
What Is a Security Operations Center (SOC)?

A Security Operations Center (SOC) acts as a centralized facility that enhances an organization's cybersecurity posture through the prevention of threats, real-time detections, and incident response activities at a rapid pace. SOC teams conduct continuous monitoring of IT infrastructure, looking for and analyzing potential threats, triaging security alerts, investigating and responding to incidents, and conducting threat hunting and remediation efforts. Teams work with advanced technologies (SIEM platforms) to analyze security data for valid threats to the organization, while inputting threat intelligence to predict evolving attack methods. The main goal is to protect organizational digital assets while ensuring operational resiliency from the threat of an ongoing cyber attack.
Organizations that have achieved an advanced, mature SOC capability deliver statistically significant superior security outcomes. IBM's 2025 Cost of a Data Breach Report notes that global data breach costs averaged $4.44 million, but those that matured in using AI and automation extensively within their security operations were able to save $1.9 million versus those that did not have those capabilities. Internal security teams now identify the compromise of systems in approximately 50% of breaches, thereby minimizing breach costs and timelines.
Recognizing what a SOC is begins with more than just understanding the technology; it is also an approach to cybersecurity involving people, processes, and capabilities using advanced technology to achieve the mean time to identify and mitigate breaches (241 days) that leading organizations achieve today.
Key takeaways:
- SOC centralizes threat detection, incident response, and security monitoring functions
- Combines people, processes, and technology for comprehensive cybersecurity defense
- Reduces breach detection time and minimizes business impact through rapid response
- Supports regulatory compliance through continuous monitoring and documentation
What Does a SOC Do?
SOCs continuously monitor IT infrastructure to discover malicious activity and orchestrate response and remediation actions to contain a threat before it results in substantial damage.
What is a SOC, you may ask?
A practical definition is that it is a centralized facility where technology is integrated into security operations and provides a comprehensive security operations centre.
SOC teams provide 24/7 monitoring to discover threats in an organization's digital infrastructure, using SIEM platforms and advanced security technology. Operations in the SOC consist of continuous analysis of real-time security events, incident response coordination, and proactive threat hunting capabilities. The overall goal of a SOC is to minimize cyber attack impact, protect sensitive data, and ensure confidentiality, integrity, and availability of your organization's information assets.
Core Functions of a SOC
Modern security operations centers perform several important and integrated functions to provide complete protection from the risks of cybersecurity. The operations of an SOC provide continuous monitoring, analysis, and response functions that protect organizational assets from applicable threats. These functions provide a layered defense-in-depth strategy that takes into consideration all the stages of the attack lifecycle, from detection to remediation.
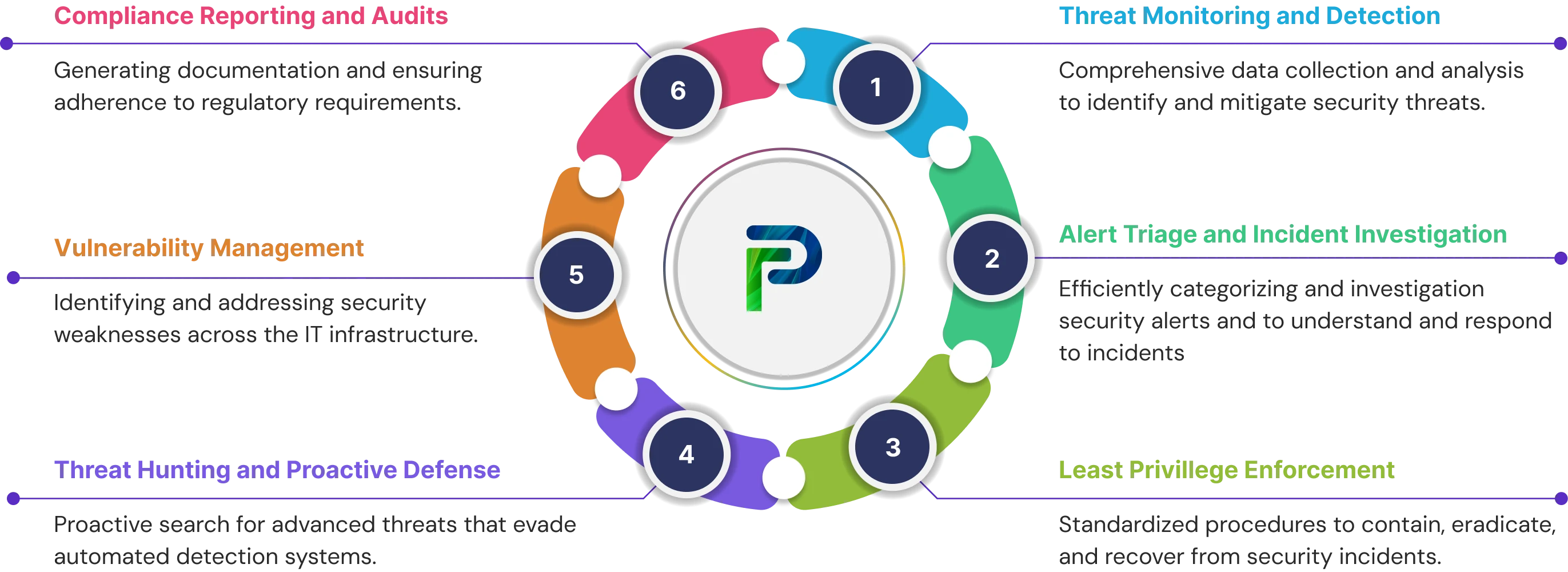
1. Threat Monitoring and Detection
SOC operations start by collecting data from all the security tools deployed throughout the entire IT environment.
The main components of monitoring include:
- SIEM tools that aggregate log data from firewalls, intrusion detection systems, and endpoint protection tools
- Correlation analysis that identifies attack vectors that span multiple systems,
- Real-time alerts of suspicious behaviour across the network.
Detection Approaches
- Signature-Based Detection: This type of detection utilizes hash values, behavioural signatures, and network indicators to identify known malware families and attack tools.
- Anomaly-Based Detection: This type of detection develops baselines of normal behaviour for a system and its users and then flags deviance from that baseline for further review, knowing that deviation may indicate a compromise. Anomaly-based detection is frequently utilized in conjunction with machine learning algorithms to assist with event detection.
- User and Entity Behaviour Analytics (UEBA): This type of analytics monitors authentication patterns, file access behaviours, and privilege usages in order to detect insider threats and compromised accounts. These systems may also generate alerts when users display behaviours that could be viewed as unusual, such as accessing atypical systems or downloading unusual amounts of data.
- Integration of Threat Intelligence: This involves external data about active attack campaigns, malware families, and indicators of compromise (IOCs) from commercial feeds and/or by virtue of sharing programmes with the government.
- Network Traffic Analysis: This analysis involves the review of all communication patterns and data flows in order to identify indicators of command and control communications, data exfiltration attempts, and lateral movement events through the application of deep packet inspection.
2. Alert Triage and Incident Investigation
SOC analysts receive thousands of security alerts daily from various monitoring systems.
Triage Process:
| Stage | Activity | Responsible Team |
|---|---|---|
| Initial Assessment | Eliminate false positives and gather preliminary data | Tier 1 analysts |
| Alert Correlation | Combine related events into cohesive incident records | Automated systems + analysts |
| Investigation | Conduct digital forensics and timeline analysis | Tier 2/3 analysts |
Investigation Techniques
- Digital Forensics:
- Volatile memory analysis identifies running malware processes and network connections
- Disk forensics examines file systems and registry entries to reconstruct attacker activities
- Timeline Analysis Correlates security events with system logs and user activity data to identify:
- Initial compromise vectors
- Lateral movement techniques
- Data access patterns
- Exfiltration methods
Evidence Preservation is responsible for maintaining chain of custody records and conducting forensic imaging for legal matters and regulatory investigations.
3. Incident Response and Remediation
-
Incident Response:
Once a security incident has been identified, the SOC team takes swift action to contain the threat, minimize harm, and ultimately aim to mitigate overall impact to the business. SOC teams follow standardized incident response procedures based on incident classification and severity levels. -
Response Framework: Detection → Containment → Eradication → Recovery → Post-Incident Analysis
-
Containment Strategies:
- Network isolation to disconnect affected systems
- Account disabling to prevent compromised credential use
- DNS blocking to prevent command and control communications
- Eradication Activities:
- Malware removal (files, processes, persistence mechanisms)
- Vulnerability patching to address security weaknesses
- Strengthening defenses against similar attacks
- System Recovery:
- Deploy clean system images
- Restore data from clean backups
- Validate security control configurations
Following an incident, the analysis of the event considers the documented attack techniques that were used, identifies gaps in your protections, and may update both your lessons learned from the incident and your incident response playbook.
4. Threat Hunting and Proactive Defense
Threat hunting is a proactive search for advanced threats that are evading detection from your automated detection systems.
Hunting Methodologies
- Hypothesis-Driven Hunting: An example of this is when you examine specific attack techniques, such as living-off-the-land attacks, flightless attacks, or any unusual execution of PowerShell that may indicate fileless malware.
- APT Hunting: There are threat hunting activities that directly target identifying advanced persistent threats (APTs).
- Covert channels in network traffic or data exfiltration patterns through your monitoring systems.
- Memory dumps may also be reviewed to determine if there has been injected code and
- Investigate the authentication logs for possibly privileged escalation attempts.
- Behavioural Hunting: Threat hunting can simply be blended in with looking for the indicators of compromise (IOCs) in user activity or system activity. Some examples of IOCs are unusual sequences of file accesses or administrative activity outside normal business hours.
- Detection Engineering: The result of the hunt can be utilized to create new SIEM rules, update the security tool configuration, or inform future needs for coverage of monitoring.
5. Vulnerability Management
SOC teams coordinate vulnerability assessment activities across the IT infrastructure.
Risk-Based Prioritization:
| Priority Level | Criteria | Action Timeline |
|---|---|---|
| Critical | Internet-facing systems + active exploitation | Immediate |
| High | High exploitability + critical assets | 24-48 hours |
| Medium | Moderate risk with compensating controls | Scheduled maintenance |
| Low | Limited exposure + low exploitability | Next patch cycle |
Patch Management Coordination:
- Emergency patching for zero-day vulnerabilities
- Scheduled maintenance windows for routine updates
- Compensating controls when immediate patching isn't feasible
Vulnerability Tracking:
- Monitors remediation progress and provides management visibility into exposure trends and effectiveness metrics.
6. Compliance Reporting and Audits
SOC operations generate comprehensive documentation for regulatory compliance and security audits.
Compliance Activities
Automated Reporting:
- Extract security metrics from SIEM platforms and vulnerability scanners
- Generate compliance dashboards for frameworks like SOX, GDPR, HIPAA, PCI DSS
Security Control Testing:
- Validate that safeguards operate effectively
- Document testing procedures and remediation activities
- Align testing frequencies with regulatory requirements
Incident Documentation:
- Maintain detailed records of security events and response actions
- Document breach notification procedures
- Track corrective actions for prevention
Audit Trail Preservation:
- Archive security events and access records per regulatory timeframes
- Ensure data integrity and accessibility for audit requests
- Monitor for configuration drift and policy violations
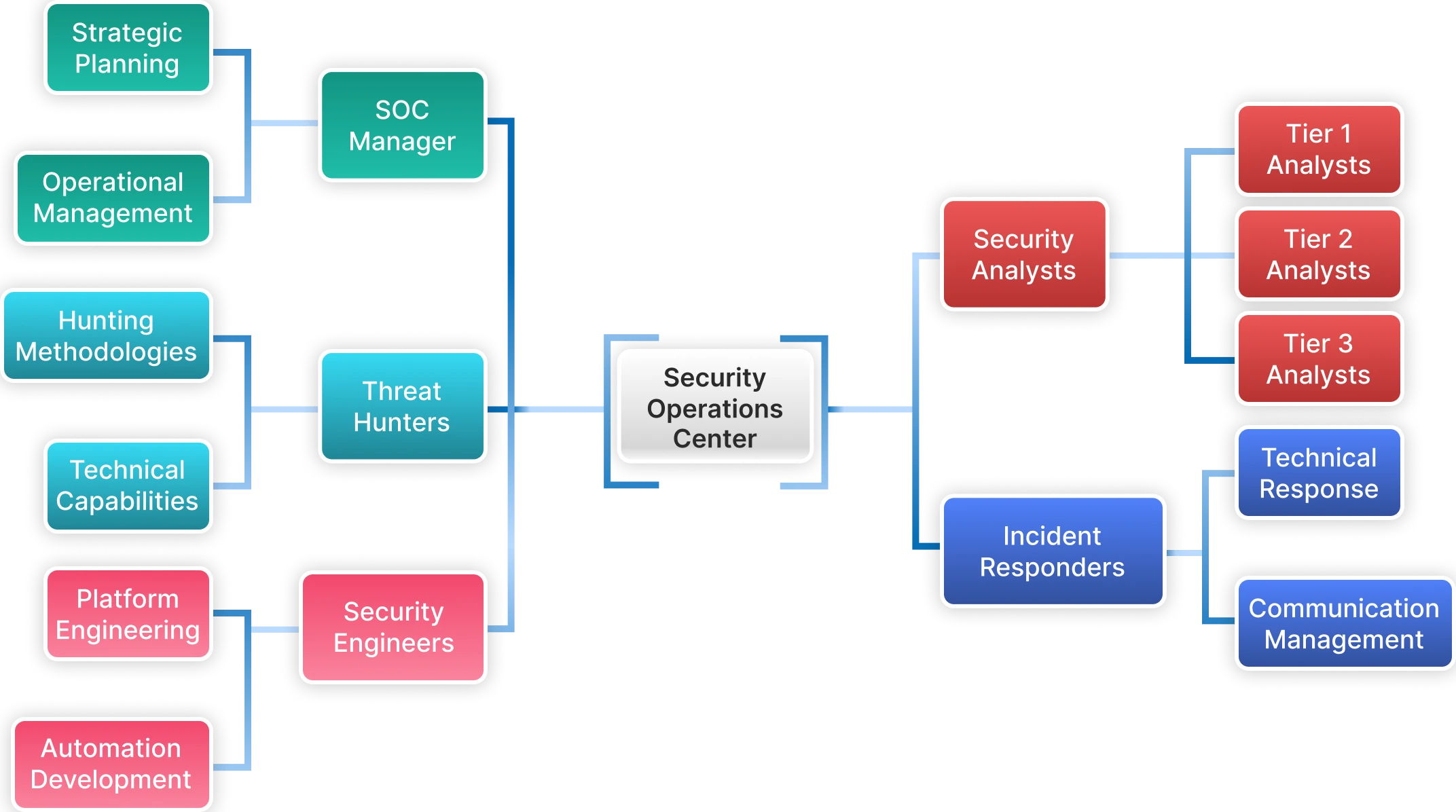
Key Roles in a SOC
SOC operations depend on specialized roles, with each role carrying specific responsibilities in monitoring, investigation, response, and management of strategic security operations. Familiarity with SOC roles is key to organizations developing their cybersecurity SOC capabilities.
1. Chief Information Security Officer (CISO)
Provides strategic security leadership, executive communication, and organizational cybersecurity governance while setting overall security strategy and managing budgets.
1.1 Key Responsibilities
- Strategic security leadership and organizational governance
- Executive communication and board reporting on security risks
- Budget management and security investment decisions
- Alignment of security strategy with business objectives
- Regulatory compliance oversight and risk management
2. SOC Manager
Oversee the daily operations of teams, tooling, workflows and activities while providing strategic leadership in security operations programs.
2.1 Key Responsibilities
| Area | Activities |
|---|---|
| Strategic Planning | • Threat landscape assessment |
| Operational Management | • Staff scheduling for 24/7 coverage |
| Stakeholder Management | • Executive leadership coordination |
3. Security Analysts (Tier 1-3)
Monitor distributed environments, investigate alerts and perform incident triage across a tiered approach ranging from basic triage of alerts through advanced forensic analysis.
3.1 Analyst Tier Structure
| Tier | Primary Focus | Key Activities | Requirements |
|---|---|---|---|
| Tier 1 | Initial Response | • SIEM alert monitoring | Security+ certification |
| Tier 2 | Deep Investigation | • Detailed incident investigation | Network forensics, malware analysis skills |
| Tier 3 | Advanced Expertise | • Complex incident investigation | GCFA, GCIH, or CISSP certifications |
4. Threat Hunters
Threat Hunters Engage in proactive hunting for advanced threats and unknown adversaries through hypothesis-driven investigation techniques that extend beyond audit-based detection.
4.1 Core Capabilities
- Statistical Analysis: Personalized queries, behavioural analysis, integration of threat intelligencePersonalized queries, behavioural analysis, integration of threat intelligence
- Technical Expertise: Network traffic analysis (Zeek, Suricata), EDR technologies, memory forensics
- Intelligence Analysis: Threat actor research, campaign tracking, indicator development
- Reports: New SIEM rules, advancement of monitoring capability, enhancement of detection capabilities
5. Incident Responders
Coordinate incident response activities in the event of security incidents to limit potential damage to the business and/or provide controls to more effectively contain the threat.
5.1 Response Framework
| Phase | Activities | Stakeholders |
|---|---|---|
| Containment | Malware containment, network isolation, evidence preservation | IT teams, Security engineers |
| Communication | Stakeholder notification, breach notification coordination | Legal, Executive leadership |
| External Coordination | Law enforcement, regulatory notifications, cyber insurance | External agencies |
| Post-Incident | Incident analysis, lessons learned, playbook updates | Security team, Management |
6. Security Engineers
Design and sustain the cybersecurity architecture, develop automation workflows, and optimize performance and efficiencies of the security tools.
6.1 Engineering Domains
- Platform Engineering: SIEM management, data integration, correlation rules, high availability
- Automation Development: Security orchestration, automated response, API programming
- Tooling Integration: Implementation of new technologies, custom dashboards, proof of concept testing
- Performance Optimization: System tuning, capacity planning, cost analysis
Types of SOC Models
While organizations may implement different SOC models based on availability of resources, expertise requirements, control preferences, and costs that align with the business objectives and risk tolerances:
1. In-house SOC
Internal SOC operations allow maximum control of the security processes, data control, and incident response coordination while further integrating the security services into the business process and organizational culture. An internal team provisions deeper situational knowledge of the internal systems and business-specific applications than a third-party provider would have. Internal SOC provisioning requires a substantial, resource-heavy investment in security talent, technology infrastructure, and permanent staff training to maintain operations on a 24/7 basis to keep pace with a constantly changing threat landscape.
2. Outsourced SOC (MSSPs)
Managed Security Service Providers (MSSPs) provide cybersecurity expertise and experience to multiple client organizations in dedicated security operations centers. MSSPs provide beneficial economies of scale, enterprise-grade security tools, and immediate access to experience security professionals without incurring the capital cost of building an internal team and staffing the operation. Organizations benefit from experienced security processes, sophisticated threat intelligence, and predictable costs through a subscription-based model; however, they accept a diminished level of control and potential complexity when it comes to integration.
3. Hybrid SOC
SOC models bring together the benefits of both internal and outsourced SOCs. These organizations have an internal SOC team and utilize an external provider for its expertise and resources. Hybrid SOCs can balance the organization's level of control, cost, and access to specialized skills.
4. Global SOC (GSOC)
Large multinational organizations use Global SOC (GSOC) architectures to distribute their security operations to regionally-based centres while centralizing threat intelligence and policy management. According to Microsoft Security, very large organization with operations in multiple countries rely on a GSOC to coordinate their detection and response across multiple local SOCs. GSOC models operate continuously 24/7, as they use local security teams to provide optimal analyst alertness and regional expertise. Local teams will have the advantage of language capability and regulatory knowledge; however, consistent delivery of service across varied time zones and global coordination of incident response across the multiple teams creates exponential complexity.
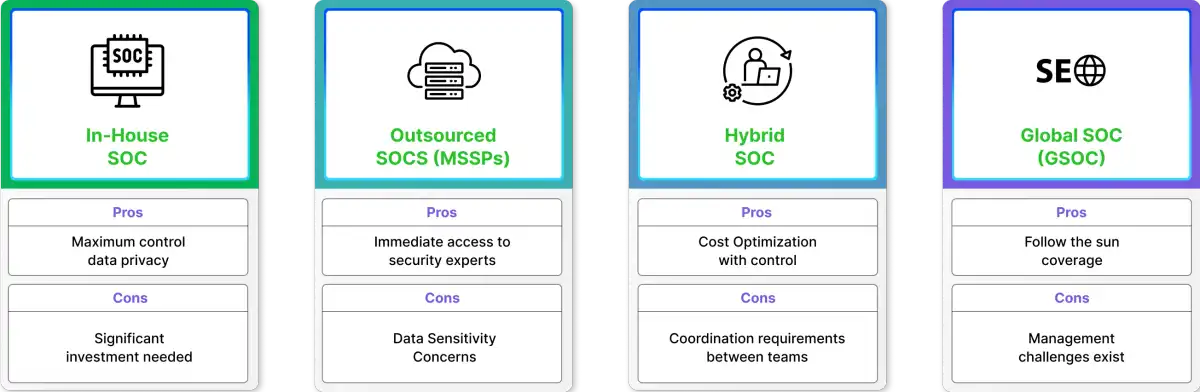
SOC Model Comparison
| Feature | In-house SOC | Outsourced SOC (MSSP) | Hybrid SOC | Global SOC (GSOC) |
|---|---|---|---|---|
| Control Level | Maximum | Limited | Balanced | High (centralized oversight) |
| Initial Investment | Very High | Low | Medium | Very High |
| Operational Cost | High (ongoing) | Predictable (subscription) | Medium-High | Very High |
| Customization | Full | Limited | Moderate | Full |
| Expertise Access | Requires hiring | Immediate | Combined | Requires hiring + local expertise |
| Response Time | Immediate | Potential delays | Immediate (critical systems) | Immediate (regional) |
| 24/7 Coverage | Requires full staffing | Included | Optimized (follow-the-sun) | Built-in (regional teams) |
| Scalability | Limited by staff | High | High | Very High |
| Technology Costs | SIEM, tools, infrastructure | Included in service | Shared | SIEM + global infrastructure |
| Best For | Large enterprises with sensitive data | SMBs, organizations with limited security staff | Mid-large orgs seeking balance | Multinational corporations |
Why Organizations Need a SOC
SOC functions mitigate the existential challenges faced by organizations in cybersecurity that cannot be resolved effectively through conventional reactive security approaches or stand-alone point solutions.
Proactive Defense Against Cyber Threats
Traditional security approaches provide clues to the damaging cybersecurity breaches only after normal practices, including periodic scans for vulnerabilities, have borne fruit, and only after incident response was implemented when the breach was identified.
This process allows cybercriminals to establish a persistent presence for days, weeks, or even months without detection! Advanced persistent threats may also enjoy this level of operation for varying lengths of time while organizations apply traditional security approaches.
An SOC capability allows for continuous monitoring of network traffic, logs on systems, and user behaviours, in real time, to identify malicious traffic patterns and attack indicators. Threat intelligence can also be integrated to improve contextual sensing or visibility, as can behavioural analysis tools, which rely on machine learning, to identify the most sophisticated attacks against organizations, including zero-day exploits and living-off-the-land attacks, that evade traditional security controls.
Reduced Breach Damage and Costs
An analysis provided in IBM's 2025 Cost of a Data Breach Report noted that organizations that had extensive AI and automation capabilities in the areas of security operations saved $1.9 million in breach costs compared to those without such capabilities. SOC capabilities reduce mean time to detection below industry averages and approaches by leading organizations of 241 days to identify and contain the breaches.
Identification of breaches before or very near to occurring limits the time for an attacker to reside in an organization, reduces event opportunities for exfiltration of data, and mitigates business disruption through structuring containment procedures and recovery planning. Evidence preservation capabilities aid, support and inform judicial proceedings and regulatory enquiries while maintaining customer confidence during a security incident.
Improved Compliance Readiness
Regulatory frameworks such as GDPR, HIPAA, SOX, and PCI DSS are increasingly requiring continuous monitoring and incident response capabilities commensurate with SOC operational capabilities. SOC operations will create the required security event logs, incident response documentation, and evidence of control testing, as required for regulatory compliance.
Automated compliance reporting removes the documentation burden while offering the auditor evidence of security controls' operational effectiveness. The SOC capabilities will allow for a quick assessment of a breach so that the notification to the regulator is within an assigned time limit and the organization minimizes the potential for penalties and proves it had proactive compliance in place.
Strengthened Business Continuity and Stakeholder Trust
Trust Cybersecurity incidents can interfere with the course of operations and damage stakeholder confidence. Security operations center (SOC) capabilities support timely incident response and effective communication and stakeholder confidence during a crisis. An organization with mature SOC capabilities signals that the organization has implemented security posture that proactively differentiates a company from other competitors.
In addition, vendor relationships may require security certifications and incident response capabilities before establishing business or procurement relationships. SOC capabilities can provide evidence of the organization's security maturity, supporting new business development, enabling better competitive positioning, and potentially supporting investor relations, while simultaneously reducing scrutiny from regulatory agencies.
Benefits at a Glance
| Benefit Category | Key Impact | Measurable Outcome |
|---|---|---|
| Proactive Defense | Early threat detection | Identifies attacks before major damage |
| Cost Reduction | Faster response times | $1.9M average savings with AI/automation |
| Compliance | Automated documentation | Reduced audit burden, avoided penalties |
| Business Trust | Security maturity demonstration | Enhanced partnerships, investor confidence |
Future of SOCs
SOC evolution continues through integration of artificial intelligence, cloud-native architectures, and extended detection capabilities that address increasingly complex threat landscapes and organizational technology environments.
AI/ML in SOC Automation
Artificial Intelligence (AI) and Machine Learning (ML): Both AI and ML enhance human analysts by freeing them from repetitive work, processing large amounts of security data, and finding patterns that suggest a cyber threat. SOC teams can invest their time and efforts toward higher-level strategy and incidents.
Automated alert correlation applies machine learning algorithms to discover connections among security events across a variety of systems, and temporal frames of reference. In reviewing repetitive, structural alerts that still demand cognitive attention, algorithms detect minor patterns not always considered by human analysts processing thousands of alerts each day, leading to more accurate detection and reduced time spent in analysis.
Threat Classification Automation: Applies natural language processing and behavioural analysis to classify security threats automatically by severity and type of attack, enabling a faster threat triage process while improving consistency in resource allocation.
Response Automation: Performs automated containment actions of the network for example, isolation, account disabling, or quarantining the malware based on the severity of the threat, enabling a faster response time to threats than the manual response time.
False Positive Reduction: Finds patterns and correlations from analyzing analyst decisions and threat intelligence through machine learning algorithms, reducing activities time wasted on investigating alerts.
Predictive Analytics: Data provides visibility across a broad spectrum of cloud workloads, containerized applications, and remote access infrastructures that SOC tools fall short of providing.
Extended Detection and Response (XDR)
XDR Platforms: Combines all security data from endpoints, network, cloud infrastructure, email systems, and identity platforms into one collective view. This allows for correlation across all security platforms, demonstrating complete attack timelines and improving responses to attacks by enabling faster coordination.
Unified Data Correlation: Automatically correlates endpoint alerts with network traffic anomalies and cloud access habits to expose the attack path from one system to another.
Cross-Platform Response: Allows actions to occur on all security tools simultaneously, isolating endpoints that may be compromised, blocking malicious traffic, and disabling accounts that may have been compromised, all in the same coordinated response.
Attack Surface Visibility: Data provides visibility across a broad spectrum of cloud workloads, containerized applications, and remote access infrastructures that SOC tools fall short of providing.
Threat Hunting Enhancement: Allows hunters to unify data access across all technology domains while lowering the complexity of tools used, leading to better security investigations and recommendations.
Cloud-Native SOCs
Cloud-Native SOC Platforms: Service-based security capabilities enable scalable cloud computing and managed security services as an alternative to the traditional SOC model with regard to flexibility and cost-effectiveness, whilst scaling operationally according to business requirements.
Elastic Scaling: Automatically adjusts computational resources based on the volumes of security events. This capacity allows organizations to effectively handle spikes in traffic when security events occur, without the hassle of investing in additional or excessive infrastructure.
Serverless Security Functions: Enable you to manage and process security events and automatic responses in the cloud without a dedicated server, drastically lowering operational overhead and scaling seamlessly as needed.
Global Accessibility: Enables security analysts and staff to conduct work on security operations center services from anywhere, supporting flexible work arrangements for both employees and freelancers, while certainly still meeting expectations for security.
Cost Optimization: Enables security to be inherently based on consumption, thus higher security costs can be scaled as required, and provide predictable monthly expenses instead of fixed infrastructure commitments.
Autonomous SOCs for Real-Time Defense
Autonomous Security Operations: Future Security Operations Center (SOC) capabilities will automatically detect, analyze, and respond to routine threats while escalating any complex incidents to human experts.
Autonomous Threat Detection: Leverages a combination of artificial intelligence (AI), behavioural analysis, and threat intelligence to automatically detect security incidents with high confidence and to differentiate between legitimate business activity and malicious behaviours.
Self-Healing Security Systems: Automatically take containment measures, apply security patches, and reconfigure security controls related to the threat detected while keeping detailed audit logs for human review.
Continuous Learning: Improve detection accuracy and response effectiveness by automatically analyzing incident outcomes and updating the system's detection and response behaviour based on new techniques used by the attacker.
Human-Machine Collaboration: Provides security analysts AI-based insights and recommended actions while keeping human review on high-level strategic decisions and complex analysis activities.
Fail-Safe Mechanisms: Ensure autonomous systems only operate within established parameters, with the ability to elevate unusual situations to human review before taking disruptive or overly aggressive action.
Conclusion
Due to ongoing advancements in the sophistication of cyber threats, a Security Operations Center (SOC) is a necessity for organizations today. SOCs represent a consolidation of technology, with cutting-edge tools such as SIEM, AI, and automation; security analysts equipped with the right processes and procedures; continuous monitoring; prompt threat detection; and prepared response when incidents occur to protect the digital assets of organizations. Whether you choose to build an in-house SOC, choose an outsourced MSSP, or a hybrid of both, developing mature SOC capabilities can reduce the impact of breaches, ensure regulatory compliance, and maintain stakeholder confidence in a threat landscape. Unchecked identities create visibility gaps in your security operations; orphaned accounts, privilege creep, and manual access reviews create easy entry points for attackers and slow your SOC team's response time.
At Tech Prescient, our Identity Confluence platform automates identity governance and access management, eliminating risky entitlements while providing your SOC with real-time identity intelligence for faster threat detection and incident response.
See how Identity Confluence strengthens your SOC while reducing identity-related security risks.
Frequently Asked Questions (FAQs)
1. What does SOC stand for in cybersecurity?
SOC stands for Security Operations Center, a centralized facility that houses cybersecurity teams, technologies, and processes for continuous monitoring and incident response. A SOC combines skilled security professionals, advanced technologies like SIEM platforms and threat intelligence feeds, and standardized processes to detect, analyze, and respond to cybersecurity threats across an organization's IT infrastructure, reducing the time between threat detection and response to minimize potential damage from cyberattacks.2. What is the role of a SOC analyst?
SOC analysts monitor security systems, investigate potential threats, and coordinate incident response activities to protect organizational assets.They work in tiered structures: Tier 1 analysts handle initial alert triage and basic incident documentation; Tier 2 analysts perform in-depth incident investigation, malware analysis, and response coordination; Tier 3 analysts conduct advanced threat hunting, develop custom detection capabilities, and contribute to security architecture planning, with career progression involving specialization in areas like digital forensics, threat intelligence, or incident response management.
3. Is SOC the same as SIEM?
SOC and SIEM are complementary but different: SIEM (Security Information and Event Management) is a technology platform that aggregates and analyzes security data, while a SOC encompasses the entire security operations function including people, processes, and multiple technologies. SIEM provides the analytical engine with log collection, event correlation, and automated alerts, but SOCs add skilled analysts, standardized procedures, and management oversight along with additional tools like EDR, threat intelligence feeds, and security orchestration platforms to transform technological capabilities into effective security operations.4. Why is a SOC important for businesses?
SOC capabilities address fundamental business risks from cybersecurity threats that can disrupt operations and damage reputation. Key benefits include: Risk Mitigation through rapid threat detection and incident response that prevents major damage; Operational Continuity by identifying threats to critical systems quickly; Regulatory Compliance with frameworks like GDPR, HIPAA, and PCI DSS through continuous monitoring and documentation; Cost Effectiveness by reducing breach costs through faster detection; and Stakeholder Trust by demonstrating security maturity that supports customer confidence and positive investor relations.5. Is SOC a blue team?
SOC operations fundamentally represent blue team activities in cybersecurity terminology, focusing on defensive security measures, including threat detection, incident response, and security control implementation. SOC blue team activities include continuous monitoring using SIEM platforms and endpoint detection systems, structured incident response procedures, proactive threat hunting, vulnerability management, and security architecture design. Contrast with red team activities that simulate attacker behaviours and purple team approaches that combine offensive and defensive perspectives for comprehensive security testing.



