
What Is Lateral Movement in Cybersecurity?

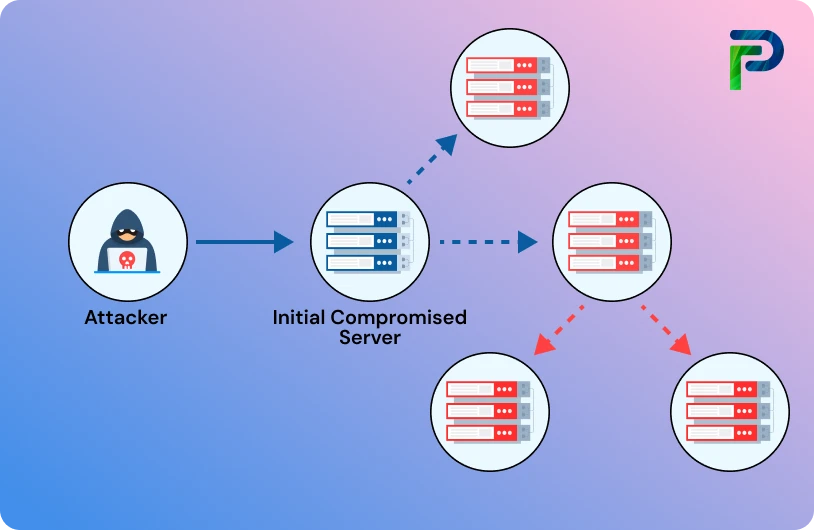
Lateral movement, in a cybersecurity context, refers to the way attackers expand their reach into a compromised network by moving horizontally from different systems in order to try and uncover valuable data or find privileged accounts. Once attackers gain an initial foothold, typically through a compromised endpoint, lateral movement allows them to strengthen their position inside the environment, explore internal systems, and quietly advance toward more sensitive assets.
Attackers usually find, access, and compromise your high-value assets as part of this process. They can move to hijack sensitive data, escalate privileges, and evade defenses in real time. It is not the first breach that does the most damage in the attack lifecycle, but what happens after the primary breach, when the attacker can then dwell inside the systems, or move laterally throughout the internal systems, typically for weeks before being discovered.
Lateral movement attacks are a crucial component of modern cyberattacks, playing a significant role in advanced persistent threats (APTs) and ransomware operations. They represent one of the most dangerous and most difficult phases of an attack to detect in the cyber kill chain.
In this blog post, we will examine the meaning of lateral movement, how these types of attacks operate, and how you can leverage identity governance, network segmentation, and Zero Trust strategies to detect and contain them before they spread throughout your organisation.
Key Takeaways
- Lateral movement occurs following an initial compromise and allows an attacker to gain increasing control within internal systems.
- Often used for privilege escalation and accessing sensitive assets, lateral movement is often seen prior to data theft or deploying ransomware.
- Techniques that employ lateral movement include, but are not limited to: Pass-the-Hash, RDP abuse, and Credential Dumping.
- It can be detected early utilising EDR, SIEM, or behavioural analytics that reveal anomalies in east-west network traffic.
- Preventing lateral movement generally involves applying least-privilege access, Zero Trust segmentation, and access control based on identity governance and administration (IGA).
Understanding Lateral Movement
Simply put, lateral movement occurs after an attacker has infiltrated your network. Rather than moving directly to a primary target, they will "move sideways" through various systems, applications, or users to locate valuable credentials, sensitive data, or higher privileges.
Imagine an intruder making entry through an unlocked side door and then making his way through a series of rooms to locate the vault. This so-called "east–west" movement within the network can often mimic normal user or admin activity, making it exceedingly difficult to detect.
Lateral movement has its purpose and is contrasted to vertical movement, where the attacker escalates their privileges on a specific system (for example, from standard user to admin). In this situation, lateral movement is spreading across systems - using existing trust relationships, weak credentials, or misconfigured permissions, to get further access.
In the cyber kill chain, lateral movement occurs between initial access and data exfiltration. This is the point in an attack when the attacker begins to consolidate control to prepare for the endgame, whether that will be to exfiltrate data, deploy ransomware, or build a persistence capability inside the environment.
How Lateral Movement Works (Attack Stages)
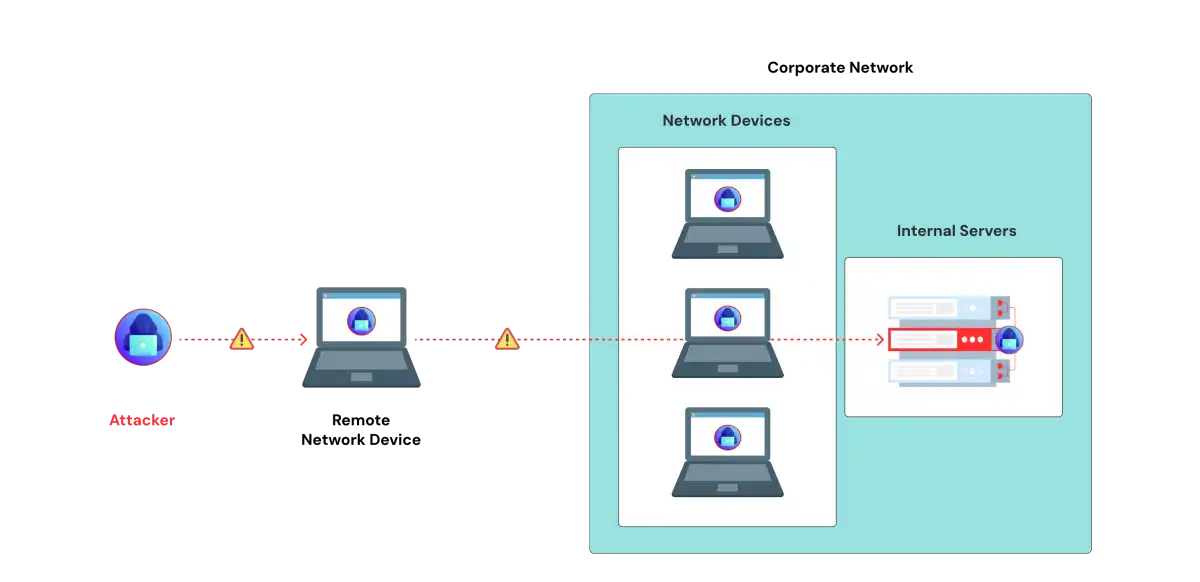
After gaining access to your environment, the next step for attackers is lateral movement to locate high-value systems, collect better credentials and escalate privileges. This usually takes place in three stages: internal reconnaissance, credential harvesting and lateral movement.
Stage 1 - Internal Reconnaissance
Internal reconnaissance represents the stage at which attackers are attempting to understand your environment from the inside. When starting with an initial access, they assess your environment, observe your infrastructure, understand how the systems are interconnected, and start to look for targets or weak points. This is where attackers are evaluating the vulnerabilities in your network and identifying the lowest effort decisions to pivot to more direct access.
Once the attackers are "inside", they start with the task of mapping your internal environment, which systems are available, what capabilities or privileges they have, which networks can be traversed, etc. Attackers scan internal IP ranges, Active Directory objects, user groups, and any listeners or other assets of which they can find access.
Common tools like Nmap, BloodHound and AD enumeration scripts help adversaries to locate misconfigured systems, exposed services and the path of least resistance to domain control.
Stage 2 - Credential Harvesting & Privilege Escalation
When reconnaissance has been completed, the next move is to steal credentials and escalate their access. This is the footprint from identity-based attacks becoming dangerous, because once an adversary can impersonate a legitimate user, bypassing many traditional defences becomes easier.
Common techniques related to credential theft, credential dumping from LSASS, Mimikatz, Pass-the-Hash, Pass-the-Ticket, and Kerberoasting, enable credential stealing and credential abuse or misuse.
Reconnaissance will elevate access; it's only a first step into moving across the network, meaning the adversary can now do higher-impact actions without restriction. They can alter system configurations, view sensitive data, create accounts, mitigate defences, plus prepare to act on larger objectives that meet the adversary’s goals, like data theft or deploying ransomware.
Stage 3 - Lateral Spread & Access Expansion
As attacks achieve higher privileges, they will begin pivoting and travelling deeper into the network, often to fully access new systems, applications, or sensitive data.
Attackers will typically spread laterally using RDP, SMB, PsExec, WinRM and PowerShell, often disguising themselves as legitimate users, are even use admin shares to remain hidden.
One of the most notable examples is the SolarWinds compromise in 2020, where attackers were able to move and expand access across multiple internal systems through the use of stolen credentials and their identity-based lateral movement behaviour.
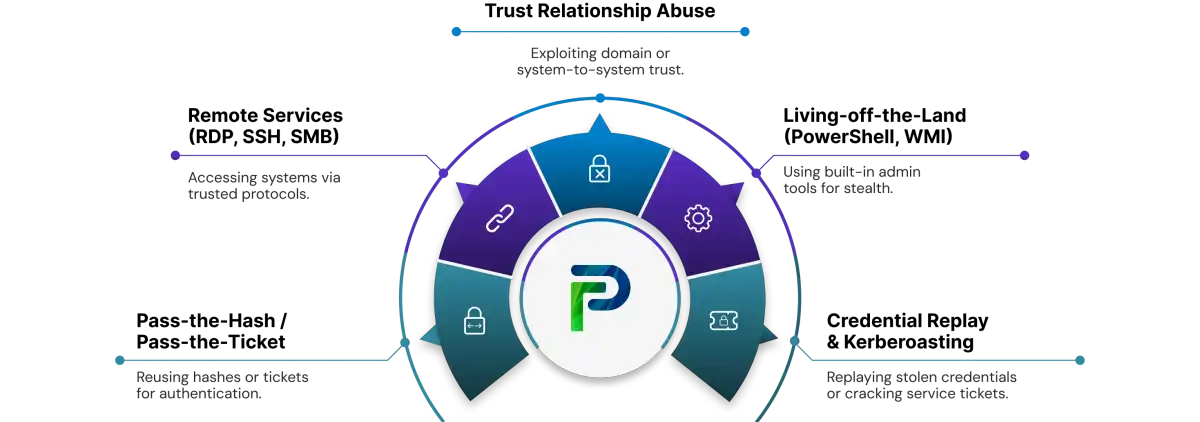
Common Lateral Movement Techniques
Malicious actors utilise trusted tools, legitimate protocols, and built-in capabilities of the system to progress laterally without notice. Much like legitimate administrators operate, these tactics blend into the normal use of identity and network activity, making these undesirable behaviours that much harder to identify.
1. Pass-the-Hash / Pass-the-Ticket
Attackers acquire a hashed version of a user's password or a Kerberos ticket from a compromised system. Rather than going through the trouble of cracking it, they simply take the hash or ticket and log in as that user without the password verification process and MFA. This allows them to surreptitiously jump from system to system without raising typical alerts for authenticating. Pass-the-Hash attacks depend heavily on the presence of active, outdated, unmonitored, or unnecessary accounts.
2. Exploiting Remote Services (RDP, SSH, SMB)
With acquired or weak credentials, attackers can access remote services, often referred to by their protocol name, such as RDP (remote Windows login), SSH (remote login for Linux systems), and SMB (file sharing protocol).
These protocols will be commonly used in an enterprise environment and use cases like IT jobs, and become similar to normal expected behaviour, allowing attackers the comfort to pivot and move laterally across systems and services.
3. Taking Advantage of Trust Relationships
Attackers capitalise on the implicit trust relationships present between systems - such as domain trusts in Active Directory, shared service accounts, or overly permissive API/VM permissions.
Once trust is compromised on one of the trusted systems, attackers can leap through environments (for example, parent-child AD domains or cloud workloads) without needing new credentials.
4. Living-off-the-Land (PowerShell, WMI, PsExec)
Rather than utilising malware, attackers use built-in administrative tools - PowerShell, WMI, and PsExec - to execute commands, move files, or take control of endpoints. Due to the legitimacy and pre-installation of these tools, the activity appears normal, and this is why they are also referred to as "LOTL" - Living off the Land. The capture of the behaviour from these tools can be exceptionally difficult to detect.
5. Credential Replay & Kerberoasting
Credential replay is when an attacker uses previously stolen username/password pairs to access other systems without any modifications, rather than trying the same username/password as a set of credentials on another system or platform. Kerberoasting occurs against a Kerberos service for service accounts, the attacker extracts a service ticket, cracks the encryption offline, seizing elevated privileges and, in many cases, total domain compromise.
Real-World Examples of Lateral Movement Attacks
The most notable cyberattacks in the past ten years indicate that lateral movement is often the most significant phase of a breach. When attackers gain entry to a single endpoint or application, they employ identity-based techniques to expand their access, elevate privileges, and penetrate mission-critical systems. It is this internal proliferation that converts a contained event into an enterprise-wide breach.
Here is a summary of three prominent cases of lateral movement that greatly expanded the scope and scale of the attack.
1. SolarWinds (2020):
The SolarWinds event is perhaps the clearest example of how lateral movement can weaponise trusted relationships. Attackers compromised the Orion build server, inserted a malicious backdoor (Sunburst) into bona fide updates that propagated to SolarWinds customers, and expanded its footprint.
Once inside the SolarWinds customer environments, attackers did the following:
- Conducted AD enumeration to understand the domain structures
- Conducted Pass-the-Ticket and Golden SAML attacks to impersonate privileged accounts
- Engaged in lateral movement across cloud and on-prem systems in an effort to reach mail servers, identity platforms, and sensitive data
Since Orion was a trusted system with extensive privileges, the lateral spread was stealthy, quick, and extraordinarily difficult to detect, affecting more than 18,000 organisations.
2. WannaCry (2017):
In May of 2017, the WannaCry ransomware attack constituted a worldwide epidemic, targeting systems based on Microsoft Windows. After infecting a system, WannaCry encrypted users' files and demanded a ransom in Bitcoin for decrypting the files. The impact of WannaCry was amplified for two main reasons: many organisations were still using outdated Windows systems, and had little to no understanding of how critical security patches work to mitigate important vulnerabilities (which allowed WannaCry to spread much faster than it should have).
WannaCry even demonstrated a highly dangerous form of lateral movement: automated worm-like propagation. Once a single device was infected, it utilised the EternalBlue SMB exploit to efficiently intrude upon internal networks without the intervention of the attacker.
Some attacking attributes of internal spread are:
- No identity or credentials required (purely exploit-driven movement)
- The ability for rapid “east-west” movement across Windows systems
- Within minutes, encryption of files across the network
This type of lateral spread resulted in outages in hospitals, manufacturers, telecoms, and others, turning one compromised endpoint into thousands.
3. Contemporary Ransomware Operations:
Modern ransom groups (Conti, LockBit, BlackCat, etc.) are fully reliant on these lateral capabilities within networks for maximum operational impact. An attacker that has been granted initial access to a network typically:
- Harvest Active Directory credentials from the LSASS dump or Mimikatz, or take tokens.
- Move laterally using PsExec, WMI, or RDP options.
- Escalate privileges in AD or become a Domain Admin.
- Deploy ransomware across servers and endpoints during a single event.
By weaponising Active Directory privileges, a single coordinated push can encrypt entire organisations very quickly, making recovery costly and slow.
How to Detect Lateral Movement Early
It is important to identify lateral movement early because attackers often carry out moves silently for long periods before executing an observable attack. The bulk of detection methods rely on behaviour analytics, log correlation and anomalies to optimise against normal patterns of identity or network behaviour.
When lateral movement is attempted by attackers, even subtle activity on its behalf creates signals across endpoints, directories, logs on authentication and east/west traffic. The goal is to find these signals before they materialise into real compromises.
1. Monitor for Abnormal East–West Traffic
Lateral movement is comport mainly as an internal (east-west) activity, not traffic into or out of your network. Internal spikes in communication, especially between systems that do not usually communicate, may indicate reconnaissance or credential reuse.
Examples include the following:
- Workstations attempting to connect to multiple servers unexpectedly
- Uninvited upticks in SMB/RDP traffic from non-admin machines
- Repeated attempts on unauthorised network segments
2. Employ EDR, UEBA, and SIEM for Pattern Detection
Modern detection is increasingly dependent on correlating activity across tools:
- EDR (Endpoint Detection & Response): Flagged suspicious processes (e.g. Mimikatz, LSASS memory access).
- UEBA (User & Entity Behaviour Analytics): Identified identity anomalous such as logins at strange times, unusual privilege usage, or abnormal device access.
- SIEM (Security Information & Event Management): Correlated logs from AD, endpoints, and network tools to identify patterns that signified lateral movement across systems.
Each of these tools can signal lateral movement involving the legitimate credentials of the victim, or while using legitimate tools associated with "living-off-the-land."
3. Look for Privilege Escalation Attempts
Privilege escalation is a common precursor to lateral movement. Things to look for:
- Sudden implementation of admin-level role assignments
- Service accounts gaining access to new applications
- Dumping LSASS memory or retrieving Kerberos tickets
- Unusual PowerShell or WMI activity
A spike in privileged access and/or sudden movement to new privileges is a red flag that must be investigated for a legitimate process or an attacker attempting to expand their foothold.
4. Correlate Lateral Authentication Attempts
Follow authentication patterns to detect credential abuse:
- Several bad logins followed by a single successful login
- Logins from new or abnormal IPs
- Use of the same credentials on different machines in succession
- Service account logins outside of their normal login patterns
When authentication logs are correlated across endpoints, Active Directory, and cloud apps, the paths for lateral movement become much more apparent.
How to Prevent Lateral Movement in Your Network
Preventing lateral movement is ultimately about reducing the number of pathways that can be exploited after an initial compromise. Two of the more effective methods are network segmentation and least privilege access, which both create structural barriers and limit how far an attacker can move, even if they have breached one system. If paired with identity-centric controls like MFA, credential hygiene, and continuous access review, organisations can contain the threat before it escalates to ransomware or a significant data breach.
1. Implement Least Privilege and MFA
Limiting every user, service account, and machine identity to just the fully needed permissions limits each user, service, and identity's lateral movement options.
- Using least privilege makes it very difficult for a compromised account to access any additional systems or sensitive data.
- Role-based and attribute-based access can further restrict privileges based on department, device posture, location, and risk level.
- Multi-Factor Authentication (MFA) would be another level of validation to prevent the reuse of stolen passwords or hashes (especially in Pass-the-Hash scenarios).
- Conditional access rules would force re-validation for flagged actions and make unauthorised lateral movements more visible.
If privileges are well-scoped, it will be much more difficult for an attacker to get elevation, and without elevation, lateral movement is much less effective.
2. Network Segmentation & Zero Trust
Network segmentation divides your environment into smaller, isolated zones to prevent attackers from moving freely across your systems.
- Micro-segmentation limits east-west communication, such that even if one endpoint is compromised, it cannot talk to every server.
- Zero trust architecture operates under the “never trust, always verify” principle; every access request is authenticated and authorised continuously.
- Service isolation ensures sensitive assets (e.g., domain controllers, AD servers, production workloads) each have their own boundaries.
- Application-level segmentation ensures applications have tightly defined communication paths that are not unnecessarily interconnected when exploitation is occurring by the attacker.
Segmentation transforms the lateral movement process into a maze of barriers, forcing attackers to expose themselves either with abnormal traffic patterns or authentication attempts.
3. Regularly Audit and Rotate Credentials
Inadequate credential hygiene is one of the most frequent facilitators of lateral spread. Regular audits prevent hackers from reusing or cracking stale explanation codes.
- Password rotation will make stolen credentials meaningless after a certain time.
- Reviewing dormant, orphaned, or unnecessary accounts will eliminate hidden access points.
- Rotating service account credentials and keys will limit any long-term exploitation (which is most threatening with excessive privileges).
- Auditing privileged accounts ensures access is appropriate, bound to a specific time frame, and least privilege compliant.
- Strong password control polices, and NtLanm disabled (if possible), are an avenue to reduce the chances of a pass-the-hash or kerberoasting situation.
Regular credential rotation closes off many of the silent security gaps that attackers depend on.
4. Keep an Eye on Identity Logs (IGA Integration):
Identity logs provide a reliable indicator of anomalous access activity, which is key to the detection of lateral movement. Integrating identity governance (IGA) solutions increases visibility and control.
- IGA solutions such as Identity Confluence by Tech Prescient correlate identity changes, entitlements, and approvals to identify suspicious privilege escalations.
- Monitoring authentication patterns across applications and systems can help to identify odd login sequences and credential reuse.
- Access certification campaigns capture users who may have unnecessary privileges over time.
- Automated remediation workflows (e.g., session termination or temporary access suspension) can be utilised for disrupting an attack from getting further into the network.
- Cross-system log correlation (IGA + SIEM + EDR) offers end-to-end visibility from identity actions to endpoint actions.
With identity being the focal point of the detection, organisations provide themselves the opportunity to disrupt attack chains before lateral movement can reach critical assets.
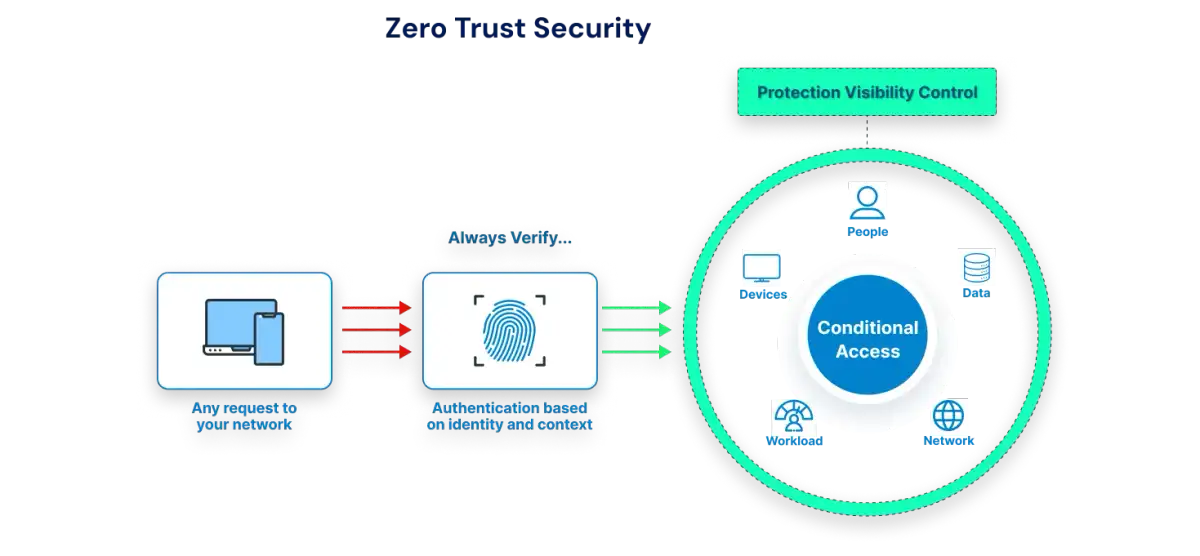
The Role of Identity Governance (IGA) in Stopping Lateral Movement
Identity Governance and Administration (IGA) greatly limits lateral movement by strictly ensuring users, service accounts, and machine identities have only the access they require, and nothing more. Because lateral movement often relies on excessive privileges, orphaned accounts, or unchecked access sprawl, a strong IGA program has decreased the number of pathways an attacker can employ once they compromise their target.
How IGA Collaborates with Stopping Lateral Movement:
1. Eliminates Over-Provisioned Access
IGA is typically based on the concept of least privilege and contains an ongoing review and refinement of entitlements. Over time, users typically collect an arbitrary amount of unnecessary permissions (often referred to as "privilege creep"), which are targets of opportunity during an attack. IGA functionality can help systematically reduce access and unused permissions, therefore reducing the attack surface area.
2. Strengthens Access Certifications
Regular certification campaigns enable managers and application owners to verify who should have access to what. This process usually reveals:
- Dormant or unused accounts
- Access based on excessive entitlement
- Risky combinations that violate Segregation of Duties(SoD)
Once we eradicate these weak points, we have reduced how far an attacker can move into your environment.
3. Detects Unusual Access Paths Through Correlation
The integration of IGA with IAM and security tools helps uncover suspicious behaviour, such as:
- A user engaging in activity outside of their role, e.g. accessing a highly privileged system.
- Privileged escalation that is inconsistent with past behaviour, or not matching historical patterns.
- Access changes are occurring at an unexpectedly high rate in Active Directory.
- The user attempts to access many different systems simultaneously over a short period of time.
Identity-level anomaly detection is critical because understanding lateral movement at the endpoint or network layer typically looks “normal”, but not at the identity layer.
4. Support a Zero Trust Strategy by Continuously Governing Entitlements
Zero Trust suggests we have to verify everything every time. IGA supports the governance layer to ensure entitlements are aligned to specific business needs so that access is:
- Business appropriate
- Time-bound
- Risk aware
- Continuously verified
This level of alignment will prevent an attacker from exploiting the granularity of entitlements that are either too long-lived or for which the access is no longer needed (east-west movement).
5. Automates Remediation to Break the Attack Chain
Modern IGA platforms can initiate automated workflows upon detecting suspicious identity changes, such as disabling an account, revoking a high-risk entitlement, or alerting your security teams. Organisations can thus respond before lateral movement results in an event that impacts critical business assets.
IGA + IAM = A Unified Defense
IAM manages access and authorisation, but IGA controls who should have access in the first place. Combined, the offer true visibility across identity lifecycles, and can work to identify abnormal access pathways that may show early attempts at lateral movement.
For deeper context on how governance complements identity access, check out IGA vs IAM explained.
Final Thoughts
Lateral movement is frequently the silent activator behind big cyberattacks. Most breaches are not catastrophic after an attacker gets in; they are catastrophic when the attacker can move laterally, escalate privileges, and access the target systems of value undetected. This is why preventing lateral movement is not just a best practice for security; it is a requirement for modern cyber resilience.
By improving identity governance, limiting excessive privileges, segmenting networks, and monitoring for abnormal behaviour, organisations can greatly limit an attacker’s ability to spread. Good security hygiene does not just make a breach hard; it makes a breach manageable, from being organisation-wide to isolated and contained.

Protect your critical assets by blocking lateral movement at the source. Experience IGA in action with Identity Confluence today.
Frequently Asked Questions (FAQs)
1. What is lateral movement in cybersecurity?
Lateral movement involves the movement of attackers throughout a network in order to gain access to more devices, accounts, or applications, after they have already gained a foothold on one system. Instead of attacking from the outside, they remain on the inside to expand their foothold, typically using stolen credentials to gain initial access and then access the better systems to further their attack.2. Why is lateral movement dangerous?
Lateral movement is dangerous because it allows attackers to blend into normal network activity to escalate privileges and identify valuable assets. They can move using the most stealthy methods possible so that the lateral movement goes entirely unnoticed until the organisation is already dealing with either a ransomware attack, theft of data, or total compromise of the domain or other serious compromise.3. How can organisations detect lateral movement?
Organisations are able to detect lateral movement using a combination of behavioural monitoring and high-quality telemetry. Combining telemetry and activities demonstrated with monitors, such as EDR, SIEM, and UEBA, will assist in flagging anomalies such as abnormal access attempts, patterns of privilege escalation, abnormal line of traffic going east-west, or all the attempts that lead to a certain service failure. If anomalies are correlated, they can provide early telemetry or visibility into suspicious activity occurring internally.4. What tools are used for lateral movement?
Attackers often use Mimikatz (credential dumping), PsExec and PowerShell (remote execution), and frameworks like Cobalt Strike (command-and-control and pivoting). Attackers exploit legitimate administrative functions to make harmful movement look normal.5. How do I prevent lateral movement?
Preventing lateral movement involves limiting unnecessary access and tightening identity controls. Following least privilege principles, enforcing MFA on all critical systems, segmenting networks, regularly rotating credentials, and conducting IGA-based access reviews assist in blocking attacker paths. Strong monitoring and Zero Trust principles will also help to limit movement.



