
What is Machine Identity Management (MIM)? Definition, Lifecycle & Security

Machine Identity Management (MIM) is the systematic process of governing and securing the digital credentials that machines use to authenticate themselves and communicate securely across your infrastructure. Think of it as identity management for your non-human workforce, the servers, APIs, containers, IoT devices, and cloud workloads that operate autonomously 24/7 without human intervention.
In modern enterprises, machines vastly outnumber humans. According to Gartner estimates, machine identities outnumber human identities by a ratio of 45 to 1. Unlike humans who log in with passwords or biometrics, machines authenticate through cryptographic keys and digital certificates. The stakes are different too: machines don't forget credentials, but mismanaged keys can sit unnoticed until they cause real damage. Machine credentials can exist for minutes or years, depending on their purpose. A cloud workload might exist for seconds, while a TLS certificate lasts for years. This mix makes tracking them difficult, and when credentials are compromised or expire unexpectedly, organizations face unauthorized access, breaches, and service outages.
Machine Identity Management transforms this vulnerability into a governed, auditable process. It prevents breaches caused by compromised credentials, eliminates costly outages from expired certificates, and ensures continuous compliance across Zero Trust architectures. In this guide, you'll learn what machine identities are, why they matter for cybersecurity, how to manage their complete lifecycle, and practical steps to strengthen your organization's machine identity security posture.
Key Takeaways:
- Machine identities are digital credentials that authenticate non-human entities like servers, APIs, containers, and IoT devices across your infrastructure
- Organizations now manage 45 times more machine identities than human identities, creating massive scale and complexity challenges
- Unmanaged machine identities lead to costly certificate-related outages, data breaches through compromised credentials, and compliance failures
- Effective Machine Identity Management requires automated discovery, lifecycle management, policy enforcement, and continuous monitoring
- Integrating MIM with Identity Governance & Administration creates unified security where both human and non-human identities receive consistent governance
What Is Machine Identity Management (MIM)?
Machine Identity Management (MIM) is how organizations assign, track, and control digital credentials for non-human entities: servers, APIs, containers, IoT devices, and cloud workloads. It ensures machines can authenticate, access the right resources, and nothing more.
Think of it like employee identity management, but for your digital infrastructure. HR manages employee credentials from hire to exit. MIM does the same for machine credentials, from creation through revocation. The difference? Machines operate at a massive scale and authenticate thousands of times per second, and one misconfigured credential can trigger organization-wide failures.
The Core Challenge
MIM validates access privileges to maintain data, application, and endpoint security. While IT and DevOps teams handle this routinely, manual approaches hit hard limits. Spreadsheets work for 100 certificates. They break at 10,000. Machines don't wait for approval workflows or help desk tickets. They need instant, automated credential management.
Why Traditional Approaches Fail
Many organizations still track certificates using spreadsheets, rely on calendar reminders for renewals, or have no centralized visibility into which machines possess which credentials. This manual approach worked when enterprises managed hundreds of certificates. Today, with cloud-native architectures, microservices, and IoT deployments, organizations manage tens of thousands to millions of machine identities. Research indicates 71% of IT professionals believe their organization does not know exactly how many keys and certificates it has, creating dangerous blind spots where expired, orphaned, or compromised credentials lurk undetected.
The Five Critical Challenges MIM Addresses
1. Discovery and Inventory
You cannot protect what you cannot see. Machine identities exist across on-premise data centres, multi-cloud environments, container orchestration platforms, CI/CD pipelines, and edge devices. Every API endpoint, database connection, microservice communication, and IoT sensor requires credentials. Without automated discovery, shadow credentials proliferate. Developers issue certificates for testing that reach production. Infrastructure-as-code templates generate API keys stored only in deployment logs. Service accounts remain active long after the applications they served are decommissioned.
Example: A financial services company discovered through automated scanning that they had 847 active API keys accessing their payment processing system, but could only account for 203 in their official inventory. The remaining 644 orphaned credentials represented potential backdoors for attackers.
2. Lifecycle Automation
Managing credentials from initial provisioning through renewal and eventual revocation demands automation. Consider the mathematics: an organization with 10,000 certificates operating on 90-day lifespans must successfully rotate 111 certificates every single day. Miss one rotation, and a critical service goes offline. Manual processes, approval workflows, and change management procedures – these human-speed activities cannot keep pace with machine-scale operations.
Example: A major e-commerce platform experienced a complete checkout system outage during Black Friday because an SSL certificate had expired. The certificate was tracked in a spreadsheet. but the renewal reminder email went to an employee who had left the company three months earlier. The four-hour outage cost $2.3 million in lost revenue.
3. Policy Enforcement
Who can request credentials? Which cryptographic standards are mandatory? When should the automatic revocation trigger? How long should certificates remain valid? Policy enforcement ensures these questions have consistent answers across distributed teams and hybrid environments. Without centralized policies, each team implements its own standards, or worse, circumvents security requirements to meet deployment deadlines.
Example: A healthcare organization's security policy mandated RSA-2048 minimum key length, but automated scans revealed 23% of their internal certificates used deprecated RSA-1024 keys because developers used outdated certificate request templates. This policy violation risked HIPAA compliance.
4. Access Governance
Not all machine identities require equal privileges. An API gateway needs different access than a logging service. A production database connector requires stricter controls than a development environment script. Applying least-privilege principles to machine identities means continuously validating that each credential possesses only the minimum permissions necessary for its function. This requires understanding what each machine does, what data it accesses, and whether those entitlements remain appropriate as applications evolve.
Example: During a security audit, a SaaS company discovered its customer data export service account had full database administrator privileges, including the ability to drop tables and modify schemas. The service only needed read access to three specific tables. This overprivileged identity violated the segregation of duties and increased the potential damage if compromised.
5. Continuous Monitoring
Machine identities are constantly authenticated. APIs make thousands of calls per minute. Microservices exchange credentials with every interaction. IoT devices transmit telemetry continuously. Monitoring this activity in real time enables detection of anomalous behaviour that signals compromise: unusual access patterns, authentication from unexpected locations, privilege escalation attempts, or dormant credentials suddenly becoming active.
Example: A manufacturing company's security operations centre detected an IoT device certificate, normally used to transmit temperature sensor data every 30 minutes, suddenly making 500 authentication attempts per second at 3 AM. Investigation revealed the device had been compromised and was being used to scan for vulnerabilities across the internal network.
The Strategic Imperative
The urgency of Machine Identity Management stems from infrastructure evolution. Machine identities are growing at twice the rate of human identities, driven by cloud migration, microservices architectures, containerization, DevOps automation, and IoT proliferation. Organizations implementing Identity Governance & Administration must extend governance to machine identities to create unified security where both human and non-human identities receive consistent oversight, audit trails, and policy-driven controls. This convergence is essential for achieving Zero Trust architectures and maintaining regulatory compliance across frameworks like GDPR, HIPAA, SOX, and PCI DSS.
Learn more about IGA fundamentals ->
How Machine Identities Work
Machine identities let systems talk to each other securely using digital keys that prove they're legitimate. No passwords needed, no human involvement. To manage these identities well, you need to understand how they build trust, grant access, and keep data safe.
Authentication Through Digital Credentials
Authentication answers one question: "Is this machine really who it claims to be?" For machines, this happens through digital certificates and cryptographic keys, not passwords.
Think of a digital certificate as a machine's passport. These X.509 certificates contain three parts: a public key (shared openly), identity information (hostname, organization, purpose), and a digital signature from a trusted Certificate Authority that confirms it's legitimate.
How Machine Authentication Works
When a browser connects to a website, when a microservice calls a database, or when an IoT device sends data to the cloud, the same process happens:
- Step 1: The requesting machine shows its digital certificate with its public key and identity
- Step 2: The receiving machine checks if a trusted Certificate Authority signed it and if it's still valid
- Step 3: The receiver encrypts random data using the public key and sends it back
- Step 4: Only the real holder of the matching private key can decrypt this data
- Step 5: Both systems create temporary session keys for encrypted communication
The beauty here: the public key encrypts data that only the private key can decrypt. The private key never travels across networks, never sits in config files, and never leaves its protected space. This removes the main weakness of passwords that can be intercepted or stolen.
Real-World Example
When you access your bank's website over HTTPS, your browser gets the bank's SSL/TLS certificate. It checks that a trusted Certificate Authority like DigiCert or Let's Encrypt signed it, confirms it hasn't expired, and verifies it wasn't revoked. Only after this check passes does your browser show the padlock icon and send your login credentials over the encrypted channel. This same process happens billions of times daily across API calls, microservice communications, and IoT data transmission.
Types of Machine Credentials
Different scenarios require different credential types:
- TLS/SSL certificates secure HTTPS connections between web services, APIs, and client applications
- Code signing certificates prove software authenticity, ensuring executables haven't been tampered with since the developer signed them
- SSH keys enable secure remote administration of servers and infrastructure without password transmission
- Device certificates authenticate IoT sensors, industrial equipment, and embedded systems connecting to networks
- Client certificates provide mutual authentication, where both parties prove their identity before exchanging data
The complexity is escalating rapidly. By 2029, major browsers will enforce 47-day certificate lifespans, requiring organizations to manage certificate rotations 9 times more frequently than the current 90-day standards. Manual tracking becomes mathematically impossible at this velocity, making automation non-negotiable.
Authorization and Access Control for Machines
Once a machine proves its identity, the next question is: what can it actually do? Authorization sets these boundaries.
Role-Based Access Control (RBAC)
RBAC gives machines permissions based on their job. A backup service gets read-only access. An application server gets both read and write access. A monitoring tool only gets access to logs.
Example: Your API gateway machine has a certificate that lets it route traffic and log requests. Your database replication service has a different certificate that only allows copying data between servers. Each machine can only do its specific job, nothing more.
Attribute-Based Access Control (ABAC)
ABAC adds extra checks before allowing access. It looks at things like: where is the request coming from? What time is it? How strong is the certificate?
Example: A machine might have valid credentials, but ABAC blocks access if it's connecting from outside your production network or using an old encryption standard. This prevents compromised development machines from accessing production data, even if they somehow get valid certificates.
Both approaches help manage machine identities by ensuring credentials don't grant unlimited access across your infrastructure.
Machine Identity Management Challenges
Managing machine identities comes with several challenges that organizations must address to maintain security and compliance.
- Ephemeral Workloads and Short-Lived Credentials
Traditional authorization assumes machines stay relatively stable. Containers and serverless functions break this assumption. A Kubernetes cluster might create 500 new containers during a traffic spike, each needing unique credentials and permissions, then shut them down 10 minutes later. Static permission assignments can't keep up with this speed.
The answer is just-in-time access. Credentials are created on demand with minimal permissions and automatic expiration. When a container starts, it gets a short-lived certificate (typically 1-24 hours) limited to its specific task. The certificate expires when the container stops, removing the risk of abandoned credentials.
Example: A video streaming platform uses ephemeral workloads to encode videos. When someone uploads a video, the system spawns a container and gives it a 2-hour certificate with write access to one storage bucket and read access to that specific file. The container processes the video and shuts down. The certificate expires automatically. If an attacker compromises the container during encoding, they only access that single video file for the remaining certificate time.
-
Visibility Gaps in Serverless and Automation Technologies like Robotic Process Automation and serverless platforms (AWS Lambda, Azure Functions) improve efficiency but create visibility challenges. These platforms embed security within functions and offer monitoring, but often lack clear answers to: who manages these functions? Who can modify or update them? What access do they actually have?
Organizations need continuous visibility into how these machine identities access data and systems, especially when automation operates without direct human oversight. -
API Access and Governance Concerns API gateways control access through authentication methods like MFA, SSO, and role-based rules. But these controls don't extend to the people who build and maintain the APIs themselves.
Critical questions often go unanswered:
- Who can access and use specific machine identities?
- How are access requests monitored and controlled?
- Who can modify or delete machine identities?
- Who owns each machine identity?
- How is ownership transferred securely?
- What privileged access are these identities using?
- How do we document everything for compliance?
The Identity-Centric Solution Organizations need to treat machine identities like human identities, with proper lifecycle management, clear ownership, and continuous governance. This approach provides the visibility and control needed to reduce unauthorized access and prevent breaches, while accounting for the unique characteristics of machines that operate at scale and speed.
Encryption and Data Protection
Authentication and authorization establish who can access what. Encryption makes sure that even if someone intercepts the communication, they can't read or tamper with it.
-
How Encryption Works for Machines
Machines use a multi-step process to secure their communications:
First, they generate key pairs using algorithms like RSA-2048 or ECDSA. The private key stays protected in a Hardware Security Module or secure vault. Many breaches happen because developers accidentally save private keys in code repositories or config files.
Next, machines exchange public keys safely. Certificate authorities solve this by digitally signing certificates, creating a trust chain from widely trusted root authorities down to individual machine certificates.
For actual data transmission, machines use a hybrid approach. They use asymmetric encryption (public/private keys) to establish trust and create a temporary symmetric key. Then they use that faster symmetric key for bulk data encryption during the session.
Finally, digital signatures ensure data hasn't been altered. The sender creates a hash of the message and encrypts it with their private key. The receiver decrypts it, recalculates the hash, and verifies that they match. -
Looking Ahead: Quantum Computing
Current encryption (RSA, ECDSA) relies on math problems that today's computers can't solve. Quantum computers threaten to break these algorithms. Organizations need to inventory their cryptographic systems now and prepare to migrate to quantum-resistant credentials when standards are ready.
Why Machine Identities Are Crucial for Cybersecurity
Machine identities authenticate every API call, database connection, and system interaction that keeps businesses running. Implementing proper Machine Identity Management transforms security from reactive firefighting into proactive protection.
Enhanced Security
MIM prevents unauthorized access at the foundation level. Every machine must prove its legitimacy before connecting to anything. This verification layer stops attackers who've stolen credentials from moving laterally through your network.
Without MIM, a mid-sized company with 1,000 employees manages roughly 45,000 machine identities with no central visibility. Research shows 75% of these credentials never get rotated. Stolen API keys from old code repositories stay active for years because nobody tracked them. Machine credentials don't lock out after failed attempts, don't expire when employees leave, and operate silently without triggering alerts designed for human behavior.
MIM closes these gaps by enforcing authentication for every machine, every time.
Operational Efficiency
Manual certificate management is a productivity drain. Teams spend hours tracking renewal dates, coordinating updates across systems, and scrambling when certificates expire unexpectedly.
Automation handles certificate issuance, renewal, and revocation without manual oversight. IT downtime costs an average of $5,600 per minute. The Microsoft Teams outage from one expired certificate affected millions globally—not from a sophisticated attack, just an overlooked renewal. Airlines have lost tens of millions from certificate-related outages. E-commerce sites go dark during peak shopping. These aren't rare events; 67% of organizations report certificate-related outages monthly.
MIM eliminates these preventable disruptions. Certificates renew automatically weeks before expiration. Expired credentials get flagged and removed. Your team stops firefighting and starts building.
Compliance Requirements
Regulatory frameworks like PCI-DSS, GDPR, HIPAA, SOX, ISO 27001, and NIST standards now mandate explicit governance over machine identities. Auditors demand:
- Complete credential inventory with clear ownership
- Automated lifecycle management with documented processes
- Regular access reviews where owners confirm permissions remain appropriate
- Audit trails tracking creation, access, and revocation
MIM provides consistent identity governance that demonstrates compliance. Organizations using spreadsheets can't produce this evidence efficiently. Failed audits result in fines, mandatory remediation projects consuming months of resources, and reputational damage as regulations tighten.
Proper machine identity management turns compliance from a burden into a competitive advantage.
Machine Identity vs. Human Identity
Machine and human identities both fall under identity management, but they need different approaches because machines and humans operate differently.
Key Differences
| Dimension | Human Identity | Machine Identity |
|---|---|---|
| Authentication | Passwords, MFA, biometrics | Certificates, cryptographic keys, API tokens |
| Lifespan | Years (employment duration) | Seconds to years (containers to servers) |
| Rotation | 30-90 days (passwords) | 30-90 days (automated) |
| Access Pattern | Interactive, business hours | Automated, continuous, 24/7 |
| Privileges | Gradual with approvals | Often elevated from the start |
| Recovery | Self-service reset, help desk | Automated reissuance |
| Scale | Thousands (1:1 with employees) | Tens of thousands to millions (45:1 ratio) |
Why Standard IAM Tools Don't Work
Traditional identity tools assume users log in during business hours, can answer security questions, and call the help desk when locked out. Machines break all these assumptions.
A container platform creating 200 instances per minute can't call IT for each certificate. An IoT sensor can't solve a CAPTCHA. An API making 10,000 requests per second can't pause for MFA approval.
A SaaS company tried using its employee IAM system for machine credentials. When a critical API certificate needed renewal, the automated process failed because it required interactive MFA. By the time teams manually approved it, the API had been offline for 3 hours, causing failures across 47 customers.
Different Lifecycles:
Human identities last for years, tied to employment. Machine identities span an enormous range. A production server might have a one-year certificate. A serverless function might get credentials for 15 minutes. A container might receive a 24-hour certificate that refreshes automatically.
Privilege Challenges:
Employees start with minimal access and gain permissions gradually. Machines often need elevated privileges from day one. A backup service needs to read every file. A monitoring agent needs to check every system. An orchestration platform needs to start and stop workloads.
The challenge is ensuring each machine has only the minimum permissions it needs, no more. During audits, organizations often discover service accounts with excessive privileges because developers used admin credentials during testing and never restricted them for production.
The Convergence Point:
The line between human and machine identities is blurring. When a developer writes code that runs as a serverless function, whose identity is it? When an AI agent makes autonomous decisions, how should it authenticate?
Organizations need unified governance frameworks that handle the full spectrum, from pure human logins to pure machine operations to hybrid scenarios where automated systems act on behalf of humans.
TechPrescient's Identity Confluence treats machine identities as first-class entities within comprehensive governance workflows, applying consistent policies while respecting their unique characteristics.
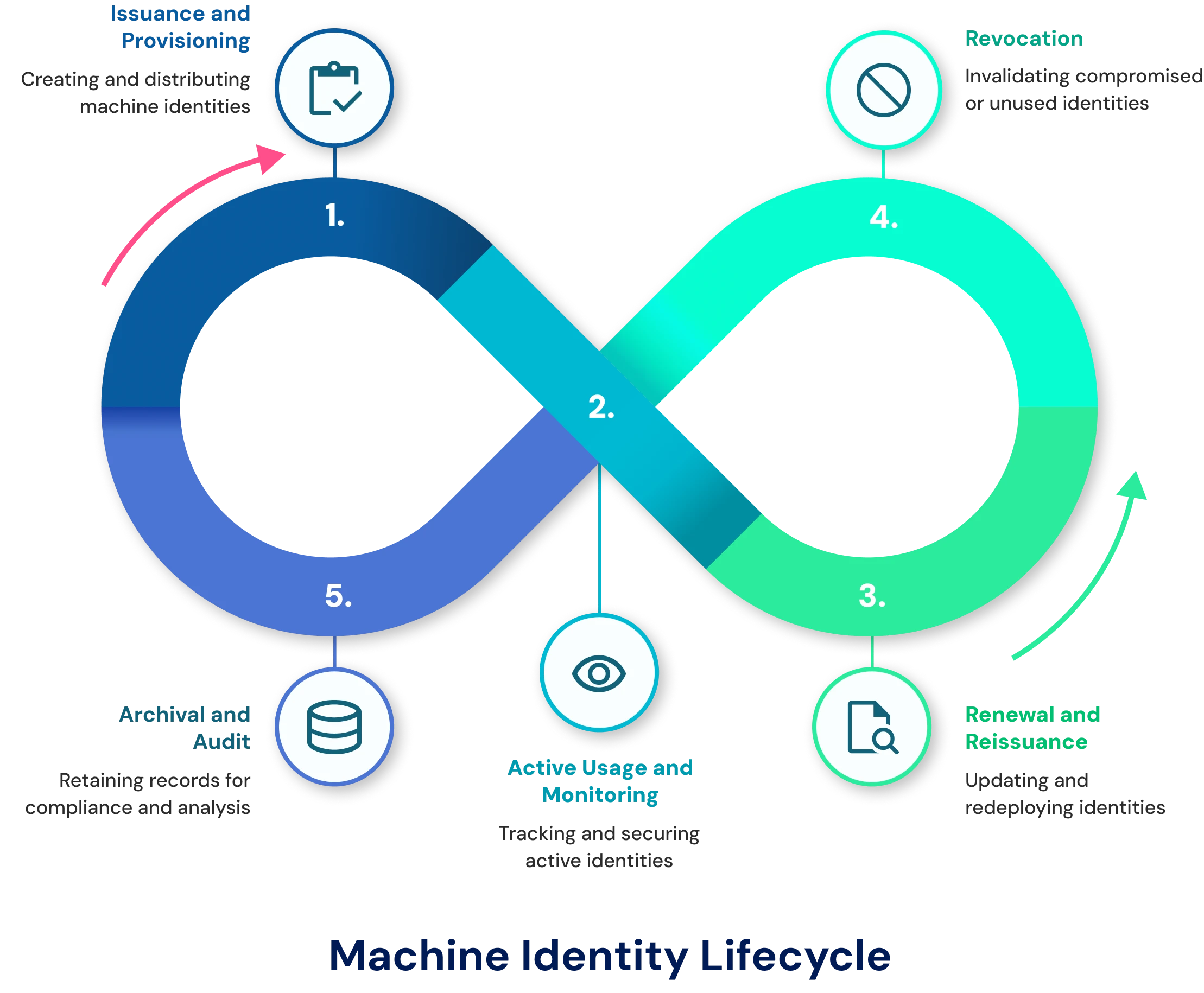
The Machine Identity Lifecycle
Every machine identity moves through stages from creation to retirement. Mismanaging any phase creates security vulnerabilities or operational risks.
Think of it like employee lifecycle management, but at machine speed and scale. Just as HR onboards employees, manages role changes, and offboards departures, machine identity management handles provisioning, monitoring, rotating, and revoking credentials.
Phase 1: Issuance and Provisioning
The lifecycle starts when a new credential is needed. A developer deploys an API, DevOps provisions infrastructure, or an IoT device activates. A Certificate Authority validates the request, checks it meets organizational policies, generates the credential, and records ownership information.
Best practices include automated generation using approved templates, HSM protection where keys never leave secure hardware, metadata tagging for ownership and purpose, and infrastructure-as-code integration for programmatic requests.
Phase 2: Active Use and Monitoring
Once deployed, machines constantly authenticate. This phase requires continuous monitoring to detect misuse while tracking credential health.
Effective monitoring includes expiration dashboards with colour-coded risk levels, usage pattern baselines that alert on deviations, compliance scanning against cryptographic policies, and dormant credential detection for credentials unused over 90 days.
A financial company's monitoring system detected a certificate suddenly accessing production databases at 2 AM on Sunday, when it normally only accessed test databases during business hours. Investigation revealed a compromised laptop, and rapid response contained the breach before data theft.
Phase 3: Renewal and Rotation
Renewal starts 30-45 days before expiration, allowing time for approvals and testing. Automated platforms request new certificates, verify they meet current standards, and deploy them without service interruption.
Rotation is proactive replacement before expiration or compromise. With 10,000 certificates on 90-day lifespans, organizations must rotate 111 certificates daily. At 30-day cycles, that's 333 daily rotations. Manual processes can't sustain this pace.
Phase 4: Revocation
Revocation immediately invalidates a credential, typically triggered by security events (suspected compromise, credentials in public repositories), lifecycle events (decommissioning servers, retiring applications), or policy violations (weak algorithms, excessive validity periods).
Certificate Revocation Lists (CRLs) provide traditional revocation but have a lag time between revocation and client updates. Online Certificate Status Protocol (OCSP) enables real-time checking but depends on responder availability.
Phase 5: Archival and Audit
Even after revocation, records must be retained for compliance and forensics. Regulations often mandate 7-year retention of lifecycle events, approvals, and access decisions.
During a breach investigation, one organization's certificate platform provided complete audit trails showing when attackers first gained access 97 days earlier and which systems they compromised. Without these trails, investigation would have required weeks of manual log analysis.
Rotation Best Practices
Effective rotation uses overlapping validity periods for zero-downtime transitions. Generate new certificates 5-15 days before old ones expire. Services gradually migrate while legacy systems complete in-flight work. Only after confirming a successful transition do you revoke old credentials.
Automated deployment distributes renewed credentials to all consuming systems and initiates graceful restarts when needed. Verification before revocation confirms services can authenticate successfully before revoking old credentials.
Renewal Alerts
Every overlooked expiration can cause organization-wide failures. Multi-tier notifications create progressively urgent reminders:
- 60 days out - Initial notice for planning
- 30 days out - Escalated to owners and managers
- 15 days out - High-priority with daily reminders
- 7 days out - Critical status with executive escalation
- 24 hours out - Crisis mode with hourly alerts
The challenge is alert fatigue. With thousands of certificates, organizations might get hundreds of weekly reminders. Effective systems use role-based routing to appropriate owners and provide one-click renewal links rather than just warnings.
Common Threats and Risks
Unmanaged machine identities create attack vectors that adversaries actively exploit.
1. Certificate Expiration
According to recent reports, 67% of organizations experience certificate-related outages monthly, with 45% experiencing them weekly. When critical certificates expire, encrypted connections fail instantly. Web services become unreachable, APIs reject requests, and microservices can't communicate.
Expired intermediate Certificate Authorities propagate to all certificates they issued, creating mass failures where thousands of identities simultaneously lose validation.
2. Shadow Credentials
Developer credentials issued for testing reach production and persist indefinitely. Infrastructure-as-code generates credentials stored only in deployment logs. Service accounts remain active after their applications are decommissioned. Former employees' access keys work months after departure because nobody connected them to that person.
A financial company discovered 847 active API keys accessing their banking platform, but could only account for 203. The remaining 644 represented unknown risk from former contractors, compromised accounts, or planted backdoors. Revoking unknown keys required three weeks of testing.
3. Compromised Keys
Unlike passwords that might trigger lockouts, compromised machine credentials provide persistent, unobstructed access. Common compromise vectors include hard-coded credentials in source code, unprotected config files, insider threats, and supply chain compromises.
Research shows that over 12.8 million secrets were discovered in public repositories in 2024. Automated bots find and weaponize them within minutes.
4. Weak Cryptography
Legacy systems often use deprecated algorithms like SHA-1, MD5, or RSA-1024 that modern tools can break. Industrial equipment might use 1990s-era standards that no longer provide security but can't be upgraded without replacing expensive operational technology.
5. Over-Privileged Access
Research shows 80% of developers possess more privileges than necessary. Machine identities get broad permissions during development for convenience, with teams intending to restrict them later but never revisiting those decisions.
Over-privileged identities enable lateral movement, where compromising one service lets attackers pivot across infrastructure. They increase the scope of harm from any single compromised credential.
Best Practices for Machine Identity Management
Effective machine identity management requires strategic planning and commitment to automation.
1. Automate Certificate Lifecycle Management
Spreadsheets can't keep up. When you're managing hundreds or thousands of certificates across different systems, manual tracking guarantees something will slip through the cracks.
Why Automation Matters
People forget. Emails get missed. Reminders go to employees who've left. These aren't rare mistakes; they're inevitable when humans manage machine-scale operations. Automation removes the human error factor entirely.
What Automation Does
Automated platforms handle the tedious work: tracking every certificate across your infrastructure, sending renewal requests before expiration, deploying updated certificates to the right systems, and flagging credentials that shouldn't exist anymore.
The Real Benefit
You stop playing catch-up. Instead of scrambling when a certificate expires at 3 AM on a weekend, the system handles renewals weeks in advance. Your team focuses on strategy, not babysitting spreadsheets.
Organizations that automate certificate management typically discover they have far more certificates than they thought; including some that expired months ago but went unnoticed. That visibility alone prevents future outages.
2. Use Strong Cryptographic Standards
Weak encryption is one of the easiest ways attackers breach systems. If your machine identities use outdated encryption, it's like locking your front door with a padlock anyone can pick.
Why Encryption Strength Matters
Modern computing power can crack older encryption methods in hours or days. What was secure a decade ago isn't secure now. Attackers specifically target organizations still using weak encryption because it's the path of least resistance.
Keep Standards Current
Use industry-recommended encryption standards for all machine credentials. Avoid deprecated methods that security experts have flagged as vulnerable. Your Certificate Authority or security team can guide you on current best practices.
Hardware Security Modules (HSMs)
HSMs store private keys in tamper-resistant hardware. Even if attackers compromise your servers, they can't extract keys from HSMs. This adds a critical layer of protection for high-value credentials.
Prepare for Future Threats
Quantum computing will eventually break current encryption methods. Start planning now by inventorying your cryptographic systems and ensuring you can swap algorithms when quantum-resistant standards become available.
3. Continuous Monitoring
Real-time expiration tracking prevents surprises. Executive dashboards aggregate risks across business units.
Anomaly detection uses machine learning to establish baselines and alert on deviations, unusual access times, unexpected locations, privilege escalation, or dormant credentials suddenly activating.
Compliance scanning continuously validates against policies, identifying deprecated algorithms, excessive validity periods, or inadequate key lengths.
Privilege monitoring enforces least-privilege through quarterly access certifications where business owners attest that service accounts retain appropriate permissions.
4. Rotate and Revoke Credentials
Machine credentials need regular updates, just like passwords. The difference is the stakes are higher; compromised API keys or certificates don't trigger account lockouts and can stay active for years if unmanaged.
Why Rotation Matters
Stolen credentials lose value when they expire quickly. If an attacker gets a certificate that rotates every 30 days, their access window is limited. Static credentials that never change give attackers unlimited time.
When to Revoke
Revoke immediately when credentials are compromised or found in public repositories, machines are decommissioned, or employees with access leave the organization. The longer compromised credentials stay active, the more damage they can cause.
Organizations that automate rotation and revocation cut their security incident response time by 80% and eliminate most credential-related breaches before they happen.
Machine Identity Management and Zero Trust
Zero Trust requires continuous verification of all identities before granting access, eliminating trust based on network location. Machine identities enable this because machines execute most authentication decisions in modern infrastructure.
Traditional security created "trusted zones" inside firewalls where systems communicated freely. Zero Trust requires every connection, microservice-to-database, API-to-API, container-to-storage, to present valid credentials regardless of location.
Machine identities outnumber humans 45:1 with access to sensitive systems. Without proper governance, they become the largest undefended attack surface. Organizations implementing Zero Trust for humans while ignoring machines secure 2% of identities and ignore 98%.
Continuous Verification
Service mesh architectures like Istio and Linkerd implement Zero Trust by issuing unique certificates to every service with short lifespans (often 24 hours), enforcing mutual TLS where both sides authenticate, automatically rotating certificates, and applying policy-based authorization defining which services can communicate.
This prevents lateral movement. Compromising one microservice doesn't enable impersonating others without their distinct private keys.
Policy-Driven Access
Zero Trust extends to all machine types: service accounts, API gateways, CI/CD pipelines, and IoT devices. Each receives just-in-time access with minimum permissions that expire after task completion.
IGA Integration
Comprehensive Zero Trust requires extending identity governance to machines. This includes unified policy management, consistent certification workflows, centralized audit trails, and automated remediation.
TechPrescient's Identity Confluence bridges IGA and MIM, treating non-human identities as first-class entities within governance workflows. This ensures organizations don't create silos where human identities receive oversight while machines operate ungoverned.
Multi-Cloud Complexity
Research shows 80% of organizations use three or more cloud providers, each with distinct identity models. AWS IAM roles, Azure Managed Identities, Google Service Accounts, and SaaS API keys create credential sprawl requiring unified visibility and enforcement.
Learn how IGA and IAM converge in Zero Trust. Read: IGA vs IAM, What's the Difference?
Tools and Vendors for Machine Identity Management
Machine Identity Management platforms automate credential discovery, lifecycle management, policy enforcement, and compliance reporting.
TechPrescient - Identity Confluence
Identity Confluence delivers unified IGA plus MIM governance, treating machine identities as first-class entities with the same rigour as human users.
Key capabilities:
- Unified governance for humans and machines with consistent policies
- Automated lifecycle with joiner-mover-leaver workflows
- 50+ pre-built integrations
- AI-powered risk insights with ML anomaly detection
- Hybrid deployment options
- Continuous compliance with automated certifications
Learn more about -> Identity Confluence
Evaluation Criteria
| Capability | Critical Question |
|---|---|
| Discovery | Automatic discovery across on-premise, cloud, containers? |
| Automation | End-to-end lifecycle with minimal human intervention? |
| Integration | Native connectors to CAs, clouds, secrets managers? |
| Policy | Centralized policies enforcing compliance? |
| Scale | Handles thousands to millions without degradation? |
| Reporting | Pre-built compliance reports for SOX, PCI DSS, GDPR, HIPAA? |
The Future of Machine Identities in the AI Era
The AI era introduces autonomous agents as a new class of machine identities requiring persistent credentials, dynamic privileges, and continuous monitoring at an unprecedented scale.
AI-powered virtual employees will execute tasks and make decisions without human checkpoints, operating independently with static credentials. These differ fundamentally: they're persistent with memory retained across sessions, they make autonomous decisions based on trained models, and they have dynamic privilege requirements needing diverse data access.
- Compromised AI agent credentials don't just leak data. Agents can autonomously exfiltrate information, create backdoors, or manipulate processes at machine speed.
- Next-generation platforms will use AI/ML for predictive renewal, anomaly detection with behavioural baselines, automated remediation revoking high-risk credentials, and intelligent access recommendations.
- The IoT explosion continues, with 41.6 billion connected devices expected by 2025. Edge environments introduce challenges like intermittent connectivity, resource constraints, physical tampering risks, and heterogeneous ecosystems.
- Organizations must also prepare for post-quantum cryptography, replacing potentially hundreds of thousands of identities with quantum-resistant credentials as standards emerge.
TechPrescient's Identity Confluence pioneers this convergence, positioning organizations to securely navigate the AI-driven future.
Final Thoughts
Machine Identity Management has evolved from a technical concern into a strategic imperative for Zero Trust security, regulatory compliance, and operational resilience.
The path forward requires three commitments:
- Unified identity governance - Breaking silos between human IAM and machine identity management for comprehensive visibility and consistent policies
- Automation-first operations - Eliminating manual tracking for automated discovery, lifecycle management, and policy-driven enforcement that scales with infrastructure
- Continuous adaptation - Building crypto-agile systems that respond to threats, including post-quantum cryptography and AI-driven security
Organizations implementing robust machine identity management transform identity governance from reactive risk mitigation into proactive enablers of secure digital transformation.
Transform your identity security with TechPrescient's Identity Confluence to see unified human and machine identity governance.
Frequently Asked Questions (FAQs)
1. What is a machine identity?
A machine identity is a digital credential such as a certificate, cryptographic key, API token, or SSH key that verifies a machine's authenticity and enables secure communication with other systems.2. What's the difference between machine and non-human identity?
'Non-human identity' can refer to identities used by services or applications to interact with cloud resources, while machine identity specifically uses cryptographic credentials to authenticate devices. These terms are increasingly used interchangeably in cloud-native environments.3. Why is Machine Identity Management important?
MIM prevents breaches, automates trust, and supports Zero Trust frameworks. Without proper governance, enterprises face certificate-related outages, data breaches through compromised credentials, and compliance failures.4. How many machine identities does a typical enterprise have?
Machines outnumber humans 45 to 1, according to Gartner estimates. The average company manages upwards of 83,000 digital certificates, with total machine identities often reaching hundreds of thousands when including API keys, service accounts, and SSH keys.5. How can companies secure machine identities?
Through automated lifecycle management, monitoring, and PKI-based policy enforcement. Best practices include Certificate Lifecycle Management platforms, strong cryptographic standards, HSMs for key protection, least-privilege access controls, continuous monitoring with anomaly detection, and extending IGA frameworks to cover machine identities.



