and in real time without any manual interaction. IC will provision the actions and enforce compliance with audit and governance policies in seconds while simultaneously providing the ability to accommodate identity changes instantly. These capabilities can help IT execute actions faster, reduce human error, and consistently provide secure access throughout the organization.
Risks of Not Deprovisioning
One of the most overlooked and highly unreported vulnerabilities in enterprise IT ecosystems has to be not de-provisioning access in an efficient and systematic way. The longer that an inactive identity retains access to systems, the more the attack surface area grows. Deprovisioning gaps not only raise security vulnerabilities, but they can also lead to compliance failures and operational inefficiencies.
- Orphaned Accounts: These accounts have been classified as user accounts that exist even after an employee, contractor, or partner is no longer with the organization. If these accounts are not correctly deprovisioned, the account retains access credentials but becomes an unmonitored entry point into your IT systems. Since they are not associated with an active user, IT and security teams often miss them hanging out on SaaS platforms, cloud environments, and on-premise applications. If these accounts have elevated privileges, they can be a tremendous risk to the organization regarding unauthorized access, data exposure, or insider threats.
- Privilege Creep: As employees move on to different roles or departments, it is common for them to unintentionally accumulate privileges over time, without their other rights being revoked. When this happens, the employee is over-permissioned by access to systems and data they no longer have responsibility for and a need to access. This unchecked access contributes to the organization's internal attack surface and demonstrates a blatant violation of the principle of least privilege, creating unnecessary exposure from a risk and compliance perspective.
- Audit Failures: Regulatory frameworks, including SOX, HIPAA, and GDPR, require strict Access Management Lifecycle controls. If you have incomplete off-boarding or missing deprovisioning logs, you will have potential audit findings and, in many cases, fines.
- Breach Risk: The inactive accounts of prior employees, contractors, or service accounts are at times neglected and are thus low-hanging fruit for attackers. These accounts can be leveraged for initial access into the system. Attackers may leverage these types of credentials to tap into them, and they will often use these accounts to perform lateral movement transitions between systems without detection and privilege escalation. Privilege escalation occurs when an attacker is able to elevate their access under a primary account and navigate to higher-level administrative privileges. They may use elevated privileges to access sensitive data, turn off security controls, and exfiltrate information, and often they do not create an alarm condition until the attack is detected. The longer an account is inactive and unmonitored, the greater the risk of full breach.
A Forrester study in 2023 revealed that 27% of data breaches involved former employees as actors or made use of unused credentials. This highlights that organizations should view deprovisioning not just as IT cleanup but as a primary security control, necessitating automation, accountability, and provisions tied to human resources systems so that the gaps can never begin to occur.
What Is Deprovisioning and Why Does It Matter
Deprovisioning is the process of systematically removing a user’s access to an organization’s systems, applications, and data, usually when a user leaves the organization, moves roles, finishes a project, or when the temporary access expires. Deprovisioning is the opposite of provisioning: provisioning gives access; deprovisioning makes sure access is removed when it is no longer required. This process is vital to maintaining security, reducing unauthorized access, and adhering to regulatory compliance such as HIPAA, SOX, and GDPR.
Core Components of Deprovisioning:
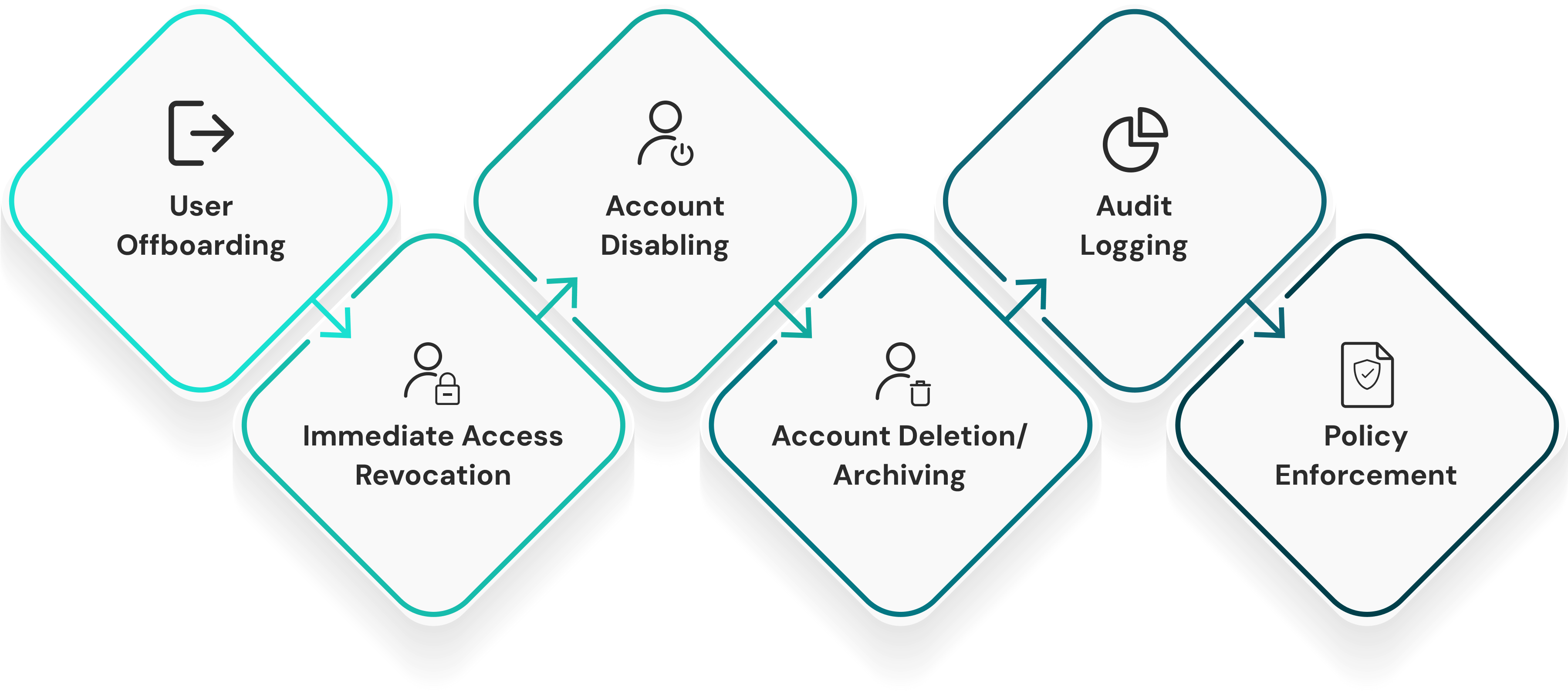
- Immediate Access Revocation: When a user's employment or role relationship ends, access to all enterprise systems should be terminated, in particular, access to cloud services, on-prem applications, internal databases, shared drives, etc. Top IAM platforms will detect these automatic deprovisionings in real time, listening for changes from the authoritative HR system. Any delays, even a few hours, present vulnerabilities for unauthorized data disclosure, sabotage, breach, etc., aided by residual session tokens and credentials.
- Account Disabling/Deletion: Revoking access starts with disabling user accounts in all directories and applications; some organizations then implement a grace period, for audit or transition purposes, before ultimately requiring that accounts are deleted to eliminate the risk of reactivation, especially in shared-service environments or multi-tenant applications.
- Audit Logging & Policy Enforcement: All access revocation should be recorded with detailed metadata: identity of user, timestamps, source of deactivation, enforcement method, and any conditional logic that was applied. This creates non-repudiable evidence for internal audits, regulatory investigations, and real-time compliance dashboards. Identity Confluence is the central repository for these logs and can accurately trace every deprovisioning action back to an Access Management Lifecycle policy and HRMS triggers.
The Risk of Zombie Accounts: Inactive accounts that persist beyond their intended lifecycle are typically called "zombie accounts." These accounts are by default hidden from daily business activity and often exploited by bad actors because of their invisibility. It could be a contractor who was never off-boarded or a cloud service that was never accounted for; these hidden backdoors are a significant risk.
Tech Prescient’s platform, Identity Confluence, elevates deprovisioning by:
- Listening to HRMS and IDP signals to auto-trigger workflows
- Executing automatic deprovisioning within minutes, not hours or days
- Surfacing dormant, privileged, or orphaned accounts for immediate action
"Orphaned accounts don’t make headlines; they make breaches."
The Benefits of Automating Provisioning and Deprovisioning
Automation not only introduces convenience, but it is the basis for scaling resilient identity operations. In traditional environments, provisioning and deprovisioning require IT staff to respond to a ticket, and then such things as updating directories, chasing approvals, etc. All this creates delay, inconsistency, and exposure. In contrast, automated identity workflows driven by real-time signals from HR or IDP systems enforce policy consistently, are less prone to oversight, and provide elimination of administrative activity.
Key benefits include:
- HR-Driven Access Management Lifecycle Sync: Automated systems are integrated with upstream HRMS systems (like Workday or SAP SuccessFactors) so joiners, movers, and leavers receive recognition in a timely fashion, and access changes are made instantly.
- Role-Based Provisioning Logic: Rather than provisioning an account individually, access is based on Business Roles (that change dynamically). A user’s access is defined by their role, department or unit of reporting, and status of employment. This policy-controlled provisioning minimizes access sprawl and maximizes least-privilege adherence.
- Minimized Manual Errors and Costs: Automation removes human involvement in repetitive tasks and minimizes misconfigurations, latency, and unauthorized access occurrences. By minimizing IT’s workload and improving audit and certification accuracy.
IC users have reported:
- 70% reduction in access review cycles
- 90 hours saved monthly in provisioning tasks
- Fewer audit flags due to role-policy alignment
Security & Compliance Implications
Access decisions have to be compliant with organizational policy and regulatory requirements. If enterprises do not tightly control who has access, when, and why, they put themselves at risk of insider threats, audit failures, and additional cyber risk.
Key Implications:
- Aligns with Zero Trust Principles: Automated provisioning and deprovisioning ensure continuous validation of access, minimizing implicit trust within systems.
- Supports HIPAA, GDPR, SOX Compliance: Enforcing timely deprovisioning and maintaining access logs helps satisfy compliance mandates around data protection, privacy, and access transparency.
- Helps Prevent Insider Threats: By revoking unused or unnecessary access immediately, organizations reduce the risk of privilege misuse whether intentional or accidental.
IC embeds enforcement into every access event and maintains a full, immutable audit trail of:
- Who was granted access
- The business justification or policy used
- When it was removed and by whom
How the Process Works (With Examples)
When organizations picture identity management, they envision account creation and account deletion as two separate tasks. In fact, identity management, or the identity life cycle, is a continuous journey and includes onboarding, role changes, and exits from the identity. Managing this identity life cycle with any speed, accuracy, and consistency across dozens (if not hundreds) of apps is a manual process doomed to fail. This is why you need automation (namely to connect Joiner-Mover-Leaver (User Onboarding and Offboarding) Automation).
Let’s highlight how Identity Confluence facilitates this life cycle in practice:
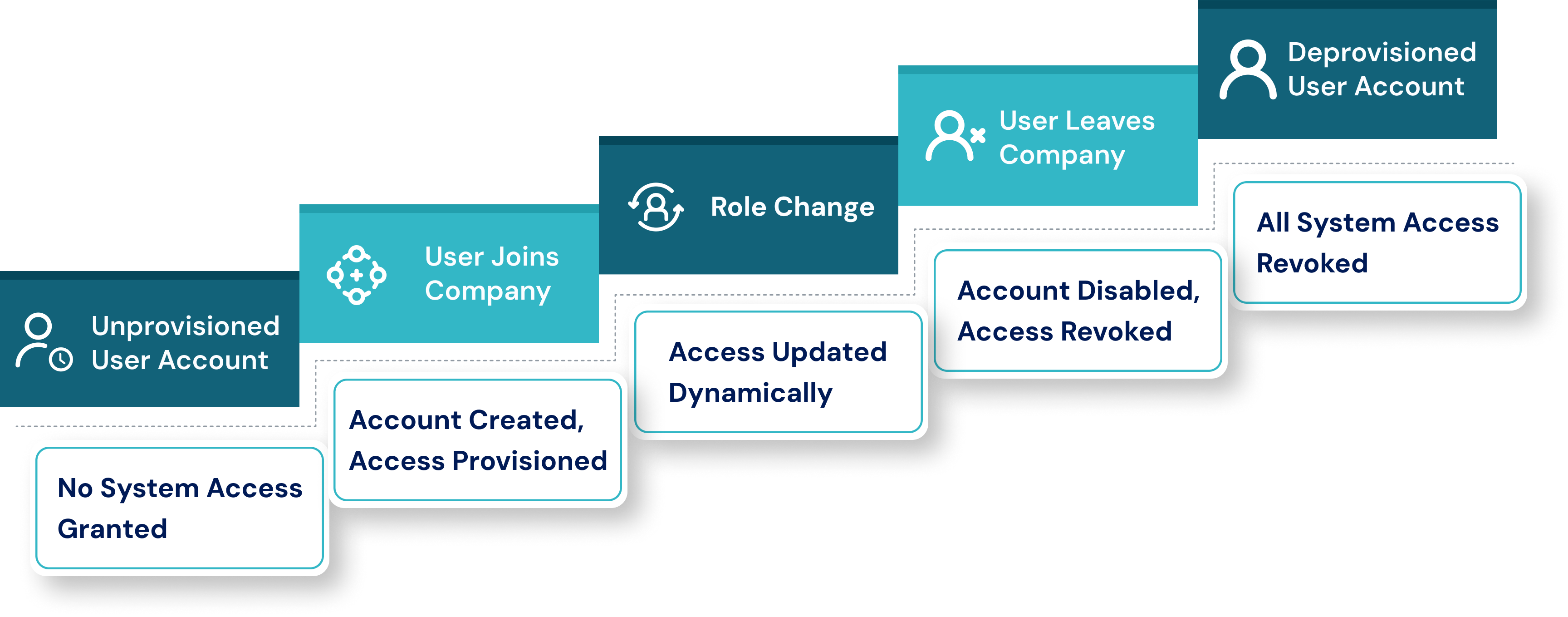
- User Joins Company → Account Auto-Created → Access Granted: When a new employee is entered into the HR system (e.g., Workday). Identity Confluence assumes the joiner event, creates membership based on a predefined business role (e.g., sales executive), and grants access according to policy across email, CRM (Salesforce), collaboration tools (Zoom), and cloud suites (Office 365).
- User Changes Role → Access Recalibrated: If the same employee moves to the marketing department, IC notes this role change and updates their access in real time. There is no need to worry about revoking permissions manually. Entitlements to marketing platforms such as HubSpot and Canva are assigned, negating the need for 1-2 weeks of waiting.
- User Leaves → Account Disabled in All Apps: When a user is separated from their organization, the HR system activates an IC workflow to deactivate all accounts, terminate all access across all systems, and log the entire event chain for compliance teams, all immediately.
These workflows remove friction, human error, and lag time, providing real-time identity governance that keeps pace with the business.
No delays. No tickets. No risk.
Best Practices for User Provisioning & Deprovisioning
Managing provisioning and deprovisioning well is more than just about configuration - it is about discipline, visibility, and enforcement. The following best practices can help enterprise teams construct a solid policy-based identity operating environment.
- Centralize Through IAM/IGA Tools (e.g., Identity Confluence, Okta): Avoid fragmented access logic across departments or applications. Leverage a centralized IGA construct with a common policy enforcement, provisioning logic, and compliance reporting.
- Apply Least Privilege Access: Provide users with the minimum access necessary to perform their relevant job functions - nothing less and nothing more. This follows the Principle of Least Privilege (POLP), which, in turn, lowers potential risks of misuse and abuse (especially insider threats) and reduces potential lateral movement in case of compromise. In order to implement POLP, there needs to be strong mappings of roles to access, access bundles that fit job responsibilities, and constant revisions to ensure alignment with business and compliance needs.
- Enable Just-in-Time Provisioning: This is particularly important for external, contractor, or temporary resources. Allow access for clearly defined timeframes, then take it away automatically when the access is no longer needed.
- Log and Monitor Everything: Every access grant and revocation should have traceability, verification, and justification. We should retain documentation and records to keep a detailed audit log, as it will assist with forensic readiness and help establish trust in the end process.
- Review Access Regularly: Recertification of access at intervals to understand how it continues to align with the business function should be done. Use certification campaigns that are automated to recertify the organization with respect to sensitive systems and users in a high-risk category.
Common Pitfalls to Avoid
Provisioning and deprovisioning missteps can lead to security incidents, audit failures, and operational inefficiencies. The following are the most common identity governance gaps seen in enterprise environments:
- Manual Provisioning Errors: Using ticketing systems or spreadsheets for approvals introduces delays, inconsistency, and risk. Whether accidentally mis-entering a role, forgetting to provision apps, or something else along the way, mistakes with manual entry lead to over-privileged users or access gaps that stifle productivity.
- Failing to Revoke Access Promptly: The longer an individual retains access after leaving, or if their role changes, the greater the risk of insider threats, data being removed or modified, and non-compliance in reporting because of access privileges. Without automation for HR-driven deprovisioning, the capability to immediately deactivate accounts upon role change or close of employment may remain active for several days, or sometimes even weeks, after an employee has left an organisation.
- No Integration with HRIS: IT teams are left working with out-of-date identity data if they don't have direct integration with a Human Resource Information System (HRIS) of record, such as Workday or SAP. A significant reliance on manual departmental coordination, outdated access rights, and mismatched roles are the results of this disconnect.
- Overreliance on AD Without App Context: Although Active Directory may be the primary source for your network access, many SaaS apps work outside of it. So while you should be assuming your changes in AD will be reflected in your cloud environment, if not monitored properly, you could have blind spots where orphan access stays active.
- Ignoring Temporary or Contractor Accounts: Contractors, interns, and other vendors will usually get full-time equivalent access without proper oversight. If we don't practice expiration policies, review entitlements, and limit access scope, we can have excessive or over permissions and expose things unnecessarily after their "engagement."
Steering clear of these traps depends on intentional alignment, automation, and constant Access Management Lifecycle governance.
Provisioning & Deprovisioning in the Context of IGA
Provisioning and deprovisioning are not isolated IT functions; they're the operational core of a mature Identity Governance and Administration (IGA) strategy. IGA solutions provide organizations with products to build policies, apply them consistently, track compliance, and respond to identity incidents in real time.
Implementing user provisioning and deprovisioning as part of a central IGA experience like Identity Confluence provides the organization:
- Policy Enforcement and Access Certifications: Access decisions are predetermined rules and periodically reviewed through automated campaigns. These processes align with security policies as well as regulatory requirements.
- Role-Based Access Reviews: IGA platforms provide finely-ground access reviews based on business roles that shrink IT burden and enable managers to make careful decisions.
- Access Management Lifecycle Workflows: Joiner-Mover-Leaver processes are automated end-to-end from HR trigger to account provisioning to real-time deprovisioning, ensuring no manual gap compromises compliance or security. In summary, Identity Governance turns provisioning into more than a single task; it becomes a constantly governed activity that scales dynamically to business and security needs.
Provisioning and deprovisioning are not two separate processes; they are two actions from the broader Identity Governance & Administration (IGA) method.
Identity Confluence embodies this by:
- Aligning every access decision to policy
- Integrating role management, certifications, and access reviews
- Identifying outliers through identity analytics.
In other words, you don’t just manage access. You govern it.
📩 Prefer to start a conversation? Email us at info@techprescient.com
Frequently Asked Questions (FAQs)
1. What is the meaning of user provisioning and deprovisioning?
User provisioning refers to the automated process of creating user accounts and assigning access based on business roles and policies. Deprovisioning is the reverse; it ensures access is revoked promptly when users change roles, leave the organization, or no longer require specific permissions. Together, they form the foundation of secure Access Management Lifecycle.2. How does automatic deprovisioning work?
Automatic deprovisioning continuously monitors changes in HR or identity systems (e.g., employment termination or role change) and immediately triggers account disablement across all connected applications. It uses Access Management Lifecycle policies to enforce consistent access removal, ensuring no accounts are left active inadvertently.3. Why is deprovisioning important for security?
Dormant or orphaned accounts are one of the most common causes of insider threats and audit violations. If access isn’t revoked immediately, former employees or vendors may retain entry into sensitive systems, putting data at risk and compromising compliance.4. What are the steps in user provisioning?
User provisioning typically involves- Identity creation,
- Mapping user attributes to roles,
- Assigning policies and permissions,
- Provisioning app access, and
- Continuous monitoring for changes.
5. How do IAM tools support provisioning?
IAM platforms like Identity Confluence integrate with HR systems and directories using SCIM, SAML, and APIs to automate access provisioning. They apply role-based logic, track every change, and maintain audit-ready logs for compliance.6. What happens if provisioning and deprovisioning aren’t automated?
Manual workflows often introduce delays, inconsistent access, and increased risk of misconfiguration. This leads to audit failures, over-privileged users, and security gaps due to human error.7. What systems typically integrate with provisioning/deprovisioning?
Leading IAM solutions integrate with HRIS systems (like Workday, SAP) to trigger lifecycle events, directories (e.g., Active Directory, Azure AD) for core identity control, and SaaS or collaboration apps (like Salesforce, Office 365, Zoom) to ensure consistent identity governance across the environment.8. How often should access be reviewed?
Access should be reviewed periodically (e.g., quarterly or biannually), especially for high-risk roles and sensitive systems. Automated certifications help reduce review fatigue and maintain compliance across the organization.