Non-Human Identity Lifecycle Management: Full Framework

Non-human identity lifecycle management involves discovering, securing, and automating the entire lifecycle of digital identities used by machines, like APIs, bots, workloads, and service accounts, rather than by humans. It ensures these identities are provisioned with the right access, their credentials are stored and rotated securely, their activity is continuously monitored, and they are properly decommissioned when no longer needed. Proper lifecycle management reduces security risks, prevents identity sprawl, and helps maintain compliance in increasingly automated and interconnected cloud environments.
As businesses increase their use of cloud services and automate processes, non-human identities (NHIs) such as APIs, bots, workloads, service accounts, and IoT devices have proliferated. In fact, research estimates that machine identities now outnumber human identities by more than >50:1 across large enterprises. However, most businesses are still managing these credentials manually, leading to unmonitored accounts, hardcoded keys, and enormous security gaps.
This blog will explore the non-human identity lifecycle framework and how automation, governance and Zero Trust principles may help organizations regain control over these powerful, yet invisible, identities.
Key Takeaways
- As organizations adopt cloud-native models and automation, the growth of non-human identities outnumbers human users.
- The challenge isn't just knowing how to manage them, but what exists, who owns it, and who can access it.
- When organizations lack visibility and governance over their lifecycle, NHI become a blind spot for attackers.
- Effective NHI management necessitates end-to-end visibility and management, from secure creation and rotation to monitoring and decommissioning.
- Tools such as CIEM and modern IGA provide automation and continuous monitoring to manage this scale securely.
- In the near future, the governance of non-human identities will be transformed through AI-enabled detection and continuous evaluation of identity access.
What is a Non-Human Identity?
Non-human identities (NHI) are credentials that are used by machines, applications, or software to gain access to systems, data, and services. These may include, but are not limited to, application programming interface (API) keys, service accounts, automation scripts, containers, serverless workloads, and other machine identities.
NHIs do not log in with a username and password or biometric scans as human users do. NHIs typically work behind the scenes to enable communication between machines, execute workflows, and authenticate across environments. NHIs are crucial to operations in the cloud, DevOps pipelines, third-party integrations, and infrastructure automation.
Common Examples of Non-Human Identities (NHIs):
-
Service Accounts: Utilized by applications, automation scripts or infrastructure, Service Accounts are used to access databases, systems or APIs.
-
API Keys and Tokens: API Keys and Tokens allow for programmatic access between services or systems, and typically will use credentials inside the scripts or keyed-in code.
-
Cloud and Workload Identities: Identities for Cloud and Workload are established by containers, serverless functions, or virtual machines to authenticate and facilitate communications with other systems.
-
System and OS Accounts: System and OS Accounts are default basic accounts that enable services, processes, or administrative tasks to function at the operating system level.
-
Application and Integration Accounts: Application and Integration Accounts synchronise the interaction and flow of applications and services either internally or externally via a variety of connected trusts, including OAuth Tokens, service-level messaging or other custom connectors.
Each of these machine identities potentially has the same, or greater, access capabilities as a human user, but these monitoring challenges leave NHIs generally invisible to security teams.
Comparison: Human vs Non-Human Identities
| Attribute | Human Identity | Non-Human Identity |
|---|---|---|
| Definition | Assigned to an individual user who interacts directly with systems. | Digital credentials assigned to a system, application, bots or process that operates autonomously. |
| Ownership | Clearly mapped to a specific employee or contractor, and managed through structured HR processes. | Often lacks clear ownership; tied to systems or teams rather than individuals. |
| Volume & Scale | Limited to workforce size. | Can number in the tens or hundreds of thousands due to automation. |
| Lifecycle Management | Managed through HR-driven joiner–mover–leaver workflows. | Frequently unmanaged; provisioned automatically and rarely decommissioned. |
| Security Risks | Insider threats, weak passwords, and phishing. | Hardcoded secrets, credential sprawl, stagnant or unrotated keys, abandoned accounts, over-privileged access, limited visibility, and weak lifecycle controls |
| Governance Tools | Identity Governance (IGA), MFA, SSO, Role-based access control (RBAC), HR-driven identity lifecycle, and compliance audits. | CIEM, Secrets Management, Certificate Management, and Machine Identity Platforms are managed through NHIM solutions that help discover all machine identities, assign ownership, enforce least privilege, and automate credential rotation. |
| Visibility | Centrally tracked and reviewed. | Fragmented across DevOps pipelines, cloud environments, and automation tools — for example, API keys stored in Jenkins, service accounts in AWS, and secrets in Kubernetes, all managed separately without centralized visibility. |
| Purpose | Used by individuals to access systems, perform business functions, and interact with digital applications. | Used by systems, applications, or devices to automate processes, enable integrations, and support secure machine-to-machine communication at scale. |
| Creation | Typically provisioned manually during employee onboarding through HR systems or identity workflows. | Automatically generated by cloud platforms, DevOps pipelines, APIs, or during application deployment and system integrations. |
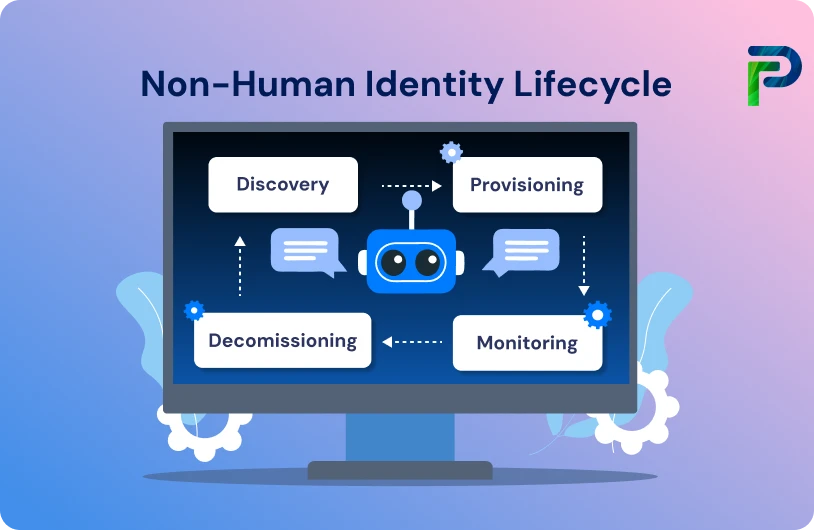
The Non-Human Identity Lifecycle Explained
The process of managing non-human identities is not a single event but instead a continual lifecycle that ensures every API key, service account, or workload is discovered, secured, and decommissioned in a responsible way. Much like a human identity governance model, the non-human identity lifecycle enables an organization to minimize blind spots, adopt least privilege and maintain compliance across continuously changing environments such as multi-cloud and DevOps pipelines.
The following discusses the components of each phase of the lifecycle, as well as the overarching security and governance considerations of each part of the process.
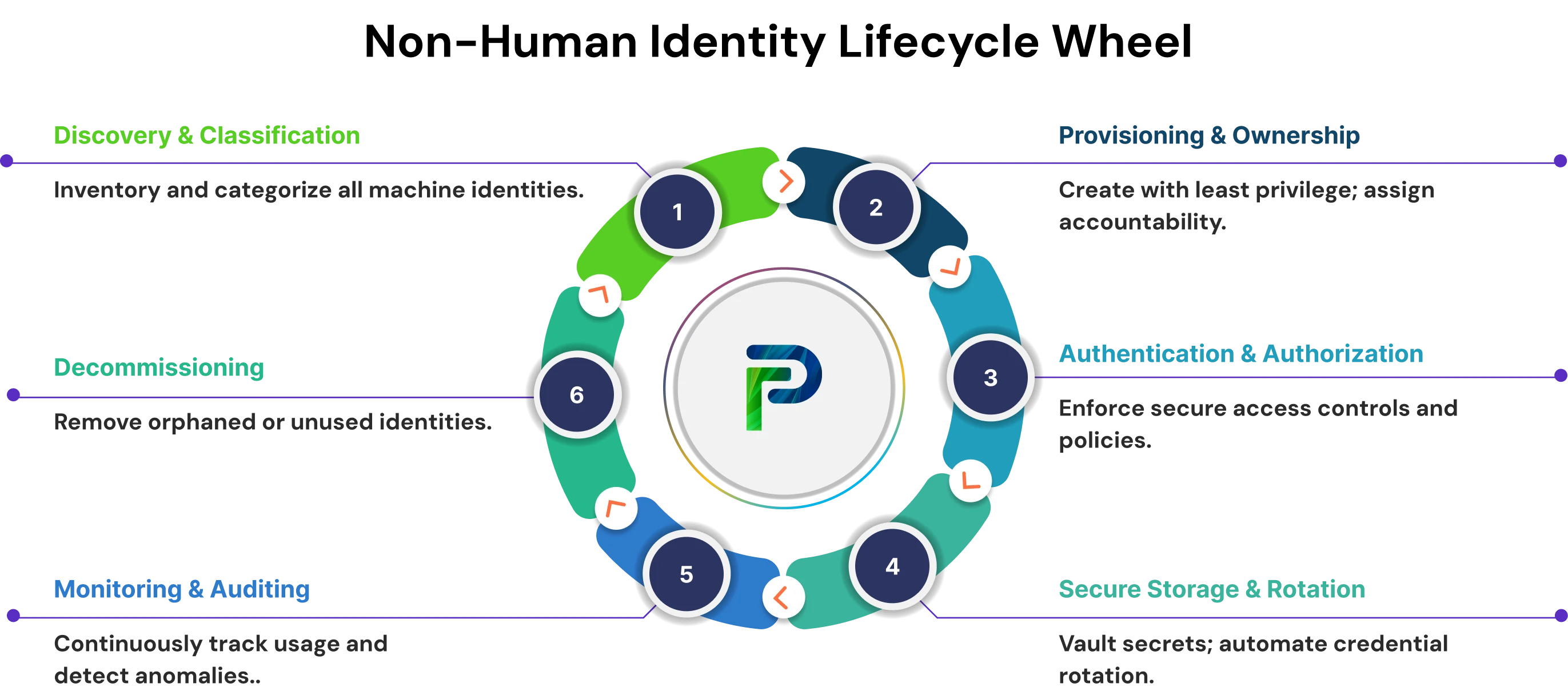
1. Discovery & Classification
The first step in governing non-human identities is to discover and list all machine accounts, API Keys, service accounts, and other credentials on cloud platforms, DevOps pipelines, containers, and on-prem systems. After identifying these identities, they should be classified based on their intended purpose, type of access, and sensitivity level (e.g., segregating highly privileged production APIs from low-risk test accounts). This will help your organization understand risk levels and enable an appropriate governance foundation.
2. Provisioning & Ownership
Provisioning is the creation of non-human identities based on least privilege, only granting permissions to perform the things they are supposed to be performing. Over-privileged service accounts are one of the major contributors to lateral movement and privilege escalation in incidents.
Ownership is about accountability. Every non-human identity should have an individual or team responsible for reviewing access and managing lifecycle events, approving changes, etc. It can be processed very heavily and relied on in DevOps and cloud-native environments.
3. Authentication & Authorization
This stage manages the mechanisms through which non-human identities prove their validity (authentication) and what they're permitted to do (authorization). Strong solutions enable authentication through certificates, tokens, or API keys for machines, and authorization through Role-Based Access Control (RBAC) or Attribute-Based Access Control (ABAC). Short-lived credentials with limited permissions help to reduce potential exposure.
4. Secure Storage & Rotation
Machine-based credentials should never be stored in clear text, code repositories, or configuration files. Instead, credentials must be secured in a secrets vault or key management system.
Automated rotation of credentials by regularly updating your keys, tokens, and certificates ensures that stale or compromised credentials are not used by attackers. This is an important step in achieving zero standing privileges.
5. Monitoring & Auditing
Regularly monitor non-human identities to identify suspicious activity, such as unusual access patterns, excessive API calls, or inappropriate credential usage. Audit NHI use regularly, both for compliance with policies, as well as to identify gaps in security protections, and to provide a record for investigations and regulatory obligations. The importance of monitoring in a cloud and DevOps environment is that it allows organizations to rapidly address misuse or deviations from defined security baselines.
6. Decommissioning
To minimize hidden security risks, identify and proactively remove stale or unused non-human identities. Revoke any credentials, tokens, and certificates when no application, service, or device needs access to them. Automated cleanup helps minimize orphaned identities, which therefore minimizes the attack surface overall.
Why Non-Human Identity Lifecycle Management Matters
Non-human identity management is fundamentally important because machine identities (APIs, service accounts, applications, etc.) are used in nearly all modern operations and are a major security risk if not managed properly. Organizations can face greater security risks when attackers exploit these identities, which can lead to data breaches, regulatory violations, and operational downtime.
1. Security Risks
Non-human identities that are not managed can easily lead to identity sprawl, where thousands of service accounts, APIs, and bots exist without clear ownership or visibility. They are oftentimes endowed with too many privileges, allowing for perfect conditions for an attacker to take advantage of.
Orphaned accounts are equally dangerous. These are credentials that remain live even after a workload or application has been turned off. These types of unused identities can be used for lateral movement, privilege escalation, or simply data theft.
In addition, credentials leaks from unsecured code repositories (where developers store source code), configuration files(which may contain passwords or API keys), and CI/CD pipelines(automated workflows for building, testing, and deploying applications) are in the top 3 for breaches. Lifecycle management means every machine credential is accounted for, rotated, and securely retired, ultimately reducing this risk tremendously.
2. Compliance Needs
Regulations (e.g., HIPAA, GDPR, SOX) require that you be able to demonstrate controls over who (or what) has access to sensitive data. This entails maintaining audit trails, demonstrating access reviews, and documenting ownership of credentials and certificates.
Non-human Identity lifecycle management delivers the visibility and traceability auditors require. By applying least privilege, maintaining logs of key usage, and mapping every machine identity to an accountable owner, organisations can confidently demonstrate compliance with elegance, not complexity.
3. Operational Efficiency
In addition to avoiding risk and ensuring compliance with its structured lifecycle, you will see measurable operational effectiveness. Manual provisioning and credential management across hundreds of systems is inefficient and prone to errors and delays. Automation of these workflows reduces manual effort, reduces misconfiguration, and improves deployment cycles.
With centralized control and policy-based workflows, security and DevOps teams can work together easily - ensuring speed can be delivered securely.
Challenges in Managing Non-Human Identities
At the enterprise scale, managing non-human identities (NHIs) is complicated, not because organizations are lacking in security tools, but because visibility, ownership, and governance lag behind the speed of automation. Each challenge builds over time, resulting in blind spots and hidden risks that traditional identity programs were never intended to solve.
1. Fragmented Inventory
In many organizations, non-human identities are tracked in disconnected tools - secrets managers, cloud IAM consoles, CI/CD scripts or even spreadsheets. It is impossible to know what identities are active, what access they have, or how they are being used, which can lead to identity sprawl and larger attack surfaces without a consolidated view.
2. Disconnected Tooling
Credential management is done in a myriad of different systems, identity providers, infrastructure-as-code scripts, and secrets managers, but they rarely connect to any other system. This leads to gaps in governance, requires prior manual reconciliation to comply, and nearly makes policy enforcement impossible due to challenges of uniformly and consistently meeting an organization policy.
3. Unclear Ownership
Some NHIs not only lack direct ownership, there have often orphaned credentials that remain active well beyond the end of life of any related workload. No individual or team assumes accountability for reviewing and decommissioning orphaned credentials. In the absence of individuals managing access review, access is rarely monitored, increasing risk and complicating compliance efforts.
4. Inconsistent Review Practices
Typically, access reviews are centred around human users, while machine identities do not receive the same examination. And, even if we account for NHIs within the review, they don't have the appropriate context for the review, and reviewers end up approving permissions without the ability to properly understand the associated risk.
5. Cross-Team Misalignment
Managing NHIs involves security teams, DevOps teams, cloud teams, and application teams. Security teams are concerned with controls, engineering teams want speed, and IAM teams want standardized processes and procedures. If these teams operate without coordination, the additions of permissions stack up on NHIs, creating possible exposure in the permission issuance process.

Best Practices for Automating the NHI Lifecycle
Effectively managing non-human identities (NHIs) requires automation, visibility, and ongoing oversight. Manual oversight cannot keep up with the scale of machine identities in today's cloud-first environments. The best practices below will provide your organization with control, risk mitigation, and compliance throughout the lifecycle.
1. Discover and Classify
Beginning with the discovery of all non-human identities in your cloud, on-prem, and development environments, including service accounts, API tokens, and automation scripts. Classify them based on function, level of privilege, and sensitive system classification. Classification ensures appropriate prioritization of non-human identities needing further control vs. minimal access.
2. Provision with Intent
When provisioning new NHIs, grant the NHI only the minimum access required, based on the specific task or workflow. This can include limiting permissions based on scope, which can include system, actions, or environment. Avoid systemic provisioning and default access privileges. Provisioning with intent prevents an NHI from evolving into an over-privileged account and future risk.
3. Assign Ownership
An NHI should have an owner or support team for the liable upkeep of the non-human identity. Ownership will provide accountability for periodic review of permissions, credential change/rotation when NHI access is still valid, and ultimately retiring the NHI when access is no longer needed. Ownership reduces orphaned credentials and supports proper auditability.
4. Store and Rotate Credentials Securely
All credentials, such as API keys, tokens, and certificates should be kept in a secure vault, such as HashiCorp Vault, AWS Secrets Manager, or Azure Key Vault. Automate the rotation of credentials regularly or when suspicious activity has occurred, and do not hard-code or store long-term licenses in code or confidential files.
5. Monitor and Analyze Usage
Utilize services, such as CIEM (Cloud Infrastructure Entitlement Management), to continuously monitor how Non-Human Identities (NHIs) use their permissions. Configure alerts to trigger when unusual behaviour occurs, such as privilege escalation, excessive resources (API calls) or authentication failures, to quickly identify potential misuse and reinforce least privilege.
6. Maintain Audit and Review Readiness
Maintain comprehensive records of ownership, permissions and activity logs so access review(s) and compliance needs are supported. Performing audits regularly (quarterly or automated through logs) is valuable for discovering misconfiguration(s), expired accounts and unneeded authorizations before they become a security risk.
7. Decommission when access is no longer needed
Promptly identify and clean up inactive or unused NHIs. Revoke the credentials used to authenticate the HNI and remove access when the application or service has been removed from the organization. Proactive cleanup will minimize "identity sprawl" too many authorized NHIs for which access is no longer being utilized, minimizes attack surfaces and maintains an accurate inventory of those created within each cloud account.
Real-World Examples of Non-Human Identity Lifecycle
The non-human identity lifecycle in action highlights how automation, governance, and visibility are essential to the overall mission of enhancing enterprise security. Here are three examples across common use cases, SaaS applications, cloud infrastructure, and IoT ecosystems.
Example 1: The Lifecycle of API Keys in a SaaS Tool
A SaaS solution offers API keys that enable safe communication between internal microservices and third-party integrations.
- Provisioning: Keys are automatically created with least privilege and limited to specific APIs.
- Monitoring: Usage is tracked continuously, and unusual activity triggers alerts.
- Rotation & Decommissioning: Keys rotate automatically every 90 days, and unused keys are deactivated.
Outcome: Regular rotation and monitoring reduce credential exposure while keeping developers productive.
Example 2: Service Account in AWS
Service accounts power automation workflows or backend services in the cloud.
- Provisioning: A service account is created with least-privilege roles and assigned to a specific team owner.
- Monitoring: Usage is monitored to ensure access is only to designated resources.
- Decommissioning: When workflows are replaced, accounts are automatically disabled.
Outcome: Automation prevents orphaned accounts and ensures compliance with IAM policies.
Example 3: Rotating Identities and Credentials for IoT Devices
IoT devices need secure identities to communicate with the cloud.
- Provisioning: Each device gets a unique certificate-based identity during onboarding.
- Authentication & Rotation: Devices authenticate via mutual TLS, with certificates rotated automatically every 60 days.
- Decommissioning: Credentials are revoked when devices reach end-of-life.
Outcome: Automated rotation and decommissioning reduce operational overhead and prevent credential misuse or device spoofing.
Future of Non-Human Identity Lifecycle Management
As enterprise infrastructure evolves into a more API-driven and automated state, non-human identity lifecycle management will be future-focused on intelligence, integration and autonomy. Organizations will transition to systems that operate with continual detection, deciding and acting in real-time rather than manual governance.
-
AI-Powered Anomaly Detection
Artificial intelligence (AI) and machine learning (ML) are changing how identity activity is monitored. Organizations can leverage AI models to learn the “normal” behaviours of service accounts, bots, or workloads; thus allowing them to detect when something deviates from that behaviour versus relying on static rules or thresholds.
If, for example, a workload suddenly accesses a resource it’s never touched before, or if the workload performs actions outside of its scheduled time, the AI model’s detection could trigger an automated containment/credential revocation event.
This allows for identity activity monitoring to change from a merely reactive to a predictive defense function, which can help to close the compromise to response gap. -
Integration with CIEM and IGA Platforms
The next stage of identity security will see a deeper melding of Cloud Infrastructure Entitlement Management (CIEM), Identity Governance and Administration (IGA) and non-human identity management systems.
Such convergence will allow organizations to maintain a single source of truth across cloud, on-prem and hybrid systems with shared policies, real-time visibility on entitlement, and shared visibility in access.
Thus, governance becomes more contextual: with the ability to see and manage every machine identity's access rights, ownership, and activity collectively, and reduce shadow identities and compliance blind spots. -
Context-aware and real-time security
Lifecycle management will have additional contextual information and considerations, such as the purpose of workloads, the user or team interacting with them, contextually specific risk scores, and even things happening in their environment. With that information, your system could automatically adjust permissions, rotate credentials, or flag risky activity as it is happening, ultimately providing context-aware security without compromising the speed of enterprise operations. -
Self-healing automation
Next-generation tools will extend beyond provisioning and decommissioning to automatically detect misconfigurations, enforce least-privilege access, and remediate deviations, all without manual oversight. This “self-healing” concept will reduce the opportunity for human mistakes, minimize orphaned identities, and ensure compliance in volatile architectures with thousands of machine identities in dynamic environments.
Final Thoughts
Non-human identities have quietly become the backbone of enterprise operations, runtime, automation, cloud workloads, machine-to-machine communication, etc. Though the hyper growth of non-human identities created an invisible attack surface that traditional identity programs were not built to support.
What the far-seeing security teams are coming to realise is that managing non-human identities is not only about access, it is about preserving trust in the automation itself. This means the ability to discover, govern, and retire non-human identities is a function of how secure, compliant and agile your digital ecosystem can be.
Identity Confluence is purpose-built for this new paradigm of managing machine identities in the world.
Identity Confluence creates end-to-end automation, contextual intelligence, and lifecycle visibility, enabling your enterprise to manage machine identity risks and simplify governance at scale proactively.
NEXT STEPS
Ready to bring visibility and control to your non-human identities?
Frequently Asked Questions (FAQs)
1. What is a non-human identity?
A non-human identity (NHI) is any digital identity or credential that exists to represent a machine, application, or service instead of a human. Non-human identities include the likes of service accounts, robots, application programming interface (API) keys, certificates, and workloads that operate autonomously from humans across systems. As the pace of automation increases, non-human identities outnumber human identities in most enterprise environments and consequently have become essential aspects of identity security.2. How do you manage non-human identities?
Non-human identities are managed through a predefined lifecycle of discovery, provisioning, monitoring, and decommissioning. This means assigning ownership, applying least-privilege access, credential rotation, and usage tracking. A lifecycle management process for non-human identities minimizes security risk since no API keys, tokens, or service accounts will be active longer than necessary.3. Why is non-human identity lifecycle management important?
Management of the NHI lifecycle helps to curb identity sprawl, orphaned accounts, and credential exposure. These are three of the most common causes of breaches in the cloud context. Non-human identities also support compliance with secure standards like HIPAA, GDPR, and SOX by ensuring that each identity has a clear owner, purpose, and audit trail. With the help of automation, organizations can ensure secure authentication while still being operationally agile.4. What are examples of non-human identities?
Examples of NHI are API keys for applications, IoT identities for smart sensors, Kubernetes secrets to authenticate workloads, and service accounts for background processes. Each NHI accounts for a unique operational role; however, they still require governance to ensure misuse or unauthorized access does not take place.5. What tools support NHI lifecycle automation?
Most organizations will usually take a multi-faceted approach by using Secrets Management tools, such as HashiCorp Vault or AWS Secrets Manager, Cloud Infrastructure Entitlement Management (CIEM) solutions for visibility and governance over access, and integrate Identity Governance and Administration (IGA) tools, such as Tech Prescient’s Identity Confluence for full automation. Collectively, these tools provide the underpinnings of Zero Trust-enabled machine identity security.