
What is AI Security Posture Management (AI-SPM)?


AI security posture management (AI-SPM) helps organizations safeguard their AI systems by continuously monitoring and strengthening defenses. It spans the complete AI lifecycle, from development to deployment, identifying risks, fixing vulnerabilities, ensuring compliance, and protecting against evolving threats. This ensures AI operations remain secure, resilient, and aligned with industry regulations.
As AI becomes more integrated into cloud environments and business workflows, AI-SPM gives teams the visibility and control they need to prevent risks such as data poisoning, prompt injection, or any unauthorized AI activity.
A recent AI security report by Zscaler indicates that nearly 4 out of 5 organizations are engaging with AI, and 83% of companies claim AI as a top priority in their business trajectory. Despite this, many organizations are not adequately securing their AI systems. In this blog, we’ll break down why AI-SPM matters, its key capabilities, benefits, and best practices. Let’s dive in and explore how it can safeguard the future of AI adoption.
Key Takeaways:
- Find out how AI-SPM keeps your AI models, data, and pipelines safe from risks like data poisoning and prompt injection
- See why securing AI is a must as it becomes central to cloud and enterprise workflows in 2025
- Learn the main AI-SPM tools and features, from tracking assets to automated fixes and compliance checks
- Understand how AI-SPM is different from CSPM, DSPM, and SIEM, and why traditional tools aren’t enough
- Discover the benefits, practical use cases, and best practices to safely scale AI across industries
Why AI-SPM is Crucial in 2025
As enterprises rapidly adopt GenAI and integrate it into mission-critical operations, they also inherit a new class of security risks that traditional tools cannot fully address. Gartner highlights risks such as data exfiltration (the unauthorized transfer of sensitive data outside the organization), adversarial attacks (the use of malicious inputs designed to deceive or manipulate AI models), misinformation, and identity fraud that can disrupt operations, damage reputations, and trigger compliance violations. Real-world incidents like Microsoft’s accidental exposure of 38TB of sensitive data and the discovery of malicious AI models on Hugging Face show how quickly these risks can escalate.
This is where AI Security Posture Management (AI-SPM) becomes indispensable. It provides enterprises with the visibility, safeguards, and resilience needed to secure their AI ecosystem. Specifically, AI-SPM helps:
1. Secure AI models against adversarial attacks
As enterprises increasingly rely on GenAI, cybercriminals are leveraging these technologies to automate and amplify their attacks. Key AI-powered threats include:
- Smart malware: Malicious software that uses AI to evade detection and adapt to defenses.
- Inference attacks: Techniques that extract sensitive information from AI models.
- Jailbreaking: Manipulating AI systems to bypass safety restrictions or policies.
- Prompt injection: Altering AI prompts to produce harmful or unintended outputs.
- Model poisoning: Subtly corrupting training data to influence model behavior and degrade reliability.
If left unaddressed, these attacks can distort AI outputs and compromise decision-making. AI-SPM continuously monitors and fortifies AI models to defend against these evolving threats.
2. Protect sensitive training/operational data
To perform effectively, AI applications depend on large volumes of domain-specific datasets, making them attractive targets for cybercriminals. Threat actors can exploit GenAI tools, databases, and APIs to exfiltrate proprietary data, while internal negligence and hidden misconfigurations can expose information without an enterprise’s knowledge. AI-SPM secures data pipelines and access points, reducing the risk of privacy violations, compliance failures, and reputational harm.
3. Prevent misconfigurations in cloud-hosted AI
Modern AI systems rely heavily on cloud infrastructure, SDKs, and APIs. However, misconfigurations and hidden vulnerabilities in these environments can provide easy entry points for attackers. AI-SPM ensures organizations gain visibility into these blind spots, enabling proactive detection and remediation of risks before they result in unauthorized access or exposure.
4. Maintain compliance and trustworthiness
The reliability of GenAI depends on the quality of its training data. Risks like AI hallucinations and data poisoning, where attackers deliberately corrupt training sets, can spread misinformation and produce harmful outputs. At the same time, regulatory scrutiny around data privacy and security continues to grow. AI-SPM ensures enterprises safeguard accuracy and data integrity while also maintaining compliance and protecting stakeholder trust.
In short, securing AI is not optional. AI-SPM is the safeguard that ensures enterprises can innovate with AI without jeopardizing security, compliance, or trust.
Key Capabilities of AI-SPM
AI-SPM equips organizations with the tools and functions needed to secure AI operations across the entire lifecycle. From visibility into hidden AI assets to proactive risk response, it ensures that machine learning models, large language models (LLMs), and AI-driven pipelines operate in a safe, compliant, and resilient manner.
1. AI Asset Discovery & Inventory
AI systems often operate without full visibility, leading to risks like shadow AI models, compliance violations, and data leaks. AI-SPM enables organizations to track and catalog all AI models, pipelines, datasets, and associated resources across cloud environments. By maintaining a complete inventory, security teams gain oversight of training data, fine-tune processes, and ground models, ensuring that every AI component is monitored and governed.
2. Continuous Risk Assessment
AI-SPM continuously scans the AI supply chain, including data sources, libraries, APIs, and pipelines powering each model to identify vulnerabilities, misconfigurations, and weak encryption or access controls. It also monitors runtime interactions with LLMs, detecting misuse, prompt overloading, abnormal activity, or unauthorized access attempts. This proactive approach strengthens resilience against emerging AI-enabled threats.
3. Automated Remediation
When AI-SPM detects high-priority misconfigurations, policy violations, or security incidents, it triggers automated workflows to resolve them quickly. By embedding security settings and policies into AI infrastructure at deployment, AI-SPM enforces best practices, corrects faulty permissions, and mitigates risks before they escalate.
4. Compliance Management
With increasing regulations such as GDPR, HIPAA, and NIST’s AI Risk Management Framework, AI-SPM plays a key role in aligning AI operations with compliance standards. It enforces governance policies, maintains audit trails with model lineage, approvals, and risk acceptance criteria, and ensures that sensitive data like personally identifiable information (PII) is handled securely and transparently.
5. Attack Path Analysis
Attackers often exploit hidden vulnerabilities in complex AI ecosystems. AI-SPM performs attack path modeling to map potential routes an adversary could take across AI models, pipelines, and cloud infrastructure. By identifying weak points and simulating exploitation paths, organizations can harden defenses, prioritize fixes, and strengthen overall security posture.
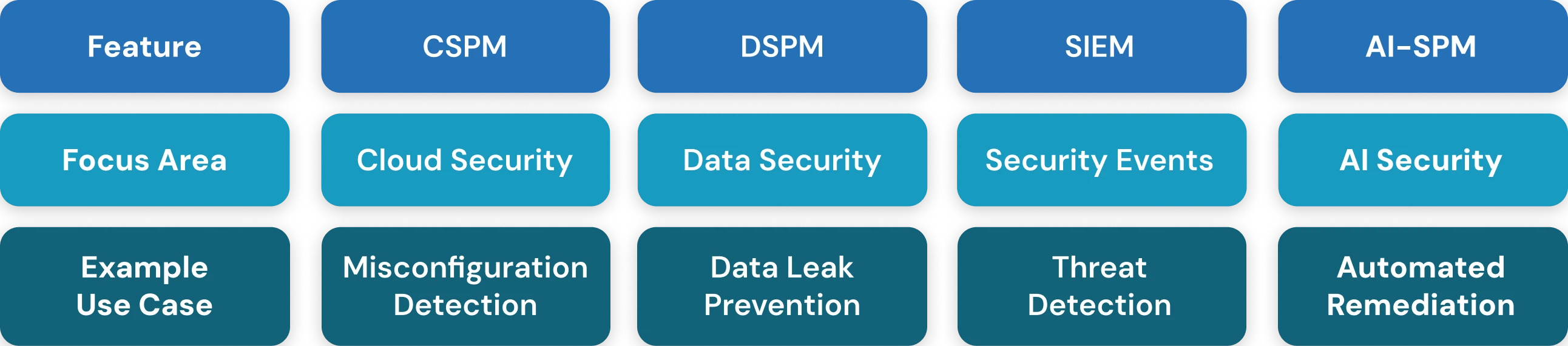
AI-SPM vs CSPM, DSPM & SIEM
To highlight the unique value of AI Security Posture Management (AI-SPM), it is useful to compare it with other well-established posture management and monitoring tools. Cloud Security Posture Management (CSPM), Data Security Posture Management (DSPM), and Security Information and Event Management (SIEM) each secure different layers of the digital ecosystem. This comparison helps explain why traditional tools alone are insufficient to address the specific risks of AI and machine learning systems, and how AI-SPM fills this critical gap.
Key Comparisons:
-
CSPM (Cloud Security Posture Management): It is a tool that provides visibility, context, and remediation capabilities for cloud environments. It helps organizations identify and address misconfigurations in real time, ensuring that cloud infrastructure in platforms like AWS, Azure, and GCP complies with security standards and prevents risks such as misconfigured S3 buckets or overly permissive IAM policies.
-
DSPM (Data Security Posture Management): It protects enterprise data, including PII, PHI, PCI, and sensitive secrets, across public and private storage buckets, serverless functions, hosted database servers, cloud-managed SQL databases, and other mission-critical platforms.
-
SIEM (Security Information & Event Management): Aggregates and monitors event logs from across the environment to detect anomalies, intrusions, and compliance breaches in near real time.
-
AI-SPM (AI Security Posture Management): It delivers specialized security capabilities designed to address the unique threats and risks associated with AI. It fills a critical gap present in many other security tools by providing comprehensive protection for AI models and assets. For example, AI-SPM expands DSPM visibility to cover AI training data and safeguards cloud-based generative AI (GenAI) models.
| Sr. No | Framework | Focus Area | Example Use Case | What’s Missing Without AI-SPM |
|---|---|---|---|---|
| 1 | CSPM | CSPM focuses on identifying and fixing cloud infrastructure misconfigurations. | For example, it can detect and remediate exposed S3 buckets. | It does not secure AI models that may be hosted within the same cloud infrastructure. |
| 2 | DSPM | DSPM specializes in discovering and protecting sensitive data across environments. | For example, it can perform GDPR scans to identify and safeguard PII. | It does not detect poisoned or tampered datasets used in AI training. |
| 3 | SIEM | SIEM aggregates and monitors event logs to detect anomalies and potential intrusions. | For example, it can flag suspicious login attempts as part of intrusion detection. | It does not capture or mitigate adversarial attacks targeted at AI models. |
| 4 | AI-SPM | AI-SPM is designed to secure AI models and pipelines against unique risks. | For example, it can defend training pipelines from data poisoning attacks. | It completes the security stack by addressing AI/ML threats that other frameworks cannot. |
Benefits of Implementing AI-SPM
Implementing AI-SPM goes beyond securing your AI infrastructure. It simplifies compliance, reduces risk, and strengthens trust. By embedding security at every stage of the AI lifecycle, organizations unlock both protection and performance gains.
1. Reduced Attack Surface
AI-SPM continuously monitors AI systems, detecting anomalies, misconfigurations, and unauthorized access in real time. By eliminating risky permissions and tightening visibility, it minimizes potential entry points for attackers and significantly reduces the likelihood of costly breaches.
2. Faster Anomaly Detection & Response
With real-time monitoring and automated risk identification, AI-SPM accelerates the discovery of threats before they escalate. This enables security teams to remediate issues proactively, streamline incident response, and focus resources on high-priority tasks instead of manual reviews.
3. Cost Savings vs. Manual Audits
AI-SPM automates compliance checks and security assessments that would otherwise require resource-heavy audits. By reducing operational overhead and manual intervention, organizations lower security management costs while maintaining stronger protection standards.
4. Stronger Compliance Reporting
Meeting regulatory requirements, such as GDPR, becomes easier with AI-SPM. It provides clear evidence of due diligence in managing AI-related risks, helping organizations demonstrate compliance, avoid fines, and maintain stakeholder confidence.
5. Builds Customer Trust in AI Adoption
A proactive AI-SPM strategy strengthens your competitive position by showing a commitment to secure AI practices. By safeguarding sensitive data and embedding security across the AI lifecycle, organizations foster trust with customers and partners and pave the way for faster AI adoption and innovation.
Use Cases & Industry Applications
AI-SPM is not just a security tool. It delivers industry-tailored protection across critical domains. Below are key scenarios where AI-SPM adds tangible value.
1. Cloud Environments: Secure Multi-Cloud AI Deployments
In complex cloud architectures, organizations often run AI workloads across AWS, Azure, GCP, or hybrid settings. AI-SPM discovers and inventories all AI models, services, SDKs, and pipelines in a unified view, preventing “shadow AI” deployments that bypass security oversight. It detects misconfigurations or risky permissions in AI infrastructure and cuts off attack paths before they materialize.
2. Healthcare: Protect AI-Driven Diagnostics from Data Leakage
Healthcare systems deploying AI for diagnostics or patient outcome predictions process highly sensitive data, including PHI. AI-SPM monitors training and inference pipelines to flag exposure of sensitive inputs, detects anomalous behavior or data leaks, and helps maintain compliance with regulations such as HIPAA.
3. Finance: Guard Against AI Fraud Models and Compliance Gaps
Banks, fintechs, and trading firms use AI-driven systems for fraud detection, risk modeling, or credit scoring. AI-SPM ensures these models are not manipulated through adversarial attacks such as data poisoning, safeguards customer data fed into or inferred from models, and provides audit trails to satisfy regulatory scrutiny.
4. SaaS: Secure GenAI Integrations and APIs
SaaS platforms often embed generative AI or LLM APIs for enhanced user features such as content generation or chatbots. AI-SPM tracks usage of these models and APIs, prevents prompt injection or model misuse, enforces least privilege around API keys or roles, and ensures that AI-enhanced services maintain integrity and trust.
Best Practices for AI-SPM Adoption
To realize the value of AI-SPM, organizations should follow a structured rollout path grounded in security hygiene, integration, automation, and education.
1. Start with AI asset inventory
Begin by discovering and cataloging your AI assets, including models, pipelines, datasets, APIs, and dependencies. Maintain this as a living inventory so you can track changes, spot shadow AI deployments, and establish a reliable baseline for security operations.
2. Integrate AI-SPM with existing CSPM / DSPM
AI risks do not exist in isolation. Embed AI-SPM into your cloud security posture (CSPM) and data security posture (DSPM) frameworks so you can correlate signals across infrastructure, data, and AI layers. This unified view helps reduce blind spots and enables more contextual risk decisions.
3. Automate remediation workflows
Define rules and policies so that low-risk findings, such as misconfigurations or overly permissive access, are remediated automatically or semi-automatically. This reduces response latency, lightens the load on security teams, and strengthens consistency.
4. Conduct regular compliance reviews
Continuously monitor mappings from AI practices to regulatory frameworks such as GDPR, AI Act, HIPAA, and NIST AI RMF. Use AI-SPM audit trails and reporting to validate controls, detect deviations early, and prove due diligence.
5. Train teams on AI-specific threats
Security, data science, and operations teams need awareness of AI risks such as prompt injection, data poisoning, model drift, or inference attacks. Provide joint training, simulation exercises, and threat modeling to foster cross-functional readiness.
Future of AI Security Posture Management
The landscape of AI security is evolving rapidly. The future of AI-SPM will be shaped by tighter integration with trust frameworks, runtime protections, evolving regulations, and securing end to end generative pipelines.
1. AI + Zero Trust integration
Expect AI-SPM systems to become core enforcers in Zero Trust architectures. AI models will increasingly help validate user, device, and access context, and AI-SPM will feed dynamic, risk-based signals into trust decisions.
2. AI native runtime firewalls
Beyond posture measurement, future tools will incorporate runtime defenses that inspect model inputs, outputs, and interactions in real time to block malicious or anomalous behavior before it can harm downstream systems.
3. Regulatory evolution (AI Act, NIST AI RMF, governance frameworks)
Legislation and standards are catching up quickly. AI-SPM must evolve to support new regulatory mandates such as mandatory logging, transparency, and impact assessments. It will likely embed mappings to evolving frameworks and automate compliance checks.
4. LLMOps security in GenAI pipelines
As enterprises build generative AI workflows that include data ingestion, prompt management, fine-tuning, inference, and feedback loops, security must follow. AI-SPM will incorporate threat modeling specific to LLM operations, such as tool exploitation, prompt chaining, and context poisoning, and guard the full pipeline.
5. Supporting identity governance for non-human identities
An often-overlooked dimension of AI security is managing non-human identities (NHIs) such as service accounts, bot accounts, and automated workflows. Integrating AI-SPM with an Identity Governance & Administration (IGA) solution enables organizations to inventory, monitor, and control these identities with the same rigor as human users. Partners like Tech Prescient can help enterprises seamlessly embed this governance layer into their AI and GenAI pipelines, ensuring accountability, least-privilege access, and compliance.
Final Thoughts
AI Security Posture Management (AI-SPM) is no longer optional; it’s the foundation for securing modern AI ecosystems. By continuously monitoring risks, automating remediation, and aligning with compliance frameworks, AI-SPM empowers organizations to innovate with confidence while defending against emerging threats like data poisoning and prompt injection.
In 2025 and beyond, AI-SPM will be central to maintaining trust, protecting sensitive data, and enabling safe AI adoption across industries. At Tech Prescient, we help enterprises implement AI-SPM strategies with expert guidance, advanced automation, and industry-aligned best practices.
Frequently Asked Questions (FAQs)
1. What does AI-SPM stand for?
AI-SPM stands for AI Security Posture Management. Think of it as a structured framework designed to secure AI systems end-to-end. It covers everything from protecting the AI models and datasets to monitoring pipelines and ensuring they are compliant with security best practices.2. How is AI-SPM different from CSPM?
While CSPM (Cloud Security Posture Management) is mainly about securing cloud infrastructure, like fixing exposed S3 buckets, AI-SPM takes a more specialized role. It focuses on the unique risks tied to AI, such as adversarial model attacks, prompt injection, and securing data pipelines. Together, CSPM and AI-SPM complement each other but solve very different problems.3. What risks does AI-SPM address?
AI-SPM tackles the threats that traditional tools often miss. These include data poisoning, where malicious inputs corrupt AI training, prompt injection, which manipulates AI outputs, and misconfigurations in cloud-hosted AI systems. It also brings shadow AI deployments into visibility so organizations do not get blindsided by unmonitored models.4. Which industries need AI-SPM?
Any AI-driven organization can benefit, but it is especially critical in sectors like healthcare, finance, and SaaS. For example, AI-SPM helps prevent diagnostic data leaks in healthcare, safeguards fraud detection models in finance, and secures GenAI integrations in SaaS platforms. Essentially, if your business runs on AI, AI-SPM is your safety net.5. Is AI-SPM part of compliance management?
Yes, AI-SPM goes beyond security to ensure regulatory alignment. It maps directly to standards like GDPR, HIPAA, and ISO, helping enterprises prove compliance while reducing audit fatigue. By automating checks and documentation, it not only protects AI assets but also keeps organizations audit-ready at all times.



