Automating User Access Reviews: The Complete 2025 Guide


In an era defined by compliance and increasing demands for security, user access reviews are no longer optional; they are a requirement. The fact remains that many organisations use legacy processes with spreadsheets, email approvals, and manual sign-offs. Each time a new tool is adopted in a department, security teams have more permissions to track, audit, and be responsible for more accounts, which introduces a risk. Manual reviews are slow, make errors, and do not adhere to today's compliance requirements, such as SOC 2 and ISO 27001 - they just can't keep up!
According to the 2025 Verizon Data Breach Investigations report, the human element is involved in 68% of breaches with misconfigurations, misuse of privileges, or simply human error. Automated access reviews meet this need to solve those issues with the key ingredients of real-time visibility, consistency, and smarter controls. Automated access reviews eliminate the tedious process of retiring accounts that should not have access, they eliminate risky access before it becomes an issue, and compliant audit readiness is no longer doing it after the audit begins.
In this blog post, we'll detail what user access reviews are and why they are important in 2025, where manual review processes fail, how automation changes the approach, and what practical steps you can take to automate your organisation's reviews.
Key Takeaways
- Automated access reviews ensure permissions match current job functions to reduce unnecessary or risky access.
- Automated access reviews improve compliance with regulations like SOX, HIPAA, GDPR, and ISO 27001, while simultaneously improving operational efficiencies.
- Automated access reviews are faster than manual reviews, increase accuracy, and provide audit-worthy evidence compared to manual methods.
- Ultimately, your organisation strengthens security and visibility, reduces compliance costs and errors, and enables people to have more time for strategic work.
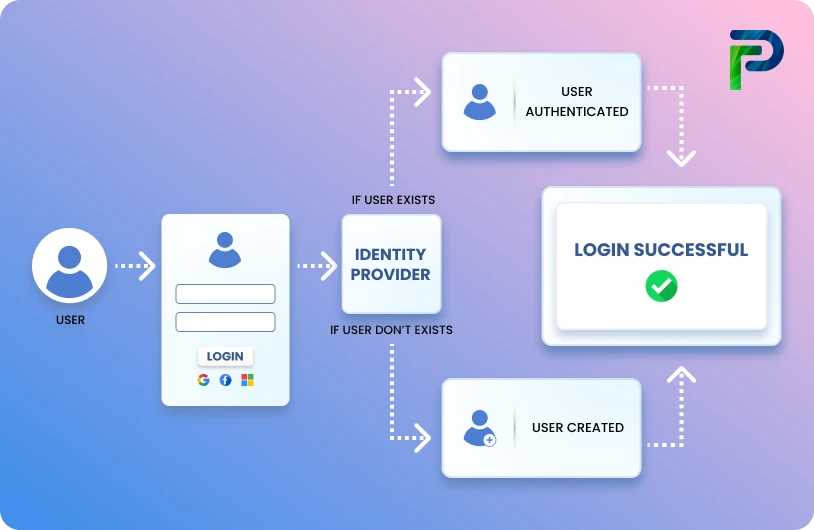
What Are User Access Reviews and Why Are They Critical in 2025?
A user access review, also known as a user access audit, is a structured, periodic verification to ensure that a user has the appropriate access aligned with their current role and responsibilities. It is a review of the access rights of employees and third-party users, including contractors, vendors, and partners. A user access review typically consists of reviewing who has access to which systems, applications, and data, then modifying access if necessary when business needs change. User access reviews ensure a user maintains the least privilege necessary by revoking stale, unused, or unnecessary entitlements.
In the absence of routine UARs, granting access permissions could easily age out. Employees carry forward inherited access rights upon being moved to a new role, contractors retain access rights upon project completion, or dormant accounts remain activated in the system. This permission sprawl is an accumulation of unnecessary or outdated privileges that is susceptible to attack or exploitation by a malicious insider.
Organizations could take it a step further with advanced user access review tools that automate certification campaigns based on roles, entitlements, or applications. These campaigns consistently flag and remediate access that may be outdated and/or inappropriate, ensuring access privileges continue to align with current and applicable top job functions and security policies across the enterprise IT systems.
By 2025, the trend toward access reviews has sharpened for three reasons: more stringent compliance requirements, increased security risk, and a leaner IT organisation.
1. Compliance
Laws and regulations such as SOX, HIPAA, GDPR, and ISO 27001 all state that organisations must be able to produce evidence that indicates whether or not the access to critical systems and data is appropriate and being reviewed on a regular basis. Auditors are not just expecting the evidence of the periodic review but also the proof of remediation when inappropriate access is found. In 2025 alone, there will be new regulations around PCI DSS 4.0, updates to the NIST CSF framework, and seemingly no end to new privacy laws worldwide. Access reviews are no longer optional; they are now the baseline for compliance.
2. Security
Certain risks to a business may emerge from the internal management of the organization. Insider threats account for a significant number of breaches, whether unintentional or purposeful. Here are two considerations that provide an example of one internal risk an organization faces:
- Excess access: Users may have more access than their job functions merit. For instance, an intern has admin access to a financial reporting application, or an HR admin is granted access to tools for the engineering team, such as GitHub or Jira. This excess access may inadvertently increase the organisation's attack surface.
- Dormant accounts: Organizations often leave contractor accounts active when they have left the organization, or employees who have separated from the organization still have active accounts. For example, a contractor leaves the company, but his account is still active for Zendesk. This represents a risk that sensitive customer data or internal records may be exposed.
Regular access reviews should be implemented to encourage the principle of least privilege to ensure users have the access they need to perform their job, and to inactive any dormant accounts before they become a risk.
3. Operational efficiency
From an IT operations perspective, uncontrolled access can lead to large systems of thousands of unused entitlements in no time flat. This complicates administration, increases license spend, and slows down audits. Organisations can maintain their systems in a clean state, remove unused accounts, and simplify identity governance with regular UARs. Automation takes this further by alleviating the manual workload, allowing IT and compliance teams to work on higher-valued deliverables rather than chasing approvals on spreadsheets or email threads.
Challenges of Manual Access Reviews
Though user access reviews are important for compliance and security, many organisations still facilitate them through manual processes - spreadsheets, email approvals, and misplaced documentation. At a small scale, this may work, but as organisations grow in size, user count, and technical infrastructure, manual processes are not practical or easily remedied.
The result? Inefficient reviews that take up IT resources and leave a trail of evidence that auditors are quick to highlight. Below are the most typical challenges for those organisations still using manual processes:
1. Time-Consuming Processes
It can take weeks to solicit user access data across several applications, aggregate the data into spreadsheets, and distribute the spreadsheets for manager approval. When large enterprise organisations are involved, each review cycle can involve thousands of entitlements across multiple systems. This arduous effort adds delays to audit cycles and takes IT personnel away from other security initiatives of greater value to the organisation.
2. Human Errors
Manual reviews often rely on managers reviewing lengthy spreadsheets and/or email attachments. Additionally, due to delays, many approvals are little more than “rubber stamps,” and by simply marking off access, access is certified without validating the requester’s right to it. This creates blind spots where access certification occurs without examining for formally excessive privileges or stale access, putting the organisation in danger of an insider threat and putting the organisation at risk for compliance violations.
3. Inconsistent Review Frequency
If there is no automation, it is difficult to enforce a consistent review schedule and process across department teams and/or applications. Some groups may conduct reviews quarterly, others once a year, and some never. This inconsistency will ruin security, as it leaves organisations exposed, and audit readiness will also wane, as regulators expect continuous or near-real-time reviews even when not automated.
4. Compliance Challenges
Auditors want to see proof that reviews took place, as well as confirmation that unauthorised access was corrected. If you're doing the work manually, collecting that proof is burdensome. Emails go missing, spreadsheets age, and records of remediation may not exist at all. If there is no reliable audit trail, you're exposed to fines, missed audits, and damage to your reputation.
Manual vs Automated Access Reviews: What’s the Difference?
| Feature | Manual User Access Reviews | Automated User Access Reviews |
|---|---|---|
| Process | Manually gathering data, compiling, and reviewing access rights can be tedious and time-consuming. | Utilises software and workflows to collect, analyse, and review user access. It automates data collection from various sources. |
| Efficiency | Resource-intensive and time-consuming, often taking weeks or months, and requiring significant coordination. This can lead to delays and skipped reviews. | Significantly improves efficiency, saving time and resources. Automated tools gather real-time data, reducing manual workload. |
| Accuracy | Prone to human errors, inconsistencies, and oversights. This increases the risk of overlooking inappropriate access. | Greatly improves accuracy by standardising the process and reducing human error. Automation flags excessive permissions and generates accurate reports. |
| Security | May lead to delayed detection of unauthorised access or policy violations. Can result in privilege creep and missed access revocations for terminated employees. | Enhances security by identifying potential risks and anomalies. It ensures consistent adherence to access policies, minimising errors. Can detect and address vulnerabilities before they escalate. |
| Compliance | May struggle to meet compliance requirements due to a lack of documentation and consistency. Generating audit-ready evidence is challenging. | Provides detailed audit trails and documentation for compliance with standards like SOX, HIPAA, GDPR, and ISO 27001. Automated systems generate comprehensive reports, streamlining audits. |
| Scalability | Does not scale effectively with organisational growth. | Enables scalable access reviews, adapting to growing organisations. Automated tools handle large amounts of data across numerous systems. |
| Real-time Insights | Often lacks real-time visibility into access rights and changes. | Automated solutions offer real-time monitoring and reporting. Can trigger alerts for unusual activity. |
| Cost | The time-consuming and error-prone nature of manual reviews can incur hidden costs due to inefficiency and potential security breaches. | Requires upfront investment but can significantly reduce long-term costs by improving efficiency and preventing security breaches and compliance fines. |
| Stakeholder Collaboration | Often involves multiple rounds of back-and-forth communication, leading to delays and misunderstandings. | Facilitates collaboration with a centralised platform for review and approval. Automated workflows notify managers, reducing delays. |
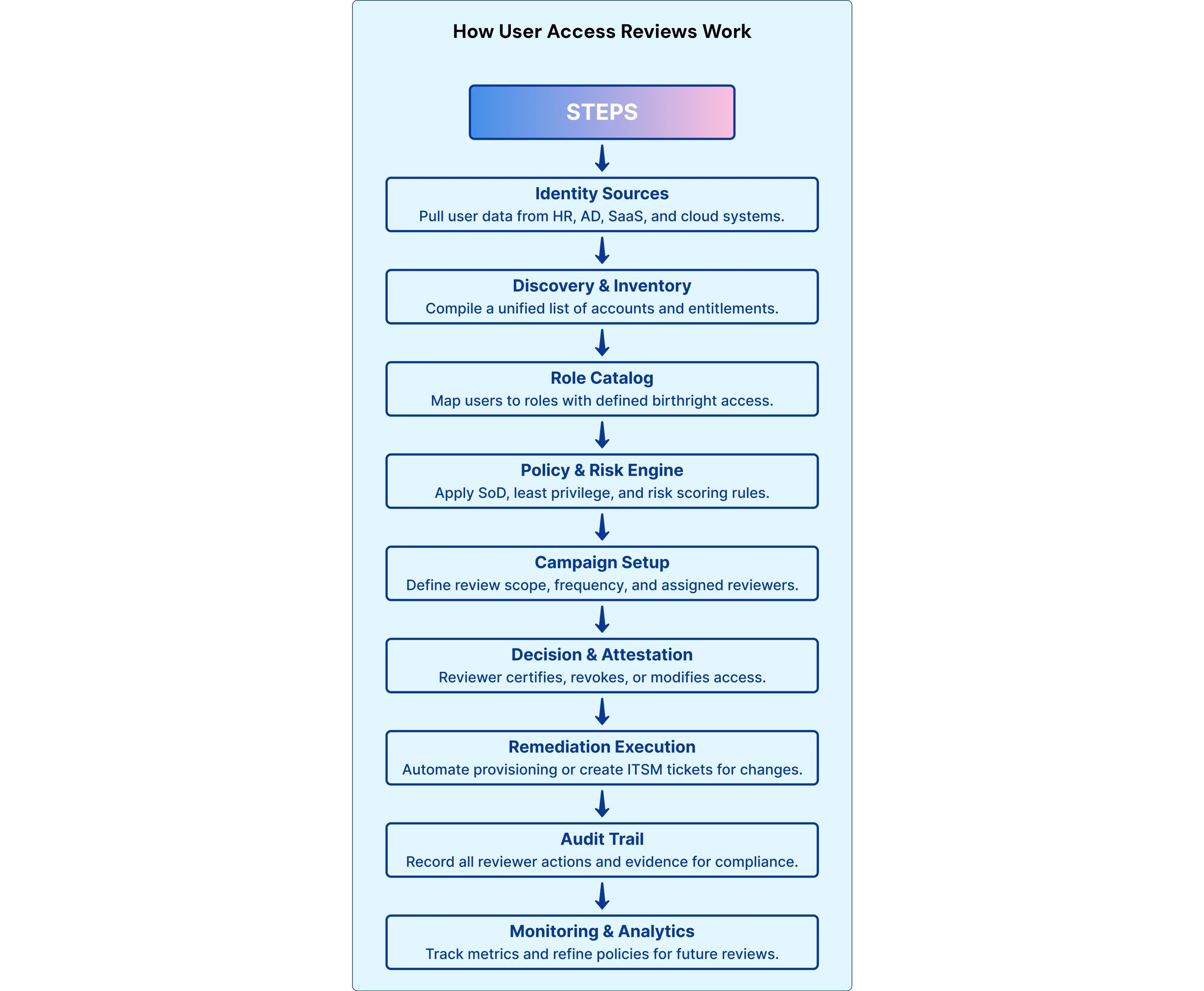
How Automated User Access Reviews Work
Automated user access reviews (UARs) convert a slow, manual certification cycle into a repeatable, auditable process. Risk is scored with continuous discovery of who has access to what, runs reviews, and either automated fixing of issues or recorded workflows to remediate. Listed below is a clear, practical and simple breakdown of how this happens, the environment needed, and the different platforms organisations use to run it.
Step-by-step Automation Workflow
-
Create Policies and Define Scope
Draft a formal user access review policy that includes scope, frequency, and stakeholders. Ensure that all applications/databases/cloud services to be reviewed are indicated, and involve department/division heads and system owners to capture genuine access requirements for review. -
Collect/Map User Access Data
Develop a full inventory of systems and applications. Automated tools can then be used to collect the data for each user, including account, roles, and access/permissions. After user data is all collected, place these into the identity warehouse for one view of the organisation. -
Review User Access
Utilise the principle of least privilege to consider each user's access as compared to their job role. Risks must be flagged, such as privilege creep, shadow admin accounts, and/or access for terminated employees. -
Automate Revocation and Changes
Automated tools can be used to revoke access that is no longer needed and to update access entitlements as needed. Provide reminders via new workflows for managers to help with reviews, and automated monitoring will allow you to track any changes to permissions so they do not go unnoticed during the review. -
Document and Review Again
You will need to maintain a written log of reviews, updates, changes and management approval status as required for compliance audits. Reviewing on a scheduled basis (quarterly or semi-annually) will help keep user access aligned with organisational changes, as well as compliance requirements.
Tools and Systems Integration
The success or failure of automation is largely determined by its integrations. Here’s a short list of the common systems to integrate, and how they are used in the automation space:
-
HRIS (Workday, SuccessFactors) - The authoritative source of truth for employment status, org hierarchy, and job codes. Use push events or create periodic syncs to trigger lifecycle events.
-
Identity Provider/SSO (Azure AD, Okta) - harvest user attributes, group membership and SSO sessions; to feed into entitlement analysis.
-
Directory services (Active Directory, LDAPs) - The source of on-prem accounts and groups, and often necessary for provisioning for several legacy / old apps.
-
SaaS apps (Salesforce, Google Workspace, Slack, etc.) - These connectors will collect per-app entitlements and last-use metrics.
-
Cloud environments (AWS, Azure) - Capture IAM roles, cloud privileges, and service principals.
-
PAM (Privileged Access Management) - isolate and monitor privileged accounts. PAM entitlement should be treated as a high-risk item in review and escalated accordingly.
-
ITSM - (ServiceNow, Jira Service Management) - routing remediation tasks, logging approvals, and ticket status to enforce your manual steps in the remediation process.
-
SIEM/Logging (Splunk, Elastic, Azure Sentinel) - forward review events from your list accounts, and any remediation log items for correlation and threat detection.
-
Provisioning protocols - SCIM (best option for modern SaaS), REST APIs, SAML / OAuth for SSO, LDAP for directories, and CSV ingestion for applications that do not have an API.
Integration best practices: Use least-privilege service accounts for connectors, enable delta (change-only) syncs where possible, secure connector credentials, and document mapping rules (attribute → entitlement).
Common Automation Platforms
Organisations have tools divided into categories: IGA suites from established vendors; IGA platforms (or modern SaaS/IGA-lite platforms); PAM integrations; and identity/workflow orchestration platforms, which include established vendors and newer focused solutions.
Things to look for in the platform:
- Connector library (SaaS, cloud, on-prem) and custom API support.
- Entitlement normalisation and Role-Mining capabilities.
- Policy engine for risk scoring and SoD checks.
- Campaign orchestration can be flexible (ad hoc, scheduled, continuous).
- Automated remediation (SCIM/API) and ITSM ticketing for manual steps.
- Audit tracking, evidence export, and compliance reporting.
- SIEM, PAM, HRIS, and SI\Devops tooling integration hooks.
- APIs and webhook support for extensibility.
Example vendors and applications:
-
Identity Confluence (Tech Prescient) — enterprise identity governance and administration, and access-review automation, including connector-based discovery, risk scoring and automated remediation workflows (an example platform for end-to-end campaigns).
-
Ping Identity— illustrative of the spectrum of the market from the IAM/IGA heavy-weights down to modern SaaS-centric automation tools. (Organisations will be one or multiple, based on environment, connector needs, and scale.)
Steps to Automate User Access Reviews Successfully
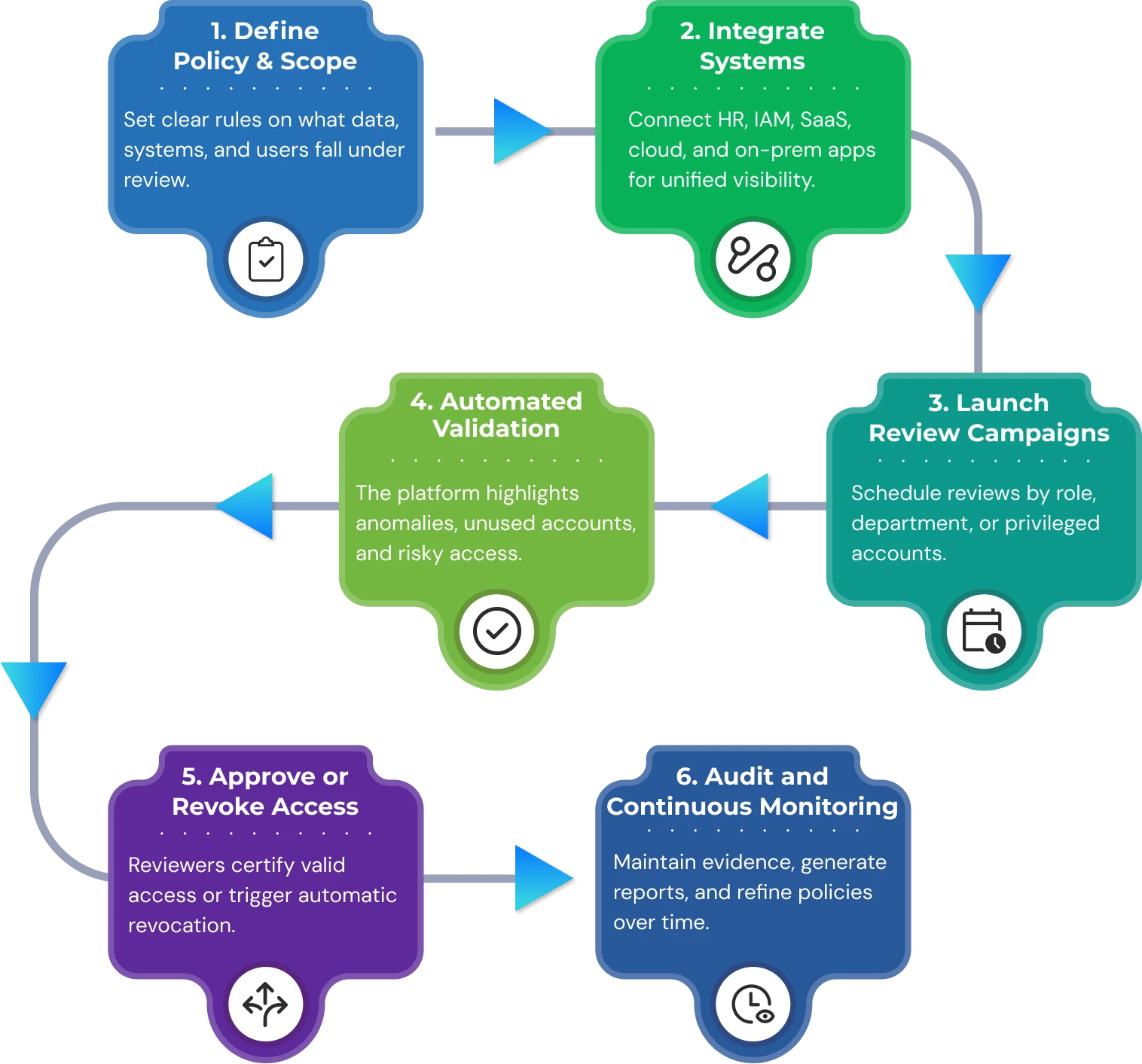
Automating user access review involves more than simply implementing a tool; it requires a systematic method for aligning policy, technology, and people. By adhering to an established follow-on method, organisations are better positioned to make reviews efficient, compliant with regulations, and a security improvement.
1. Policy and Scope
Start by declaring the rules of engagement. Identify which systems and data should be in scope, how often the reviews will run, and who will approve them. Financial applications, for instance, may require quarterly reviews, while privileged accounts may need to be reviewed monthly. Documenting this all upfront helps ensure consistency across departments and prepares the organisation for future external audit engagements.
2. Select Your Technology
Select an automation platform that fits your organisation's size, risk profile, and technology landscape. The selected solution should have strong connectors to your SaaS applications, cloud providers, and your legacy applications, plus risk scoring and reporting that is ready for compliance reporting. Using a proof-of-concept is usually the best way to determine whether the technology meets operational and compliance needs prior to a full rollout.
3. Integrate with IAM/IGA Tool
Connect the automation platform to your identity sources (HRIS, Active Directory, Azure AD/Okta) as well as your target systems (SaaS, databases, cloud providers). This creates a hub of data that connects users to their entitlements, job functions, and access permissions. By integrating the systems connected with the automation solution, you will offer a thorough review that is based on accurate, current source-of-identity data.
4. Set up Review Campaigns
Set up campaigns around business logic. Campaigns can be scoped by application type, department, privileged roles, and geographic regions. Assign reviewers automatically (e.g., line managers, data owners) and configure fallback owners to resolve bottlenecks. Leverage notifications and reminders built into the platform to help keep the momentum and completion rates up.
5. Monitor & Analyze
Once campaigns launch, review campaign progress through dashboards. Modern platforms will flag anomalies such as unused accounts, orphaned identities, or entitlements not aligned with a job role. Keeping track of review completion rates and escalation trends will help refine the process and identify training or automation needs.
6. Remediation & Reporting
The final stage is acting on review decisions. Automation completed the tasks regarding used entitlements, access modifications, or ITSM tickets for manual tasks. All actions are logged in an immutable audit trail. Next, reports can be generated instantly for auditors, compliance teams, or executives with access hygiene and regulatory compliance.
Real-World Use Cases of Automated Access Reviews
Automated access reviews are not just an abstract best practice; they are already changing how organisations manage compliance and mitigate risk across industries. Here are three real-world examples:
-
Finance: SOX-Aligned Review Cycles
In many financial services that are heavily regulated, Sarbanes-Oxley (SOX) mandates an undeniable burden of oversight as to who has access to financial reporting systems. Time-consuming and inefficient manual reviews can take months, and often result in gaps. Access reviews can automate the review process and allow financial institutions to easily implement quarterly certification campaigns, synced with SOX timeline requirements, automatically flagging excess privileges, and evidencing the whole process at audit time. All these controls help reduce the risk of fraud, whilst helping reduce the cost of audits. -
Healthcare: HIPAA User Certification
Hospitals and healthcare providers must adhere to the HIPAA Security Rule, dictated by the US Federal government, to ensure only authorised individuals have access to electronic protected health information (ePHI). An automated review ensures continuous validation of access based on roles - i.e., a nurse will not have access to ePHI in a different department. Anytime access entitlements seem suspicious, alerts come up within the consent, and workflows for immediate access revocation support the hospital in reducing risk associated with unauthorised exposure to patient data, while also confirming adherence to review protocols. -
SaaS: Entitlements and Deprovisioning Reviews
Modern enterprises use many SaaS apps, often dozens or even hundreds, which makes it impractical to manage entitlements manually. Instead, automated reviews provide centralised visibility across all SaaS platforms, enabling IT teams to identify inactive accounts, over-permissioned users or employees who retain access after offboarding. Automated workflows for deprovisioning then remove unnecessary accounts instantly, creating savings and reducing security risk.
Common Pitfalls to Avoid in Review Automation
Although automated user access reviews can significantly improve both efficiency and security, organisations sometimes struggle when the implementation is rushed or only partially completed. To ensure value is maximised, it is essential to avoid the following:
1. Inadequate Policy Scope
The most common mistake is not outlining what will be reviewed and why. Reviewing without having policies in place can either skip critical access or burden the reviewers with unnecessary reviews. Defining a precise scope of what needs to be reviewed makes sure the review is performed on sensitive systems, accounts with privilege, and regulatory reviews, and anything tied to those controls, and does not become a review of every single permission in the environment.
2. Poor Tool Integration
Automation is only as good as the systems it connects to. If the system chosen to measure the audit does not integrate well into IAM / IGA systems, SaaS apps, cloud, on-prem, etc., audits will leave blind spots that create a false sense of security because certain entitlements will not be audited. Overall, successful implementations always favour tools that have API based heavy integrations or integrations in directory systems.
3. Over-Permissioning Users
Automation can help identify excessive access; however, if they have a weak policy, a user can be left with too much access or permissions, which undermines the principle of least privilege and increases insider threat risk. Organisations must ensure that strong role-based access controls (RBAC) are in place and pair them with automated provisioning and entitlement cleanups.
4. Skipping Revocation Workflows
Identifying access no longer needed is only half the challenge. If there are no automated revocation workflows to help minimise the excess access that has been flagged, the unnecessary access can linger for weeks or months, leaving the organisation exposed. Automated platforms should always include automated deprovisioning workflows to remove or adjust access rights, which reduces the attack surface.
The Future of Access Reviews – AI & Predictive Security
As organisations move into the latter half of 2025, automated access reviews are evolving past efficiency and compliance. The new frontier is predictive security with AI, systems that do not merely react to risky access but rather anticipate situations and mitigate risks prior to them becoming undesirable. This evolution is already happening, with organisations including machine learning, anomaly detection, and risk-based intelligence into their Identity Governance and Administration (IGA) programs.
Here’s how AI is reshaping access reviews:
- Anomaly Detection
Anomaly detection involves the consistent monitoring of user activity by AI, which then compares user activity against known behaviour patterns. Instead of just relying on static rules and policies, anomaly detection flags atypical activity immediately as it occurs. For instance:
- An employee accessing sensitive financial data for the first time.
- A contractor downloading large data sets during non-business hours.
- A privileged user requesting higher-level access privileges without approval.
This approach allows organisations to shift from scheduled review campaigns and instead respond to risks as they develop.
- Predictive Analytics
Predictive analytics uses AI to analyse vast amounts of user activity, access behaviour, and historical incidents to assess where risks are most likely to be. This type of analytics allows organisations to:
- Predict the entitlemets that are misused most often.
- Predict the departments or applications where privilege creep is likely to occur.
- Predict compliance issues prior to audits.
Shifting reviews from reactive cleanup to predictive risk prevention.
- AI-Driven Risk Assessments
No two entitlements can be evaluated through the same lens. AI evaluates risk scores for users and entitlements based on contextual factors such as:
- Role Sensitivity (e.g., Finance vs. General Staff)
- Data Sensitivity (e.g., Access to Payment Card Data vs. Access to Internal Wiki)
- Behavioural History (e.g., Behaviour flagged as anomalous, frequent escalations in access)
Risk scoring allows IT and compliance teams to evaluate reviews based on the highest exposure, thus reducing waste in reviewing accounts that may pose little risk.
- Proactive Revocation
Historically, reviews have revealed risky access, and organisations have waited for approvals or campaigns to act. Going forward, the practice will be to revoke access on a proactive basis using AI. The AI system can disable or limit suspicious entitlements autonomously based on already defined thresholds and behaviour - for example, when multiple anomalous login attempts are detected, the AI can revoke admin rights. The idea is to limit the attack vector created by an entitlement to the greatest extent possible.
Choosing the Right Automation Tool
Choosing the appropriate automation platform may mean the difference between just digitising access reviews and enabling a volumetric, risk-mitigation and compliance-oriented process. With numerous vendors offering an overlap of capabilities, IT leaders must focus on capabilities that correspond with each of their security strategies and regulatory requirements.
At a minimum, your automated user access review capability must support Role-Based Access Control (RBAC), Segregation of Duties (SoD) and reporting capabilities. These are fundamental elements for meeting compliance obligations and demonstrating the enforcement of least-privilege access.
Here’s what to evaluate when making your choice:
1. Integration Ability with Current IAM or SSPM Tools
The tool needs to easily integrate with your IAM, IGA, and SSPM systems. Integrating with tools in these areas will help avoid siloed reviews with blind spots with the SaaS, cloud, or privileged. Look for pre-built connectors and APIs that allow for the smooth interchange of data across your IT ecosystem.
2. Customizable Workflows for Different Departments
Every department has different access needs. The finance area may need a strict quarterly review due to Sarbanes-Oxley compliance, while the engineering department may need to review privileged accounts more frequently. A good tool surrounding access review would allow you to customise the workflow of reviews by each department, application, or role in your organisation.
3. Reporting and Audit Logs That are Real-Time
One of the leading contributors to automating access reviews is the ability to be ready for an audit. Select a solution that will provide real-time reporting, detailed audit logs, and visual dashboards. This will ensure you can act quickly with audit requests and provide coverage with SOX, HIPAA, GDPR, or ISO 27001 without looking through records for evidence.
4. Scalability and Compliance Certifications
Growth presents a challenge for organisations when relying on manual and semi-automated methods and tools in the face of data scalability. Scalable solutions can accommodate thousands of users, apps, and entitlements in hybrid environments with no degradation in performance or sluggishness. Then, signify whether or not the vendor is also compliant with recognised compliance certifications (e.g., ISO 27001, SOC 2, and GDPR alignment), ensuring that they can effectively secure and protect sensitive data to access data.
💡 Expert Suggestion
“Don’t just look at features on a checklist. The right automation tool should fit into your organisation’s broader identity governance strategy. Prioritise solutions that integrate natively with your IAM/IGA platforms, offer intelligent risk scoring, and provide audit-ready reporting. This way, you’re not only streamlining compliance but also strengthening your overall security posture.”
~ Mukesh Rathod, CTO
Final Thoughts
Today, access reviews have gone from being a box-checking exercise to a frontline defence against identity-related risks. The stakes are higher than ever as regulatory oversight is increasing, the attack surface is expanding, and manual review cycles can no longer keep up with the complexity of today's enterprise. Automation will not only provide you with efficiencies, but it will also give you confidence that your compliance and security controls are working together at all times.
Future-thinking organisations are already taking on new platforms that combine automation with intelligent governance, which allows them to identify risks more frequently, never be out of audit-readiness, and lessen the workload on IT and Compliance. The real opportunity, however, is that these platforms go beyond the typical compliance certification and integrate access governance into a larger identity lifecycle.
With platforms like Tech Prescient's Identity Confluence, organisations capture the essence of simplifying user access reviews while spending time and having reporting around provisioning, deprovisioning, and privileged access controls. In the end, it's more than automation; it's an aligned identity governance framework balancing compliance, efficiency, and security.
NEXT STEPS
With Identity Confluence, your team can run user access reviews that are not only compliant but also efficient and audit-ready. Here’s how to get started:
- Learn more about Identity Confluence → Explore now
- See Identity Confluence in action.
Frequently Asked Questions (FAQs)
1. What is a User Access Review (UAR)?
A User Access Review (UAR), also known as an access certification, is a process where a company checks to make sure that everyone employees, contractors, and other partners have the right level of access to company systems and data. The main goal is to confirm that only authorised people have access and to remove any permissions that are no longer needed.2. Which regulations require User Access Reviews?
Several industry standards and laws mandate periodic access reviews, including:- SOX (Sarbanes-Oxley Act) for financial compliance
- HIPAA for protecting healthcare data
- GDPR for safeguarding personal information in the EU
- PCI DSS for payment card security
- ISO 27001 for global information security management
Automated reviews make it easier to stay compliant with these regulations.
3. What features should I look for in an automated UAR tool?
An effective UAR solution should include:- RBAC & SoD enforcement to flag conflicts
- Deep integrations with IAM, HR, cloud, and SaaS platforms
Customizable workflows for business-specific needs - Real-time dashboards & secure audit logs for compliance
- AI-driven insights for anomaly detection and risk scoring
These features ensure scalability, accuracy, and future-readiness.