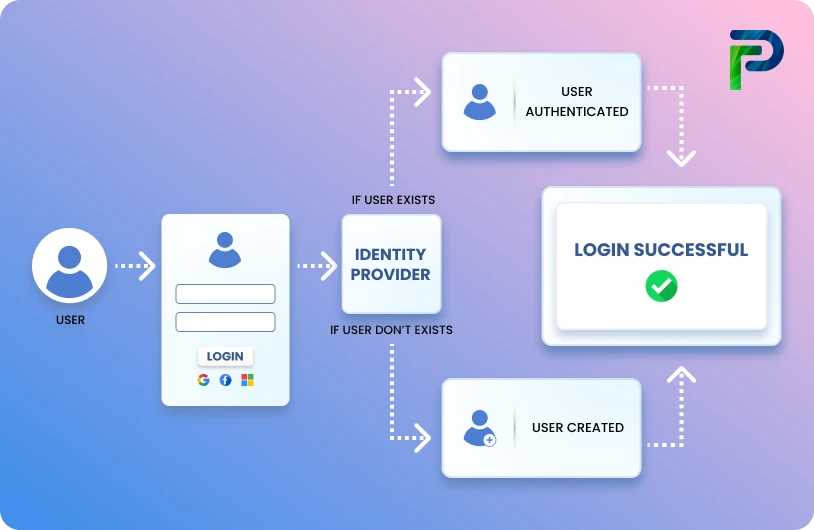
What is DSPM? A 2025 Guide to Data Security Posture Management!

Data Security Posture Management (DSPM) is a comprehensive approach to safeguarding the company's most important asset, its data, against unauthorized access, exposure, alteration or theft. This holistic framework integrates data classification, encryption, access controls, monitoring and automated remediation to provide an effective barrier around sensitive data. Consider DSPM to be your organization's smart guardian that constantly discovers where sensitive data is located, identifies gaps in protection, and makes safeguards stronger to prevent data breaches and maintain compliance with regulations
Unlike classic security tools that build barriers around networks, DSPM follows your data everywhere it goes, regardless if it's in cloud platforms, SaaS applications, or on-premise systems. On top of that, it looks over what actually matters most regarding your assets: the data itself.
Key takeaways:
- Learn why DSPM is becoming essential as data breaches cost $4.88M on average
- Discover how DSPM differs from DLP, CSPM, and CASB in protecting your data
- Explore measurable business benefits, including faster incident response
- See real-world use cases across healthcare, finance, and AI implementations
- Get practical guidance on selecting the right DSPM solution for your organization
Why DSPM Matters More Than Ever
Data Security Posture Management leverages artificial intelligence to identify data, evaluate risks, and automate policy enforcement throughout your data landscape. But why now, the urgency associated with data-centric security plans?
Traditional security models are very good at protecting networks and finding suspicious activities across users, APIs, IoT devices, and applications. These legacy solutions have improved data security and threat detection across organizations in a meaningful way.
However, the rapid acceptance of cloud computing, cloud-native development, AI, and machine learning has created new classes of data risks that the existing security tools were not designed to address. The resulting technological evolution has created significant security gaps that put organizations at risk of data breaches and violations of compliance.
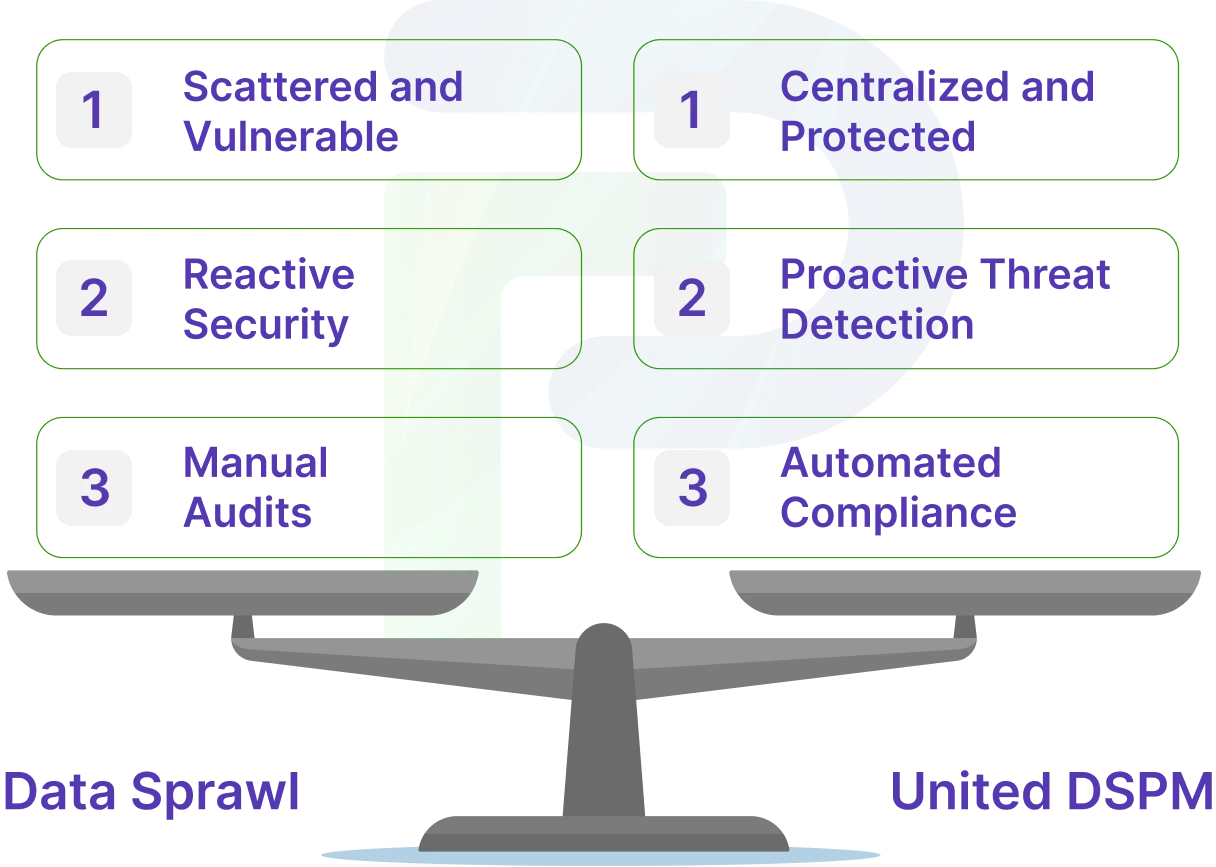
The most fundamental challenge is what has been referred to as "Shadow Data" – unauthorized copies, backups or replicas of sensitive data that exist outside of enforced security policies.
Imagine a typical scenario - a marketing team downloads a customer contact list from a CRM system to prepare a targeted email campaign which they save to their shared drive for team collaboration. Without adequate access controls and encryption, the content containing thousands of customer email addresses and personal identifiable information is now exposed to unauthorized access.
What's driving this surge?
It's simple: Data sprawl. Your sensitive data isn't residing neatly in one database anymore. It's replicated across development environments, it's in your cloud backup, it's in application logs, and it's in many of the SaaS tools the teams use every day.
This is exactly where Data Security Posture Management (DSPM) is critically important. DSPM continuously discovers, classifies, and monitors data throughout all environments ensuring that sensitive data that is hidden or not managed stays within security controls. With DSPM, organizations can reduce risk, maintain compliance, and protect sensitive data in any location.
Consider the financial impact: data breaches now cost organizations an average of $4.88 million, according to IBM's 2024 Cost of Data Breach Report, a 10% increase from the previous year.
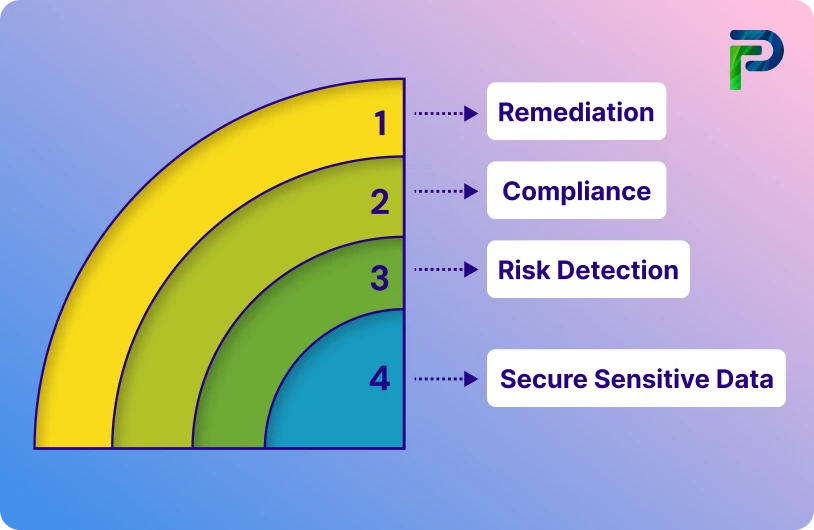
DSPM tackles this challenge head-on through three core capabilities:
- Automated Data Discovery: DSPM begins by finding and inventorying data sources across the organization, data sources could reside in databases, file systems, cloud storage, and third-party applications. The inventory helps organizations understand where their sensitive data lives - to include customer PII in backup files, financial records in someone else's forgotten database, intellectual property in collaboration platforms, etc.
- Risk-Based Classification: DSPM tools gauge data security by identifying vulnerabilities and threats using processes like vulnerability scans and risk correlation. This helps organizations prioritize data assets that need help with immediate remediation, enabling organizations to focus their resources on the risks that matter most, instead of treating all information the same.
- Automating Policies: These security tools ensure that data security configurations and policies are configured correctly and comply with best configurations and regulatory standards. It identifies any misconfiguration or weak access controls within systems and applications and enforces security policies to minimize exposure across the organization, in pursuit of ensuring credentialed access to data.
Here's where it gets interesting for identity governance. When you combine DSPM with platforms like Tech Prescient's Identity Confluence, you create a powerful synergy. DSPM tells you what data is sensitive, and it ensures only the right people can access it. This integration reduces data-related security incidents by 67% compared to manual approaches.
The bottom line?
Data-first security isn't just a trend; it's becoming a business necessity.
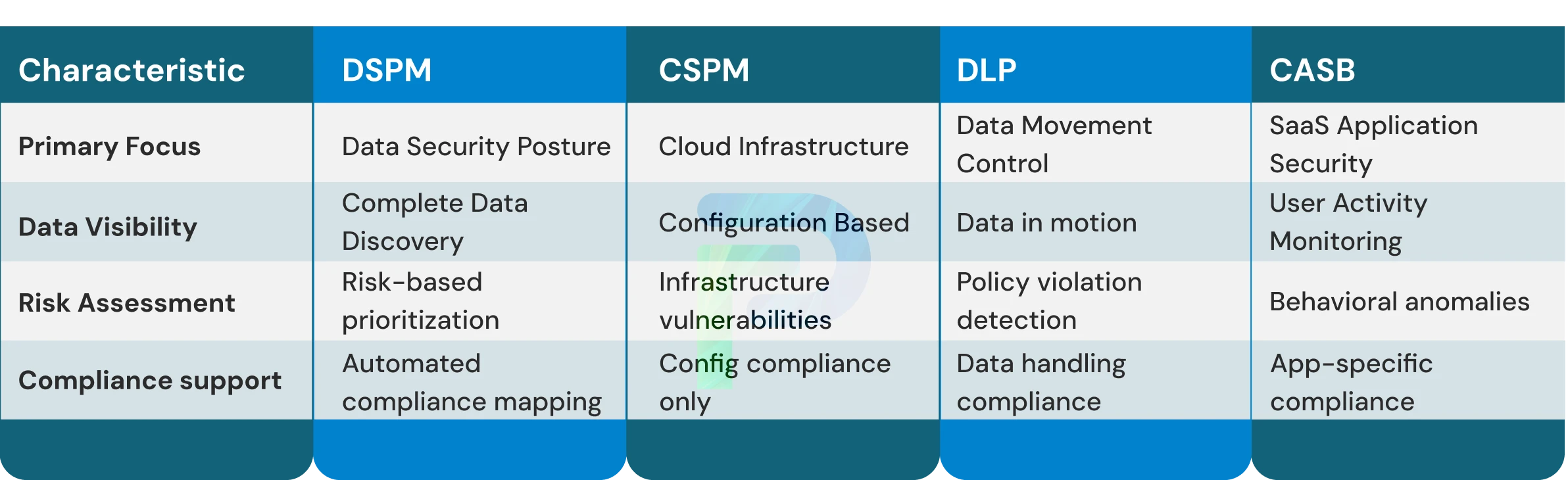
DSPM vs. Traditional Security Tools
Unlike DLP or CSPM, DSPM focuses directly on the data, not just access or infrastructure. But how exactly does it differ from the security tools you're already using?
Let's break down the key distinctions:
DSPM vs. CSPM
While both the Data Security Posture Management (DSPM) Solution and Cloud Security Posture Management (CSPM) solution reinforce a security framework across an organization, respectively, they address different security issues. CSPM emphasizes infrastructure, while DSPM emphasizes protecting data. Each domain provides a security capacity that supports, but is not a part of the other.
Cloud Security Posture Management (CSPM) focuses on continuous security monitoring, assessments, and enhancements of security configurations across cloud computing environments. Organizations use CSPM solutions to identify and mitigate misconfigurations, security vulnerabilities, and compliance gaps for their cloud-based resources continuously across environments in Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS).
CSPM solutions directly integrate with cloud-native application environments through the use of APIs, automation, and machine learning to acquire and assess security configurations from different cloud resources: virtual machines, storage, networks, and applications. CSPM evaluations of security configurations are assessed against established benchmark standards (CIS), regulatory standards (NIST, GDPR, HIPAA), and industry best practices/baselines. CSPM solutions identify deviations from the established security baseline and provide organization prioritize corrective actions that mitigate risk.
CSPM secures the cloud environment while DSPM secures the data residing in that environment. DSMP components work together to find sensitive content, classify that content by sensitivity, apply encryption and access controls to the content, and continuously monitor for data exfiltration or unauthorized activity. DSPM solutions provide holistic reporting and auditing capabilities that allow organizations to elevate data usage patterns, demonstrate compliance, and identify opportunities for improvement.
Key Distinction: CSPM secures the infrastructure; DSPM secures the information
DSPM vs. DLP
Data Loss Prevention (DLP) refers to a method and technologies that help to prevent data leaks, data exfiltration (data theft), anddata loss through continuous data movement tracking and applying security policies. DLP solutions monitor data in motion, while it is being communicated or transferred across different transmissions: emails, file transfers, web uploads, and network transmission - and can enforce security policies controlling the access and movement of data, at data is crossing into an external environment.
DLP is like a security checkpoint that inspects data as it attempts to leave your environment through various transmissions, denying or blocking anything that looks suspicious or is non-compliant with your policies.
DLP is very effective at what it does, since it is more reactive in its approach, watching data in motion, and intervening to stop sensitive data for moving in an unauthorized direction. DLP utilizes content pattern scanning in order to identify policy violations and prevent data movement from crossing outside perimeters.
Data Security Posture Management (DSPM) is fundamentally different from DLP since it proactively orchestrates transparency of data at rest, in transit, and in use. Rather than waiting for data to be try and transfer sensitive data, DSPM entails finding out when sensitive data is vulnerable, and prescriptive remediation in real time.
Key Distinction: DLP blocks data movement; DSPM prevents exposure conditions.
DSPM vs. CASB & CNAPP
Data Security Posture Management (DSPM) helps protect sensitive data regardless of where it exists or how it is being accessed, while Cloud Access Security Brokers (CASB) help with managing user access to Software as a Service (SaaS) applications, and Cloud-Native Application Protection Platforms (CNAPP) help to secure cloud-native applications throughout the entire lifecycle.
DSPM focuses on discovering, classifying and then monitoring sensitive data to gain an understanding of risk, as well as to comply with regulations related to protecting sensitive data. The primary purpose of DSPM, as it relates to securing sensitive data, is to provide visibility into where sensitive data lives and how it is being used, as well as put in place controls to minimize the risk of a data breach.
CASB is focused on monitoring and managing user access to cloud applications and services, specifically to Software as a Service (SaaS) applications. CASB provides an enforcement point for security policies to protect user access to cloud applications; detects user behaviours that put sensitive data at risk for exfiltration from the organization; and identifies unauthorized cloud applications as part of a shadow IT programme. CASBs act as intermediaries between users and cloud applications by monitoring access to cloud applications and reporting on the security policies you have in place with those SaaS applications.
CNAPP is an all-in-one security platform aimed at securing the entire lifecycle of a cloud-native application and workloads from pre-deployment (development) to deployment and into operations. CNAPP provides many security capabilities, encompassing Cloud Security Posture Management (CSPM), Cloud Workload Protection Platform (CWPP), and DSPM using the same reference architecture and providing a single source of visibility across all the security features to support cloud-native application security. CNAPP provides end-to-end security that spans development, build, deployment, and operation.
Top Business Benefits of DSPM
From faster audits to AI risk reduction, DSMP enables secure innovation by transforming how organizations approach data security governance. But what does this actually mean for your business?
Steps:
1. Full Visibility into Sensitive Data
Here's a startling reality: Most businesses do not know where sensitive data actually resides. During DSPM implementations, organizations consistently find 40-60% more sensitive data repositories than they realized were present.
Seriously think about it, when was the last time you took a hard look at every place you had customer social security numbers within your environment? Most organizations believe they are only in their CRM and HR systems. However, DSPM regularly discovers the same sensitive information lurking in:
- Backup and archive systems from years past
- Development and testing environments
- Application logs and error files
- Shadow IT deployments
- Third-party integrations and data exports
This in-depth transparency of data changes the way you will manage risk. You can't defend what you can't see, and you can't make a smart security decision based on partial insight. When combined with Identity Confluence, this visibility allows for accurate access decisions. Instead of providing access through broad role-based permissions, we automatically give users access to only the data they need based on real-time sensitivity labels.
2. Proactive Risk Detection
By consistently monitoring data stores and data flows for vulnerabilities and threats, DSPM provides organizations with enhanced security. By automating the management and identification of misconfigurations, stale access controls, and over-permissioning, this solution mitigates data breach risk while increasing data protection by regularly applying and updating cloud data security controls, all while enforcing least privilege
DSPM shifts security from reactive to proactive by identifying conditions that could lead to data exposure before incidents happen. Organizations implementing proactive risk detection report 51% lower incident response costs, according to IBM's Cost of Data Breach Report.
Common scenarios DSPM catches before they become headlines:
- Shadow Data Repositories:
Employees create "helpful" copies of customer lists for marketing campaigns or duplicate financial data for analysis. These well-intentioned actions often create unprotected sensitive data repositories. - Configuration Drift:
Systems that start with appropriate security controls gradually lose protection through routine changes, updates, or administrative errors. DSPM continuously monitors protection status. - Access Creep:
Users accumulate permissions over time that exceed their current needs, or sensitive data becomes accessible to broader groups than intended. Traditional security tools miss these gradual changes.
When DSPM identifies these risks, Identity Confluence can automatically adjust access permissions to minimize exposure while remediation occurs, no waiting for manual intervention.
3. Compliance Automation (GDPR, CCPA, HIPAA)
Manual compliance processes are resource-intensive, error-prone, and can't keep pace with modern data environments. DSPM transforms compliance from a periodic scramble into continuous, automated adherence.
- GDPR Automation:
DSPM automatically maintains Article 30 records by discovering personal data across your environment and mapping processing activities. When individuals request access to their data, DSPM instantly locates every instance for complete responses. - HIPAA Automation:
Healthcare organizations benefit from automatic PHI discovery across clinical systems, research databases, and communication platforms. DSPM ensures all Protected Health Information receives appropriate protection regardless of location. - CCPA Automation:
DSPM tracks personal information collection and monitors third-party sharing to support transparency requirements and enable rapid consumer request responses.
The time savings are substantial. Organizations achieve significant reductions in audit preparation time and compliance program costs through workflow automation.
4. Stronger Access Governance
Traditional access governance uses static role definitions that can become obsolete quickly. Data Security Posture Management (DSPM) gives you the data context that allows you to make intelligent, adaptive access decisions.
Instead of broad permissions for every user, DSPM grants protection by the risk associated with the data. For example, a user reading publicly available information may only need single factor authentication, while a user reading customer financial data requires multi-factor authentication, session recording, and limited time access.
Identity Confluence uses the DSPM classifications to implement access governance based on changes in the data sensitivity. When it discovers (through policies) that previously unrestricted data has sensitive information, it will automatically adjust the access permissions.
5. Faster Incident Response
When security incidents occur, security teams need immediate answers about potential data impact. DSPM accelerates incident response by providing instant data context and impact assessment capabilities.
- Immediate Impact Assessment: DSPM instantly identifies what sensitive data exists within affected systems, enabling security teams to quickly determine whether incidents involve public information or critical assets like customer PII, financial records, or intellectual property. This immediate classification allows for appropriate response prioritization.
- Targeted Response Strategies: Understanding data impact enables precise containment approaches. DSPM helps teams decide whether incidents require immediate system isolation (for sensitive data exposure) or can allow continued operations during remediation (for non-sensitive data incidents).
- Regulatory Notification Support: Many data protection regulations require breach notifications within specific timeframes. DSPM provides the data impact information necessary to determine whether regulatory notification requirements apply and what specific data types were affected.
Organizations with comprehensive data context reduce average incident response time by 42%, and every day of faster response saves an average of $1.2 million in business disruption costs.
Common Use Cases for DSPM
DSPM adapts to multi-cloud, healthcare, finance, SaaS, and more industries by addressing specific data security challenges unique to each sector.
1. Protecting PHI in Healthcare
Healthcare organizations face a perfect storm:
Vast amounts of Protected Health Information (PHI) spread across increasingly complex systems, strict HIPAA requirements, and significant financial penalties for violations.
DSPM typically discovers PHI in unexpected places beyond primary clinical systems:
- Communication Platforms:
PHI appears in email attachments when clinicians consult on cases, instant messages coordinating patient care, and collaboration tools sharing medical images. - Research and Analytics:
De-identification processes often leave residual PHI in research datasets, creating compliance risks and requiring re-anonymization. - Legacy Systems:
Backup and archive systems may contain PHI from patients treated years ago, potentially violating data retention policies.
The results speak for themselves: healthcare organizations implementing comprehensive PHI discovery and protection report 89% reduction in HIPAA compliance audit findings. This improvement translates directly to reduced regulatory risk and lower compliance program costs.
Identity Confluence integration becomes particularly powerful in healthcare, enabling automated access decisions based on clinical roles, department assignments, and specific patient relationships.
2. Reducing SoD Risks in Finance
Financial services organizations navigate complex Segregation of Duties (SoD) requirements designed to prevent fraud and ensure regulatory compliance. Traditional SoD monitoring relies on static role reviews that can't detect subtle violations spanning multiple systems.
DSPM enhances SoD compliance through granular visibility into actual financial data access rather than theoretical permissions. It tracks specific transaction data interactions, identifies cross-system access patterns that create conflicts, and enables time-based policies that adapt to business cycles.
The automation potential is significant. A regional bank discovered that 12% of users had accumulated permissions creating potential SoD violations across multiple systems. Automated remediation workflows reduced these violations by 94% within 60 days while maintaining operational requirements.
3. Enabling Responsible AI Data Use
Organizations adopting AI capabilities face a new challenge:
Ensuring AI systems access only appropriate training data while maintaining privacy protections and preventing bias.
DSPM provides the foundation for responsible AI implementation by automatically identifying sensitive information in potential training datasets, tracking data lineage through AI development processes, and monitoring AI model outputs for potential privacy violations.
This becomes critical as 67% of executives consider AI governance a top priority for 2025, according to IBM's AI Governance Report. Organizations implementing robust AI data governance reduce regulatory risk by 67% while enabling faster AI deployment.
4. Meeting Regulatory Deadlines
DSPM transforms regulatory compliance from reactive scrambles to proactive readiness. When new regulations emerge or deadlines approach, DSPM provides comprehensive data inventory, automated gap analysis, and real-time compliance tracking.
A healthcare organization recently faced a state privacy law implementation deadline of 180 days. Using DSPM, they completed comprehensive personal data discovery across 847 systems within 21 days and achieved full compliance 30 days ahead of schedule. Manual approaches would have required 18-24 months for the same scope.
How to Choose the Right DSPM Solution
Focus on scale, speed, AI-native capabilities, and contextual intelligence when evaluating DSPM solutions. The right platform should integrate seamlessly with your existing security stack while providing flexibility for changing business requirements.
When selecting a DSPM solution, evaluate these five essential criteria:
- Deployment Speed: Select platforms that enable rapid implementation and deliver immediate value through agentless integration approaches. Quick deployment minimizes disruption while accelerating time-to-insight for data discovery and risk assessment.
- Environmental Scale: Ensure your chosen DSPM solution handles extensive, complex infrastructures effortlessly. The platform should scale seamlessly across multicloud, on-premises, and hybrid environments without performance degradation as data volumes grow.
- Classification Precision: Choose solutions that deliver accurate data classification through sophisticated AI-based methodologies rather than basic pattern matching. Advanced machine learning algorithms reduce false positives while identifying sensitive data variations that rule-based systems miss.
- AI-Native Architecture: Prioritize DSPM platforms built for the modern era, leveraging advanced AI and machine learning capabilities to discover and classify information that traditional security tools overlook. AI-native solutions adapt and improve classification accuracy over time.
- Contextual Intelligence: Select platforms that provide comprehensive data insights including origin tracking, applicable regulatory requirements, and risk level assessments. Rich context enables informed decision-making about protection priorities and compliance strategies.
- Real-time Compliance Reporting: Look for solutions that maintain continuous compliance posture and generate audit-ready documentation for GDPR, HIPAA, CCPA, and other frameworks automatically rather than requiring manual report generation during audit periods.
- Identity Governance Integration: DSPM solutions deliver maximum value when integrated with comprehensive identity governance platforms like Identity Confluence. This enables automated access decisions based on data sensitivity rather than static role assignments.
Organizations implementing AI-native DSPM solutions achieve strategic advantages by reducing security risks while enabling innovation, ensuring sensitive data remains protected throughout digital transformation initiatives.
Final Thoughts: Why DSPM Is a Must in 2025
Data-first security is the new perimeter. DSPM is the foundation for secure growth in an era where data drives business value and regulatory scrutiny continues to intensify.
The convergence of several factors makes DSPM not just helpful but essential: Regulatory Evolution: Privacy and data protection regulations continue expanding globally, creating complex compliance obligations that manual approaches simply cannot address effectively.
AI-Driven Transformation: Organizations pursuing AI initiatives need robust data governance to access large datasets while maintaining strict privacy controls and regulatory compliance.
Threat Landscape Changes: Modern cyber threats target data directly rather than relying solely on infrastructure vulnerabilities or user access compromises.
- Organizations implementing integrated approaches typically achieve:
- Significant reduction in data-related security incidents
- Improved compliance audit outcomes
- Lower compliance program costs
- Enhanced access provisioning accuracy
The question for organizations in 2025 isn't whether they need DSPM; it's how quickly they can implement it to capture competitive advantages while meeting evolving security and compliance requirements.
Tech Prescient's Identity Confluence platform exemplifies this integration by leveraging data classification and sensitivity information to make intelligent access decisions automatically. Rather than relying on static role assignments, it adapts permissions based on real-time risk assessment.
Ready to See DSPM in Action? Book a Demo Today.
Frequently Asked Questions (FAQs)
1. What is DSPM?
Data Security Posture Management (DSPM) is a cybersecurity discipline that discovers, classifies, and protects sensitive data using automated risk analysis and compliance enforcement across cloud, on-premises, and hybrid environments.2. What is the difference between DSPM and DLP?
DLP blocks data movement; DSPM focuses on data visibility, risk detection, and prevention before breaches happen. DSPM maintains continuous awareness of data location and exposure risks across your entire environment.3. How does DSPM support compliance?
DSPM maps sensitive data to regulatory requirements, flags violations, and automates compliance reports for GDPR, HIPAA, CCPA, and more through continuous monitoring and policy enforcement.4. Does DSPM work in hybrid and cloud environments?
Yes, DSPM supports cloud, on-premises, SaaS, and multicloud infrastructures through agentless deployment and API-based integration that provides unified visibility across diverse environments.5. Is DSPM needed if I already use CSPM or IAM?
Yes, DSPM complements those tools by focusing on the security of the data itself, not just infrastructure or identity management. DSPM provides the data context that makes other security tools more effective.