
What Is an Insider Threat in Cyber Security? Types & Prevention


When you design security systems, you build them to keep unauthorized people out. Firewalls block external connections. Intrusion detection systems watch for suspicious network traffic. Antivirus software catches malware at the perimeter. But what happens when the threat comes from someone who's already inside, someone with a valid username, legitimate password, and approved access to your systems?
This is the insider threat problem. It's not about bad people getting in. It's about trusted people, or compromised accounts belonging to trusted people, misusing access they're supposed to have.
According to the 2025 Ponemon Cost of Insider Risks Global Report, insider incidents cost organizations an average of $17.4 million annually. More concerning: these incidents take an average of 81 days to detect and contain, giving malicious actors nearly three months to exfiltrate data, sabotage systems, or enable external attackers, all while appearing to be normal users doing normal work.
Why traditional security fails against insider threats: Your firewall can't block someone who's already inside the network perimeter. Your antivirus can't catch malicious behavior performed through legitimate applications. Your intrusion detection system sees valid credentials accessing approved systems. All your defensive layers designed to keep bad actors out become irrelevant when the threat actor has a valid employee badge, correct passwords, and approved system access.
This is where identity governance becomes critical. If you can't prevent insiders from having access (they need it to do their jobs), you must focus on giving them only the minimum access they need (least privilege), continuously verifying that the access remains appropriate (access certification), and detecting when their behaviour deviates from normal patterns (behavioural analytics).
Key Takeaways
- What insider threats are and why they're different from external attacks
- Three main types: malicious, negligent, and compromised insiders
- Real-world breach examples (Edward Snowden, Capital One, healthcare cases)
- How to detect insider threats using UEBA and behavioral analytics
- IGA-based prevention strategies: least privilege, access certification, automated offboarding
What Is an Insider Threat in Cyber Security?
An insider threat is any security risk that originates from within an organization's trust boundary, meaning it comes from someone who has legitimate, authorized access to systems, networks, data, or facilities. Unlike external attackers who must breach your perimeter defenses, insiders already possess the keys to your kingdom.

The insider category is broader than most organizations realize. It includes:
- Current employees across all departments and seniority levels who have approved access to organizational resources
- Contractors and consultants working on temporary assignments who often receive the same access privileges as full-time staff
- Business partners with access to shared systems or data through integrations and collaborations
- Vendors and service providers who manage your infrastructure or applications and hold administrative privileges
- Former employees whose access hasn't been properly revoked is a common security gap in many organizations
- Merged or acquired company employees who retained legacy system access that was never properly reviewed or integrated.
The threat part is equally nuanced. Not every insider threat involves malicious intent. According to SentinelOne's research, insider threats fall into three main categories:
- Careless or unintentional threats occur when an employee or contractor unintentionally causes a security breach through lack of awareness, training, or simply making a mistake. These incidents range from sending attachments to the wrong recipients and misconfiguring database or network settings, to misplacing company equipment or falling victim to scams and phishing attacks.
- Malicious insider threats occur when an employee or contractor intentionally causes harm to the organization. This includes stealing or leaking sensitive data, selling company secrets to competitors, sabotaging systems and IT infrastructure, or destroying critical business resources for financial gain, revenge, or ideological purposes.
- Compromised insider threats occur when an attacker gains unauthorized access to an employee's or contractor's account through phishing attacks, social engineering, or other attack vectors, then uses those legitimate credentials to carry out malicious activities while appearing as a trusted user.
What Makes Insider Threats Different from External Attacks
When an external hacker wants to access your systems, they face multiple barriers. They need to find an entry point through your perimeter defenses, obtain valid credentials through phishing or password cracking, navigate your network without triggering intrusion detection, locate valuable data among your systems, and exfiltrate that data without being caught.
An insider starts at the final step. They already have valid credentials. They already know where data lives. They understand your security controls and how to work within them. They appear in your logs as legitimate users performing approved activities.
The trust paradox: You must trust your employees, contractors, and partners to do their jobs. You can't operate a business where everyone is treated as a potential threat. But this necessary trust creates vulnerability. The credentials and access you provide to enable productivity are the same credentials and access that can be misused to cause harm.
This is why identity governance isn't about eliminating trust, it's about verifying it continuously. You trust your employees, but you verify that they have only the access they currently need (not everything they've ever been granted), their access aligns with their current role (which may have changed since access was granted), their behavior matches normal patterns for their job function (detecting anomalies), and their access is regularly reviewed and revalidated (not just granted once and forgotten).
Insider Threat Definition and Examples
Insider threat is a security risk originating from someone within an organization who has authorized access to systems, data, or facilities and uses that access in ways that harm the organization, whether intentionally or accidentally.
Common Insider Threat Examples
- Data exfiltration: Employees copying sensitive files to USB drives, uploading documents to personal cloud storage accounts, or emailing confidential information to personal email addresses.
- Intellectual property theft: Developers copying source code repositories before leaving for a competitor, sales representatives downloading customer databases to take to a new employer, or researchers exfiltrating years of experimental data.
- Sabotage: Deliberately disrupting systems to cause damage, deleting critical databases or backup files, modifying code to introduce bugs or backdoors, or disabling security controls or monitoring systems.
- Unauthorized access: Viewing employee emails or HR records out of curiosity, privileged administrators accessing confidential customer information unrelated to their tasks, or help desk staff viewing executive compensation data.
- Fraud and financial crime: Creating fake vendors and approving fraudulent invoices, manipulating payroll systems to issue unauthorized payments, or diverting customer payments to personal accounts.
Distinguishing Internal vs External Threat Sources
External threats come from attackers outside the organization who lack legitimate access. They must breach security controls, steal credentials, or exploit vulnerabilities to gain entry. Their activities often trigger security alerts because they operate outside normal patterns.
Internal threats originate from individuals with authorized access. Their activities blend with normal business operations, making detection significantly more challenging. They don't need to bypass security controls because they have permission to be there.
The challenge intensifies with compromised insider threats, where external attackers use stolen credentials from legitimate users. These attacks combine the stealth of insider threats with the malicious intent of external actors, making them particularly dangerous.
Types of Insider Threats Explained
Understanding the different categories of insider threats helps you build appropriate detection and prevention strategies. According to the 2024 Cybersecurity Insiders Insider Threat Report, 74% of organizations reported that insider attacks have become more frequent.
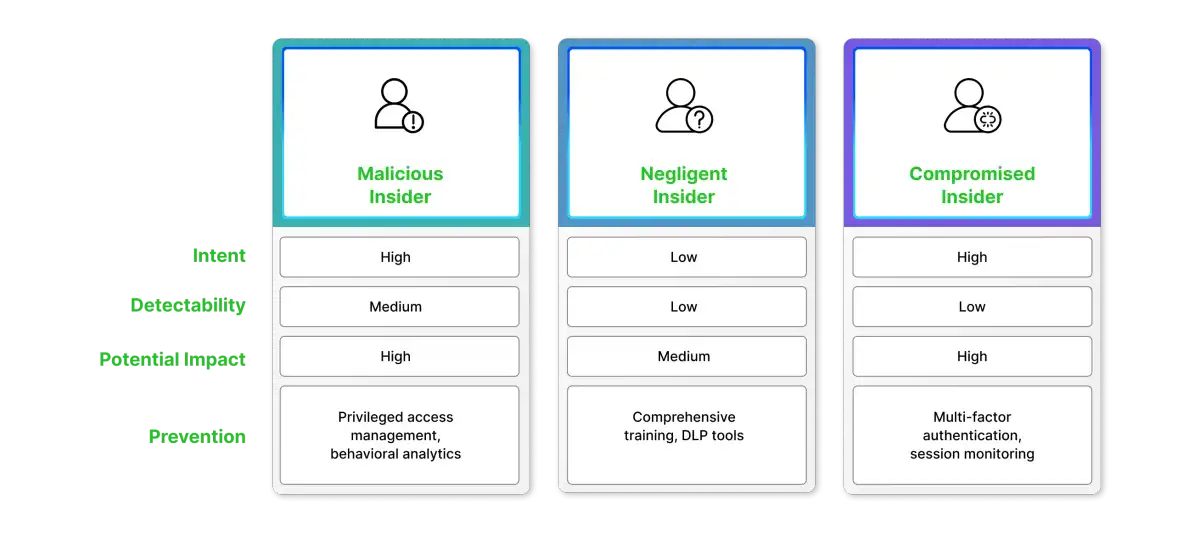
1. Malicious Insider Threat
A malicious insider is someone who intentionally abuses their authorized access to harm the organization. Their motivations vary from financial gain and revenge to espionage and ideology.
Common characteristics include behavioral warning signs before acting (sudden financial stress, vocal dissatisfaction with management, policy violations), gradually escalating privilege abuse over time to test detection capabilities, operating during off-hours or just before termination, and targeting specific high-value data like intellectual property, customer databases, or financial records.
Real-world example: Edward Snowden, a contractor at the National Security Agency (NSA), leaked classified information in 2013. Snowden used his authorized access to systematically download and exfiltrate thousands of classified documents, exploiting his understanding of internal security controls to avoid detection until after the damage was done.
Prevention tactics include implementing least privilege access so employees have only the permissions necessary for their current role, using privileged access management (PAM) to monitor and control administrative accounts, deploying user behavior analytics (UBA) to detect anomalous access patterns, conducting regular access reviews to ensure permissions remain appropriate, and maintaining comprehensive audit logs that track who accessed what data and when.
2. Negligent Insider Threat
A negligent insider causes harm through carelessness, lack of security awareness, or failure to follow security policies. They have no malicious intent but their actions create vulnerabilities that attackers can exploit. According to SentinelOne's research, negligent insiders are responsible for 62% of all insider incidents, making this the most common category.
These incidents include falling for phishing attacks that compromise their credentials, using weak passwords or sharing credentials with colleagues, misconfiguring cloud storage to be publicly accessible, sending sensitive data to personal email accounts for convenience, installing unauthorized software that contains malware, and leaving laptops unlocked in public spaces.
Real-world example from healthcare: An employee at a healthcare organization wanted to work on patient records from home. They emailed files containing protected health information (PHI) to their personal Gmail account for convenience. The personal account had weak security and was later compromised in a credential stuffing attack, exposing thousands of patient records and resulting in HIPAA violations and regulatory fines.
Prevention tactics include providing comprehensive security awareness training covering phishing, password hygiene, and data handling, implementing data loss prevention (DLP) tools to block unauthorized data transfers, using multi-factor authentication (MFA) to protect against compromised passwords, deploying endpoint protection that prevents installation of unauthorized software, creating clear, simple security policies that employees can actually follow, and using automated provisioning to ensure new employees receive appropriate, not excessive, access.
3. Compromised Insider Threat
A compromised insider is a legitimate user whose credentials have been stolen by an external attacker through phishing attacks, social engineering, malware, or other attack methods. The attacker then uses these valid credentials to access organizational systems and carry out malicious activities while appearing in logs as the legitimate employee, making detection extremely difficult since all access appears authorized. According to the 2024 IBM X-Force Threat Intelligence Index, compromised credentials are involved in 16% of all security breaches.
How credentials get compromised:
- Phishing attacks trick users into entering credentials on fake login pages designed to look identical to legitimate corporate portals.
- Password reuse across multiple sites, where a breach at one site exposes credentials used elsewhere, makes users vulnerable to credential stuffing attacks.
- Keyloggers and malware are installed on employee devices that record every keystroke, including usernames and passwords.
- Credential stuffing attacks use passwords leaked from other breaches, where attackers systematically test stolen credentials against your systems.
- Social engineering is where attackers pose as IT support to obtain passwords, exploiting human trust rather than technical vulnerabilities.
Real-world example: A marketing employee received a convincing phishing email that appeared to be from their IT department, asking them to verify their credentials on what looked like the company login page. The attacker captured the credentials and used them to access the company's customer database, downloading contact information and purchase histories over several weeks. The breach was only discovered when anomaly detection flagged unusual file access patterns from the employee's account during vacation time.
Prevention tactics include enforcing multi-factor authentication organization-wide to prevent credential-based access, deploying endpoint detection and response (EDR) to identify malware and keyloggers, using session monitoring to detect impossible travel scenarios (same user logging in from different countries within minutes), implementing behavioural analytics to flag access patterns inconsistent with the user's normal behaviour, requiring periodic password changes and prohibiting password reuse, and using identity governance platforms that can automatically suspend accounts showing signs of compromise.
4. Collusion Threats
Collusion threats involve insiders collaborating with outsiders or other insiders to bypass security controls and steal data or commit fraud. These threats are particularly difficult to detect because they involve multiple individuals with legitimate access working together to circumvent normal oversight mechanisms.
Common scenarios include IT administrators partnering with external hackers to provide access credentials or disable security controls, employees in finance departments collaborating to create fraudulent transactions that bypass separation of duties policies, and contractors working with competitors to steal intellectual property or customer lists.
Prevention tactics include implementing strong separation of duties (SoD) policies that prevent any single individual from completing sensitive transactions alone, using identity governance platforms to detect conflicting permissions that enable collusion, monitoring for unusual patterns of access by multiple users to the same sensitive resources within short timeframes, and conducting regular access certifications that require managers to justify why each employee needs specific permissions.
What Causes Insider Threats?
Understanding root causes helps organizations address vulnerabilities proactively rather than reacting to incidents after they occur. Insider threats stem from both human factors and systemic weaknesses in organizational security.
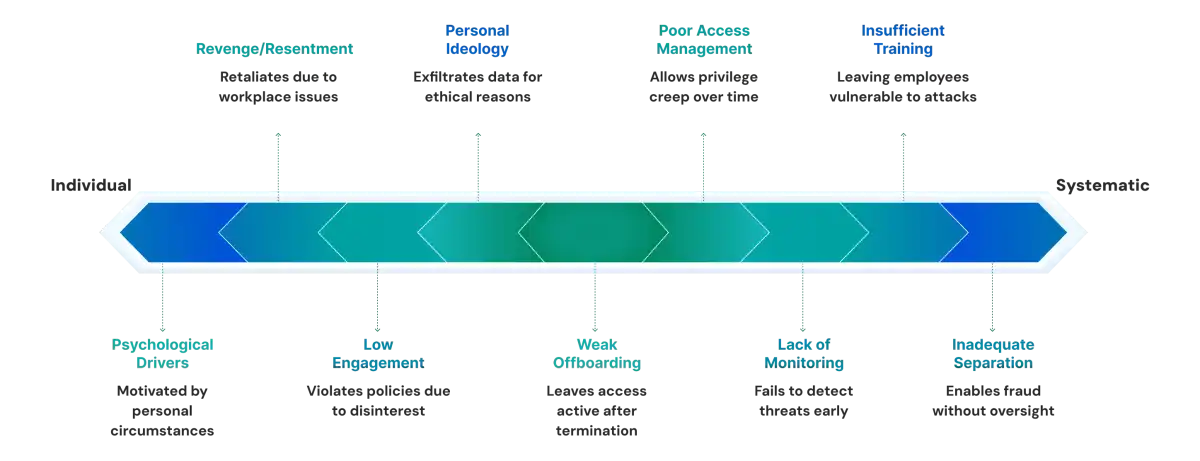
1. Human Factors
Psychological and emotional drivers:
- Financial stress pushes employees to steal data or commit fraud for monetary gain. According to research, financial difficulties are a leading indicator of potential malicious insider behavior.
- Revenge and resentment motivate sabotage and data theft. Employees passed over for promotion, facing disciplinary action, or experiencing workplace conflicts may retaliate against their employer.
- Low engagement and job dissatisfaction correlate with increased security policy violations and careless behavior. Disengaged employees are less likely to follow security procedures carefully.
- Personal ideology or beliefs can drive data exfiltration for whistleblowing purposes, as seen in high-profile cases like Edward Snowden.
2. Systemic Causes
Organizational and technical weaknesses:
- Weak offboarding processes leave access active for terminated employees, creating significant security gaps.
- Poor access management results in privilege creep, where employees accumulate permissions over time without proper review.
- Lack of monitoring and behavioral analytics means insider threats go undetected for extended periods.
- Insufficient security awareness training leaves employees vulnerable to phishing and social engineering.
- Inadequate separation of duties enables single individuals to complete fraudulent transactions without oversight, facilitating both malicious activity and collusion.
- Complex cloud environments and rapid digital transformation create security gaps.
Insider Threat Detection and Indicators
Detecting insider threats requires a fundamentally different approach than detecting external attacks. You're not looking for someone breaking in; you're looking for someone misusing access they legitimately have.
1. Behavioral Indicators and Warning Signs
Unusual access patterns:
- Accessing data outside normal job responsibilities, such as a marketing employee querying financial databases or an HR staff member viewing engineering project files.
- Large data downloads or file transfers, particularly when the volume significantly exceeds typical usage patterns for that user's role.
- Access to systems during unusual hours, especially when the employee typically works standard business hours and suddenly logs in at 3 AM or on weekends.
- Repeated access to the same sensitive files without clear business justification, suggesting potential preparation for data exfiltration.
2. Policy Violations
- Failed login attempts followed by successful access from unusual locations, indicating potential credential compromise.
- Attempts to access restricted systems or escalate privileges beyond granted permissions, suggesting reconnaissance for potential attacks.
- Using unauthorized external storage devices or cloud services to transfer data violates data loss prevention policies.
- Disabling security software or attempting to clear audit logs indicates efforts to hide malicious activity.
3. User and Entity Behavior Analytics (UEBA)
User and Entity Behaviour Analytics (UEBA) continuously analyzes user behaviour to establish individual baselines for login patterns, data access volumes, application usage, and work locations. When activity deviates from these established norms, like a 9-to-5 employee logging in at 3 AM or downloading 100x their usual data volume, the system triggers alerts for security investigation.
What UEBA monitors:
- Login times and locations to detect access from unusual places or times that don't match the employee's normal work pattern.
- Data access patterns showing what files users view, how much data they download, and how often they access specific resources.
- Application usage tracking which systems users interact with, when they use them, and for how long.
- Network activity monitoring data transfers, connections to external sites, and bandwidth usage.
- Privileged action frequency tracking administrative commands, configuration changes, and high-risk operations.
Real-world detection scenario: A financial analyst who typically accesses 10-20 customer records per day suddenly queries 5,000 records. This triggers an alert. An employee who normally works 9-5 EST suddenly logs in at 3 AM from a different country. This generates a high-risk signal. A developer who usually commits code changes during business hours suddenly downloads the entire source code repository at midnight. This raises red flags.
4. IGA Integration for Detection
Modern identity governance solutions incorporate behavioural analytics directly into the access management workflow. When anomalous behaviour is detected, the system can automatically trigger additional authentication requirements, temporarily suspend access pending investigation, notify security teams for immediate response, or initiate an access review of that user's permissions to determine if they have excessive privileges.
Identity Confluence provides continuous monitoring that validates every access decision remains appropriate in real-time, tracking role changes to ensure employees who move to new positions don't retain unnecessary access, monitoring project completion to remove project-specific access when initiatives end, automatically revoking time-based access grants when they expire, identifying separation of duties violations for immediate remediation, and detecting orphaned accounts for terminated employees whose access wasn't properly disabled.
How to Prevent Insider Threats (IGA-Linked)
Preventing insider threats requires a multi-layered approach combining people, processes, and technology. Identity governance forms the foundation by ensuring users have appropriate access throughout their employment lifecycle.
Enforce Least Privilege Access via IGA
Least privilege means users receive the minimum permissions necessary to perform their job functions, nothing more. This fundamental principle dramatically reduces insider threat risk by limiting what any single compromised account can access.
How least privilege prevents insider threats:
- Reduces the potential damage any single compromised account can cause by limiting the scope of data and systems accessible with those credentials.
- Limits accidental exposure of sensitive data by ensuring employees can only access information directly relevant to their work.
- Decreases the attack surface for credential theft, as stolen credentials have limited value when they only grant minimal access.
- Makes anomalous activity easier to detect because any unauthorized access attempt becomes immediately suspicious when users should only access specific, well-defined resources.
Continuous Access Review and Certification
Static access grants become inappropriate over time as employees change roles, complete projects, or accumulate permissions without corresponding need. Regular access certifications address this privilege creep.
Access certification campaigns require managers to periodically review and validate all access rights held by their team members. The process asks: "Does this employee still need access to this application for their current role?" Managers approve, modify, or revoke each entitlement based on current business needs.
Best practices for effective certifications:
- Schedule certifications at least quarterly for systems containing sensitive data or privileged access
- Make the process easy for managers with clear explanations of what each permission allows and why the employee originally received it
- Automatically revoke access if managers don't respond within the certification deadline, ensuring that unjustified permissions don't persist indefinitely
- Provide analytics showing which teams have the most unreviewed or excessive permissions to identify high-risk areas requiring attention
- Use risk scoring to prioritize which access requires the most scrutiny based on sensitivity and potential for abuse
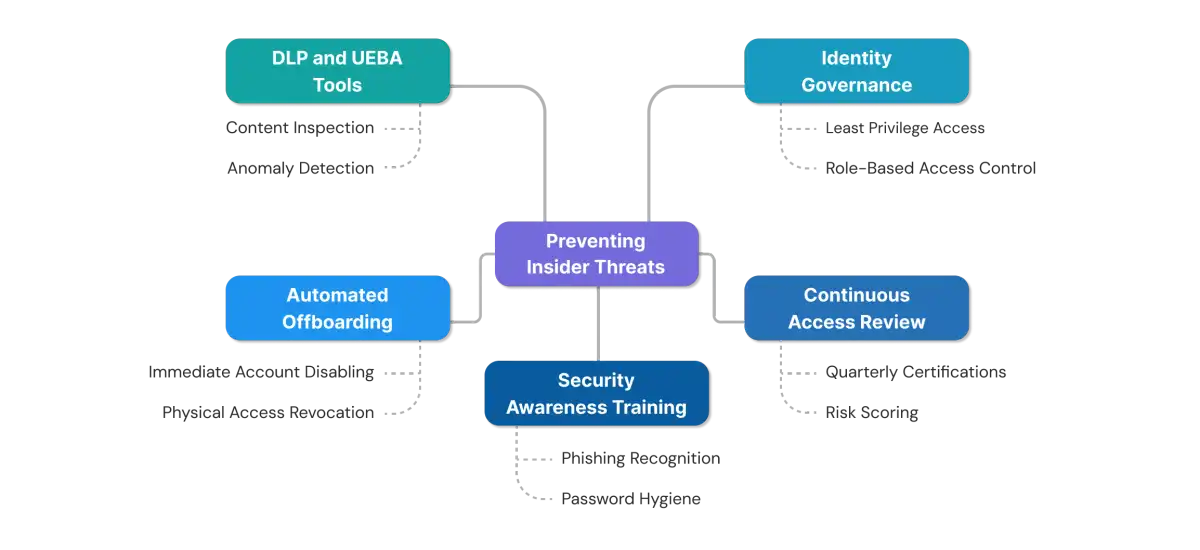
Train Employees on Security Awareness
Most negligent insider incidents result from lack of awareness rather than malice. Comprehensive security awareness training transforms employees from security vulnerabilities into active defenders.
Effective training programs cover:
- Phishing recognition teaching employees to identify suspicious emails, fake login pages, and social engineering attempts.
- Password hygiene emphasizing strong, unique passwords, proper credential management, and dangers of password reuse.
- Data handling procedures explaining how to properly store, transmit, and dispose of sensitive information.
- Policy understanding ensuring employees know organizational security policies and consequences of violations.
- Incident reporting procedures making it easy for employees to report suspicious activity or potential security incidents.
Training should be:
- Ongoing and reinforced regularly, not just annual checkbox exercises.
- Interactive and engaging using real-world scenarios and simulations rather than dry presentations.
- Role-specific addressing the particular threats and responsibilities relevant to each employee's position.
- Measurable with assessments and simulated phishing tests to verify effectiveness and identify areas for improvement.
Automate Offboarding and Access Revocation
Terminated employees whose access hasn't been revoked represent one of the highest-risk insider threat scenarios. They may have motivation for revenge, advance knowledge of security controls, and extended time to exfiltrate data before departure.
Automated offboarding eliminates this risk by triggering immediate access revocation across all systems when employment status changes.
This process is part of comprehensive Identity Lifecycle Management that orphan accounts.
Complete offboarding process:
- Immediate account disabling across all applications, databases, VPNs, and cloud services the moment termination is entered in the HR system.
- Physical access revocation including building badges, parking passes, and access cards.
- Password resets for shared accounts the departed employee had access to, preventing them from using passwords they may have memorized.
- Data transfer ensuring any business-critical files owned by the departing employee are transferred to appropriate team members.
- Device recovery retrieving laptops, mobile phones, and other hardware that may contain organizational data.
- Audit of recent activity reviewing the employee's access logs in the period before termination to identify any suspicious data downloads or unusual behavior.
Use DLP and UEBA Tools
Data Loss Prevention (DLP) and User and Entity Behavior Analytics (UEBA) provide complementary capabilities for detecting and preventing insider threats through technical controls and intelligent monitoring.
DLP tools monitor data movement across the organization, identifying and blocking unauthorized transfers of sensitive information. When integrated with identity governance, DLP becomes context-aware, understanding not just that data is being copied but whether that user's role justifies the action and whether the timing aligns with normal business operations.
DLP capabilities include:
- Content inspection scanning files, emails, and network traffic for sensitive data based on patterns, keywords, or classification labels.
- Policy enforcement automatically blocking or quarantining data transfers that violate organizational policies.
- Encryption enforcement ensuring sensitive data is encrypted before leaving the organization's control.
- Endpoint protection monitoring and controlling data transfers via USB drives, cloud storage, email, and other channels.
- UEBA tools establish baseline behavior patterns for users and entities, then alert on deviations that may indicate insider threats.
UEBA capabilities include:
- Behavioral baselines establishing what normal looks like for each user's access patterns, work hours, data usage, and application interactions.
- Anomaly detection identifying deviations from established baselines that may indicate compromise or malicious activity.
- Risk scoring calculating risk scores for users based on their behavior, access rights, and contextual factors.
- Peer group analysis comparing user behavior to peers in similar roles to identify outliers requiring investigation.
Real-World Insider Threat Examples
Examining actual insider threat incidents provides valuable lessons about how these attacks occur and how organizations can prevent similar breaches.
Edward Snowden - Malicious Intent
Edward Snowden, a contractor at the National Security Agency (NSA), leaked classified information in 2013. Snowden used his authorized access to systematically download and exfiltrate thousands of classified documents about government surveillance programs.
What made it possible:
- Snowden held privileged access as a systems administrator, giving him broad permissions across NSA systems.
- He understood internal security controls and knew how to access and download files without triggering immediate alerts.
- The NSA lacked sufficient monitoring of privileged user activity to detect the massive data exfiltration in progress.
Lessons learned and IGA prevention:
- Privileged access management with comprehensive monitoring and session recording would have detected unusual download patterns.
- Separation of duties preventing any single administrator from accessing and exporting massive volumes of classified data without approval.
- Behavioral analytics flagging when a user's access patterns deviate dramatically from their normal work activities.
- Just-in-time access granting elevated permissions only for specific tasks and automatically revoking them afterward.
Capital One Insider Data Breach - Negligence and Compromise
In 2019, Capital One suffered one of the largest financial data breaches, affecting over 100 million customers in the U.S. and 6 million in Canada. The breach was caused by Paige A. Thompson, a former Amazon Web Services (AWS) engineer who exploited a misconfigured web application firewall.
According to U.S. Department of Justice records, Thompson used her knowledge of cloud infrastructure from her previous employment at AWS to identify and exploit misconfigurations. She created a scanning tool to systematically test AWS accounts for firewall vulnerabilities, identifying Capital One's vulnerable servers.
Court documents reveal that Thompson posted about her theft on GitHub and other platforms, bragging about accessing Capital One data under the alias "erratic." The breach went undetected from March through July 2019 until an anonymous tip alerted Capital One to data being stored openly on GitHub.
What made it possible:
- Misconfigured firewall settings allowed commands to reach internal servers from external sources.
- Overly broad IAM roles granted permissions wider than necessary for the application's functions.
- Insufficient monitoring and alerting failed to detect when Thompson ran specific command-line instructions to list and copy S3 buckets.
- Complex cloud infrastructure created visibility gaps where security teams couldn't monitor all data and systems effectively.
- According to research published in ACM Transactions on Privacy and Security, Capital One failed to establish effective risk assessment processes prior to migrating IT operations to the cloud and lacked appropriate risk management including network security controls and data loss prevention capabilities.
The consequences:
- Capital One was fined $80 million by the Office of the Comptroller of the Currency (OCC).
- The company settled customer lawsuits for $190 million.
- Thompson was convicted of wire fraud and unauthorized access to a protected computer, facing up to 20 years in prison.
- Capital One's stock initially fell 5.9% and lost 15% over two weeks following the breach disclosure. The breach cost Capital One over $270 million in fines and settlements.
Calculate your organization's potential insider threat exposure based on your current security posture.
Calculate ROI
Lessons learned and IGA prevention: Least privilege access, ensuring cloud IAM roles have only the minimum permissions required for their specific functions.
- Automated access reviews regularly certify that access rights remain appropriate and identify overly broad permissions.
- Configuration management using tools like AWS CloudTrail for monitoring and alerting on command-line activity and security configuration changes.
- Identity governance providing visibility into who has access to what across complex cloud environments and detecting access anomalies.
- Regular security assessments identifying misconfigurations and vulnerabilities before attackers exploit them.
Healthcare Insider Leak Case - Negligence
Healthcare organizations face unique insider threat challenges due to the sensitivity of protected health information (PHI) and strict HIPAA requirements. A common scenario involves employees accessing patient records for reasons outside their job responsibilities.
In a typical case, a hospital employee used their authorized access to view medical records of family members, neighbors, and even celebrities being treated at the facility. The unauthorized access violated HIPAA regulations and resulted in significant fines and reputational damage.
What made it possible:
- Broad access grants giving employees permission to view any patient record in the system rather than limiting access to patients under their care.
- Lack of monitoring for unusual access patterns such as viewing records unrelated to assigned duties.
- Insufficient audit log review to detect unauthorized access after it occurred.
- Absence of separation of duties policies limiting who could access particularly sensitive patient records.
Lessons learned and IGA prevention:
- Role-based access control limits access to patient records based on specific job functions and assigned patients
- Automated monitoring detects when employees access records for patients they're not assigned to treat
Why Insider Threats Are a Growing Cybersecurity Risk
Insider threats are increasing in frequency, sophistication, and cost, driven by technological changes and evolving work patterns that expand the attack surface.
Hybrid Work and Remote Access
The shift to hybrid and remote work has fundamentally changed insider threat dynamics, creating expanded security challenges with distributed workforces. Remote work increases insider threat risk through expanded network perimeters as employees access systems from home networks and public spaces with varying security levels, reduced visibility when security teams can't observe physical actions or monitor on-premises traffic, personal device usage that blurs corporate and personal data boundaries, decreased social oversight as employees work in isolation, and VPN infrastructure becoming prime targets for credential-based attacks that provide direct paths into organizational networks.
Cloud Access and SaaS Proliferation
Cloud adoption and Software-as-a-Service (SaaS) applications create new opportunities for insider misuse through multiple challenge vectors. Organizations face data stored across multiple cloud platforms, creating visibility gaps where security teams can't monitor all resources; SaaS applications with independent access controls that aren't integrated with central identity governance, allowing privilege creep; easy data exfiltration through cloud storage services and file sharing platforms; misconfigured cloud resources exposing sensitive data due to the complexity of security settings, as demonstrated in the Capital One breach; and shadow IT, where employees adopt unauthorized cloud services creating access and data movement outside IT visibility.
Regulatory and Compliance Impact
Insider threats carry significant regulatory consequences beyond direct incident costs, as organizations face mounting pressure from regulations holding them accountable for protecting sensitive data against internal threats. GDPR requires appropriate technical measures, including access controls to prevent unauthorized insider access, with violations resulting in fines up to 4% of annual global revenue. HIPAA mandates minimum necessary access to protected health information and comprehensive audit logging, with insider breaches resulting in substantial fines and mandatory breach notifications. SOX requires the separation of duties and access controls for financial systems to prevent fraud, triggering regulatory investigations and potential criminal charges for insider financial crimes. PCI DSS requires least privilege access and regular access reviews for systems handling payment card data, with insider breaches resulting in fines and potential loss of payment processing capabilities.
Role of Identity Governance in Preventing Insider Threats
Identity Governance and Administration (IGA) provides the visibility, control, and automation needed to address the insider threat challenge comprehensively. While traditional security tools focus on keeping external threats out, IGA manages threats that originate from within by controlling and monitoring access rights.
Understanding the difference between IAM and IGA is crucial, as IGA specifically addresses governance aspects that prevent insider threats.
Why IGA Is Essential for Insider Threat Prevention
IGA platforms address insider threats at their root by ensuring that access rights are appropriate, monitored, and continuously validated throughout the employee lifecycle.
-
Centralized visibility across all applications, databases, and systems shows who has access to what, enabling faster threat detection
-
Policy enforcement defines and automatically enforces access policies based on roles, attributes, and risk. This prevents unauthorized access before it happens rather than detecting it after damage is done
-
Automated workflows eliminate manual processes that create delays and errors in provisioning and deprovisioning, enabling immediate response to threats
-
Audit and compliance, maintaining complete records of who accessed what, when, why, and under whose approval. This provides forensic evidence for investigations and generates reports for SOX, GDPR, HIPAA, and other regulatory requirements
-
Risk-based access applies stricter controls to high-risk users and sensitive resources while maintaining user productivity for low-risk scenarios through adaptive authentication and dynamic access policies
How Identity Platforms Address Insider Threats
IGA Platform provides comprehensive insider threat prevention through integrated identity governance capabilities designed specifically to address internal security risks.
-
Automated User Lifecycle Management
Integrates with HR systems to automatically provision appropriate access for new employees, adjust permissions when roles change, and immediately revoke all access when employment ends. This eliminates the common vulnerabilities of delayed deprovisioning and forgotten accounts that create insider threat opportunities.
The platform maintains a complete identity profile for each user, tracking their role, department, location, manager, and employment status. When any of these attributes change in the HR system, the platform automatically triggers appropriate access adjustments without manual intervention. -
Dynamic Access Policies
Uses role-based access control (RBAC) and attribute-based access control (ABAC) to ensure users receive only the access their current role and attributes justify. When roles change, access automatically adjusts without manual intervention.
The platform supports complex access policies that consider multiple factors: role, department, location, seniority, project assignments, and custom attributes. This enables fine-grained access control that adapts to your organization's specific requirements. -
Continuous Access Certification
Managers regularly review and validate team member access rights through automated certification campaigns. It recommends access that should be removed based on role changes or inactivity, tracks certification completion with automated reminders and escalations, and automatically revokes unjustified permissions after certification deadlines pass.
The platform provides intelligent recommendations during certifications, identifying access that appears excessive, hasn't been used recently, or doesn't align with the user's current role. This helps managers make informed decisions quickly without requiring deep technical knowledge of every application. -
Separation of Duties Enforcement
It automatically detects and prevents conflicting permission combinations that violate separation of duties policies. Before granting new access, the platform checks whether it would create SoD violations and flags them for compliance review before allowing exceptions.
The platform comes pre-configured with common SoD rules for financial systems, privileged access, and sensitive data, while also supporting custom rules tailored to your organization's specific compliance requirements. -
Identity Analytics and Risk Scoring
Identity Confluence calculates risk scores for each user based on their access rights, behavior patterns, and contextual factors. The platform highlights users with excessive privileges, unusual access patterns, or risky entitlement combinations requiring investigation.
Risk scoring considers factors including the number and sensitivity of permissions, recent access changes, failed authentication attempts, access during unusual hours, data download volumes, and deviations from peer group behavior patterns. -
Comprehensive Audit Trails
Every access change, approval, certification, and policy violation is recorded across all connected systems. Identity Confluence provides forensic evidence for investigations and generates compliance reports for auditors demonstrating how the organization controls and monitors access rights.
Audit trails capture not just what changed but also who approved it, why it was granted, when it was last reviewed, and what business justification supported the access decision. This level of detail is essential for regulatory compliance and insider threat investigations. -
Pre-Built Connectors
Identity Confluence integrates with 50+ enterprise applications including Salesforce, Azure AD, Google Workspace, SAP, Workday, AWS, and major cloud platforms. This ensures consistent governance across your entire technology stack without requiring custom integration development.
The platform's connector framework enables rapid onboarding of new applications as your technology environment evolves, maintaining comprehensive access governance even as systems change.
Final Thoughts
Insider threats represent one of the most challenging aspects of modern cybersecurity because they exploit the trust and access necessary for business operations. Traditional security defenses designed to keep attackers out offer little protection against threats that originate from within.
As we've seen throughout this guide, insider incidents are costly and difficult to detect. Whether the threat comes from malicious insiders, negligent employees, or compromised credentials, the impact can be devastating to organizations of all sizes.
The solution lies in identity governance. By implementing comprehensive IGA solutions that enforce least privilege, automate user lifecycle management, maintain continuous access oversight, and provide identity analytics, organizations can significantly reduce their insider threat risk while enabling the access employees need to be productive.
Identity Confluence provides the integrated identity governance capabilities needed to address insider threats effectively. From automated provisioning and deprovisioning to continuous access certifications, separation of duties enforcement, and identity risk analytics, the platform helps organizations transform identity from a vulnerability into a security strength.
The question isn't whether your organization faces insider threats; it's whether you have the visibility, controls, and automation to detect and prevent them before they cause significant damage.
Ready to protect your organization from insider threats?
Discover how Identity Confluence provides comprehensive identity governance to prevent insider risks through automated access controls, continuous monitoring, and intelligent behavioural analytics.
The future of cybersecurity is not about building taller walls but about knowing who is at the gate and what they should be able to access once they get through the gate.
Frequently Asked Questions (FAQs)
1. What is an insider threat in cybersecurity?
An insider threat is a security risk from someone within the organization who has legitimate access and uses it to cause harm, either intentionally, accidentally, or through compromised credentials.2. What are the main types of insider threats?
The three main types are malicious insiders (intentional harm), negligent insiders (careless mistakes), and compromised insiders (stolen credentials used by external attackers).3. How can insider threats be prevented?
Prevent insider threats through least privilege access, regular access certifications, automated offboarding, user behaviour analytics, data loss prevention tools, and security awareness training.4. What is an example of an insider threat?
The Capital One breach, in which a former AWS engineer exploited misconfigured firewalls to steal data from 100 million customers, or employees emailing sensitive files to personal accounts.5. How does IGA help prevent insider threats?
IGA automates least privilege, continuously monitors access rights, immediately revokes access upon termination, detects anomalies, enforces separation of duties, and maintains audit trails.6. How long does it take to detect an insider threat?
Average detection time is 81 days according to the 2025 Ponemon Report, though organizations with mature IGA programmes detect threats significantly faster.7. What industries face the highest insider threat costs?
Financial services face the highest costs, followed by healthcare, professional services, and technology sectors, due to sensitive data and regulatory requirements.8. What are the warning signs of a potentially malicious insider?
Warning signs include financial stress, workplace dissatisfaction, accessing data outside the job scope, unusual access hours, large downloads, privilege escalation attempts, and behavioural changes.9. How quickly should access be revoked when employees leave?
Access should be revoked immediately upon termination through automated offboarding integrated with HR systems to eliminate security gaps.10. What role does behavioural analytics play in insider threat detection?
Behavioural analytics establishes normal user patterns and alerts on deviations like unusual access times, locations, data volumes, or application usage that indicate potential threats.



