Types of Cyber Attacks: A 2026 Cybersecurity Guide


In 2025, cyber attacks are more advanced, frequent and expensive than ever before. From large-scale ransomware attacks, to spear phishing schemes, to breaches by insiders, today’s attackers find a way to exploit every aspect of the digital ecosystem, be it human, application and infrastructure.
Recognizing the different types of cyber attacks is not only about being aware, but this knowledge is the foundation for determining and building a better defense mechanism for successful mitigation. Organizations can improve their ability to detect, extend response times, and limit the impact of incidents that would cripple operations.
In this guide, we will outline the major types of cyber attacks, how each type can work against an organization, and evidence-based prevention instruments using contemporary security practices, including Zero Trust, continuous monitoring and AI-based threat detection.
Key Takeaways
- Cyber attacks target vulnerabilities in users, systems, or networks for data theft or disruption of use.
- Phishing, ransomware, DDoS, password attacks, and insider threats are common types of attacks.
- Attackers may have various motivations, including financial gain, espionage, sabotage, or hacktivism.
- Smart defences, such as multi-factor authentication (MFA), Zero Trust, and routine patching, will greatly mitigate risk.
- Continuous user awareness of threats is also critical to staying ahead of a constantly evolving cyber threat environment.
What are Cyber Attacks?
A cyberattack is an intentional and unauthorized attempt to compromise digital systems, networks, or users for illegal purposes, including to steal data, earn money, conduct espionage (spying to gain confidential or strategic information), or disrupt operations.
Usually, the attacker seeks some form of benefit, financial, strategic, or political, from disrupting the victim’s network. Cyberattacks can target a wide range of victims, from individual users to enterprises and even governments. When aimed at businesses or organizations, the attacker’s goal is often to access sensitive and valuable resources such as intellectual property (IP), customer data, or payment information.
Cyber attacks are no longer discrete technical problems; they represent a persistent, evolving business risk. Threat actors are coming after every layer of an organization’s digital ecosystem: endpoints, cloud infrastructure, applications and users. They can deploy methods ranging from exploiting unpatched software vulnerabilities to manipulating employees with sophisticated social engineering techniques.
There are also multiple motivations behind cyber attacks. Financial motivations are still on top of most incidents, as we have seen with ransomware and business email compromise (BEC) attacks. Espionage and theft of intellectual property are about competitive and geopolitical interests, and campaigns aimed at disruption are to alter public trust or disrupt operations of an organization, even essential services.
The concern over cyber attacks for executives is less about the technical aspects of an attack and more about the business implications of an attack, such as regulatory damage, reputational damage, and operational damage. During the digital transformation process, organizations are moving to the cloud and connecting with third-party ecosystems, expanding their attack surface. Cyber attackers exploit that expanded view to attack an organization's misconfigurations, weak identities, and unmonitored workflows. Therefore, organizations must advance their cybersecurity methods from reactive defense to proactive posture management consisting of continuous monitoring, automated identity protection, and active threat intelligence.
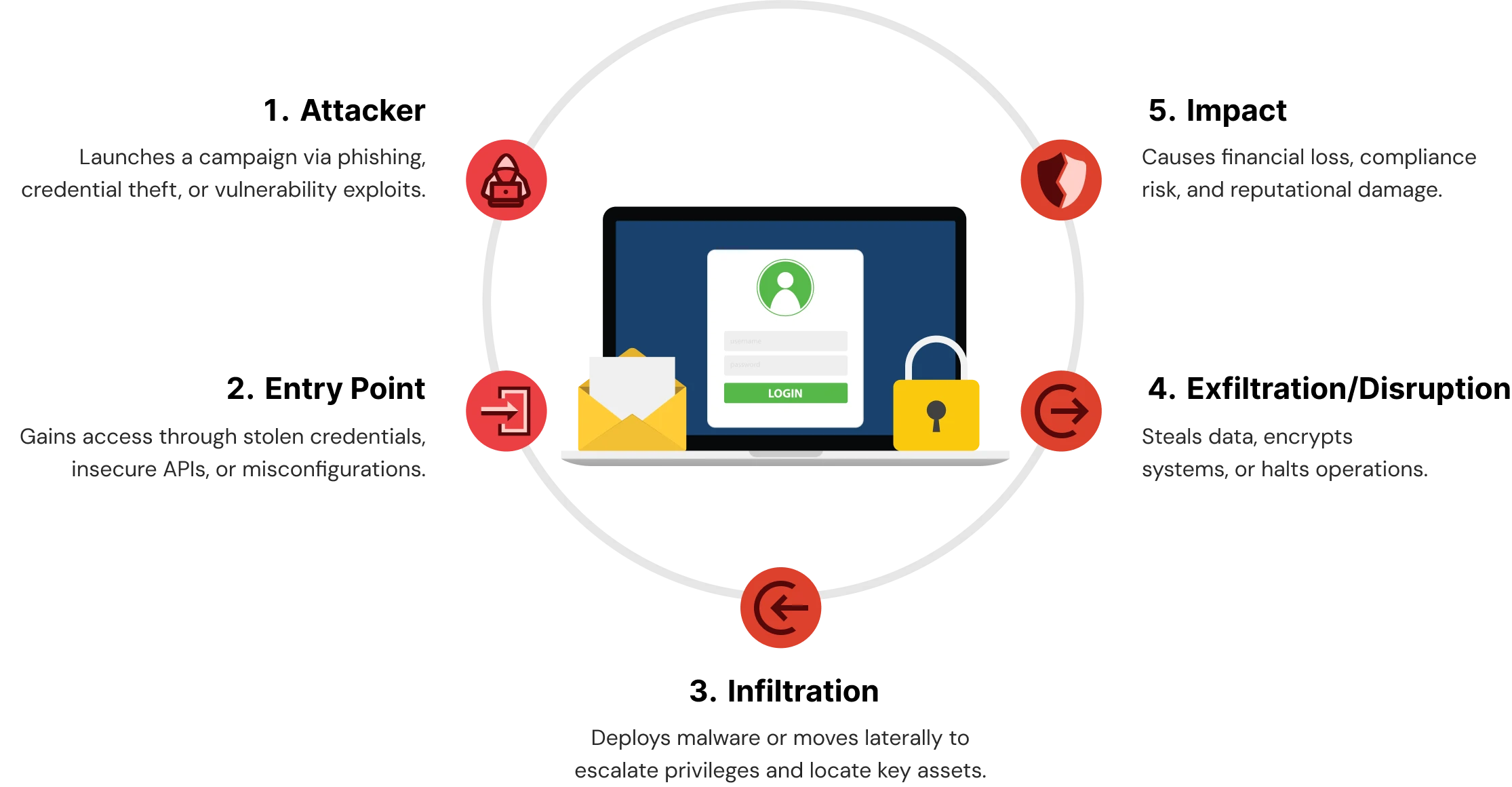
Common Types of Cyber Attacks
Organizations encounter a wide range of cyber attacks that take advantage of technical weaknesses, human behaviour, and operational gaps. Each attack varies in its sophistication and impact, from financial theft and the compromise of data to operational disruption. The following comprise the top five attack types when counting the volume of attacks in 2025 and represent the bulk of incidents in enterprises globally.
1. Malware & Ransomware Attacks
Malware is any harmful software that is intended to enter, damage, or exploit computer systems. The typical way that malware enters a network is through vulnerabilities (e.g., a user clicks on a link or opens an unsafe email attachment). Once malware has circumvented security defenses, it can block access to essential parts of the system, install malware, steal sensitive information (like spyware), or render all operations inoperative. Malware remains one of the most commonly used vectors for cyberattacks in enterprises, governments, and not-for-profit organizations of all sizes.
Ransomware is a specific form of malware that encrypts key files or systems and demands a ransom for access. Ransomware's effects on business continuity are unlike any other malware operation. Ransomware can lock users out of crucial data or systems, and if not contained, ransomware can spread quickly through a network. Ransomware is targeting enterprises, hospitals, and critical infrastructure consistently, which is rapidly becoming one of the most expensive and catastrophic cyber threats in our current landscape.
Common Subtypes:
- Viruses: A virus is a self-replicating program that replicates itself on files and can spread throughout systems.
- Worm: A worm is a form of malware that spreads on a network and is independent of a user.
- Trojan: A Trojan is a malicious program disguised as legitimate software to enable to gain unauthorized access.
- Ransomware: Ransomware is a malware type that can encrypt files and request a ransom. Ransomware is being increasingly used against enterprises, hospitals and critical infrastructures.
2. Phishing & Social Engineering
Phishing refers to sending deceptive messages, almost always through email, that seem to come from a trusted source. The purpose is to deliberately mislead the victim to disclose sensitive information like account passwords, credit card numbers, or personal information, or to unknowingly install malware on their device. Certain forms of phishing include spear phishing, which targets specific individuals or teams, and whaling, which targets organizations at high-value and high-risk executives. Phishing by SMS is called "smishing" and is becoming more prevalent as the use of mobile devices grows, so phishing has quickly proven to be a dynamic and prolific cyber threat.
Social engineering is the practice of exploiting human behaviours to gain unauthorized access or information. While phishing is often confined to digital messages, social engineering entails exploiting human psychological triggers for influence over behaviour, such as fear, urgency, or trust. In security breaches, employees often operate as the weakest link; attackers exploit human behaviours instead of exploiting technology. Successful social engineering may result in credential theft, unauthorized access to systems, and financial fraud.
Common Subtypes:
- Phishing: Mass email/messages that aim to steal login credentials or deliver malware.
- Spear Phishing: Targeted attacks focusing on specific individuals or teams.
- Whaling: Phishing designed for high-value compromise of executives.
- Smishing: Phishing by text intended for mobile phones.
3. Password Attacks
Password attacks take advantage of weak, stolen, or easy-to-remember credentials to gain unauthorized access to your systems. Attackers can obtain passwords in a variety of ways. They may guess passwords, capture unencrypted network traffic, pay an insider, or use social engineering techniques to get the user to disclose their credentials. One or more of the following are often the target of attacks due to insufficient password hygiene. Default passwords (e.g. “admin”), easily remembered numeric strings like "1234567," or personal information (e.g. birthdate, pet name or hobbies) are essentially given away from the start; all present a considerable risk.
The most effective method for addressing password attacks is to use a lockout policy, where access is prohibited for a short period of time after exceeding a predefined threshold of accepted login attempts for a particular account. Lockout policies effectively limit an attacker's ability to guess password credentials without detection. If an account is locked due to multiple attempts to log in, it should reset immediately.
Common Subtypes:
- Brute Force: If a hacker tries every possible password credential. If successful, the attacker may gain knowledge of personal information in order to guess password credentials.
- Dictionary Attacks: A hacker creates a list of common words, phrases, or relevant terms, and attempts to guess password credentials.
- Credential Stuffing: Credential stuffing is accessing accounts using known credentials from previous attacks.
- Keylogging: When the attacker installs a keylogger and obtains the username and password information directly.
4. Denial-of-Service (DoS/DDoS) Attacks
DoS and DDoS attacks aim to disrupt the availability of systems, networks, and/or services. By overwhelming resources, the attackers can bring operations to a halt and/or disrupt revenue flow and/or distract security personnel while conducting secondary attacks. Modern DDoS attacks may target cloud-based services, IoT networks, and applications, requiring proactive protection and mitigation techniques.
Common Subtypes:
- Volumetric Attacks: Flood the network with excessive traffic to exhaust the bandwidth.
- Application-Layer Attacks: Target specific applications to exhaust server resources.
- Protocol Attacks: Exploit flaws or weaknesses in communication protocols that disrupt service.
5. Man-in-the-Middle (MitM) Attacks
Man-in-the-middle attacks refer to communications being intercepted between users and systems, which means that an attacker might be able to eavesdrop, modify or capture sensitive information. If secure communications or encryption are not utilised, confidential data may be compromised, transactions may be modified without recognition, and authentication mechanisms may be undermined.
Common Subtypes:
- Session hijacking: Establishes control over an active session between the user and a system.
- SSL stripping: Degrades HTTPS communications to listen and capture sensitive information.
- Eavesdropping: Observing the transfer of data over a network or in communication that captures confidential information.
Advanced & Emerging Attack Types
Although traditional cyber attacks continue to be prevalent, sophisticated threat actors are now seen taking advantage of advanced techniques and newly discovered vulnerabilities to obtain financial gain, espionage, and to operationally disrupt. Organisations should be aware of these high-impact attack types to anticipate, detect, and mitigate risks in 2025.
1. SQL Injection & Code Injection
SQL and code injection attacks target vulnerabilities in applications in order to perform unauthorized commands, affect databases, or grant elevated privileges. They are often the result of insufficient input validations, which leads to data breaches, unauthorized data manipulation, or even a complete compromise.
Common Subtypes:
- SQL Injection (SQLi): injecting malicious SQL queries to access or manipulate databases.
- Command Injection: executing arbitrary commands on an affected host operating system by leveraging vulnerable applications.
- Cross-Site Scripting (XSS): injecting scripts into web pages with the intent to manipulate users' browsers or steal credentials.
2. Zero-Day Exploits
Zero-day attacks take aim at vulnerabilities that are not yet known to the software vendors; therefore, there is no patch available in immediate response. These represent highly sought-after exploits for attackers, since they defeat traditional protective means, risking critical systems, access to intellectual property or customer data before it can be identified.
Common Subtypes:
- Remote Code Execution (RCE): Exploits unpatched vulnerabilities to run commands remotely.
- Privilege Escalation: Gains access privileges in an unintended manner through an unknown bug.
- Browser and OS Zero-Days: Takes advantage of known vulnerabilities of the most commonly used software platforms.
3. Supply Chain Attacks
Supply chain attacks take advantage of weaknesses in third-party vendors or service providers to indirectly attack target organizations. Supply chain attacks are especially dangerous because they are difficult to detect and can create cascades of attacks within organizations, spreading malware, stealing sensitive data, or preventing operations from occurring.
There are two main types of supply chain attacks:
- Software Supply Chain Attacks: Malicious actors embed harmful code into applications, libraries, or APIs. Since modern applications rely on third-party components and open-source libraries, a single compromised part can put all users at risk.
- Hardware Supply Chain Attacks: Attackers obtain access to physical components, such as chips or network devices, to gain access or exploit vulnerabilities that were embedded before the hardware reached the organization.
By focusing on suppliers that are trusted rather than directly focusing on the target organization, attackers leverage the trust organizations have in suppliers as a means to create organisational-wide impact. Attackers have created an avenue that can be difficult to detect or mitigate.
4. Insider Threats
Insider threats arise from internal actors such as current or former employees, contractors, or partners, who have legitimate access to systems, sensitive data, intellectual property, and knowledge of business processes. These individuals’ knowledge of internal processes and security policy gives them a unique advantage in exploiting weaknesses, whether done intentionally or not.
Insider threats are especially problematic because the insider is a person who has access rights, making perimeter defense less effective for protecting data from insider threats. Examples of motivations for malicious insider activity on purpose include financial gain, such as selling confidential data on the dark web, revenge, or espionage. There are quotidian insiders that expose or place the organization at risk unintentionally, often out of a lack of knowledge or misunderstandings related misunderstandings.
Common Subtypes:
- Malicious Insider: Intentionally withdraws sensitive information, installs malware or disrupts business operations. Motivations may include financial gain, personal grievance, or espionage.
- Negligent Insider: User unintentionally exposes sensitive information or misconfigures circumstances due to mistakes, lack of knowledge, or inability to follow the process.
- Credential Abuse: A user with authorized access to information and systems who extracts sensitive information, often without obvious malicious intent to the credential abuse.
💡Many insider risks stem from excessive access privileges, a challenge best addressed through periodic access reviews and Identity Lifecycle Management.
5. DNS Tunnelling & IoT Attacks
DNS tunnelling is an advanced attack vector that uses the Domain Name System (DNS) protocol to sidestep traditional security mechanisms. Attackers can embed either malware or sensitive data in DNS queries and responses, enabling covert and selective compromise of a target, while remaining undetected by traditional controls, such as firewalls and intrusion detection systems. By masquerading data exfiltration as routine DNS data transmission, attackers can go undetected and maintain persistence.
In IoT Attacks, attackers leverage the vast and growing distributed federation of connected devices like sensors, cameras, connected appliances, and industrial control systems. These devices typically leave the manufacturer with default usernames and passwords, have firmware that remains unpatched, and communicate over insecure protocols. Once attackers compromise these devices, they can use them to re-access and/or to spread malware throughout larger network segments or, worse, install remote backdoors.
Common Subtypes:
- DNS Tunnelling: Embeds malicious data in DNS queries to circumvent security controls
- IoT Device Exploitation: Enables compromise through default weak credentials, unpatched firmware or insecure protocols.
- Botnet and DDoS using IoT Vice: Compromised devices will be leveraged for large-scale attacks.

How to Prevent Different Types of Cyber Attacks
To defend against cyber attacks, a combination of technological controls, process improvements, and employee awareness is necessary. Organizations need to implement a proactive and layered security approach to respond to changing threats across networks, endpoints, applications, and human elements. In 2025, successful defense will depend on adopting Zero Trust principles, multi-factor authentication (MFA), continuous patch management, and broad employee training.
Key Best Practices
-
Enable Multi-Factor Authentication (MFA)
Multi-Factor Authentication provides a critical layer of security, requiring users to verify their identity using multiple factors (e.g., a password, authentication app, OTP via email/SMS, or biometric scan) before accessing systems. If attackers obtain credentials, MFA raises the bar required to gain unauthorized access. This is a baseline control that organizations should enable for cloud services, VPN and high-privilege accounts. -
Embrace a Zero Trust Security Model
The Zero Trust model is built on the concept of “never trust, always verify.” The idea is that a breach might already be happening, and users need to be verified continuously, for every user, device, and application, to confirm whether they may access resources - no matter where they are located. By enforcing stringent identity verification, device authentication, network segmentation, and least-privilege access in this model, ZTO limits lateral movement and increases protection of sensitive data in modern perimeterless environments. -
Establish Efficient Patch Management
Patch management is the ongoing process of identifying, testing, and applying software updates following a structured lifecycle to ensure the operating systems, applications, and firmware are secure, operational, and protected against cyber-attacks. Patches are required for three levels: security patches (to mitigate risks), bug fix patches (to address specific operational errors), and feature update patches (to enable new or enhanced functionality). Vigilant patch management ensures the exposure to risk from known vulnerabilities is minimized. While automation has made it easier to track and apply patches, the patch management process is about planning, testing, and deploying effective patches in a way that respects the integrity of systems within environments.
💡Beyond software updates, true cyber resilience depends on visibility into every identity and entitlement that could be exploited. To learn more about it, read our detailed Identity Orchestration guide.
-
Increase Employee Education and Awareness
Even the best technology cannot protect against human error. Employees who go through regular cybersecurity training will be able to identify phishing emails, questionable links, and other social engineering attacks. Regularly strengthening the culture of awareness and accountability can minimize insider risk and improve responses to incidents. -
Improve Endpoint and Network Security
Endpoints (any device that connects to the network, including laptops, mobile devices, and IoT devices) are often common entry points for attackers. Strong endpoint protection, combined with constant network monitoring, can help to identify and block malicious activity before it advances beyond a certain point. Newer tools focused on endpoint detection and response (EDR) can be combined with a firewall and intrusion detection systems to give visibility and response capabilities across the attack surface intelligence. -
Schedule Ongoing Access Reviews and Increase Identity Governance
Access reviews are needed to ensure users keep only the permissions needed to do their job and to avoid modified privileges or misuse. Identity governance tools provide visibility into access roles and automate the review process to highlight excessive privileges while enforcing least-access policies for systems and resources. This not only minimizes risk by reducing insider threat but can also lessen compliance scope for frameworks such as SOX GDPR, and HIPAA with less effort.
💡With Identity Confluence by Tech Prescient, organizations can further automate and simplify access reviews, gaining real-time insights and actionable recommendations to stay secure and compliant.
- Implement a Strong Backup and Disaster Recovery Plan
While backups can protect our vital business data, a disaster recovery plan will help diagnose whether our systems can be restored in a hurried manner following a cyber incident. Making sure backups are saved in encrypted data files and stored in a separate location can shield our critical data from ransomware and other attacks. Organizations can test their recovery plan, such as simulating ransomware attacks to ensure they can restore backup databases, which means taking a primary system database offline and restoring it from a backup. They can intentionally fail over their primary systems to secondary systems, or sites, to ensure continuity with minimal operational downtime.

Final Thoughts
Cyber attacks are now a permanent and evolving operational risk, not just isolated events. As organizations leverage multi-cloud environments and a distributed workforce, security isn't simply about limiting your exposure at the perimeter. Today's security requires continuous visibility, greater controls, and automation. That’s where Identity Confluence by Tech Prescient provides value; it strengthens the identity security framework, imposes least privilege access, and integrates into existing cloud and security layers to reduce the exposure across your attack surface.
NEXT STEPS
With Identity Confluence, your team can run user access reviews that are not only compliant but also efficient and audit-ready. Here’s how to get started:
- Ready to take a proactive stance against modern cyber threats? ⇒ Explore Identity Confluence to see how unified identity security can help you minimize risk.
- Watch a short demo to learn how automation and continuous monitoring strengthen your cloud defense.
Frequently Asked Questions (FAQs)
1. What are the most common types of cyber attacks in 2025?
Some of the most common and damaging forms of cyber attacks in 2025, which negatively impact the information assurance (IA) process at organisations, are phishing, ransomware, DDoS, malware and insider threats. Phishing is a common attack type regardless of awareness because human beings are susceptible to issues of vulnerability. Ransomware seeks to utilise formal organisations for additional financial gain, while DDoS attacks aim to disrupt services to cause outages and operational disruption. Malware threats and vulnerabilities, while also an exploitive form of attacks, typically exploit vulnerabilities within systems of an organization, while insider threats penetrate the defenses with privileged access of a user, making the organization susceptible and vulnerable to compromise of data for malicious intent. By looking at the reasons and examples of common attack types, organizations can better tailor their defenses to anticipate and reduce risks overall.2. What are the 4 main types of cyber attacks?
The four main forms of cyber attacks include: malware, phishing/social engineering, password attacks, and denial-of-service (DoS & DDoS). Malware encompasses various forms of viruses, trojans, and worms that may damage systems or steal data. Phishing/social engineering manipulates human users into providing sensitive information. Password attacks take advantage of weaknesses in reused passwords or credential access. DoS and DDoS attacks overwhelm the machine resources of platforms or applications to cause outages and operational disruption.3. How do password attacks work in cybersecurity?
Password attacks exploit weak or stolen credentials to illegally access systems. These attacks target poor password habits, social engineering schemes like phishing, and weak multi-factor authentication. Common types include brute force attacks, where the attacker tries all possible combinations; dictionary attacks, using common passwords or phrases; credential stuffing, where attackers use information from other data breaches; and keystroke logging, which captures login details. Password attacks highlight the importance of controlled access, strong passwords, and multi-factor authentication in cybersecurity.4. What is the difference between malware and ransomware?
Malware is any software program designed to corrupt, disrupt, or gain unauthorized access to computer systems. Ransomware is a specific type of malware that encrypts data, prevents user access, and demands a ransom to recover data. In essence, ransomware is a type of malware, similar to other classifications of malware such as viruses and spyware.5. How can companies protect themselves from insider threats?
Organizations can mitigate the risk of insider threats by enforcing least privilege access so users have access only to those permissions that are required for their job responsibilities. Actively monitoring user activity and behaviour can help detect suspicious actions that may alert the organization to an insider threat. In addition to active monitoring, organizations must regularly review user access to sensitive information, provide training for staff on security policies, and set alerts for any unusual actions by employees. All of these best practices help reduce the chance that malicious insiders or careless employees present any risk to an organization.