
DAC vs MAC: Understanding the Core Access Control Models in Cybersecurity

DAC and MAC are two main access control models in cybersecurity. Each model handles permissions, security, and compliance in a unique way. Discretionary Access Control (DAC) is a versatile and excellent tool for cooperation since it gives resource owners the ability to choose who may access their data. For high-security settings, Mandatory Access Control (MAC) is perfect because it employs centralized, system-enforced rules and security labels. In cybersecurity, understanding DAC and how it varies from MAC enables businesses to efficiently balance control, security, and access.
According to the latest data breach statistics by Secureframe, 46% of all data breaches contained consumer personally identifiable information (PII) in 2025, which demonstrates the need for precise, restricted access models for securing sensitive data in businesses. The modern digital world contains a great deal of sensitive data. Protecting this data from breaches and illegal access has become a top concern in cybersecurity. This can be supported by the use of an approach called access control, which makes sure that only those with the appropriate permission rights can access sensitive data. In this blog, you will know the major distinctions between DAC and MAC, how they operate in real-world circumstances, and how to select or combine them to better access governance, satisfy compliance needs, and boost your overall security posture.
Key Takeaways:
- DAC vs MAC take different paths: flexibility for DAC, strict control for MAC
- DAC boosts collaboration by letting owners set and change permissions
- MAC locks down sensitive data with centralized, non-overridable rules
- The right choice depends on your risk, compliance, and scalability needs
- Both models strengthen identity governance and Zero Trust security
What Is Discretionary Access Control (DAC)?
Discretionary access control (DAC) is an identity-based access control mechanism that grants users some control over their data. It’s commonly found in smartphone apps, Google Docs, and operating systems worldwide. In a DAC system, data owners, such as resource owners or any other users allowed to govern data, can specify access rights for specific users or groups of users. In other words, the resource owner determines who has access and what rights are granted.
Unlike centralized models, DAC allows subjects to share information with other users, grant privileges, change object attributes, choose which attributes are associated with newly created objects, and set different forms of access control without needing central authorization. These permissions are typically stored in an access-control list (ACL), which specifies which users and groups have access to data, as well as their access levels. An ACL can be created automatically or by an administrator when access is granted. A system administrator can also implement an ACL as part of a security policy, one that normal users cannot modify or override.
How Does Discretionary Access Control Work?
Permissions in DAC are typically assigned by resource owners or administrators. For example, in personal computer operating systems, file access can be restricted by granting specific rights to selected users. Common permission types include Read (R), which lets users view a resource without altering it; Write (W), which allows modifying or creating content; and Execute (X), which enables running files, scripts, or applications.
While these permissions are essential for functionality and collaboration, they must be carefully managed to prevent accidental changes, malicious actions, or security breaches. DAC decides who can use a resource based on the identity of the user and their ownership of that resource. The process typically involves:
- Identify the subject
The process starts by figuring out who is trying to access the resource—whether it is an individual user or a user group. They need to log in or otherwise verify their identity. - Check the object
The system then examines the resource, such as a file, application, or data, to see what permissions have been set. - Match permissions
If the user’s identity or group matches an entry on the allowed list, they get the corresponding access level. If not, the system denies access. - Owner control
At any time, the resource owner can modify permissions, granting or removing rights for specific users or groups.
DAC can be implemented in two main ways:
- Access Control Lists (ACLs)
This is basically a record that lists which users or groups can access a resource and exactly what actions they are allowed to perform. - Capability Systems
In this approach, access is given based on something the user has—like a private key, a security token, or a unique access link.
A familiar example of what is DAC in cyber security can be found in Google Drive file sharing, where the document owner decides who can view, comment on, or edit a file. This owner-driven flexibility makes DAC ideal for collaboration-heavy workflows but also underscores the need for diligent permission management to prevent data exposure or unauthorized actions.
What Is Mandatory Access Control (MAC)?
Mandatory access control (MAC) is a type of access control in which the operating system grants users access depending on data confidentiality and user clearance levels. This model grants access based on need-to-know: users must demonstrate their need for knowledge before getting access. MAC is also known as a non-discretionary access control paradigm, which indicates that control is not provided at the option of the user or file owner. The MAC model's control mechanisms enable businesses to apply zero-trust principles. MAC is regarded as one of the most secure access control methods. System administrators manually establish access rules under this paradigm, which are rigidly enforced by the operating system or security kernel. Regular users cannot change security characteristics for data they have produced.
How Does Mandatory Access Control Work?
At its core, the basic principles of Mandatory Access Control (MAC) focus on ensuring the utmost privacy and confidentiality of an organization’s resources. No one has default privileges to view or edit another person’s data; every access request must be authorized. Access provisioning is centrally administered, meaning control rests with the system, not the individual users. Both individuals and resources are assigned security labels that define their classification and category, forming the foundation for all access decisions.
- Label-Based Access Control in MAC
MAC manages and controls access to resources using label-based access control for data and clearance levels. It assigns a security label to each resource in the system, and these labels or classifications are important indicators of the resource's criticality and sensitivity. Resources are marked with security designations, such as confidential, secret, or public. Individuals inside the organization are also allocated clearance levels, and the clearance level issued to each individual determines which resources they have secure access to. - How Access Is Granted in MAC?
Whenever a user requests access to a resource, the system checks the user's security label and clearance level to ensure that they have the necessary clearance before granting access. Assume a government agency has material that is categorized as extremely private with a national security classification. This material is only accessible to people who have both a highly secret security clearance (classification) and authority to access national security documents (category). Such users have access to information that needs a lesser level of clearance, but workers with lower clearance levels or no rights to national security papers do not. - Real-World Example in Banking
In banking, the same idea applies: client financial records categorized as sensitive and tagged with a fraud investigation category would only be available to individuals with the necessary clearance level and investigation authority. All other employees, even those who work in the bank, would be denied access to these documents.
DAC vs MAC: Key Differences Explained
The ways MAC and DAC manage security, flexibility, and user control are different. Understanding these distinctions allows you to select the best model for your company's needs.
| Characteristics | MAC | DAC |
|---|---|---|
| Data Confidentiality | MAC's rigorous regulations ensure that sensitive data is properly safeguarded, with no way for users to provide access. | DAC relies on resource owners to maintain data confidentiality, which can lead to leaks if not maintained appropriately. |
| Security Use Cases | MAC is ideal for high-security environments, such as government institutions, the military, and critical infrastructure, where strict control over data access is essential. | DAC works well in environments that require flexibility and easy access, such as corporate settings and small enterprises. |
| Flexibility and Convenience | It is more complex to establish than other models, but once implemented, it delivers unparalleled security through its strict, centrally enforced rules. | It is flexible and simple to set up, but it lacks the stringent restrictions and centralized control found in MAC. |
| Front-End versus Back-End Control | MAC places all access control decisions in the hands of system administrators, ensuring consistent enforcement while leaving end users with no ability to alter permissions. | DAC gives end users responsibility for managing access to their own resources, providing additional front-end control over who can view or modify data. |
| Access Control Decisions | MAC makes decisions based on policies, classifications, and clearances, without user interaction. | DAC allows owners or resource managers to make decisions; however, this comes at the expense of security. |
| Practical Examples | A practical example of MAC is a military communication system, where messages are classified as Confidential, Secret, or Top Secret, and only personnel with the corresponding security clearance can access or send them, ensuring strict control over sensitive information. | DAC appears in everyday tools. Facebook group admins setting view or post rights, smartphone owners granting apps access to contacts or GPS, file owners in Windows or UNIX setting read/write permissions, and Google Docs or Dropbox owners deciding who can edit, view, or share. |
Real-World Examples of MAC and DAC
Real-world use cases can help you understand how MAC and DAC work in diverse contexts. Each type serves a distinct purpose depending on security requirements and user flexibility.
- MAC in Military or Government Agencies
MAC is commonly utilized in military and government environments where data security is paramount. For example, tight security labeling and clearances are used to limit access to sensitive information. Only those with the necessary authorization may see or manage this data, reducing the danger of unwanted access. - DAC in a Corporate Setting
DAC is often used in business situations where flexibility is essential. Employees are responsible for managing their own files and deciding who has access to or can alter them. For example, a project manager may provide team members access to a shared folder, allowing for seamless communication without the need for system administrators.
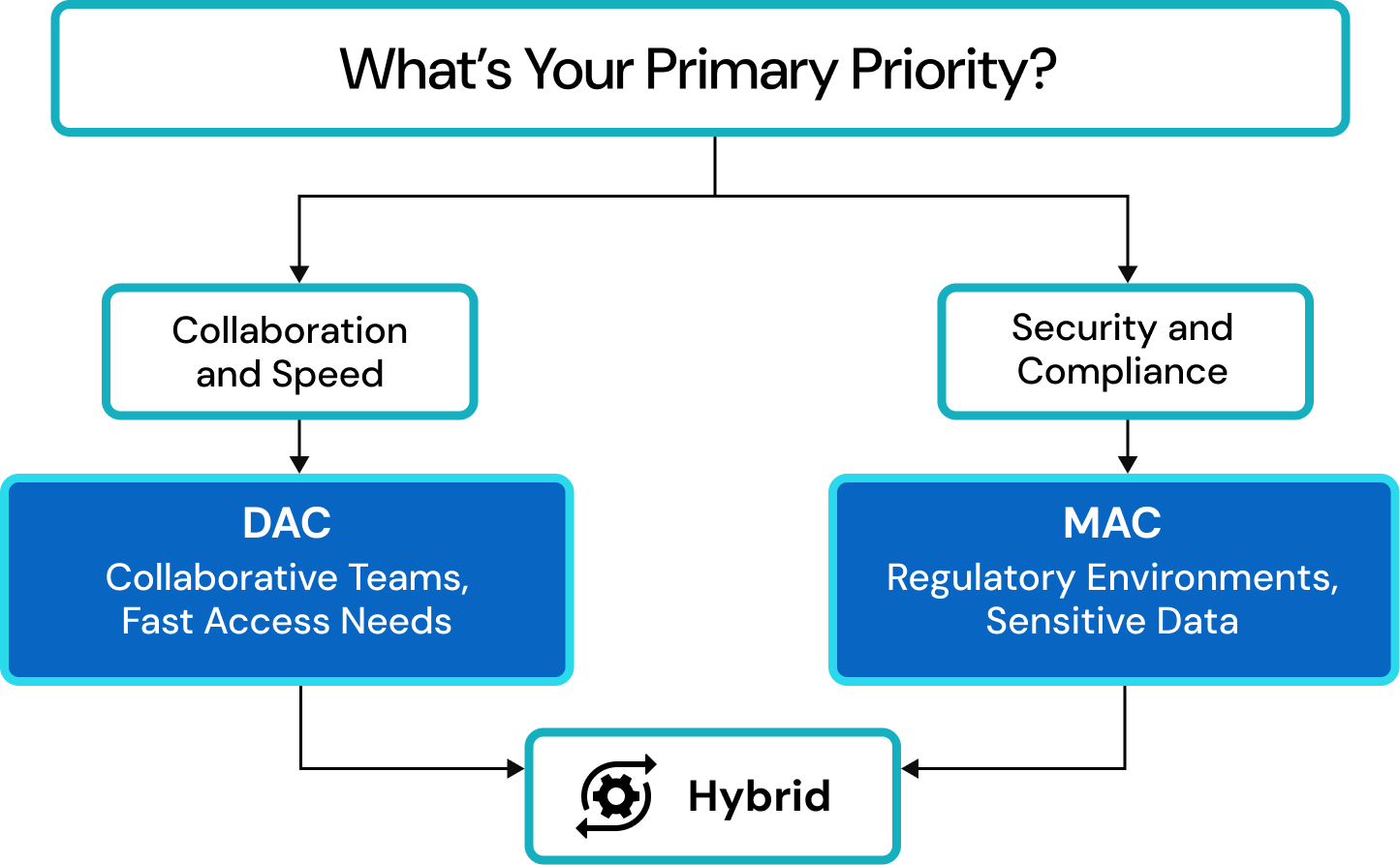
Choosing the Right Model for Your Organization
The security needs and operational goals of your business dictate whether to use MAC or DAC. Understanding when to use each model enables you to strike the right balance of security and flexibility.
When to use MAC
- Primary Use and Applications
Government entities, armies, and law enforcement agencies primarily employ this access control paradigm. The United States government employs MAC to protect secret material as well as to facilitate tiered security policies and applications. Organizations use MAC to manage access to client account data to improve data protection and compliance in the insurance and banking industries. This non-discretionary access control approach may also safeguard database access, where the objects include procedures, tables, views, and other aspects. - Suitability and Limitations
MAC is appropriate for enterprises that prioritize data security above operational flexibility and expense. Because of its complexity and inflexibility, MAC is hardly used in private organizations. A MAC-only architecture offers a high and granular level of protection. However, it is tough to install and maintain. - Hybrid Implementation with Role-Based Access Control (RBAC)
This is why MAC is frequently used in conjunction with other access control types. For example, using it with a role-based paradigm speeds up user profile configuration. Instead of assigning access privileges to each user, an administrator can construct user roles. Each organization has users with comparable responsibilities and access privileges, such as workers in the same position, third-party providers, and so on. Rather than creating individual user accounts from the start, an administrator may establish responsibilities for these groups. - Hybrid Implementation with Discretionary Access Control (DAC)
Another frequent combination is MAC with discretionary access control, or DAC. MAC can protect sensitive data, but DAC enables coworkers to exchange information in a corporate file system.
When to use DAC
- Unsuitability for Highly Sensitive Environments
Organizations that operate with very sensitive data (medical, financial, military, etc.) should avoid using DAC for various reasons:
- If user 1 shares access privileges with user 2, there is no guarantee that user 2 needs this access for work, will not steal or alter data, or will not offer access to a hostile user.
- It is impossible to regulate how information flows within a network.
- The concepts of the principle of least privilege, need to know, and separation of duties are all impossible to execute.
- Suitability for Small Businesses At the same time, DAC is an excellent option for small firms with limited IT personnel and cybersecurity expenditures. It facilitates information sharing and ensures that the business runs smoothly.
- Scalability Considerations When used in firms with 20 to 30 workers, DAC has less complexity and governance difficulties than when used in organizations with hundreds or thousands of employees.
Can You Combine DAC with MAC?
The combination of Mandatory Access Control (MAC) and Discretionary Access Control (DAC) results in a more balanced access management strategy. MAC implements administrator-managed security standards that protect sensitive data through tight classifications and clearances. DAC increases flexibility by allowing resource owners to control access to less sensitive data depending on current needs.
A government agency, for example, may utilize MAC to safeguard confidential documents, whereas DAC controls generic files to facilitate collaborative work. This hybrid solution is ideal for enterprises that want stringent control over secret data as well as flexibility in everyday operations. Though it necessitates careful preparation, it improves vital asset protection while providing users with the freedom to remain productive.
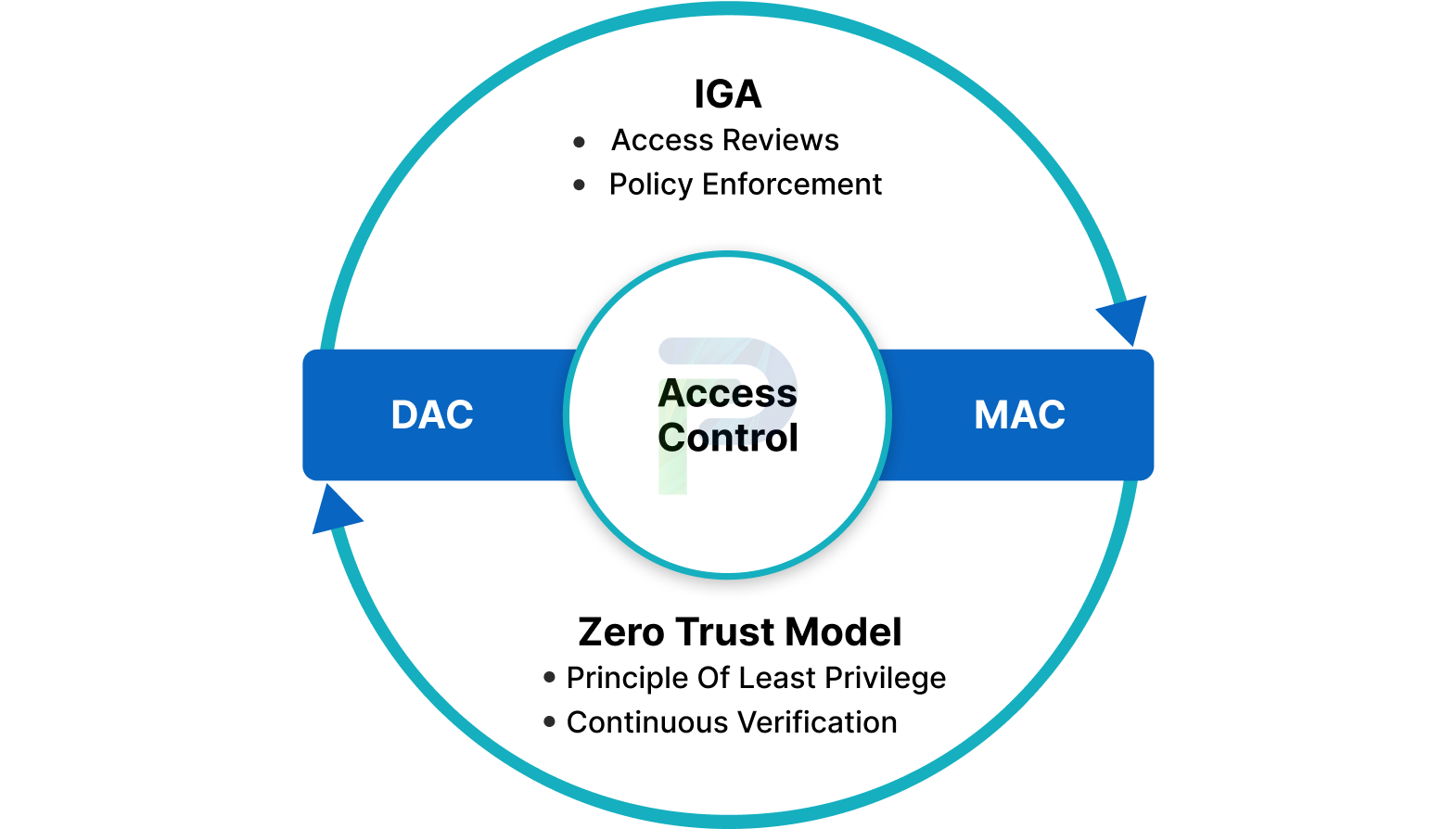
DAC and MAC in the Context of IGA and Zero Trust
Discretionary Access Control (DAC) and Mandatory Access Control (MAC) are core access control models that play a pivotal role in Identity Governance and Administration (IGA) and support the Zero Trust security framework. Together, they help organizations define, enforce, and continuously verify user access in a way that aligns with compliance and security objectives.
- DAC/MAC as Foundational Access Control Mechanisms
In the IGA context, DAC and MAC act as the baseline for how access is provisioned and managed. DAC empowers resource owners to grant permissions, offering flexibility for collaboration and operational agility. In contrast, MAC enforces centrally managed, policy-driven controls that users cannot override, ensuring strict adherence to security classifications. By combining these approaches, organizations can establish strong governance over who can access what and under which conditions. - Role in Enforcing Least Privilege and Access Review
The principle of least privilege, a cornerstone of Zero Trust, ensures that users only have access to the resources necessary for their role, and nothing more. DAC and MAC both contribute to enforcing this principle by restricting excess permissions and ensuring that high-sensitivity resources remain tightly controlled. When integrated into IGA workflows, they enable periodic access reviews and certification campaigns, helping detect privilege creep and ensuring that outdated or unnecessary access is revoked promptly. - Link to Role-Based Access Control (RBAC) and Policy Enforcement
DAC and MAC complement RBAC by determining how roles and permissions are assigned and enforced. RBAC provides a scalable way to group access rights based on job functions, while DAC and MAC define the boundaries for how these rights are granted and maintained. This integration simplifies compliance with frameworks such as SOX, HIPAA, and GDPR, while ensuring consistent policy enforcement across all systems and applications.
Final Thoughts
Choosing the right access control model isn’t just a technical decision; it’s a strategic one. Whether your organization values the flexibility of DAC, the strict governance of MAC, or a hybrid that blends both, aligning your approach with IGA and Zero Trust principles is essential for safeguarding data, meeting compliance, and enabling secure collaboration at scale.
At Tech Prescient, we help organizations design, implement, and optimize access control strategies that fit their unique risk profile, compliance requirements, and operational needs.
Secure the right access for the right people, every time. To see how Tech Prescient can help you put DAC, MAC, and Zero Trust into action:
Frequently Asked Questions (FAQs)
1. What is the discretionary access control (DAC) model?
DAC is an access model where the resource owner controls who can access it and what actions they can perform, like read or write.2. What is an example of DAC in cybersecurity?
An example is a user setting file permissions on a Unix system or sharing a Google Doc with edit access.3. What is the difference between DAC and MAC?
DAC is owner-controlled and flexible, while MAC is system-enforced and more secure but rigid.4. When should I use MAC instead of DAC?
Use MAC in highly regulated industries like defense, banking, or healthcare where security policies must be strictly enforced.5.Can DAC and MAC be used together?
Yes, some systems use hybrid models to combine user flexibility with system-enforced rules



