
Authentication vs Authorization: What’s the Difference and Why It Matters in Cybersecurity

Authentication and authorization are sometimes misunderstood, yet they perform two separate functions in cybersecurity. Authentication verifies that a user is genuinely who they claim to be, while authorization determines the level of access or actions that the verified user is allowed to perform. Think of it like entering a secure building: first, you prove your identity to get through the door, and then your access card decides which rooms you can actually enter. Together, these two processes form the foundation of identity and access management and play a critical role in ensuring secure and controlled access across systems.
Consider authentication to be the process of opening a door with a key, and authorization to be the process of determining which rooms you may access once inside. From app signing to cloud access, both methods ensure that only the appropriate individuals have the appropriate level of access at the right time. Without this equilibrium, systems remain vulnerable to identity theft and data breaches.
According to a report published by Identity Defined Security Alliance's in 2024, 90 percent of enterprises have had at least one identity-related incident in the previous year. Strengthening authentication and authorization is thus more than simply good practice; it is critical protection. Let's look at how these two security pillars collaborate to protect digital identities and access in today's Zero Trust scenario.
Key Takeaways:
- Authentication verifies user identity, while authorization determines their access rights.
- Modern authentication uses methods like MFA, biometrics, and passwordless login for stronger identity proofing.
- Authorization relies on models like RBAC and ABAC to manage permissions based on roles and policies.
- IAM and IGA solutions unify authentication and authorization using protocols such as OAuth 2.0, SAML, and OpenID Connect.
- In a Zero Trust framework, every access request is continuously authenticated and authorized to minimize security risks.
What Is Authentication?
Authentication is the process of confirming that a user is truly who they claim to be before granting access to a system, network, or application. It establishes trust between the user and the system and serves as the foundation of Identity and Access Management (IAM).
Authentication can be carried out in several ways, such as:
- Passwords and Usernames: The most widely used method, where users enter a recognized combination of credentials to prove identity.
- One-Time Passcodes (OTPs): Temporary codes provided for a single login session or transaction to ensure short-lived, secure access.
- Authenticator Applications: Apps that generate verification codes independently, adding another layer of trust.
- Biometric Verification: Physical characteristics like fingerprints, facial recognition, or iris scans are used to confirm identity.
In many environments, systems require more than one of these methods to be verified together. This approach, known as Multi-Factor Authentication (MFA), strengthens security by reducing reliance on a single credential type, such as passwords alone.
How Authentication Works
At its core, authentication requires users to provide one or more credentials, which serve as proof of identity. These credentials typically fall into three main categories:
- What you know: This refers to information that only the user should have access to. Examples include a password, passcode, personal identification number (PIN), date of birth, Social Security number, or other personally identifiable information (PII) that the system can validate against its stored records.
- What you have: This refers to a physical or digital item that the user possesses to prove their identity. This could be a key, keycard, key fob, swipe card, smart card, security token, or even a trusted mobile device that helps confirm access.
- Who you are: This category uses biometric traits such as a fingerprint, thumbprint, facial scan, voice pattern, hand geometry, or retina scan to verify identity. The biometric data must match the unique physical characteristic recorded when the user was originally enrolled in the system.
When a user presents these credentials, the system checks their validity. If they match the information stored during the user’s registration, access is granted and trust between the user and the system is established.
Types of Authentication
Different systems use varying levels of authentication strength depending on their security needs. These can include:
- Single-Factor Authentication (SFA): This method relies on just one credential, typically a username and password combination, to verify a user’s identity.
- Two-Factor Authentication (2FA): This adds an extra layer of security by requiring a second factor, such as a one-time code or biometric verification, in addition to the password.
- Multi-Factor Authentication (MFA): This approach uses two or more independent factors, such as a password, fingerprint, and one-time code, to provide stronger identity verification.
- Passwordless Authentication: This modern method removes the need for traditional passwords and instead uses secure alternatives like passkeys, hardware tokens, or mobile-based verification.
By combining multiple verification methods, organizations can significantly reduce the risk of unauthorized access and credential-based attacks.
Real-World Analogy
Think of authentication as showing your ID card to a security guard before entering a restricted area. The guard checks the ID to ensure that it matches your appearance and name. Only when the verification is successful are you allowed entry. In the digital world, authentication works the same way by validating your credentials before granting access to systems or data.
What Is Authorization?
Authorization in system security refers to assigning a user the rights or permissions needed to access particular resources or perform specific actions. It is commonly associated with access control and user privilege management.
For example, one user may be permitted to download specific files from a shared server, while another user may be granted administrative access to configure or manage an application. In every case, authorization occurs only after authentication. The system first verifies the user's identity and then determines what level of access that user should receive.
Understanding Authorization and Its Role
Authorization grants users permission to access certain digital or physical resources, such as documents, databases, applications, or systems. While it is often confused with authentication, the two serve distinct purposes and occur in sequence. A user must first be authenticated before the system can evaluate what privileges they have.
However, permission can mean different things depending on organizational policies. Just because a user passes authentication and logs in does not mean they automatically get access to everything within the application or platform. Specific permissions, such as viewing, editing, or downloading a file or deleting data, are defined by the organization to maintain security and data integrity.
These permissions and access levels are essential to prevent data exposure and misuse. For example:
- Prevent unauthorized access: A banking app allows a customer to view only their own account details, not every customer’s account.
- Restrict premium content: SaaS products and subscription services use permissions to limit free users from accessing paid or premium features.
- Separate internal and external access: Employees and customers may use the same system, but internal staff will have deeper access to data and configurations than external users.
When implemented correctly, authorization ensures that users can access only the information and functionality relevant to their roles, no more, no less.
Types of Authorization Models
Authorization can be managed in several ways depending on the organization’s size, complexity, and security needs. The most common models include:
1. Access Control List (ACL)
An ACL defines a static list of permissions tied directly to individual users. While simple to implement, it becomes hard to maintain at scale. In large environments with hundreds of users, updating or revoking permissions manually can lead to inefficiencies and security gaps.
2. Role-Based Access Control (RBAC)
In Role-Based Access Control (RBAC), permissions are linked to predefined roles rather than assigned directly to individual users. A role may represent a job function such as HR Manager or IT Administrator. When a user is associated with a role, the system checks the role’s defined permissions to determine whether the user is allowed to perform a specific action or access a particular resource. If the required permission is part of the role, access is granted; if not, it is denied.
RBAC is widely adopted because it simplifies permission management and aligns well with organizational hierarchies. However, it can face challenges such as "role explosion," where the number of roles grows excessively to accommodate edge cases or unique access needs, making the model more complex to maintain over time.
However, RBAC can suffer from role explosion, where the number of roles grows excessively to cover exceptions and specific cases, making administration cumbersome.
3. Attribute-Based Access Control (ABAC)
Attribute-based access control uses a more flexible and context-aware method of determining permissions. Instead of relying solely on predefined roles, ABAC evaluates a combination of attributes such as a user's department, job function, device type, location, time of request, and the sensitivity level of the resource being accessed. These attributes are then checked against a policy that defines the conditions under which access is allowed. This makes ABAC highly adaptable to dynamic environments where access decisions need to consider multiple real-time factors.
In ABAC, access decisions are evaluated at the time of the request rather than being tied to static permissions. The system checks attributes such as user role, department, device type, location, time of access, and the sensitivity of the resource against a defined policy. This evaluation is performed by a Policy Decision Point (PDP) within an Entitlement Management System (EMS), which centralizes and enforces authorization across all applications.
This model supports highly granular and context-aware rules. For example, a policy could specify that a user may only view records that belong to their own account. Because ABAC rules are centrally managed and reusable across systems, organizations can scale authorization more easily and maintain consistent access governance without configuring permissions separately in each application.
Why Authorization Matters
Setting the right permission levels is just as crucial as choosing the right authentication factors. Proper authorization ensures that:
- Sensitive data is shielded even if an account is compromised
- Employees have the right access to perform their jobs efficiently without unnecessary barriers
- Systems maintain separation between different user groups, reducing internal risks
Ultimately, authorization is about balance, providing users with enough access to be productive while minimizing security risks. It ensures that even in the event of a breach, damage remains contained because attackers cannot move beyond the limits of the compromised account.
Authentication vs Authorization: Side-by-Side Comparison
In cybersecurity, authentication and authorization are closely related yet serve entirely different purposes. Authentication focuses on verifying who a user is, while authorization determines what that verified user is allowed to do within a system. Together, they form the backbone of secure access control, protecting sensitive applications and data from unauthorized use.
To understand how these two processes differ and complement each other, the following comparison outlines their key functional, technical, and process-based distinctions. This side-by-side view clarifies their order, purpose, and how they work together in a typical access control workflow.
Comparison Table: Authentication vs Authorization
| Sr No. | Aspect | Authentication | Authorization |
|---|---|---|---|
| 1 | Purpose | Authentication verifies a user’s identity to ensure they are who they claim to be. | Authorization determines what actions a verified user can perform and what resources they can access. |
| 2 | Step in the process | Authentication always occurs first as it establishes the user’s identity. | Authorization follows authentication, as access can only be granted once identity is confirmed. |
| 3 | Basis of validation | Authentication is based on credentials such as passwords, one-time passwords (OTPs), or biometric data. | Authorization is based on user roles, privileges, and predefined security policies established by the organization. |
| 4 | Practical example | For example, when a user logs into a company’s system using valid credentials, they are completing the authentication step. | After authentication, the system determines whether the user can access specific files or applications; this is authorization. |
| 5 | Core question answered | Authentication answers the question, “Who are you?” | Authorization answers the question, “What are you allowed to do?” |
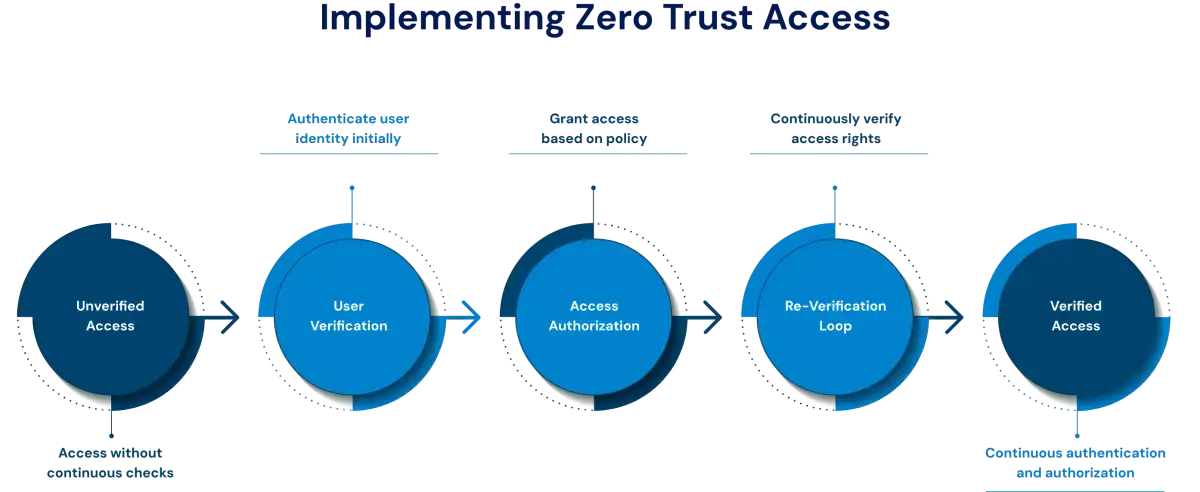
How Authentication and Authorization Work Together in IAM
Identity and Access Management (IAM) solutions combine authentication and authorization to enforce secure, policy-driven access across enterprise systems. Together, they ensure that only verified users can log in and that their actions and privileges remain aligned with organizational policies, compliance standards, and business needs.
How IAM Tools Implement Both Processes
Modern IAM platforms like Okta, Azure Active Directory (Azure AD), and Auth0 seamlessly combine authentication and authorization within a unified access management process. When a user initiates a login request, the platform first authenticates their identity by validating credentials or using multifactor verification. After successful authentication, the system enforces authorization policies, leveraging predefined roles, group memberships, and access rules to determine which applications, data, and systems the user is allowed to interact with.
This dual enforcement enables organizations to centralize access control, simplify user experience with Single Sign-On (SSO), and maintain consistent policy application across cloud and on-premises environments.
Integration with Identity Governance and Administration (IGA)
IAM solutions often work hand in hand with Identity Governance and Administration (IGA) systems to ensure continuous compliance and accountability. IGA adds layers of oversight such as access reviews, user provisioning and de-provisioning, and automated role assignments.
By integrating IAM and IGA, organizations can verify not only who is accessing resources, but also why and under what authorization context. This unified model strengthens compliance with frameworks like ISO 27001, GDPR, and SOX by providing clear visibility into how identities and entitlements are managed across the organization.
Common Protocols Supporting Authentication and Authorization
The seamless coordination between authentication and authorization in IAM is made possible by well-established industry protocols. Among the most widely used are OAuth 2.0, OpenID Connect (OIDC), and SAML.
1. OAuth 2.0
OAuth 2.0 is an open standard that defines a framework for delegated authorization. It allows applications to access protected resources on a user’s behalf without requiring the user’s credentials to be shared directly.
When a user attempts to access a resource, OAuth 2.0 issues access tokens that define what actions can be performed and on which resources. These tokens carry specific scopes and permissions that the resource server enforces. This model ensures that authorization is granular, secure, and centrally managed, which is ideal for environments where users and applications interact across multiple services.
2. OpenID Connect (OIDC)
OpenID Connect (OIDC) extends OAuth 2.0 by adding an authentication layer on top of its authorization framework. While OAuth 2.0 focuses on what a user is allowed to do, OIDC focuses on who the user is. During an authentication flow, OIDC issues an ID token that contains verified identity information such as the user’s name, email, and unique identifier. This token is digitally signed and can be trusted across multiple applications.
By combining OIDC for authentication and OAuth 2.0 for authorization, IAM solutions enable secure Single Sign-On (SSO) experiences where users can log in once and access multiple systems without repeated credential checks, while still maintaining strict access boundaries.
3. SAML (Security Assertion Markup Language)
A widely adopted federation and SSO protocol in enterprise IAM environments, it enables identity providers (IdPs) to transmit authentication assertions and user attributes to service providers (SPs). Since IAM solutions are responsible for both authentication and authorization, they typically support one or more such protocols to ensure seamless handling of identity verification and access permissions across connected systems.
How IAM Synchronizes Both Processes
In a standard IAM workflow, authentication and authorization function as sequential yet interdependent processes. Authentication verifies and establishes digital trust by validating a user’s identity, while authorization applies policy controls that assign roles, entitlements, or group-based permissions. Modern IAM platforms manage these processes through centralized policies and standardized tokens, enabling uniform access enforcement across enterprise systems. This integrated approach strengthens security posture and enhances user efficiency by providing seamless, auditable, and compliant access to resources.
Real-World Examples of Authentication and Authorization
In enterprise environments, authentication and authorization often work together behind the scenes to protect systems, applications, and sensitive data. The following real-world scenarios demonstrate how both processes operate in different sectors and use cases.
1. Corporate Systems: MFA Login and Controlled Admin Access
In a corporate IT environment, employees typically log in using multi-factor authentication (MFA) that verifies their identity through a combination of passwords, OTPs, or biometric checks. Once authenticated, the system applies authorization rules to determine access privileges. For instance, only administrators may access configuration settings, while other employees are restricted to user-level dashboards and tools.
2. Healthcare: Secure EMR Access Based on Roles
In healthcare institutions, authentication is required when medical professionals sign into Electronic Medical Record (EMR) systems. This step ensures that only verified personnel can access patient information. After authentication, authorization policies determine the scope of access. A nurse may only view patient files assigned to their department, while a doctor or specialist might have broader access based on their clinical role.
3. Finance: Token-Based Authentication with Approval Layers
Financial platforms often rely on token-based authentication to validate user sessions and reduce credential-related risks. Once authentication is complete, authorization controls govern transaction permissions. For example, routine transactions might be automatically approved for standard users, whereas high-value transfers require additional authorization from a senior manager or multi-party verification to maintain compliance and mitigate fraud.
4. Cloud Applications: OAuth and Role-Based Access Control
In cloud-based applications, users often authenticate through Single Sign-On (SSO) mechanisms powered by protocols like OAuth 2.0 or OpenID Connect. After the user’s identity is verified by a trusted identity provider, authorization comes into play through Role-Based Access Control (RBAC) or policy-driven models. This ensures that each user’s permissions align with their role, enabling secure and efficient access to SaaS resources and services.
Common Challenges & Best Practices
To maintain strong identity security, organizations must prevent weak authentication mechanisms, excessive permissions, and poor access governance. Achieving this balance requires robust policies, continuous monitoring, and the right IAM tools. While authentication and authorization strengthen enterprise security, both can fail without structured controls and consistent governance. The sections below highlight common challenges and the best practices to overcome them.
Common Challenges
Even with modern IAM systems, many organizations continue to face recurring issues that weaken their access control frameworks. These challenges usually stem from configuration errors, inconsistent policy enforcement, or a lack of visibility across systems.
1. Credential Theft: Stolen or compromised credentials remain one of the most common causes of data breaches. Attackers often exploit weak or reused passwords, phishing attempts, and unprotected login endpoints to gain unauthorized access.
2. Over-Permissioning: Employees and service accounts are frequently granted broader access than required for their roles. This over-privileged access increases the risk of insider threats, accidental data exposure, and non-compliance with security policies.
3. Inefficient Access Governance: Many organizations lack centralized visibility into user permissions and activity across systems. This leads to inactive or orphaned accounts, outdated privileges, and difficulty in maintaining compliance with regulatory standards.
Best Practices
To counter these challenges, organizations should adopt structured IAM strategies that integrate both authentication and authorization within a framework of continuous governance. The following best practices ensure a proactive approach to identity security.
1. Enforce Multi-Factor Authentication (MFA): Implement multi-factor authentication across all user accounts to enhance identity verification and reduce credential-based attacks. MFA combines two or more authentication factors such as passwords (something the user knows), one-time passcodes or hardware tokens (something the user has), and biometric verification like fingerprint or facial recognition (something the user is). Common MFA methods include SMS or email OTPs, authenticator apps, hardware security keys, and biometric scans. Using multiple factors makes it significantly harder for attackers to gain unauthorized access.
2. Apply the Principle of Least Privilege: Limit user access strictly to the resources necessary for their job functions. Regularly reviewing and adjusting permissions ensures that no user retains unnecessary privileges over time.
3. Conduct Periodic Access Reviews: Schedule routine reviews of user and system access to detect unused accounts, redundant privileges, or policy violations. Revoking excess access helps maintain a clean and compliant access environment.
4. Use Centralized IAM or IGA Platforms: Deploy integrated IAM or Identity Governance and Administration (IGA) solutions like Okta, Azure AD, or SailPoint. These platforms enable centralized policy enforcement, automated provisioning, and detailed audit trails for better compliance and security.
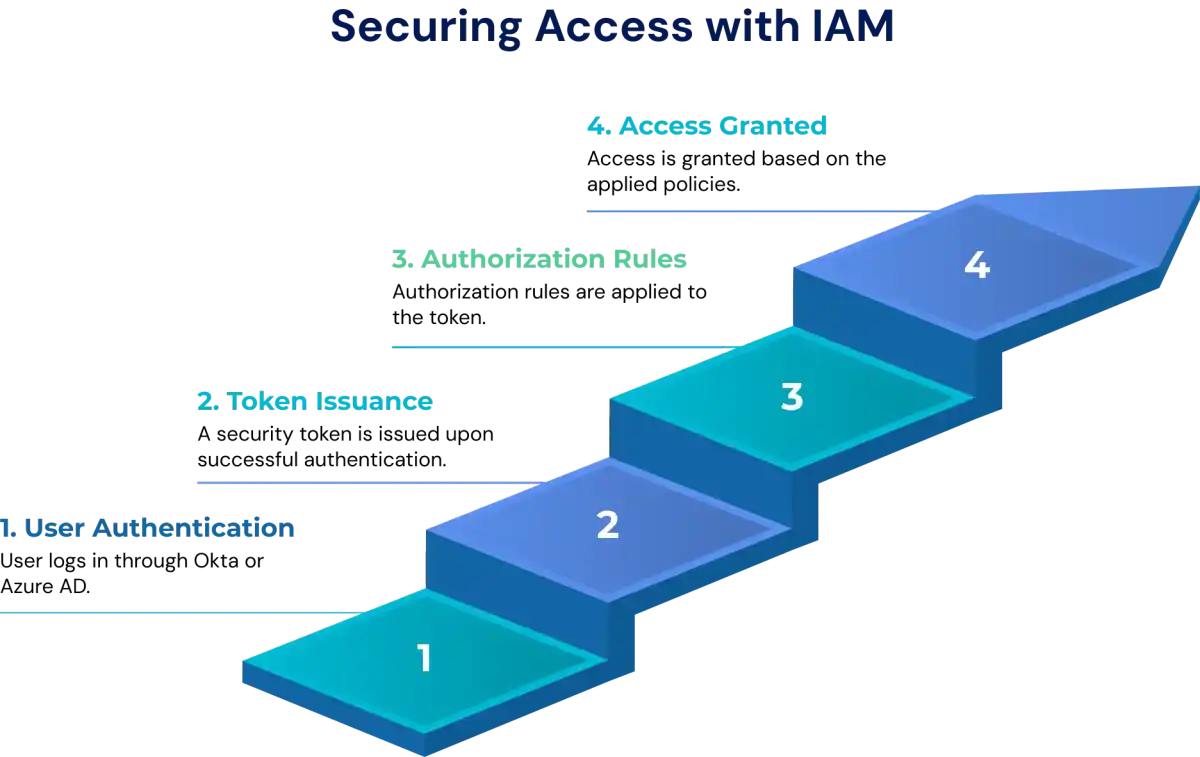
The Role of Authentication and Authorization in Zero Trust
In a Zero Trust model, every access request is continuously authenticated and authorized. The “never trust, always verify” approach ensures that users, devices, and sessions are revalidated at every step. Together, authentication and authorization serve as the foundation of Zero Trust by enforcing continuous verification and adaptive, context-driven access control.
1. Continuous Verification and Adaptive Access
In a Zero Trust framework, authentication and authorization are not single events but ongoing processes. Adaptive access policies evaluate risk factors such as user behavior, device health, and network conditions. Based on this real-time assessment, access privileges are dynamically adjusted to maintain security without disrupting user productivity.
2. Integration with Threat Detection and Context-Based Controls
Authentication and authorization mechanisms are tightly integrated with threat detection and analytics tools. Each access request is evaluated in context, considering user activity, location, and device posture. If anomalies are detected, the system can instantly restrict, revalidate, or revoke access to contain potential threats.
3. Role of AI and Analytics in Access Risk Scoring
Zero Trust systems leverage AI and analytics to calculate dynamic risk scores for every access attempt. These scores are based on behavioral data, session history, and device telemetry. The insights help determine whether to allow, limit, or challenge access, enabling continuous and intelligent enforcement of trust.
Final Thoughts
Authentication and authorization form the foundation of identity security, ensuring every access request is both verified and permitted. While authentication confirms who the user is, authorization governs what they can do, together creating a seamless yet secure digital experience.
In today’s multi-cloud and hybrid environments, the balance between security and usability depends on how effectively organizations manage these two processes. By implementing adaptive authentication, enforcing least privilege access, and integrating both within modern IAM and IGA frameworks, enterprises can reduce risk while enabling trusted access across systems.
To explore how Tech Prescient helps businesses build unified authentication and authorization systems that strengthen security and enhance user experience,
Frequently Asked Questions (FAQs)
1. What is the main difference between authentication and authorization?
Authentication is all about verifying who you are by confirming your identity through credentials like passwords or biometrics. Authorization, on the other hand, decides what you’re allowed to do once you’re authenticated. In short, authentication proves identity while authorization defines access rights.2. Can you have authorization without authentication?
No, you can’t. Authorization only works once the system knows who the user is, and that’s what authentication establishes first. Without an authenticated identity, the system has no basis to assign or verify access permissions.3. Which comes first, authentication or authorization?
Authentication always comes first in the access process. A user must first prove their identity before the system can determine what level of access they should have. Only after authentication does authorization decide what actions are permitted.4. Is OTP authentication or authorization?
OTP (One-Time Password) is a form of authentication. It is used to verify that the person attempting to log in truly owns the registered device or account. Once validated, the system can move on to authorization if needed.5. Why are both authentication and authorization important in cybersecurity?
Together, they form a layered defense against security threats. Authentication ensures only legitimate users gain access, while authorization limits what those users can do within the system. This combination prevents unauthorized access and helps protect sensitive data from breaches.



