
What is Attribute-Based Access Control (ABAC)?

In today's distributed cloud-based world, static access control models like Role-Based Access Control (RBAC) often fail. Roles alone are insufficient to express the complexity of modern work environments, where users access resources on multiple device types, in multiple locations, and in multiple contexts; roles lead to either overly broad permissions that expose excessive security risk or restrictive roles that drive extreme productivity inefficiencies.
Attribute-Based Access Control (ABAC) fills this gap by granting access based on a combination of attributes about the user, the resource, the action, and the context. Organizations can implement fine-grained, context-aware security policies that can scale across numerous systems and user situations.
ABAC is a common technique used in complex, high-stakes situations such as cloud infrastructure, governmental systems, or healthcare. In these instances, primarily, static roles do not account for the variety of factors that underlie how access should be granted. Instead, it grants access with multiple attributes, including user metadata, authentication mechanism, device posture, and situation context. This helps ensure that the right people get the right level of access at the right time.
In this blog, we will take a look at how ABAC works, its comparison with RBAC and PBAC, benefits and challenges, use cases, and best practices. We’ll discuss everything you need to know about whether ABAC is a good fit for your organization’s identity and access management strategy.
Key Takeaways:
- ABAC is a dynamic, context-aware access control model that relies on attributes rather than static roles to define permissions.
- It provides fine-grained policy enforcement, which is most applicable in high-complexity situations such as cloud computing, healthcare, and government.
- Compared to RBAC, ABAC provides more flexibility and scalability while also aligning to modern Zero Trust security practices.
- A successful implementation of ABAC will require clearly defined attributes, accurate, reliable data, and possibly integration to IAM/IGA.
How Does Attribute-Based Access Control (ABAC) Work?
Attribute-Based Access Control (ABAC) grants or denies access based on the evaluation of many attributes about the user, resource, action, or environment against prescribed security policies. ABAC operates differently from role-based models, which are more static. It dynamically adjusts to changes in real time, making it ideal for complex or dynamic environments.
Here is how it works:
1. Understand the Four Attribute Types
ABAC decisions are based on the combination of four fundamental categories:
1. Subject (User Attributes): Who is making the request?
This could include their name, role, department, level of security clearance, type of employee, or even the identity of their device. This information is typically fetched from HR Systems or from auth tokens used during the login process. Example: John Smith, Finance Manager, Clearance Level 3, corporate laptop.
2. Resource (Object Attributes): What is being requested?
Each file, database, or application has its own attributes such as data classification (public, internal, confidential), owner, creation date, or sensitivity level. Example: A loan document marked "Confidential - Finance Department Only."
3. Action: What does the user want to do?
This is the specific action, such as view, download, edit, delete, or share, that the user wants to do. Actions can have multiple attributes. Example: John wants to "download" the file.
4. Environment: What context is the access requested in?
The environment is the global context within each access request. Contextual attributes such as time of day, network type, location, IP address, or device compliance status. Contextual information can be made up of risk signals that an organization has defined, like authentication strength and the subject’s expected behavior. Example: Request made at 9:45 am, from the corporate VPN, in the office network.
2. Policy Creation and Structure
The key aspect of ABAC is its policies - rule sets that explain who can access what, using which method, and under what conditions. You can think about these policies as precise "if-then" statements that check attributes of the subject, resource, action, and environment, and make an access decision.
A simple example of a policy might be: If Department = Finance AND Clearance Level ≥ 3 AND Time = Business Hours AND Location = Corporate Network THEN Access Granted
Key Aspects of Attribute-Based Access Control Policies:
- Logical rules: Policies generally combine multiple conditions using Boolean logic (AND, OR, NOT). This ability allows organizations to create complex rules, such as granting access to three departments only if employees are using an approved device to do a transaction at a specified location.
- Fine-grained condition: Policies can evaluate other conditions beyond role or department. It can evaluate contextual checks like device compliance, encryption level, and transaction amount.
- Resemblance to natural language: Policies look and behave like human-readable statements, making them easier for administrators to change and inspect. Organizations can modify the policies without relying on external programming skills.
- Scalability: A single policy can address multiple scenarios dynamically, by referencing attributes in policies in those contexts. Instead of hundreds of separate access rules, organizations can rely on fewer policies.
3. Real-Time Evaluation Process
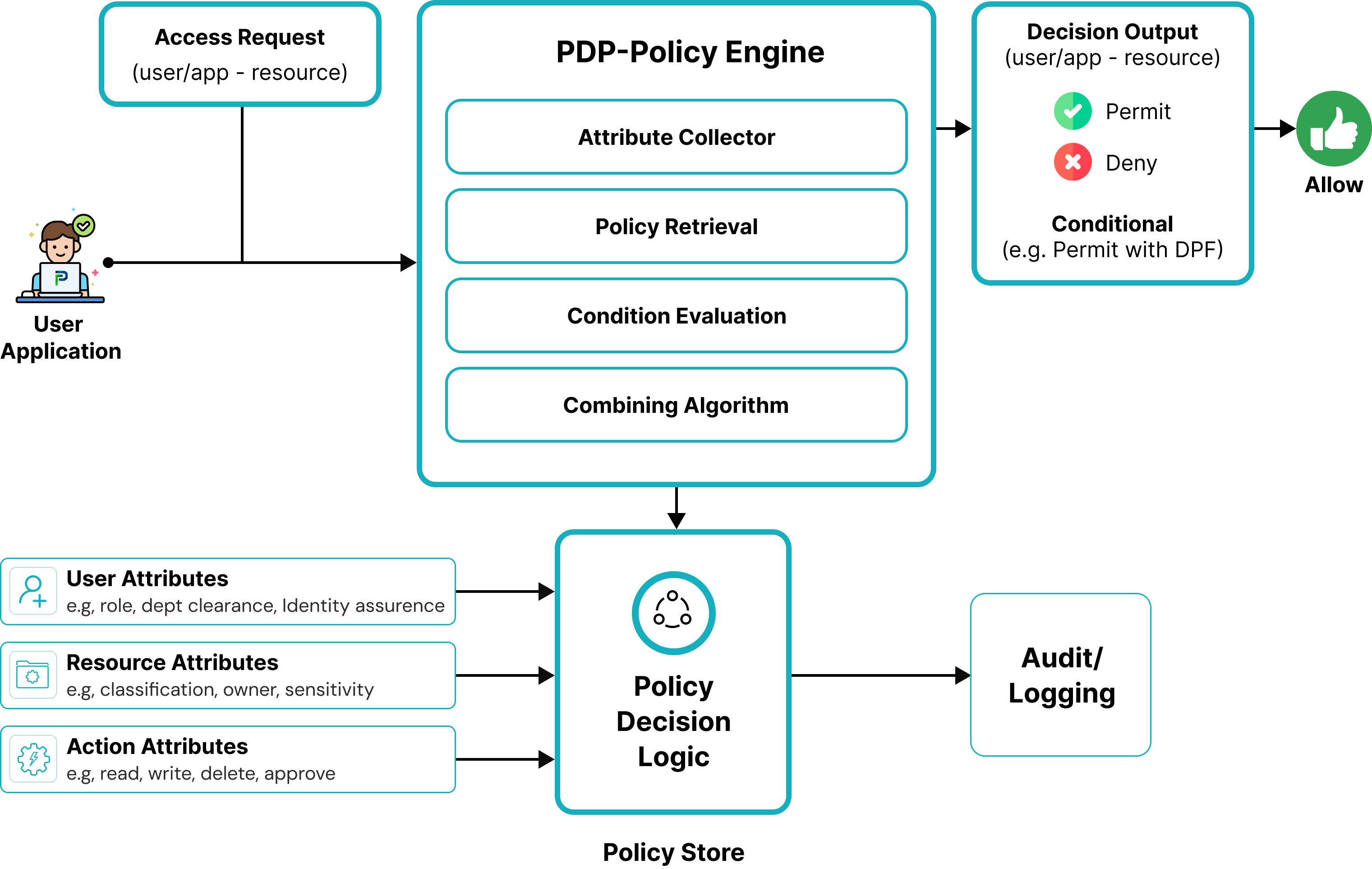
When a principal attempts to access a resource, ABAC takes a defined process to make an on-demand decision:
- Attribute Collection The ABAC system collects the relevant attributes that officially matter, in real-time, from a number of different attribute sources.
- Identity providers (e.g., Azure AD, Okta) for user and group attributes.
- HR systems for department, manager, job title, or employment type.
- Device management systems (e.g., Intune, Jamf), for device health, encryption status, and owner type.
- Application metadata for resource sensitivity, classification.
- Security tools for risk scores, geolocation, or anomalous behavior.
- Policy Matching
- The ABAC policy engine checks the attributes against the policy set.
- This matching process applies the Boolean logic and comparison operators that are defined in each policy.
- If policies were returned or matched by the engine, the ABAC engine will use the pre-defined decision-combining algorithms, such as “deny overrides” or “permit overrides,” to arrive at a final decision.
- Decision and Enforcement
- If the attributes match all the conditions, access will be granted instantly.
- If any attribute does not meet the defined policy criteria, access will be denied.
- This system will usually log a decision-making record that can be used for auditing, logging the matched vs. non-matched status of which attributes matched or did not match. This is valuable in terms of reliability, either for compliance seat work or to facilitate investigation when users feel their access is being unduly restricted.
Since these operations occur in milliseconds, ABAC can update the user context in real time. For example:
- A device going out of compliance while in session can instantly terminate the session.
- A role change in HR data can instantly revoke or change access rights without any manual intervention.
ABAC vs RBAC vs PBAC: What’s the Difference?
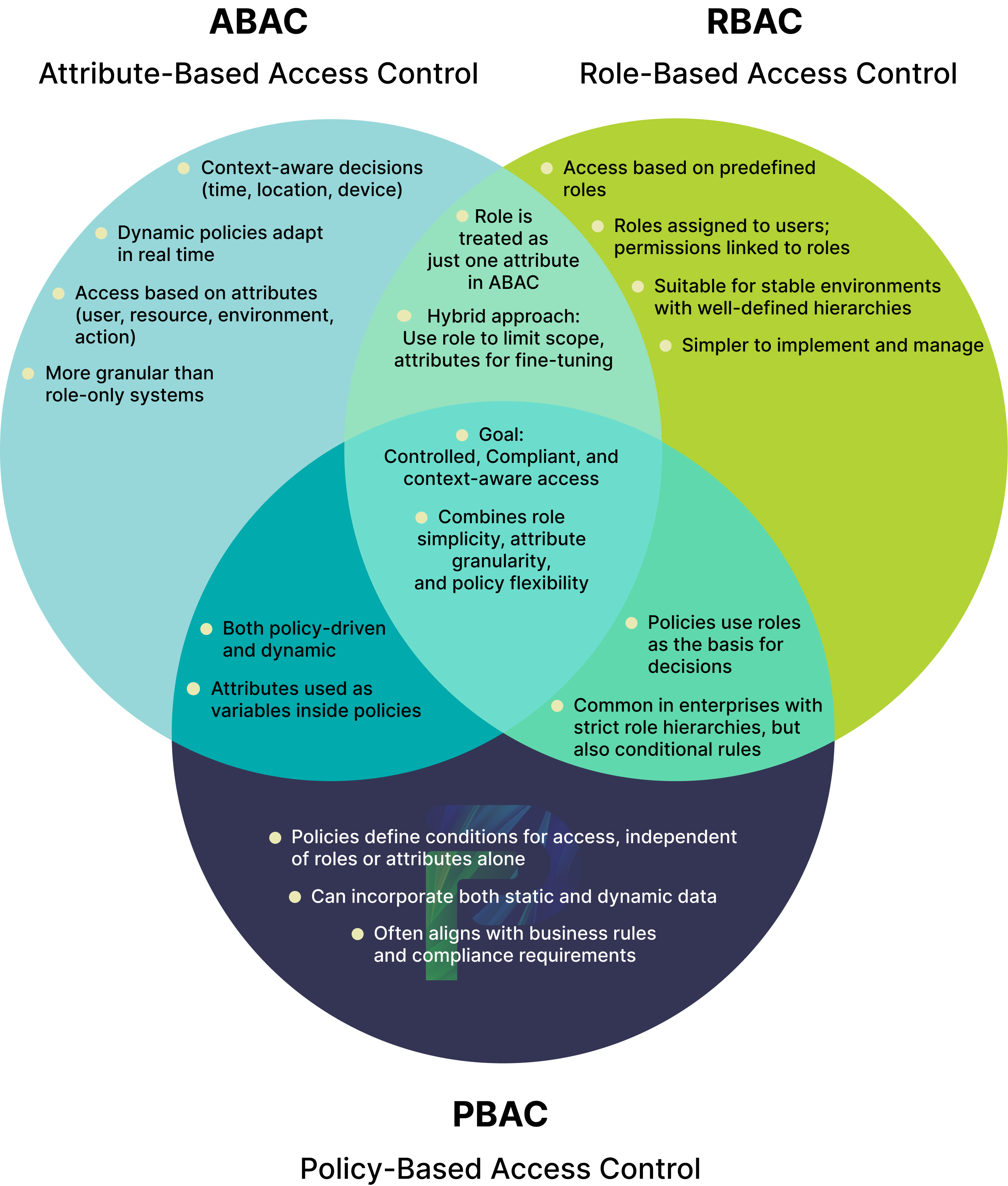
Access control modes serve a singular purpose: ensuring that the right individuals have the right access at the right time. Each model goes about achieving this goal differently, three of which include ABAC (Attribute-Based Access Control), PBAC (Policy-Based Access Control), and RBAC (Role-Based Access Control).
How They Work At a High Level
1. RBAC (Role-Based Access Control):
RBAC is based on pre-defined roles, each with a set of authorization permissions. Anyone assigned to the role of Finance Analyst would have the same access permissions as everyone in the role of Finance Analyst. If your role is Finance Analyst, you have all the permissions associated with that role, no more or no less. While this could be simple to manage, it is static. If your access needs change, you would have to remove your access to the current role and assign or create a new role that meets your access needs, which can lead to a "role explosion" in a large organization.
2. PBAC (Policy-Based Access Control):
PBAC is based on policies, where the policy establishes a set of rules to determine what access is authorized or not. PBAC can use a combination of attributes (e.g., department, device type, clearance level, etc.) to determine what the authorization decision will be. PBAC is powerful because of policy logic, which specifies how the policies will work together. The key benefit of PBAC is that the decisions made by the policy logic are decoupled from any metadata files, which allows organizations to modify access rules without disrupting the business function of an application or other resources. For these reasons, PBAC is more flexible than static-based models, like role-based models.
3. ABAC (Attribute-Based Access Control):
In contrast, ABAC takes what PBAC does and builds on it by accessing dynamic qualities about the user, resource, action, and environment. Access decisions in ABAC involve every attribute about the user, resource, action, and environment data points in real time against policies. This gives the organization granular control because the decision-making, or context, changes instantly.
| Feature / Model | RBAC | PBAC | ABAC |
|---|---|---|---|
| Primary Basis for Decisions | Uses predefined roles, each granting the same set of permissions to all assigned users. | Sets of specific policies that determine relevant attributes and permissions. | Dynamic attributes of subject, resource, action, and environment. |
| Flexibility | Is low. Roles must be pre-defined. | Is medium. Policies can reference conditions. | Is high. Policies reference dynamic attributes. |
| Granularity | Coarse-grained | Medium-grained | Fine-grained |
| Context Awareness | New roles can be defined for each new context of permissions needed. | Attribute sets can be tailored for every new permission scenario. | Policies can be created to adjust attributes dynamically for each unique access context. |
| Scalability | May cause role explosion as more roles are needed for different access needs. | More scalable than RBAC, with fewer roles required. | Highly scalable, avoids role explosion entirely. |
| Typical Use Cases | Small/medium orgs with stable roles | Regulated industries need policy oversight | Enterprises needing adaptive, risk-based access |
| Cost to implement and maintain | Relatively inexpensive, as it can be managed by a small IT team | Implementation can be expensive, but easy to maintain | Expensive because a large IT team is required to maintain |
| Ease of compliance | Compliance is difficult to ensure. | High compliance as it has an easy-to-use GUI, and the policy-based structure enables direct permission setting. | Strong compliance support with granular control and audit trails. |
| Ease of modification | Easy to define new roles or revoke certain accesses for a given role. | Relatively easier, as new policies can be defined using high-level policy language. | Attributes and policies can be updated quickly without restructuring roles. |
| Example | Adding a new role for remote workers. | Change weekend access hours via policy update. | Instantly block access if a device is non-compliant. |
How Are They Used Differently?
When RBAC is Most Effective:
- Organizations that have clearly defined and stable job roles.
- Environments where access needs rarely change.
- For Example, A small accounting firm where all the accountants have the same access rights.
When PBAC is Most Effective:
- Organizations that require rules beyond jobs (e.g., access only during business hours).
- Compliance-driven industries that outline specific policies.
- For example, a healthcare system allows doctors access to patient records only for patients they are currently treating.
When ABAC is Most Effective:
- Large changing environments with frequent user movement and complex access scenarios.
- Organizations implementing a Zero Trust security strategy where device and access are verified on each request.
- For example, a global enterprise allows access to sensitive design files only if the user is in the Engineering department, is using a company laptop, and is connecting from an approved country.
Why is ABAC Considered the Evolution of RBAC?
Role-Based Access Control represented a meaningful progression from assigning permissions manually; it freed administrators from some burdens. However, RBAC does not promote fluidity and change, and as such, roles can become static. This leads to the issue of "role explosion," in which organizations typically have to manage hundreds of roles.
Policy-Based Access Control was introduced to add flexibility by allowing decisions to be made on rules rather than predefined conditions; however, PBAC, in practice, often still incorporates conditions that do not make use of real-time context.
Attribute-Based Access Control builds on both RBAC and PBAC elements by leveraging attribute-based policies that are dynamic, rather than static roles or a properly defined rule. This means that decisions around permissions do not just take identity into account, but also location, device, action, and current conditions, which affords much more flexibility and security.
Key Benefits of Attribute-Based Access Control
The main advantage of Attribute-Based Access Control (ABAC) is that it exceeds static role-based permissions by considering who the user is, what they are trying to access, and what circumstances are in play. ABAC offers a current, dynamic approach to access control by truly considering the variables at play. Here are some of the reasons ABAC is just so powerful as a model today:
1. Granular Policy Enforcement
ABAC allows for fine-grained control over access decisions, as you can enforce policies with very specific conditions. For example, you could allow a financial analyst to access budget reports only if the data classification is classified as internal, the document has not been modified in the last 24 hours, and the analyst is connecting from a corporate device.
This degree of precision ensures:
- Reduced risk by depriving unnecessary over-permissioning.
- Enhanced compliance with data protection regulations that require tighter controls around sensitive data handling.
- Customized user access so employees are only seeing exactly what they need to see and nothing more.
2. Dynamic and Context-Aware Decisions
ABAC policies can respond to all aspects of the context of the request in real time, unlike static access models. Environmental attributes can also determine if access is granted or denied. Environmental attributes can include time (the time of the day), location (geographic location), network status (the security/integrity or confidence level of the network), or even COVID Status or device health directly affects access, for example:
- A sales executive may access the CRM from the office, but they may be blocked when logging in from an untrusted public Wi-Fi source.
- A clinician may be able to open patient records during their scheduled shift, but they could lose access immediately after their scheduled shift ends.
These context-aware models drastically reduce the attack surface and help thwart credential theft, insider threats, and compromised devices.
3. Scalability for Large Organizations
In complex environments like large healthcare networks, multinational corporations, and government agencies, the manual or fixed role management for access is quickly going to become untenable. ABAC gives:
- An opportunity to use the policies across multiple platforms, without duplicate role structures,
- Centralized policy management means that changes can be rolled out instantly across the enterprise,
- Support for hybrid and multi-cloud infrastructures in that attributes can be keyed off of non-standard systems like HR systems, IAM software, or device posture checkers.
This scalability represents actual ABAC in that the ABAC solution should not tie down IT teams in a world of constant role maintenance for thousands (or millions) of users, devices, and application access.
Challenges and Considerations
Although Attribute-Based Access Control provides unparalleled flexibility and control, it is not without its challenges. Organizations often underestimate the work required to create policies, find attributes, and maintain the accuracy of those attributes over time. Here are two of the most prevalent challenges to watch for.
1. Complex Implementation
ABAC is not a simple plug-and-play model. Its strength is in complicated, contextual decisions that require well-thought-out policies and reliable source attributes. To implement ABAC appropriately, you will have to:
- Determine and source attributes from various sources such as an HR database, IAM directories, device posture scan tools, and application metadata.
- Create policies that map properly to business rules but can still be maintained and investigated easily. Using complex "if-then" statements can cause a policy explosion and result in unwanted access blocks.
- Integrate into any existing infrastructure, which may involve designing connectors, APIs, or application middleware to provide ABAC with attributes in the right place at the right time.
Without a concrete implementation plan, ABAC has the potential to be cumbersome and difficult to update, particularly for large enterprises that utilize disorganized and disparate data systems.
2. Attribute Trust and Accuracy
The effectiveness of ABAC decisions hinges on data quality. If those attributes are obsolete, incorrect, or missing, access decisions will be compromised, which may inadvertently lock out a legitimate user or allow the wrong people in.
Key considerations include:
- The need for real-time updates to ensure attributes are current snapshots of the user, device, and environmental context.
- The ability to validate the attributes at some level to ensure that they are authoritative or have some sort of rigor to ensure that the same data is being reported across the functional areas.
- The need to secure the attribute data from corruption. If an attribute store were attacked, the attacker could influence access decisions if they were able to tamper with the attribute data.
Understanding attribute governance, like what the ownership of attributes is, how frequently they will be updated, and what workflow will be used to govern validation, will help make ABAC a mechanism that is both trusted and secure.
Attribute-Based Access Control in Real-World Use Cases
Apart from true contextual access control, Attribute-Based Access Control introduces a level of precision that is far beyond what any traditional model, such as RBAC, can accomplish at scale. By factoring multiple subject, resource, action, and environmental attributes, organizations are better able to apply real-world factors to access decisions. Let's see how this manifests in various industries.
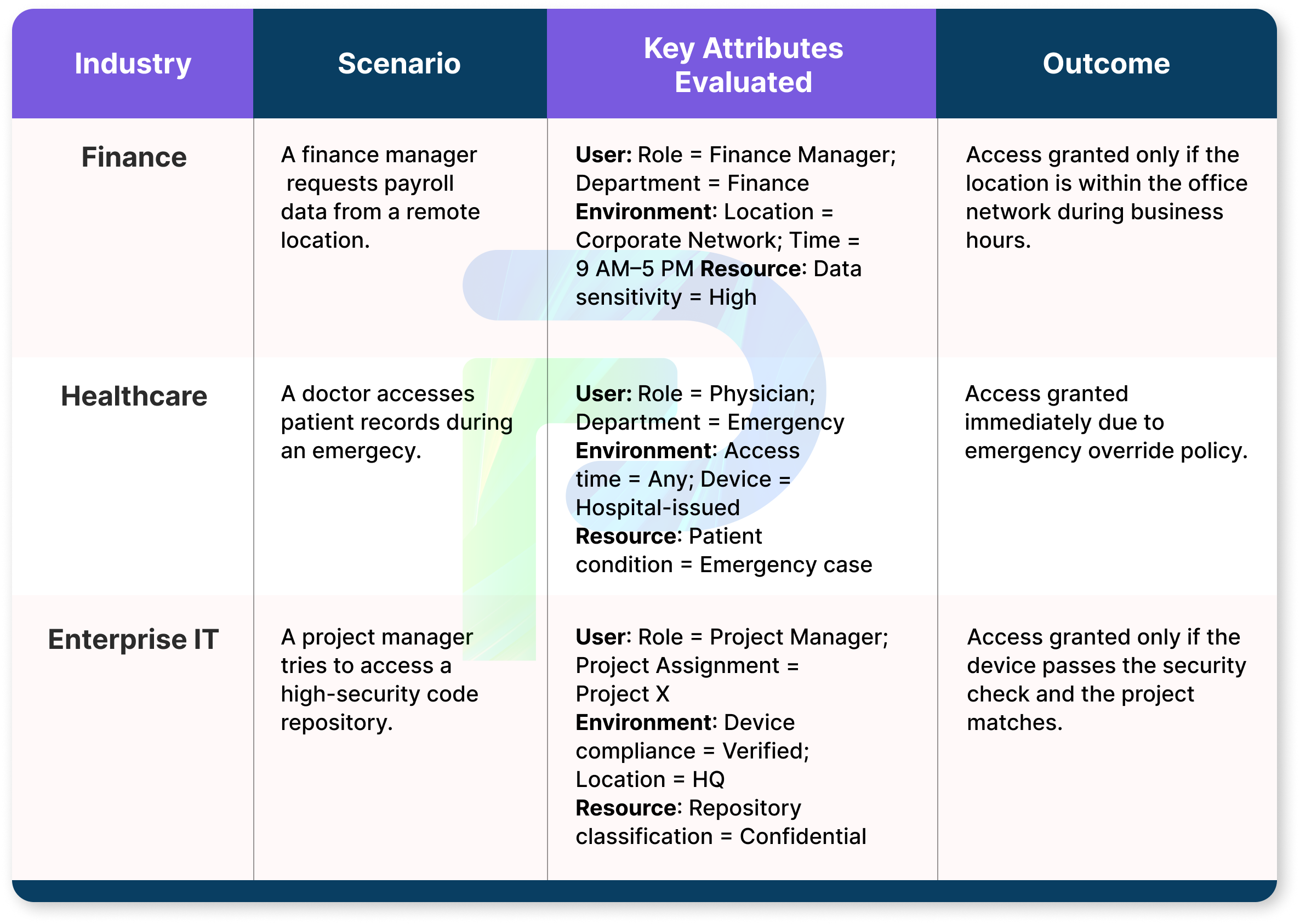
Healthcare:
In healthcare, compliance with privacy regulations (e.g., HIPAA) requires strict patient privacy while still permitting quick and unencumbered access by approved providers at the time of care.
- Subject attributes: role (doctor, nurse, admin staff), area of care (e.g., cardiology, oncology), employment status.
- Resource attributes: record type (inpatient, outpatient), patient relationship, data sensitivity (confidential, sensitive, etc).
- Environmental attributes: (e.g., controlled (hospital site) or uncontrolled environment, after shift is over, device compliance, e.g., smartphones, laptops, tablets) where the security is less than the hospital.
Example: A cardiologist is currently working in the hospital and is permitted to view and edit ECG results of patients for whom they are the direct care provider, and is prohibited from accessing records of patients from departments to which they have no relationship, and when they have exceeded their employment shift. It protects against snooping of unauthorized hospital patients while providing critical user-context-sensitive access to authorized medical professionals for on-duty medical care.
Cloud SaaS:
ABAC provides organizations with the flexibility to manage fluid project teams in cloud-based file-sharing applications without needing to change permissions manually.
- Subject attributes: which project role (e.g., manager, contributor), the employer, and security clearance.
- Resource attributes: file ownership, stage in the project lifecycle (in-progress, archived), and classification (e.g., public, confidential).
- Environmental attributes: the network from which access is being made (e.g., corporate VPN or Public Wi-Fi), and the method of access (e.g., desktop app or browser).
Example: A contractor may be able to upload and edit files for a project while the project is “active.” Once the project has been archived in the project management tool, the contractor is automatically only able to access files in a read-only state. No manual updates are required; the access changes occur almost instantly because of the attribute changes.
Government:
Government entities function in a regulated security setting, typically with many layers of clearance and context checks before access is granted.
- Subject attributes: Clearance level, agency, and mission assignment.
- Resource attributes: Classification level (confidential, secret, top secret), source, and ownership.
- Environmental attributes: Time periods, location (secure facility), and device credentialing.
Example: An intelligence analyst with “Secret” clearance can access classified mission briefings only while physically in a secure government facility and during their scheduled working day. Even if a user is validated as having valid clearance, access will be denied to an analyst if their request is coming from a device that is not secure, or from the analyst outside of approved time periods.
Implementing Attribute-Based Access Control in Your Organization
Transitioning to ABAC is more than simply a technology change; it is a methodical transition utilizing clearly stated attributes, organized policies, and the integration into the identity and governance stack of your organization.
Step 1: Define and Structure Attributes
Your first step is to create a clear attribute inventory. An attribute inventory is a list of attributes you will need for subjects, resources, actions, and environments.
- Subject attributes should include job role, department, clearance level, group memberships.
- Resource attributes should include file type, data classification, owner.
- Action attributes should include read, write, approve, delete.
- Environmental attributes should include time of access, location, device posture.
To be precise and consistent, you should standardize naming conventions, for example, using “Dept_Finance” vs. “Finance” and regularly syncing attributes from sources of record or authority, such as HR systems, Active Directory, or asset management systems.
Step 2: Build and Test Access Policies
Once you have established your attribute, define your business needs through policies that can be implemented using Boolean logic.
- Example: If Department = Finance AND Clearance ≥ 3 AND Device = compliant → Permit Access.
- Group related policies together (example: "HR policies", "Finance policies") to simplify maintenance.
- Establish a testing environment to verify your policies that will ensure that policies behave as intended, including allowing legitimate access and blocking unauthorized access attempts.
Utilize an ongoing review process and update policies to accommodate changes in users, activities, and regulatory requirements.
Step 3: Integrate with IAM/IGA Systems
For ABAC to achieve its full potential, it needs to integrate with your identity governance and administration (IGA) or identity and access management (IAM) systems.
- IAM platforms provide authentication and real-time identity attributes.
- IGA tools such as SailPoint provide attribute quality, compliance, and central control for access governance.
When you can integrate ABAC to these platforms, you can automate the updates to attributes, immediately enforce policy changes, and retain a complete audit trail for compliance reports.
Final Thoughts
Today’s environments are hybrid, multi-cloud, and compliance-heavy. Relying on static access rules can become a pitfall for organizations in a rapidly evolving context. ABAC provides your organization with the flexibility and intelligence needed to mitigate risk without compromising security or user productivity.
Using real-time attributes across users, resources, and environments allows ABAC to provide organizations with precise and context-aware access decisions. The model requires thoughtfulness in terms of attribute management and policy design, but the benefit is a security model that can scale your business and respond to changing threats.
And because of this, you are closing security gaps, decreasing insider risk, and enabling access for your teams, at the right time and for the right services, without burying your admins in manual requests.
NEXT STEPS
Identity Confluence makes implementing ABAC simple, giving you fine-grained, context-aware access control without the complexity. Our platform unifies policy management, automates attribute sourcing, and integrates seamlessly with your existing IAM and IGA systems.
Learn more about Identity Confluence → Explore now
Frequently Asked Questions (FAQs)
1. What is attribute-based access control in simple terms?
Attribute-Based Access Control (ABAC) is an access control model where access control decision-making is based on evaluating specific attributes, or characteristics, of the user, resource, action, and environment. Instead of discrete roles, ABAC performs real-time checks of attributes against defined policies to determine whether to either permit or deny access.2. How is ABAC different from RBAC?
Role-Based Access Control (RBAC) is a method of granting permissions based on predefined roles; these roles don't frequently change. On the contrary, ABAC evaluates dynamic attributes like the department of the user, classification of the data, time of day, or geographic location from which the user is accessing. ABAC is more flexible and aware of context. This allows for more finely-grained and precise access decisions.3. What are examples of ABAC in action?
In healthcare, for example, a nurse may only be able to access a patient’s record if they are on duty, assigned to that patient, and accessing the electronic health record through a hospital-secured device. In finance, a trader may only be permitted to create transactions during market hours and from approved locations. These requirements are evaluated and enforced in real-time through ABAC policies.4. Is ABAC better than RBAC?
ABAC allows for more granular control and is likely more applicable to larger, more complex, heavily regulated environments where context is important. In comparison, RBAC can be much easier to manage and is usually enough for smaller organizations with simpler access needs. As most organizations do, both models are typically used together as a hybrid model.5. What does PBAC mean in access control?
Policy-Based Access Control (PBAC) emphasizes writing explicit access rules in the form of policies, typically in logical statements like "if condition A and condition B, then grant access." PBAC can leverage attributes similar to ABAC, but how the policies are defined makes it more oriented on the policy, which is similar but not always the same as ABAC6. Is PBAC the same as ABAC?
Policy-based access control (PBAC) and attribute-based access control (ABAC) are both types of access control frameworks that use attributes to determine authorization policies. However, with PBAC, you can write policies in a high-level policy language to direct the authorization engine on what to do in a specific circumstance. With ABAC, typically, you not only need to tell the authorization engine what to do but also how to do it.7. What are the 3 rules of RBAC?
The three rules associated with RBAC are:- Role assignments: A user is assigned a role.
- Role authorization: The role assigned to a user must be authorized. Users cannot assign roles to themselves.
- Permission authorization: A user can only exercise the permissions assigned to their role.




