What Is an Orphaned Account? Definition, Risks & Fixes

An orphaned account is a digital identity that remains active but is no longer tied to a valid user. These accounts often exist long after an employee has left the company or a contractor has completed their project. In enterprise environments with multiple directories, cloud apps, and identity silos, orphaned accounts are common security blind spots.
They typically arise due to poor offboarding practices, manual identity management, or a lack of HR–IAM integration. They introduce unnecessary cost in dollar terms and pose access risks, as they are prone to hacking.
Orphaned accounts are a genuine threat existing in many organizations: digital identities that are still active after the employee with the account has left or has changed job roles, or even after the completion of a contract or a contractor. Orphaned accounts result in ungoverned access to sensitive data, unauthorized access, and, in many cases, the cause of a data breach or compliance violations. Orphaned accounts represent a serious failure of user lifecycle governance in Identity and Access Management (IAM). With the right design and controls, including IAM automation, real-time HR integrations, and regular access reviews, an organization can identify ghost accounts and can terminate orphaned accounts before they create a risk.
Key Takeaways:
- What orphaned accounts are and why they exist
- How they create hidden security and compliance risks
- Real-world examples across industries like finance and healthcare
- Best practices to detect, prevent, and decommission orphaned accounts
- How IAM and IGA tools (like Identity Confluence) solve this problem
What Is an Orphaned Account?
An “Orphaned Account” occurs when a user account exists in your organization’s systems but doesn’t reside with any current employee, contractor, or other legitimate identity. These accounts are still usable, and they can still access internal systems, applications, and data, but no one actively owns or tracks them. An active user account, on the other hand, belongs to a real person who is a current employee of the organization, with clear ownership, access justification, and lifecycle visibility.
Simply put, let’s say there’s a content marketer who worked for your organization for five years before recently moving on to another role. During the offboarding process, she had most of her accounts disabled: email, Slack, project tools, etc. However, one account remains active, an old login to a legacy CMS that she hardly used. That account still works and has publishing access. No one is watching that account, and no one remembers that it exists.
Extrapolate that risk across hundreds of employees, cloud apps, vendors, and integrations, and it becomes obvious how little orphaned accounts quietly aggregate and expand your attack surface.
The Dangers of Orphaned Accounts
When it comes to Identity and Access Management (IAM) environments, orphaned accounts can be exceptionally dangerous because they operate outside normal governance structures. Specifically, these orphaned accounts have the following characteristics: they do not have an active HR profile, manager, or business owner, and therefore, they:- Do not participate in lifecycle automation workflows (Joiner–Mover–Leaver)
- Do not partake in periodic access certifications
- Skip behavioral analytics or policy-based deprovisioning
- Oftentimes retain privileged levels or access to sensitive systems
Even though they are not actively used, they still typically contain valid login credentials, API tokens, or SSO access or can plug in via integration hooks. Clearly, they are attractive targets for exploitation.
Common Sources of Orphaned Accounts:
Despite best intentions, most organizations unintentionally accumulate orphaned accounts over time - often because of process gaps, integration failures, or lack of role clarity. These accounts don’t just appear in one system - they can span across Active Directory, SaaS platforms, cloud infrastructure, and even internal DevOps tools.Here are the five most common and high-risk sources of orphaned accounts you need to audit for:
1. Ex-Employees Offboarded from HR, but Not IAM
This is the most widespread and dangerous cause. When an employee exits the organization, their status is updated in the Human Resources Information System (HRIS) (e.g., Workday, BambooHR, SAP), but the identity systems - such as Active Directory, Okta, Azure AD, or custom apps - aren’t automatically notified.2. Contractors and Third-Party Vendors Without Auto-Revoke Policies
Contract-based workers, freelancers, MSSPs, and technology partners are often granted temporary access to internal systems. However, they frequently bypass the standard onboarding/offboarding process because:- They aren’t stored in core HR systems
- Their access is provisioned manually
- End dates aren’t enforced in IAM tools
3. Temporary or API Accounts Created for Projects or Testing
These accounts are usually created for:- Pilot programs
- QA/testing environments
- DevOps workflows
- Temporary service-to-service integrations
But because these are often provisioned outside formal identity workflows, they lack:
- Assigned owners
- Role expiration rules
- Central visibility in IAM systems
4. Cloud-to-Cloud Integrations Without Assigned Ownership
As enterprises migrate to SaaS and hybrid environments, they often connect systems like:- Slack → GitHub
- Salesforce → Marketo
- Azure AD → Zoom
- ServiceNow → AWS
These integrations typically rely on machine accounts, integration tokens, or OAuth-based connectors. But during re-orgs, team changes, or migrations, the owner of the integration is removed - yet the connector continues functioning.
The hidden danger:
The integration account becomes an IAM orphan. It continues to sync, push, or pull data - without anyone monitoring or revoking its access.
5. Shared Accounts That Persist Across Team Transitions
Despite being discouraged by IAM and cybersecurity best practices, shared credentials are still common in:- Small IT teams
- Field sales
- Remote support operations
- Operational technology (OT) environments
These shared accounts often have:
- No unique identity tied to a user
- High levels of privilege (e.g., “admin,” “support@company.com”)
- No multi-factor authentication (MFA)
When users sharing the account leave or change teams, no action is taken - because no single person “owns” the account
Synonyms and Related Terms
The terminology around orphaned accounts may differ depending on the context - whether it’s an audit report, a cloud security tool, a Governance, Risk, and Compliance (GRC) platform, or an IAM engineer’s daily workflow. Understanding these alternate terms is critical for expanding your detection and monitoring logic across various systems, reports, and teams.Below are the most commonly used synonyms and how they show up in real-world environments:
1. Zombie Account
A zombie account refers to an account that appears inactive - i.e., it hasn’t been used in a long time - but is technically still enabled, authenticated, and active. Like zombies in movies, they’re supposed to be “dead” but are still operating silently in the background.2. Stale Account
A stale account is similar but subtly different. It usually refers to an identity that hasn’t had a recent login or activity - for example, no sign-in events in the last 90 days - but it may still be valid and assigned to an active user.3. Inactive Account Without Ownership
This is a more formal, audit-facing term used in compliance reports, IAM logs, and GRC platforms. It indicates an account that shows:- No associated user profile (e.g., HRMS has no matching employee ID)
- No clear business owner or manager
- No login or access activity
- But still has access entitlements in one or more systems
4. Ghost Login
This is a commonly used informal term widely used by IT administrators, auditors, or cybersecurity analysts. It refers to any login that is- Still functional
- Not listed in current HR, user provisioning, or onboarding systems
- Appears in system logs or authentication events (e.g., VPN, RDP, SSH)
Pro Tip:
Every orphan account always starts off as a legitimate identity, but once ownership is lost, it becomes risky and concerning if left unattended. To mitigate this, organizations must develop an approach to identify, monitor, and govern them continuously. Managing orphaned accounts is not a one-time event; it is an ongoing identity and access management (IAM) and compliance team's responsibility to ensure orphan accounts are detected, monitored, and appropriate owners are assigned to them.
Orphaned accounts represent a loss of visibility, context, and control. The longer they remain undetected, the greater the risk of privilege escalation, policy drift, or data exposure.
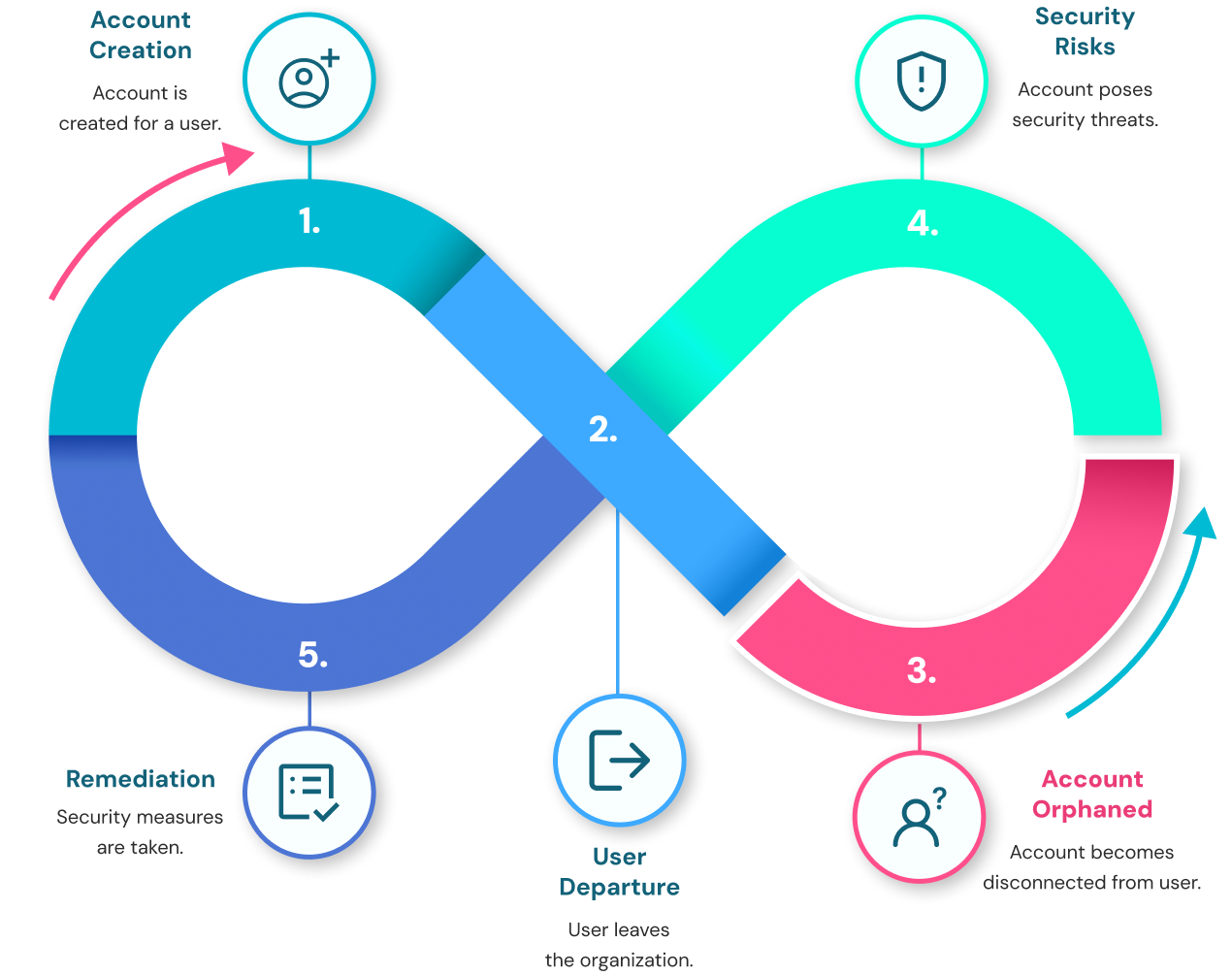
Why Do Orphaned Accounts Exist?
Orphaned accounts are not created maliciously - they are the byproduct of breakdowns in identity lifecycle governance. These breakdowns occur when people, systems, or processes fail to close the loop between user status changes and access control enforcement.
Common Causes of Orphaned Accounts:
While each organization’s identity architecture may differ, the root causes of orphaned accounts tend to fall into five consistent categories:1. Employee Turnover Without Timely Access Revocation
When employees resign, retire, or are terminated, access should be removed immediately upon exit. However, in many organizations:- Deactivation relies on manual coordination between HR and IT
- Shared drives, SaaS apps, or VPN credentials are overlooked
- Custom access outside the central IAM system isn’t tracked
Why does this happen?
There is often no unified offboarding workflow across HRIS, IAM, and application owners. This leads to a gap between status change and access enforcement.Result:
Former employees retain access to sensitive systems - including customer data, financial records, or source code - without being detected.2. Incomplete or Manual Offboarding Workflows
Even in organizations with formal offboarding checklists, manual execution is error-prone. IT teams often manage dozens of user systems (email, ERP, cloud infrastructure, CRM, and ticketing tools), and without automation, it’s easy to miss something.Why this is dangerous:
These oversights often create stale identities that remain active - but hidden - in non-core systems, especially Shadow IT.3. Cloud Migrations That Duplicate or Ignore Old Accounts
As organizations transition from on-premise to cloud-native infrastructure, identity data is often migrated imperfectly. Legacy user accounts from systems like LDAP, AD, or internal databases are:- Duplicated in cloud IAM systems (e.g., Okta, Azure AD)
- Not mapped correctly to current HR profiles
- Forgotten altogether if they're outside the scope of the project
What this causes:
Accounts that existed before the migration are left active in the new environment - but no longer tied to any business owner or employee.Extra risk:
Migration tools often grant default roles post-migration - meaning that a stale or duplicate user could end up with elevated access in the cloud without anyone noticing.4. Third-Party and Vendor Access Without Expiration Policies
Often, contractors, auditors, freelancers, and external technology partners are granted access to internal systems via service accounts, which are non-human identities for automated processes or vendor integrations.However, these accounts:
- Don’t exist in your HR system
- They are typically not tracked at all in centralized IAM dashboards
- They usually don't have automated deprovisioning or expiration policies
The project ends, but the service account never deactivates, operating with some level of powerful privileges like S3, database roles, remote desktop credentials, or persistent SSH keys. These non-human accounts, because they typically operate in the background, have little to no human oversight assigned to monitor or remove them.
Real-world example:
The contract is finished with the third-party IT security vendor; however, the vendor’s service account, with VPN and remote desktop access, is never disabled. Months later, the account now has backdoor access and creates an unmanaged risk by allowing unauthorized access or, worse, exfiltration of company data.Third-party identities are more likely to avoid MFA, access reviews, and internal compliance because they are “external". These identities are often one of the most dangerous forms of orphan accounts, invisible, over privileged, and exploitable.
5. Poor HR-IAM Integration
Perhaps the most foundational issue is that if your Human Resources Information System (HRIS) and Identity Governance Platform don’t communicate in real-time, you can’t build a responsive access control system.Modern IAM solutions like Tech Prescient’s Identity Confluence close this gap by enabling policy-based automation triggered by HR events (e.g., terminations, transfers, extended leaves).
Real-World Example:
- A contractor was hired for a 90-day finance automation project and was given access to the organization’s ERP system, internal dashboards, and an SFTP server for file uploads. When the project ended, their HR status was updated - but their IAM identity wasn’t revoked.
- Eight months later, during a SOX compliance audit, the orphaned account was discovered still active, with permissions to access payroll files. It had no recent login activity but was never included in the company’s access reviews or deprovisioning reports.
Outcome:
The organization was flagged for a SOX compliance violation when auditors identified an active orphaned account that had access to sensitive payroll systems. Although the account had no recent activity, it had bypassed the routine access review and automated deprovisioning workflows altogether. The company was required to formally disclose the incident, perform a full access audit for the orphaned accounts, and spend weeks discovering and remediating similar identity governance gaps, ultimately revealing systemic deficiencies in their user lifecycle management process and risk posture.Risks of Orphaned Accounts
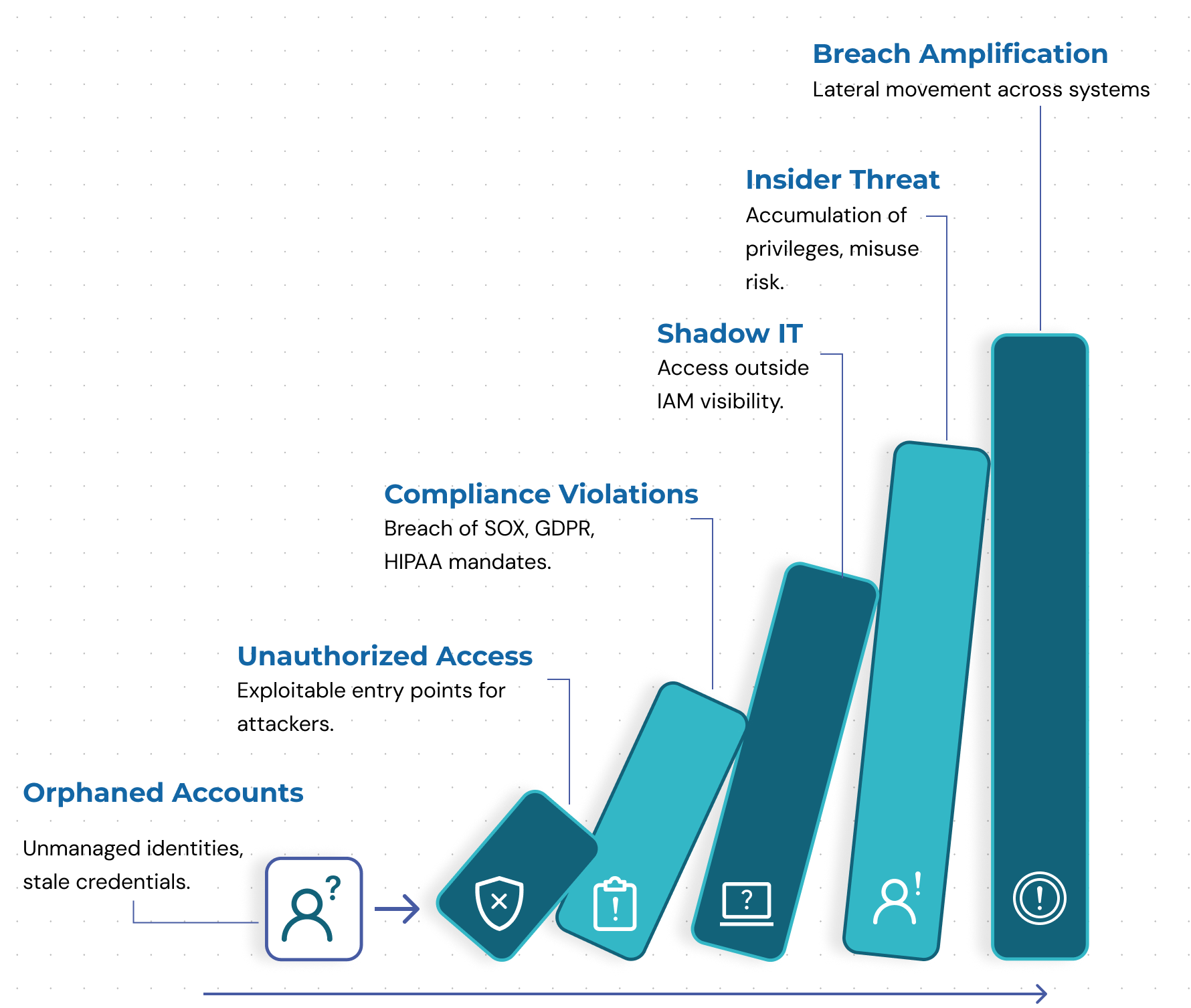
Orphaned accounts are more than just forgotten credentials - they represent a critical failure in identity governance. Because they lack an active owner, they fall outside the scope of regular audits, access reviews, and behavioral monitoring - making them ideal targets for both external attackers and internal misuse.
Below are the most pressing risks orphaned accounts introduce across security, compliance, and operational domains:
1. Unauthorized Access Vectors
Orphan accounts usually still have access to critical systems, sometimes with high privileges like administrator, database owner, or cloud root roles. Because these identities are not tied to a current employee, contractor, or managed entity, they fall outside of normal monitoring and governance procedures.Threat vectors include:
- Attackers are taking advantage of leaked credentials or dead API keys
- Former employees who are logging in after they have left the company using credentials that are still active (for example, in Active Directory, Google Workspace, or Salesforce)
- Automated scripts or service accounts that have leftover access tokens embedded in legacy workflows
Insights:
In many examples of breaches in the real world, orphaned credentials were the entry point for the attacker. According to a New York Times article, the Capital One breach in 2019 was facilitated by a former employee of a cloud service company who enabled an attacker to exfiltrate over 100 million records from a dormant IAM role with elevated privileges that had misconfigured permissions. This was possible even with the account appearing inactive.The example illustrates how unmonitored, orphaned, or misconfigured identities, especially ones with persistent credentials as in this example, can serve as silent backdoors into sensitive environments.
2. Compliance Penalties (HIPAA, SOX, GDPR, ISO 27001)
Regulatory compliance frameworks mandate that user access must be revoked promptly upon role change or termination. Orphaned accounts directly violate these mandates and expose organizations to:- Audit failures: Security and compliance teams can’t explain why the account still exists or who owns it.
- Fines and sanctions: Regulators can impose heavy penalties for improper user access management.
- Incident escalation: In the event of a breach, the existence of orphaned accounts can be cited as negligence.
Examples by standard:
HIPAA:
HIPAA, the Health Insurance Portability and Accountability Act, is a federal law in the U.S. that regulates national standards for the privacy and security of a person's health information. With respect to the HIPAA Security Rule, covered entities must disable user access to Protected Health Information (PHI) in a timely manner when employees or contractors leave the organization.What is PHI? An example of PHI is an individually identifiable health information, like medical records, treatment history, or someone's health condition, which is specifically related to demographic information about a person.
Neglecting to deactivate orphaned accounts that have access to PHI violates your HIPAA obligations, which can have significant consequences from fines to reputational loss. The stakes are even higher in the healthcare context, where the sensitivity of data means that audits could draw more scrutiny.
SOX:
SOX, short for the Sarbanes-Oxley Act of 2002, represents a federal law in the United States that mandates strict requirements for financial reporting and internal controls for publicly traded companies. The main purpose of SOX is to promote transparency, deter corporate fraud, and protect investors by imposing liability on organizations related to their financial statements.Part of this responsibility includes ensuring that access to financial systems is:
- Traceable: every user action must be logged
- Revokable: access should be certified periodically
- Role-based: only those who are authorized should be able to access any financial data or systems.
Orphaned accounts violate these requirements by creating untraceable access paths. This may make it extremely difficult to perform SOX compliance audits, and they result in an increased risk of financial misstatements or fraud.
GDPR:
The General Data Protection Regulation (GDPR) is an EU regulation that governs how an organization collects, processes, and stores the personal data of its diverse citizenry or market. To comply, the GDPR requires data controllers to ensure that only those authorized have access to personal data, thereby reducing exposure to unauthorized use or exposure. Orphaned accounts and active accounts to which no owner has been assigned circumvent this requirement by creating unauthorized access paths to sensitive information.3. Shadow IT and Unmonitored Access
In large, fast-moving organizations, teams often create user accounts in third-party tools like Slack, Trello, GitHub, or SaaS CRMs - without going through central IT.When those employees exit, these tools are often forgotten:
- The Slack account is removed, but the user’s OAuth tokens still allow GitHub access.
- A Google Sheet shared with a Gmail account remains editable by a departed intern.
- A former contractor still appears in the Trello board with full edit permissions.
This is shadow identity risk - where access exists outside your IAM platform. These orphaned identities are invisible in standard access reviews, yet they remain fully functional.
4. Insider Threat Enablement
While most insider threats are unintentional (e.g., employees clicking phishing links), orphaned accounts increase intentional misuse risk:- A disgruntled ex-employee could use leftover access to delete data or expose sensitive information.
- Vendors with expired NDAs may still access client repositories or internal knowledge bases.
- Misuse is hard to detect - the access trail leads to a deactivated or non-existent user.
Because no active user is associated with the account, alerting, monitoring, and accountability all break down.
5. Breach Amplification and Lateral Movement
Once an attacker gains a foothold in your network, orphaned accounts help them move laterally:- Legacy service accounts often lack MFA or logging
- Orphaned accounts with over-permissioned roles can unlock databases, file shares, or production systems
- No business owner is responsible for those accounts—so they're rarely reviewed or questioned
In security incident response investigations, orphaned accounts frequently show up as privilege escalation paths, especially in cloud-native environments.
Our Expert Quote
“Orphaned accounts are the invisible enemies of enterprise security. They bypass identity governance controls, escape certification workflows, and silently expand your attack surface - until an auditor or attacker finds them first.”How to Detect Orphaned Accounts.
Detecting orphaned accounts is not just about spotting idle users - it requires a multi-layered detection framework that accounts for ownership, activity, HR status, and entitlement relevance. Because orphaned accounts don’t announce themselves, your identity architecture must be proactive, not reactive.
Below are the core components of a robust orphan account detection strategy:
1. Regular Access Audits
Access audits are your first line of defense. These are structured reviews of user entitlements across applications, systems, and cloud environments - aimed at validating whether each active account is still:- Required
- Appropriate for the user’s role
- Tied to a legitimate, active business function
Key best practices:
- Run quarterly or biannual access certification campaigns
- Run reconciliation between target Applications and the Identity source (HRMS/HCM) to identify accounts without named users
- Use context-rich audit reports with last login, HR status, and assigned manager
- Prioritize privileged accounts, API/service accounts, and accounts with elevated roles
2. Automated Detection Tools
Manual review isn’t scalable. You need IAM platforms that continuously scan your environment for identities that:- Are not linked to any active user in HR systems
- Haven’t been used in a defined activity window
- Appear in logs but not in the centralized directory
- Exist in one system (e.g., Okta) but not another (e.g., AD or HRMS)
Risk signals to detect:
- Accounts without assigned managers
- Accounts without common user attributes, such as location, employment type
- Identities with no role or policy context
- Orphaned service accounts with persistent access tokens
3. HR System Syncs
An orphaned account almost always begins with an HR event that doesn’t flow downstream. That’s why real-time integration between your Human Resource Information System (HRIS) and your IAM platform is mission-critical.What happens without sync:
- HR terminates an employee, but IT is unaware
- IAM continues provisioning access based on updated department or title
- Offboarding delays allow the account to remain live and exposed
Key best practices:
Integrate platforms like Workday, SAP SuccessFactors, or BambooHR with your IAM tool via SCIM or REST APIs Use “termination effective date” as a trigger to auto-deprovision access Ensure access is removed not just from core systems, but also from SaaS, VPN, cloud, and developer tools4. Reviewing Logs and Activity Anomalies
Not all orphaned accounts are completely dormant. Some are used after a user has left—often by mistake, occasionally by malice. This is why log analysis is vital.What to look for:
- Login events from deactivated or delinked identities
- Access attempts from users not listed in HR
- API calls, VPN sessions, or system logins by users with ��“no active profile”
- Unusual login patterns (e.g., logins during leave of absence, weekends, or after termination)
Integrate with:
- SIEM platforms (Splunk, Sentinel, Chronicle)
- Endpoint logs, cloud access logs, and VPN logs
- IC’s built-in identity behavior analytics
5. Access Certification Workflows
A powerful way to detect orphaned accounts is through recertification campaigns - asking business stakeholders to review and revalidate the access of their teams.How it works:
- Campaigns are launched by app, department, or region
- Managers review a list of users and their entitlements
- Each account is reviewed for validity, activity, and business necessity
- Orphaned, inactive, or misaligned accounts are flagged for remediation
Orphaned accounts often persist because no one claims them. This process makes it someone’s responsibility.
Callout Tip:
The best way to maintain a secure posture is to tightly connect your HR and IAM systems, so that every employee lifecycle event (termination, leave of absence, internal role transition, etc.) automatically prompts notifications of access controls to ensure they are updated in real-time. Following this level of automation would mean orphaned accounts could be immediately highlighted or decommissioned to limit the amount of time they are at risk of exposure (as well as the space for insider threats or compliance contraventions). It is also important, once identified, for orphan accounts to be categorized into Non-Human accounts with owners assigned. This ensures that, for each account, ownership is established and their usage can be tracked. In short, make every account in the organization accountable.
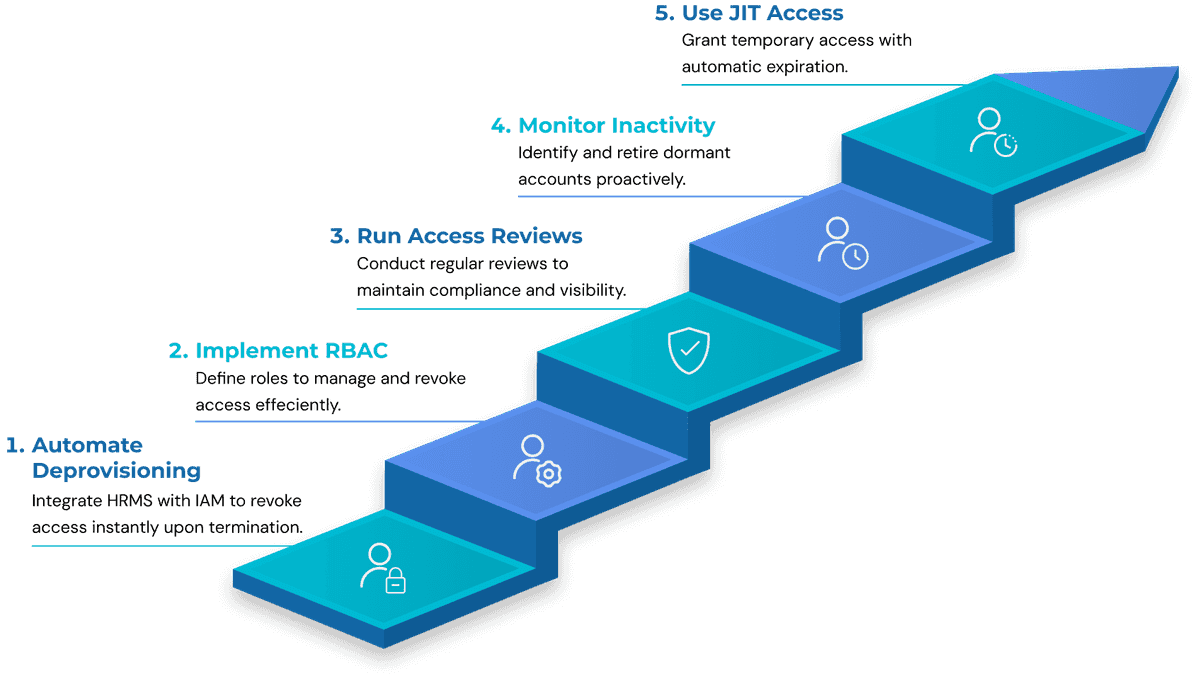
5 Best Practices to Prevent Orphaned Accounts
Preventing orphaned accounts isn’t just a good hygiene measure - it’s a core pillar of identity governance. Without proactive controls, organizations accumulate zombie identities that increase their attack surface, reduce audit readiness, and erode least privilege enforcement.
Here are the five most strategic and scalable practices to eliminate orphaned accounts in your IAM program:
1. Automate Account Deprovisioning
Why It Matters:
The biggest source of orphaned accounts is delayed offboarding. If HR terminates a user but IAM doesn't deactivate access instantly, that identity becomes a vulnerability - often with full system access.How to Implement:
- Integrate HRMS (e.g., Workday, SAP SuccessFactors, BambooHR) with your IAM platform
- Use real-time termination triggers to deactivate all linked identities - including those in SaaS apps, AD, cloud platforms, and internal systems
- Ensure system-wide revocation via SCIM, SAML, REST APIs, and custom connectors
2. Implement Role-Based Access Control (RBAC)
Why It Matters:
When access is assigned directly to individuals, tracking entitlements becomes complex and error-prone. RBAC enforces structure by granting access based on business roles - which are easier to govern, expire, and revoke.How to Implement:
- Define Business Roles like “Sales Executive” or “Finance Analyst” - each mapped to appropriate application roles.
- Align RBAC models with job functions, geography, employment type, and department
- Use attribute-based triggers (ABAC) to assign roles automatically based on user metadata
3. Run Quarterly Access Reviews (Access Certifications)
Why It Matters:
Orphaned accounts often persist because no one is reviewing them. Without regular access certifications, dormant or invalid identities remain invisible - until an audit uncovers them.How to Implement:
- Schedule quarterly certification campaigns across apps, departments, and roles
- Involve managers, app owners, and system administrators in certifying who still needs what access
- Include contextual metadata in review dashboards:
- Last login
- HR status
- Associated risk score
- Entitlement origin
- Review both standing access and elevated privileges (e.g., admin, root, finance role)
4. Monitor for Account Inactivity
Why It Matters:
Not all orphaned accounts are created by failed offboarding some originate from accounts that are simply abandoned. A user on leave, a long-retired service account, or a forgotten test identity can sit idle for months - yet still have access.How to Implement:
- Set inactivity thresholds (e.g., 30, 60, or 90 days)
- Track account login activity, token usage, and app interaction logs
- Flag accounts exceeding the threshold for review, auto-disable, or revalidation 4.Cross-reference inactivity with HR status to distinguish between legitimate idle users (e.g., parental leave) and true orphans
5. Enforce Just-in-Time Access (JIT)
Why It Matters:
Temporary users - such as contractors, vendors, auditors, or interns - often receive access without a clear expiration plan. This is a primary source of orphaned accounts, especially in fast-moving or outsourced environments.How to Implement:
- Mandate time-bound access requests with enforced expiration dates
- Integrate with ITSM tools (e.g., ServiceNow, Jira) to approve access just-in-time, not “forever.”
- Assign scope-limited roles based on purpose and risk level
- Automate revocation of all access when the timeframe lapses or the task is completed
Real-World Examples of Orphaned Account Risks
1. Finance: Unauthorized Transactions via Orphaned Payroll Account
In a mid-sized financial institution, a payroll analyst resigned, but their system account wasn’t fully deprovisioned. Although email and workstation access were removed, their internal financial application login remained active. Two months later, a compliance check uncovered unauthorized salary modifications traced back to this orphaned account. The breach triggered an internal investigation and highlighted serious gaps in the HR-to-IAM offboarding workflow.2. SaaS Company: API Integration Left Behind, Source Code Leaked
A fast-growing SaaS company disabled a user’s Slack access following their departure, but overlooked a connected GitHub API token tied to that user’s Slack identity. Months later, the integration was compromised through token misuse, resulting in a codebase leak. The breach occurred despite formal deactivation because the system treated the integration token as a separate identity - one that wasn't included in any access review or audit cycle.3. Healthcare: Retired Doctor’s Account Triggers HIPAA Violation
At a regional hospital network, a physician retired after four decades of service. While HR marked the doctor as retired, their Electronic Medical Record (EMR) account remained active. During a routine HIPAA audit, it was discovered that the account had been used to access patient data months after the doctor’s retirement. The organization was fined $500,000 for non-compliance and failure to implement timely deprovisioning.How IAM & IGA Tools Help Manage Orphaned Accounts
Preventing orphaned accounts at scale requires more than manual checklists or reactive audits - it demands automated identity governance frameworks. This is where modern Identity and Access Management (IAM) and Identity Governance and Administration (IGA) tools come in.
Capability | IAM (Identity Access Management) | IGA (Identity Governance & Administration) | Identity Confluence (IC): Unified IAM + IGA |
|---|---|---|---|
Core Focus | Automates identity lifecycle (joiner–mover–leaver) | Governs identity access with oversight, policy, and audit | Combines automation + governance in one platform |
Access Provisioning | Auto-assigns access on onboarding | Validates appropriateness of access via policy and reviews | Auto-provisioning based on roles, HR triggers, risk scores |
Offboarding | Triggers deprovisioning via HR exit data | Flags orphaned accounts during reviews | Real-time auto-deprovisioning + orphan detection |
Role Management | Supports role-based assignment | Defines RBAC/ABAC models for compliance | Visual role mapping with dynamic provisioning |
Policy Enforcement | Limited or manual | Policy-driven access approvals, SoD enforcement | Unified policy engine with risk thresholds |
Access Reviews | Not native – requires external support | Built-in campaigns, reviewer workflows | One-click access certifications with context |
Risk Analytics | Basic anomaly detection | Role conflict checks, access risk scoring | Flags stale, orphaned, and high-risk identities |
Audit & Compliance | Limited logging | Audit-ready trails (SOX, HIPAA, GDPR) | Real-time compliance dashboards, exportable logs |
Integration Scope | Directories (AD, LDAP), select apps | Enterprise systems, cloud, and SaaS apps | 50+ integrations via SCIM, SAML, REST, APIs |
Ideal For | IT provisioning, user management | Compliance teams, risk governance | Security, compliance, IT, and business teams |
IAM: Automating the Identity Lifecycle
IAM platforms focus on managing the identity lifecycle - from user onboarding to access provisioning, modifications, and offboarding. When integrated with HR systems and directories, IAM tools ensure that:- New joiners receive the right access instantly
- Role changes trigger automatic entitlement updates
- Leavers are automatically deprovisioned across all connected systems
This automation significantly reduces the likelihood of orphaned accounts resulting from manual offboarding delays, which are the most common source of identity drift.
IGA: Enforcing Governance, Policy, and Oversight
IGA tools extend IAM by adding oversight, certification, and policy enforcement layers. While IAM handles the “plumbing,” IGA ensures the access granted is appropriate, justified, and reviewable.Key IGA capabilities include:
- Access certification campaigns to regularly validate user access
- Role-based access control (RBAC) and attribute-based policies (ABAC) for scalable governance
- SoD (Segregation of Duties) policies to prevent toxic role combinations
- Audit-ready logs and risk scoring to support compliance efforts
With IGA in place, orphaned accounts are flagged during access reviews, policy violations are surfaced proactively, and all identities are traceable back to an active owner or business justification.
Identity Confluence: Bridging IAM and IGA in One Platform
Identity Confluence (IC) is a next-gen identity platform that combines IAM automation with IGA-level governance in a single, cloud-native solution.What sets IC apart:
- Real-time HRMS integration to trigger deprovisioning at exit
- Continuous access reconciliation across SaaS, AD, cloud, and internal tools
- Built-in risk analytics to flag inactive, overprivileged, and orphaned accounts
- Contextual access certification workflows with usage visibility and justification capture
- Audit-ready dashboards to prove control during SOX, HIPAA, GDPR reviews
Result: No account exists without a valid owner, business justification, or usage trail - drastically reducing the attack surface and ensuring regulatory readiness.
Want to understand how IAM and IGA differ - and why both are essential for a Zero Trust identity architecture?
IAM vs IGA: What’s the Difference?
Frequently Asked Questions (FAQs)
1. What is an orphaned account in IAM?
An orphaned account is an active user identity within an Identity and Access Management (IAM) system that no longer corresponds to a valid, known, or employed user. This typically occurs when offboarding processes fail - such as when HR marks an employee as exited, but their system access isn’t revoked. Orphaned accounts often persist in directories (e.g., Active Directory), SaaS apps, or cloud platforms without ownership, justification, or audit visibility.2. Why are orphaned accounts dangerous?
Orphaned accounts are unmonitored backdoors into your environment. Since they have no owner, they often escape routine access reviews, MFA enforcement, and behavioral monitoring. This makes them prime targets for:-
Insider threats
-
Credential theft or reuse
-
Privilege escalation attacks
-
Compliance failures (HIPAA, SOX, GDPR)
They violate the Zero Trust principle by retaining standing access without active validation or contextual relevance.
3. How do you find orphaned accounts?
Detecting orphaned accounts requires a combination of automated IAM intelligence and cross-system correlation:-
HR-IAM synchronization to flag users who’ve exited but still have access
-
Access certification workflows involving business owners
-
Login inactivity tracking (e.g., accounts unused for 90+ days)
-
Orphan detection rules in tools like Identity Confluence, SailPoint, or Okta
Proactive detection relies on aligning identity context (HR, directory, access) with real-time usage data.
4. Are orphan accounts the same as inactive accounts?
No, orphaned and inactive accounts are not the same. Inactive accounts can belong to legitimate users (e.g., employees on leave, seasonal workers, seldom-used service accounts) and should be under supervision or planned to be suspended or expired. Orphaned accounts are ownerless, unmonitored, and have no expiration logic. Orphaned accounts present a problem, especially if they have privileged access.5. What is an example of an orphaned account?
A common real-world case:An ex-employee’s Active Directory and Salesforce accounts remained active three months after departure. The credentials were later reused by a third-party contractor who found the credentials in an old email thread. The result? Unauthorized access to sensitive customer data, followed by a costly breach investigation and failed compliance audit.