
What Is Single Sign-On (SSO) and How It Works

Single Sign-On (SSO) is an authentication mechanism that enables users to access multiple applications with a single set of login credentials. Rather than logging in to each application individually, users only need to authenticate once using their username and password to seamlessly access all connected and authorized systems or SaaS applications.
Organizations frequently adopt Single Sign-On (SSO) to streamline authentication for employees who use multiple tools and platforms throughout the day. By integrating these applications under a unified authentication framework, IT teams can centrally manage user access, strengthening overall security while enhancing convenience and efficiency.
This approach is particularly valuable for remote workers and teams operating in cloud-based environments, as it removes the need for repetitive logins and helps minimize password fatigue. Notably, a recent study by HIPAA Journal found that 49 % of employees reuse the same credentials across multiple work applications, underscoring the importance of secure, centralized authentication systems.
In this blog we will cover everything you need to know about SSO: what it is, how it works, its benefits for users and organizations, associated security considerations, the key protocols (SAML, OAuth, OpenID Connect), real-world examples, how to implement SSO in your organization, how it fits into the broader identity and access management (IAM) landscape, and a look ahead at the future of cloud native and passwordless authentication.
Key Takeaways:
- Learn what Single Sign-On (SSO) is and how it enables one login for multiple applications.
- Understand how SSO authentication works through tokens like SAML, OAuth, and OpenID Connect.
- Explore the key benefits and security considerations of using SSO.
- Compare major SSO protocols and real-world examples from Google, Microsoft, and Okta.
- Discover how to implement SSO and its evolving role in future identity security.
What Is Single Sign-On (SSO)?
Single Sign-On (SSO) is an authentication method that allows users to access multiple applications or systems using a single set of login credentials. It enhances both security and user convenience by eliminating the need to log in separately to every app or service.
Think of SSO as your single access point. When you sign in once, for example using your Google account, you automatically gain access to other connected services like Gmail, Drive, or YouTube without having to enter your credentials again. This same concept applies in the workplace, where employees can log in once to access their company email, CRM, HR portal, and cloud-based tools.
At its core, SSO uses secure authentication protocols such as SAML (Security Assertion Markup Language), OAuth, or OpenID Connect to verify user identity across multiple platforms. This ensures that users remain authenticated across all integrated systems without compromising security.
Why It Matters?
Single Sign-On (SSO) is a cornerstone of modern Identity and Access Management (IAM) strategies. By authenticating users once and securely managing their sessions across multiple applications, organizations can achieve:
- Reduced password fatigue and fewer helpdesk password reset requests
- Stronger access control through centralized authentication policies
- Improved security visibility with consolidated access logs and audit trails
- Enhanced user experience with seamless access to connected systems
Ultimately, SSO streamlines authentication processes while maintaining stringent security standards, empowering users with effortless yet secure access to all their business-critical applications.
How Does Single Sign-On Work?
Single Sign-On (SSO) functions through a trust-based relationship between an Identity Provider (IdP) and multiple Service Providers (SPs). This relationship is built using digital certificates and authentication tokens such as SAML assertions, JWTs, or OpenID Connect (OIDC) tokens that securely verify a user’s identity across different systems. Once authenticated, users can move seamlessly between applications without having to re-enter credentials.
In essence, SSO acts as a bridge between users and applications, centralizing authentication while distributing access securely. To understand this better, let’s break down how the SSO process works step by step.
Step-by-Step Process
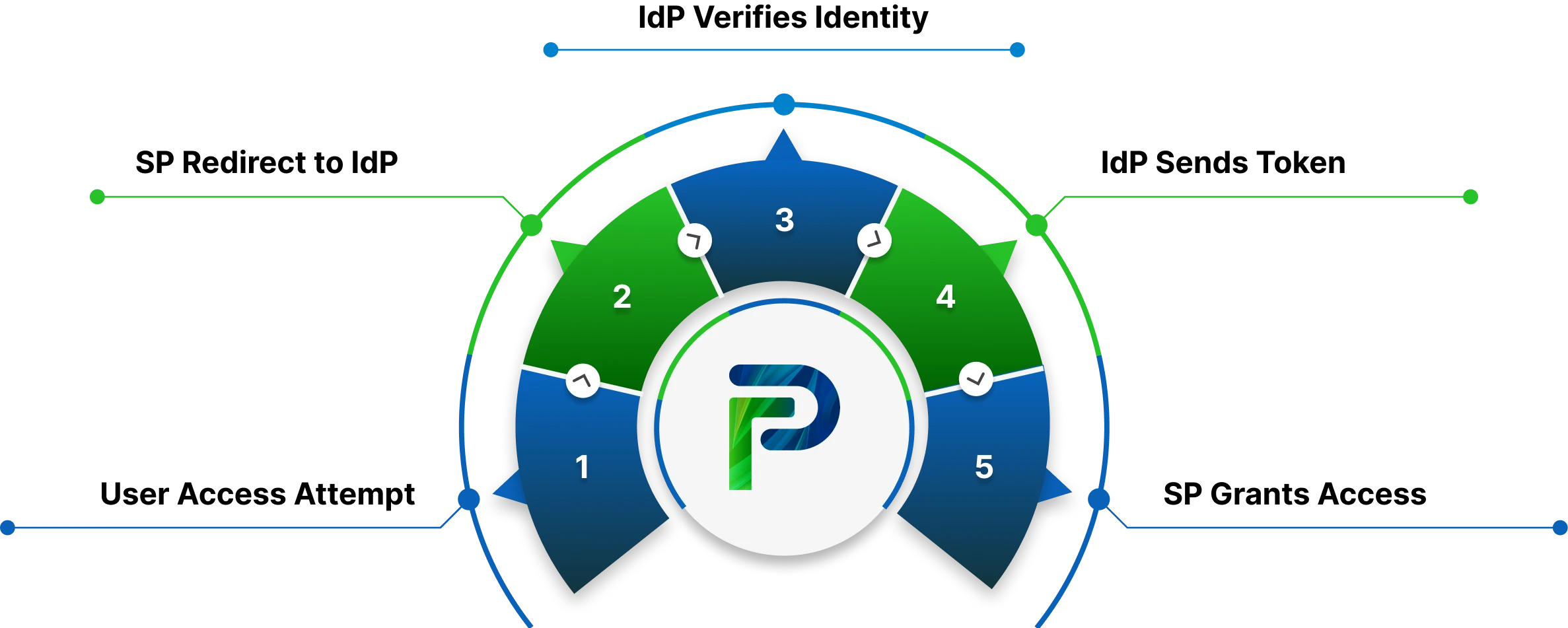
1. User Initiates Login
The process begins when a user tries to access an application or website, known as the Service Provider (SP). Instead of the SP managing authentication locally, it redirects the login request to a centralized Identity Provider (IdP) that is responsible for verifying user credentials.
This ensures that authentication happens only through the IdP, maintaining consistent security standards across all applications. The SP acts as the entry point, while the IdP handles the actual verification, simplifying login management for both the user and the organization.
2. Service Provider Redirects to Identity Provider
After receiving the login attempt, the SP generates a secure authentication request and redirects it to the Identity Provider. This redirection often uses industry-standard protocols like SAML, OAuth 2.0, or OIDC, which ensure encrypted and standardized communication.
By redirecting to the IdP, the SP offloads the responsibility of verifying user credentials, reducing risk and centralizing control. This also ensures that sensitive authentication data never passes directly through the SP, maintaining a higher level of data security.
3. User Authenticates with Credentials
Once redirected, the IdP checks if the user already has an active session. If not, the user is prompted to log in using credentials such as a username and password, or through advanced mechanisms like Multi-Factor Authentication (MFA), adaptive authentication, or device trust validation.
This step ensures that only authorized individuals gain access to the connected applications. The IdP’s verification methods can also include contextual checks such as device, location, or IP address to further strengthen identity assurance.
4. Identity Provider Issues Authentication Token
Upon successful authentication, the IdP generates a digitally signed authentication token, typically formatted as a SAML assertion, JSON Web Token (JWT), or OIDC token. This token contains verified identity attributes like the user’s email address, username, and access rights.
The digital signature ensures that the token cannot be forged or modified. This token is then passed back to the Service Provider through the user’s browser or a secure backend channel, confirming the user’s identity in a verifiable and tamper-proof manner.
5. Service Provider Validates Token and Grants Access
The Service Provider receives the authentication token and validates it against the trust relationship previously established with the Identity Provider. If the token’s signature and contents are verified successfully, the SP grants the user access to the requested application or resource.
From this point onward, as long as the session remains active, the user can access any other application within the same SSO ecosystem without re-entering their credentials. This streamlined experience reduces login fatigue while maintaining centralized security oversight.
Example
Consider the experience of signing into Microsoft 365. When a user logs in once through Microsoft’s Identity Provider, that single authentication session grants automatic access to multiple Service Providers within the ecosystem such as Outlook, Teams, and OneDrive.
The underlying trust relationship between the IdP and these applications ensures that each service validates the same authentication token, confirming the user’s identity without requiring another login. This unified access model not only enhances productivity but also strengthens overall security through centralized identity control.
Benefits of Using SSO
Implementing Single Sign-On (SSO) brings significant advantages for both users and organizations by enhancing security, simplifying authentication, and improving overall efficiency. By unifying access control under a trusted Identity Provider (IdP), SSO not only reduces password-related vulnerabilities but also streamlines daily operations, enabling users to focus more on productivity and less on login hassles.
Let’s explore how SSO benefits both users and organizations.
For Users
1. No Need to Remember Multiple Passwords
With SSO, users no longer have to juggle multiple usernames and passwords across different applications. A single secure authentication through an Identity Provider grants them access to all authorized apps within the SSO ecosystem.
This approach eliminates password fatigue and reduces the likelihood of password reuse or weak credential creation, which are among the most common causes of credential-based cyberattacks. Instead, users only need to maintain one strong, unique password for their primary login.
SSO eliminates this scenario by reducing all logins down to just one.By simplifying authentication, SSO provides users with both security and convenience, ensuring a smooth and frustration-free access experience across all platforms.
2. Faster, Seamless Access to Apps
By removing repeated login prompts, SSO delivers a fluid and frictionless experience across both cloud-based and on-premise applications. Whether employees are switching between productivity tools or customer management systems, authentication happens instantly in the background.
This streamlined login process saves valuable time and improves productivity, particularly in hybrid or remote work environments. Moreover, when combined with Multi-Factor Authentication (MFA) or adaptive authentication, users enjoy fast access without compromising on security.
For Organizations
1. Centralized Control Over Access
From an administrative perspective, SSO consolidates identity management into a single, centralized system. IT teams can define role-based access controls (RBAC) and enforce consistent authentication policies across all applications from one dashboard.
This centralization supports regulatory compliance frameworks like HIPAA, GDPR, and SOC 2 by maintaining transparent access logs and detailed audit trails. Organizations gain full visibility into who accessed what, when, and from where, enabling tighter governance and faster incident response.
2. Reduced Helpdesk Costs from Password Resets
Password management represents one of the most time-consuming IT challenges. With SSO, password-related helpdesk tickets drop significantly since users need to remember and reset only one credential.
Research shows that the average password reset takes about 10 minutes of employee time. In a company of 100 users resetting passwords twice a year, this can add up to over 33 hours of lost productivity. SSO not only minimizes this inefficiency but also frees IT teams to focus on strategic initiatives instead of routine password requests.
Simplified and Stronger Password Policy Enforcement With authentication centralized through SSO, IT teams can easily enforce consistent password security standards across the organization. For instance, if a company requires periodic password updates, SSO streamlines the process by managing it in one place instead of across multiple apps and services.
Although the need for frequent password resets is still debated, many organizations continue to treat them as an important part of their security framework. SSO makes these policies easier to implement while maintaining a balance between user convenience and strong access control.
3. Stronger Enforcement of MFA and Zero Trust
SSO acts as a foundation for implementing advanced security frameworks like Zero Trust Architecture (ZTA). It enables organizations to enforce Multi-Factor Authentication (MFA) and other security checks such as device trust, geolocation, or risk scoring at a single point of authentication.
By combining SSO with identity federation and adaptive access controls, businesses can ensure that only verified users access sensitive systems. This layered approach strengthens defense against credential theft, session hijacking, and unauthorized data access while simplifying security management across the enterprise.
Single Sign-On (SSO) not only enhances user convenience and productivity but also empowers IT and security teams with centralized visibility, better compliance control, and reduced operational overhead. It is a foundational step toward building a secure, scalable, and user-friendly identity ecosystem that aligns with modern digital workplace demands.
Is SSO Secure?
Single Sign-On (SSO) simplifies access and reduces credential fatigue by allowing users to log in once and gain access to multiple applications. However, because it consolidates authentication into a single access point, a weak or misconfigured SSO setup can become a single point of failure. To ensure robust protection, SSO must be paired with strong Multi-Factor Authentication (MFA), adaptive access controls, and continuous monitoring.
Security Advantages
1. Fewer Credentials Reduce Phishing
An effective SSO solution from a trusted provider strengthens enterprise security by minimizing the number of credentials users must manage. Instead of maintaining multiple weak passwords across different platforms, users rely on a single, strong set of credentials managed by an Identity Provider (IdP). This consolidation drastically reduces the risk of phishing attacks and credential reuse across vulnerable systems.
IT teams can also leverage centralized security policies that adapt to user behavior and login context. Built-in monitoring and threat detection tools help identify and block suspicious login attempts in real time, enhancing the organization’s defense against credential theft and brute-force attacks.
2. Easier to Enforce MFA and Password Policies
SSO simplifies the enforcement of critical security controls such as multi-factor authentication (MFA), password complexity, and access governance from one central interface. Administrators can define global authentication policies and apply them instantly across all connected applications.
For example, when an employee leaves the organization, IT can revoke all associated access in a single step, reducing the risk of unauthorized entry. This centralized approach also supports advanced MFA methods, including biometric verification and risk-based authentication, to deliver a secure yet seamless login experience.
3. Strengthened Compliance and Security Governance
By consolidating authentication through a single system, SSO makes it easier for organizations to meet regulatory and compliance requirements. Centralized visibility and control over user access help maintain compliance with frameworks such as GDPR, HIPAA, and SOC 2.
With audit trails, consistent password policies, and unified authentication management, SSO provides the transparency and accountability auditors look for, ensuring that both user convenience and compliance standards are upheld.
Security Risks
1. If SSO Credentials Are Compromised, All Linked Apps Are at Risk
While SSO enhances convenience, it also concentrates access risk. If a hacker compromises a user’s SSO credentials, they could potentially gain entry to all connected applications under that account. This risk increases when MFA is not enforced or when users become susceptible to push fatigue, approving fraudulent MFA prompts without verifying their legitimacy.
Moreover, misconfigured SSO integrations can create vulnerabilities that attackers may exploit. For example, incorrect token handling or poor session management can allow lateral movement across systems. Organizations must ensure that their SSO tokens are properly secured and automatically revoked if suspicious activity is detected.
2. Dependence on Uptime of the Identity Provider
Another risk of SSO lies in its dependence on the Identity Provider’s uptime and configuration. If the IdP experiences downtime or network failures, users may lose access to all dependent applications until the service is restored. To mitigate this, enterprises should choose reliable, scalable SSO providers that offer redundancy, failover systems, and 24/7 monitoring.
To further strengthen the setup, modern providers like Entrust enhance SSO with additional layers of protection such as token revocation, reauthentication triggered by unusual login behaviors, and passwordless authentication using biometrics or security tokens. These measures eliminate the weakest link in traditional password-based systems by removing passwords altogether, reducing the attack surface to near zero.
Different Types of SSO (Single Sign-On)
When exploring Single Sign-On (SSO), you’ll often come across related technologies and standards that may sound similar but serve distinct purposes. Understanding how these components work together helps clarify how SSO actually functions.
1. Federated Identity Management (FIM)
Federated Identity Management establishes a trusted relationship between two or more independent identity domains or systems. In simpler terms, it is a framework that allows users from one organization or domain to access resources in another without needing separate credentials.
SSO typically operates as a capability within a FIM setup. While FIM defines the trust framework, SSO provides the authentication experience enabled by that trust.
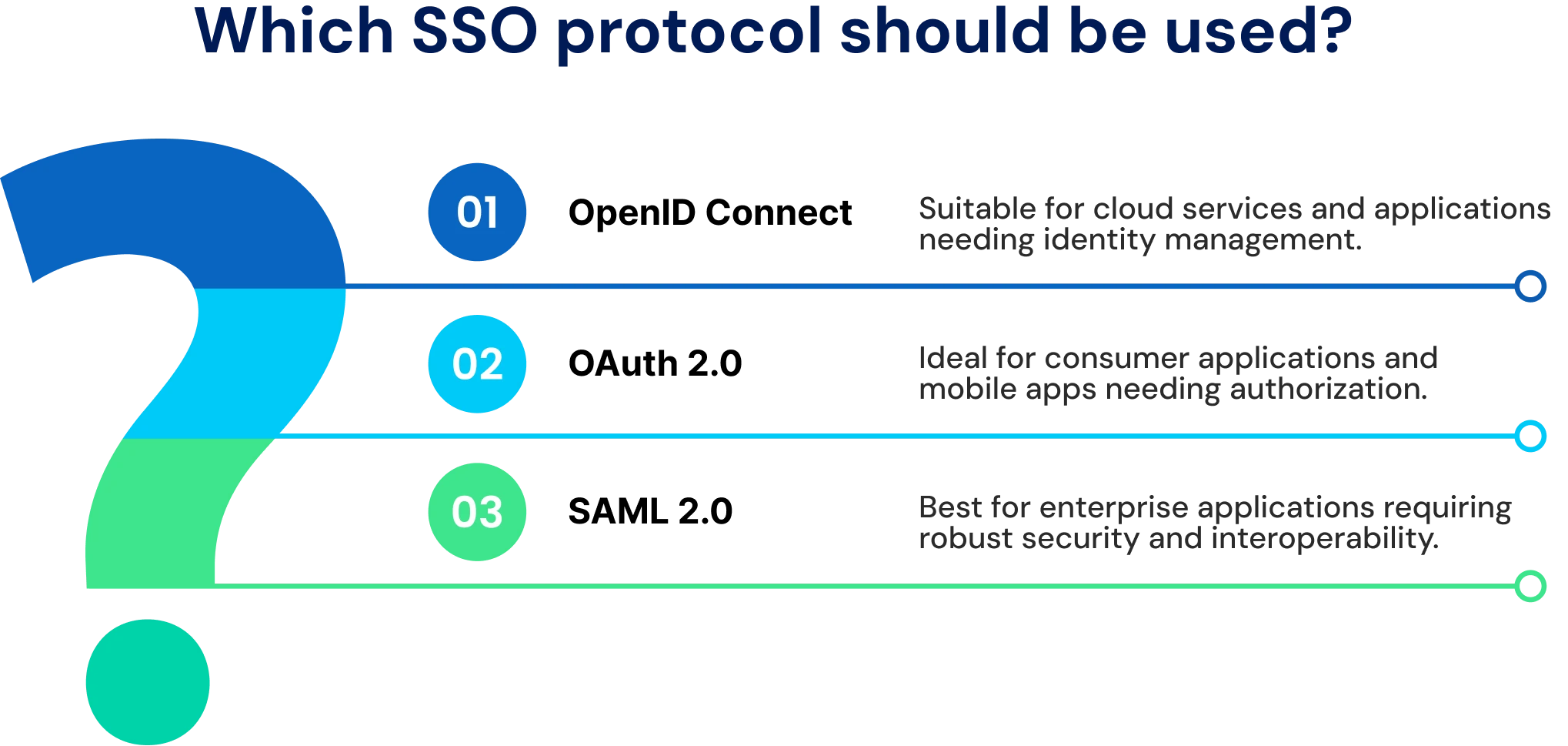
2. OAuth 2.0
OAuth 2.0 is an authorization framework designed to allow secure sharing of user data between systems without exposing credentials. Unlike an authentication system, OAuth does not verify who the user is. It simply grants permission for one system to access specific information or resources from another.
Think of it like this: “Allow this app to use certain details from your account elsewhere.” OAuth ensures this happens in a secure and controlled way.
3. OpenID Connect (OIDC)
OpenID Connect builds on top of OAuth 2.0 to add authentication, which is the process of verifying a user’s identity. OIDC enables true Single Sign-On by allowing users to authenticate once and gain access across multiple applications.
Today, most modern web and cloud applications implement OIDC and OAuth 2.0 together, using OAuth for authorization and OIDC for authentication.
4. Security Assertion Markup Language (SAML)
SAML is one of the earliest and most established standards for Single Sign-On, especially in enterprise environments. It uses XML-based messages to exchange authentication and authorization data between identity providers and service providers.
While it is considered older technology, SAML remains common in large organizations and legacy systems because of its reliability and compatibility.
5. Same Sign-On (Not the Same as SSO)
Same Sign-On is often mistaken for Single Sign-On but works quite differently. Here, users have the same username and password across multiple systems, usually because credentials are synchronized. However, each system still requires a separate login event.
Since there is no federated trust or token-based authentication involved, Same Sign-On is less secure than true SSO and does not offer seamless session continuity.
Common Identity Systems Supporting SSO
Single Sign-On relies on underlying identity systems that manage user credentials, access, and authentication across applications. These systems act as the backbone for enabling seamless and secure access within or across organizations. Below are some of the most widely used identity systems that support or integrate with SSO.
1. Active Directory (AD / ADDS)
Microsoft’s Active Directory is a centralized directory service that manages users and access within Windows environments. Using protocols like Kerberos and NTLM, it allows users to sign in once and access all connected systems, effectively providing SSO within an internal network.
2. Active Directory Federation Services (ADFS)
ADFS extends Active Directory’s capabilities beyond the internal environment. It supports standards such as SAML and OIDC, enabling federated authentication across organizations or with cloud identity providers such as Azure AD. This makes it possible to achieve secure SSO across different domains.
3. Lightweight Directory Access Protocol (LDAP)
LDAP is not an authentication protocol in itself. It is a standard for organizing and accessing directory data. It helps systems look up and verify user attributes such as identity and group membership before granting access.
While solutions like OpenLDAP can integrate authentication extensions such as SASL, LDAP alone does not deliver Single Sign-On. Instead, it supports access management as part of a broader identity system.
| SR No. | Term | What It Does | Role in SSO |
|---|---|---|---|
| 1 | FIM | Federated Identity Management establishes trust between two or more identity systems or domains. | Single Sign-On typically functions within this federated trust framework. |
| 2 | OAuth 2.0 | OAuth 2.0 provides a secure way to authorize one system to access specific data from another without sharing login credentials. | It enables secure, cross-domain access and facilitates authorization in SSO workflows. |
| 3 | OIDC | OpenID Connect verifies user identities while working alongside OAuth 2.0. | It provides true, modern, web-based Single Sign-On for cloud and web applications. |
| 4 | SAML | SAML authenticates users by exchanging XML-based assertions between identity and service providers. | It supports enterprise-level Single Sign-On, especially in corporate or legacy environments. |
| 5 | Same Sign-On | Same Sign-On allows users to use the same credentials across multiple systems without actual federated authentication. | It is often confused with SSO but is not true Single Sign-On, as it requires separate logins. |
| 6 | AD / ADDS | Active Directory serves as a centralized directory service that manages user credentials and permissions. | It provides internal Single Sign-On within Windows-based networks. |
| 7 | ADFS | Active Directory Federation Services extends AD capabilities to external systems using federated authentication protocols. | It connects internal AD users to external identity providers for secure, federated SSO. |
| 8 | LDAP | LDAP defines how directory data is organized, queried, and accessed across systems. | It assists in verifying user identities and access control but does not perform Single Sign-On on its own. |
Real-World SSO Examples
SSO simplifies access across ecosystems like Google Workspace and Microsoft 365, proving vital for both enterprise and consumer identity management. It brings together convenience and security, ensuring users can move seamlessly between tools and platforms without juggling multiple credentials.
In the real world, Single Sign-On is present across both personal and professional digital environments. Whether logging into cloud applications or internal business systems, SSO ensures every authentication request is consistent, secure, and user-friendly.
-
Google Workspace (Gmail, Docs, Drive)
When a user signs in to their Google account once, that single authentication grants access to Gmail, Google Docs, Drive, and other connected services without requiring another login. Behind the scenes, Google’s identity provider uses secure tokens to verify the user across its ecosystem. This setup enhances productivity and reduces the risks of password fatigue and credential reuse, which are common issues in multi-app environments. -
Microsoft 365 (Outlook, Teams)
In the Microsoft ecosystem, SSO works in a similar way. Once authenticated through Azure Active Directory, users can move between Outlook, Teams, SharePoint, and OneDrive without entering credentials multiple times. This unified experience extends to enterprise networks, allowing organizations to apply centralized security policies such as Multi-Factor Authentication (MFA) and conditional access across all Microsoft 365 apps. -
Corporate Systems Using Okta or Ping Identity
For large enterprises that manage a mix of on-premises and cloud applications, identity providers like Okta form the foundation of SSO. Employees authenticate once through a secure company portal and can then access various business applications such as Salesforce, Zoom, and internal HR systems without repeated logins. These solutions not only simplify access but also give IT teams better visibility, control, and compliance across all connected systems.
In essence, these examples show how SSO acts as the connection point between users and systems. Whether in cloud-based ecosystems like Google and Microsoft or in enterprise setups powered by Okta and Ping Identity, SSO improves security, reduces login friction, and delivers a seamless experience across all digital touchpoints.
Implementing SSO in Your Organization
Deploying SSO in an organization involves seamless integration between identity providers (IdPs) and service applications. The goal is to create a unified, secure, and frictionless authentication experience for users while ensuring strong identity governance and compliance.
Steps to Implement
- Choose an Identity Provider (IdP)
Begin by selecting a trusted Identity Provider (IdP) such as Okta, Azure AD, or Ping Identity. The IdP will store and manage all user identities and credentials. Ensure your chosen solution is scalable, compliant, and supports both on-premises and cloud-based environments depending on your organization’s needs.
Before finalizing, define clear implementation goals:
- Who are your different user groups, and what are their access requirements?
- Will the solution adapt to future business growth and integration needs?
- What security controls (like MFA or Device Trust) are essential for your environment?
- Integrate via SAML/OIDC Protocols
Next, establish trust between your IdP and each Service Provider (SP), which are the applications and services that will leverage SSO. Integration typically occurs using standards such as SAML 2.0 or OpenID Connect (OIDC).
During setup:
- Configure authentication flows that redirect users from the SP to the IdP.
- Ensure authentication assertions or tokens are signed and encrypted to maintain integrity and confidentiality.
- Validate that the chosen protocol aligns with your existing systems and compliance standards.
- Enforce Multi-Factor Authentication (MFA)
To strengthen authentication, implement MFA or Adaptive Authentication as part of your SSO flow. This ensures that only trusted users and devices can access your systems. Additional measures like IP Allow Listing or Device Trust policies can further reduce unauthorized access risks.
Follow the Zero Trust and the principle of least privilege, meaning users should only have the minimum permissions needed to perform their roles.
- Monitor and Audit Login Activities
Once your SSO solution is live, continuous testing and monitoring are key.
- Conduct pre-deployment testing to verify all integrated applications work as expected.
- After rollout, regularly audit authentication logs to detect anomalies, potential vulnerabilities, or unauthorized activity.
- Reassess integrations periodically as your ecosystem evolves to ensure sustained compliance and security.
In short, a successful SSO implementation is not just about connecting applications. It is about building a secure, adaptive, and user-first authentication framework that evolves with your organization’s growth and risk landscape.
SSO in Identity and Access Management (IAM)
Single Sign-On (SSO) is a core component of Identity and Access Management (IAM). While IAM encompasses authentication, authorization, and governance, SSO focuses primarily on verifying user identities and streamlining secure access across applications.
SSO plays a vital role in the broader IAM framework by authenticating users and granting appropriate permissions based on their identity. To function effectively, it should be integrated with access control mechanisms, activity logs, and user behavior monitoring tools. This ensures that user authentication is not only convenient but also auditable and compliant with enterprise security policies.
How SSO Compares to Other Access Management Solutions
- SSO vs. MFA
Single Sign-On (SSO) and Multi-Factor Authentication (MFA) address different but complementary aspects of access management.
- SSO simplifies access by enabling users to log in once and gain access to multiple applications, improving convenience and productivity.
- MFA strengthens security by requiring multiple verification factors before granting access, significantly reducing the risk of unauthorized entry.
When implemented together, SSO and MFA balance ease of use with robust authentication, ensuring secure yet seamless access across enterprise systems.
- SSO vs. Federated Identity SSO and Federated Identity Management (FIM) both simplify access, but they differ in scope.
- SSO works within a single organizational domain, allowing users to access multiple internal applications using one set of credentials.
- Federated Identity extends this capability across organizational boundaries, enabling users to securely access external resources through trust relationships and standards like SAML and OAuth.
While SSO focuses on internal efficiency, Federated Identity enables interoperability and secure collaboration between different organizations.
- Identity-as-a-Service (IDaaS)
Identity-as-a-Service (IDaaS) platforms deliver comprehensive IAM capabilities through a cloud-based model. These typically include SSO, adaptive MFA, user directories, and automated provisioning. By centralizing identity operations, IDaaS simplifies security management, improves user experience, and enhances operational efficiency for organizations of all sizes.
Ultimately, SSO is only one element of a complete IAM strategy. While it focuses on authentication, it must work alongside access controls, permission policies, and activity monitoring to ensure comprehensive identity protection. Without accurate identity verification, no system can effectively authorize or restrict user actions. To achieve end-to-end governance and compliance, it’s equally important to understand how Identity Governance and Administration (IGA) complements IAM.
Future of SSO and Cloud Security
Cloud-native and AI-driven authentication will redefine how organizations manage identity in 2025. As enterprises adopt hybrid and multi-cloud ecosystems, SSO will evolve into a more intelligent, adaptive, and context-aware security layer that balances frictionless access with uncompromising protection.
- Passwordless authentication
The shift toward passwordless authentication will be one of the most significant advancements in SSO. By replacing passwords with biometrics such as facial recognition, fingerprints, or retinal scans, organizations can eliminate one of the weakest links in security, credential theft. This approach enhances both security and convenience, enabling users to authenticate seamlessly across cloud and enterprise applications. - Decentralized Identities
With advancements in blockchain and other emerging technologies, organizations are moving away from relying on centrally stored credentials. This decentralized approach not only minimizes the risks associated with a single point of failure but also strengthens user privacy and control over personal data. - Token and Session Security
As cyberattacks increasingly target the authentication tokens used in SSO systems through methods such as malware injection or token interception, security practices are adapting accordingly. Modern strategies now emphasize frequent token rotation, shorter token lifespans, and continuous monitoring to quickly detect and respond to potential compromise attempts. - Adaptations for Cloud and Hybrid Environments
The growing complexity of cloud-first and hybrid infrastructures demands that SSO solutions become more adaptive and intelligent. Modern SSO platforms are expected to scale efficiently across multiple environments, automate key identity management functions such as user provisioning, and maintain consistent enforcement of access and security policies across all connected systems.
Final Thoughts
Single Sign-On (SSO) has become a cornerstone of modern identity management, offering secure, seamless access across multiple applications with a single login. By reducing password fatigue and centralizing authentication, SSO strengthens both user experience and enterprise security.
Evolving alongside Zero Trust, AI, and passwordless technologies, SSO is shaping a future of intelligent, context-aware access that delivers simplicity without compromising protection.
To see how Tech Prescient helps organizations implement advanced SSO frameworks that balance security, compliance, and convenience,
Frequently Asked Questions (FAQs)
1. What is meant by Single Sign-On (SSO)?
Single Sign-On (SSO) is an authentication method that allows users to log in once and securely access multiple applications without re-entering credentials. It uses centralized identity management to simplify access while maintaining strong security across systems.2. Is SSO secure?
Yes, when properly configured and paired with Multi-Factor Authentication (MFA), SSO can significantly enhance security. It reduces password-related risks like phishing and credential reuse while ensuring centralized control over user access.3. What are examples of SSO?
Popular examples of SSO include Google Workspace, where one login grants access to Gmail, Drive, and Docs, and Microsoft 365, which connects Outlook, Teams, and OneDrive. Many enterprises also use Okta or Azure AD to power secure, unified access.4. How does SSO authentication work?
SSO works through a trust relationship between an Identity Provider (IdP) and connected Service Providers (SPs). When a user logs in, the IdP verifies their credentials and issues a secure token that allows seamless access to all linked applications.5. What are the benefits of Single Sign-On?
SSO simplifies the login experience, boosts productivity, and enhances security by minimizing password fatigue. It also reduces IT helpdesk requests for password resets, helping organizations save time and operational costs.