About Client
Our client is a prominent provider of cloud-based communications to businesses and consumers who can communicate through any device using cloud-hosted chat, video, voice, and short message service.
We partnered with them to develop:
- An automated solution to deliver on all aspects of RBAC right from employee onboarding to employee off boarding.
- A fine-grained access control approach to set up clearly defined roles, permissions and protocols by implementing the principle of least privilege thereby reducing the risk of granting unwarranted access.
- An auditing and reporting functionality to provide objective insight, optimize operational efficiency, and ensure compliance with standards and regulations.
Business Need
Challenges
- Fill the gaps between the user interface and the OKTA identity management system in terms of how we communicate with it, what is stored in Okta, and then cascading of privileges to the various applications at the client side through our system, RBAC.
- Offer a provision to include approval of privileges by approvers and in turn provide accuracy to owners of applications with respect to access authorization controls.
- Facilitate managers to be in control of the level of access within their teams, give them the flexibility to change/redefine access level in a single click operation, and allow them to have a bird’s eye view of who has what level of access to what application/s in their teams.
- Role Clarity—For effective role assignment, access authorization, and employee eligibility, our platform should create new business roles and associated privileges based on comprehensive triggers and controls and perform periodic review of business role to application access mapping.
- Onboarding of New Employees/Department or Role Change/Off boarding—Our service should streamline the process of onboarding new full-time employees or third-party resources, handling department/role change, and off boarding employees.
Technical Details
Our system consists of two main applications — RBAC Admin Management and RBAC Provisioning. The deeper dynamics are given as follows:
RBAC Admin Management
The main personas are Admin, Owner, Approver, Manager and Auditor, which are managed through RBAC Admin Management as follows:
- Admin: This persona allows admin to manage users and other admins, add and deactivate business role (BR), add and remove applications list and related permissions keys, and manage business role owners and approvers. A BR can only contain those applications that are incorporated by the RBAC handlers. Thereafter, owners can add applications to BR and update the configuration of the application and send it for approval. Owners are validated by OKTA APIs.
- Owner: This persona deals with users who are responsible for managing individual business roles. It provides functionality of managing the addition/removal of applications and their respective permissions in a particular BR. Once the owner makes the changes, they are shared with an approver for approval, and the owner can also send reminders to the approver for follow-up purposes.
- Approver: This persona checks the configuration of BR with the specific application configuration. An approver cannot make changes to BR; sh/e can only approve or reject changes.
- Manager: This persona allows a manager to look at tickets created for a role change, which applications have been granted/revoked as part of role change and the corresponding user details. S/he can also assign a role to a new or existing user.
- Auditor: This persona is implemented as a part of compliance requirements. An auditor can only track the progress of any application in terms of user access to the application, roles assigned to the users, and changes requested/approved for the business roles.

RBAC Provisioning
The process of user login in the RBAC system is managed by Okta SSO. For providing permissions inside the web application, we are using Okta groups. For the assignment of a particular okta-group, we have defined the level of access in the web application. Any user with a valid assignment of any of the personas’ respective okta-group will be able to login into the web application.
The RBAC provisioning application is created inside AWS Cloud. When there is a change in Business Role (BR) for a specific user or when it is set/reset, the application is triggered by a REST endpoint from Okta workflow. It then triggers an automation workflow where application specific handlers work on provisioning and setting up appropriate access for a user or change access to applications based on BR Mapping. The same automation workflow is applicable in the case of deprovisioning roles.
In the case of reprovisioning, when BR mapping changes then RBAC finds all the users in that BR and forces provisioning calls for the concerned users.
API Gateway allows only Okta server IP addresses to access the Gateway REST API.
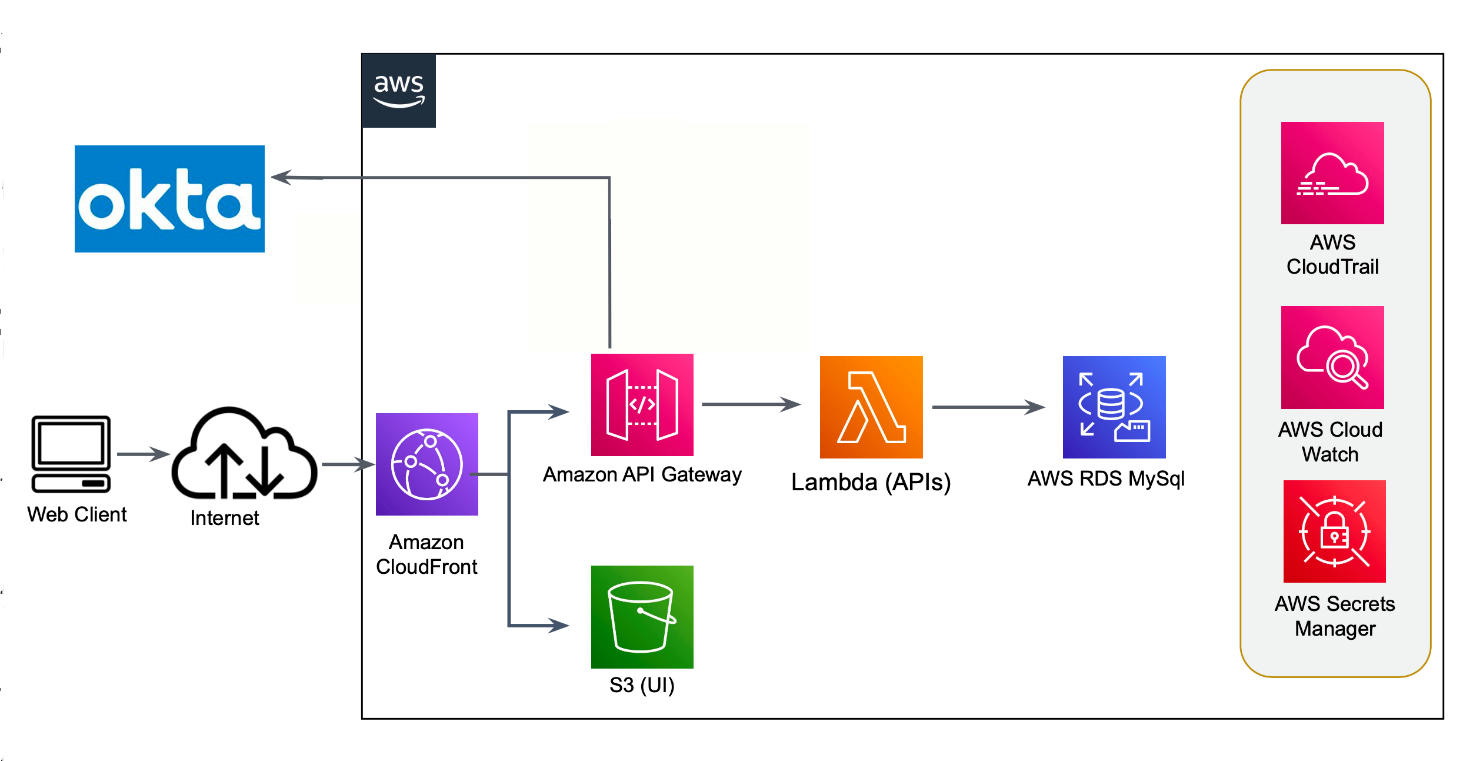
Architecture
The solution leverages AWS Serverless technology for hosting the web application. The following details provide a snapshot of the various technologies used to build the various components of the solution right from the user interface to the database management system.
- Front-End: UI is developed using the React.JS framework. It is hosted in AWS S3, and it is served by using AWS CloudFront. Lambda.
- Back-End: REST APIs are developed using AWS API Gateway and AWS functions.
- Database: AWS RDS serves as a persistent layer for the APIs. It is used to store RBAC web application data.
- Testing Automation: It is done using Selenium.
- Identity Management: Okta is used as an Identity Provider for the web application.
- Authorization: It is handled separately by using an authorization lambda that integrates with the API Gateway.
- AWS Secrets Manager: It handles the auditing and monitoring of service accounts credentials.
Business Impact
- Compliance: Compliance with standardized regulatory and statutory requirements related to security, confidentiality and privacy is made possible. The solution reduces risk of audit exceptions for new/modified access compliance requirements through the feature of periodic certification.
- Traceability: Comprehensible role creation and access authorization helps to trace and track which employee has been assigned which roles, approved by whom, and for what purpose.
- Auto approval of JIRA access tickets: This functionality saves a lot of time as managers need not to be chased for approvals because JIRA access tickets are auto-approved.
- Reduced administrative work: There is less administrative work as comprehensive rules and triggers are maintained and changed through our automated solution.
- Integration of new hires: The onboarding process is made smoother as there is crystal-clear clarity in roles and their related privileges.
Future Direction
- Scale the existing solution as a hub and spoke configuration in case the client includes new systems that hold raw, reference data.
- Integrate with mobile-based apps through APIs.
Technology









Tech Prescient was very easy to work with and was always proactive in their response.

The team was technically capable, well-rounded, nimble, and agile. They had a very positive attitude to deliver and could interpret, adopt and implement the required changes quickly.

Amit and his team at Tech Prescient have been a fantastic partner to Measured.

We have been working with Tech Prescient for over three years now and they have aligned to our in-house India development efforts in a complementary way to accelerate our product road map. Amit and his team are a valuable partner to Measured and we are lucky to have them alongside us.
We were lucky to have Amit and his team at Tech Prescient build CeeTOC platform from grounds-up.

Having worked with several other services companies in the past, the difference was stark and evident. The team was able to meaningfully collaborate with us during all the phases and deliver a flawless platform which we could confidently take to our customers.

We have been extremely fortunate to work closely with Amit and his team at Tech Prescient.

The team will do whatever it takes to get the job done and still deliver a solid product with utmost attention to details. The team’s technical competence on the technology stack and the ability to execute are truly commendable.







