
Types of Non-Human Identities in Organizations

Non-Human Identities (NHIs) refer to digital credentials that are linked to applications, services, devices, and automated workflows that operate independently of any human action. These machine identities differ from employee accounts, which represent individual people, and allow software to authenticate, communicate and access resources in your infrastructure.
The scale reveals the challenge. Entro Security's H1 2025 NHI Risk Report found that organizations now have 144 non-human identities for every employee, up from 92:1 just one year earlier. In heavily automated cloud-native environments, Sysdig's research shows this ratio can reach as high as 40,000:1, though this represents extreme cases rather than typical enterprise averages.
Non-Human Identities (NHI) can often evade detection while possessing more access than is required. Unprotected NHIs can easily be used by attackers, as they can pick up on things such as issues with configuration, exposed data, and excessive access.
GitGuardian's 2025 State of Secrets Sprawl Report documented 23.77 million secrets leaked on GitHub in 2024 alone. Managing NHIs effectively requires specialized security strategies to reduce risk and maintain control.
Here's a guide to what NHI means and how to protect NHIs within your organization.
Key takeaways:
- Understand the seven major types of non-human identities: API keys, service accounts, machine certificates, RPA bots, container identities, cloud workload identities, and IoT device credentials
- Learn about different access types for machine identities, including privileged access, service-to-service API access, data access, and ephemeral credentials
- Discover practical management strategies: centralized inventory, secrets management, credential rotation, access reviews, and behavioral monitoring
- Explore best practices for securing non-human identities through least privilege, automation, and unified governance frameworks
What Are Non-Human Identities?
A non-human identity (NHI) refers to digital entities – applications, devices, services, or automated processes – where they operate in lieu of an individual's identity. NHIs authenticate and authorize access to an organization's technology systems and resources, utilizing a credential, such as an API key, token, certificate, or service account.
When you log into the company's systems, you access those systems using your credential that is tied to you as an individual, and that access is mapped back to your job role. When you exit the company, HR will initiate deactivation of your account.
Machine identities operate differently. For example, consider a web application that queries a database. For that application to authenticate with a connected database, it will authenticate as a service account using database credentials. There is no human identity involved; the application executes and provides a result back to you. Your payment gateway to process transactions connects to Stripe using an API key that authenticates and authorizes each request to transact. Smart thermostats and industrial sensors are examples of devices that utilize IoT device credentials to securely transfer data back to a backend. A software bot automatically processes an invoice by logging into an ERP system and authenticates with its own credentials established to authenticate.
The rapid expansion can be precisely attributed to a model of operations structured around current application architectures. Ten years ago, deploying a monolithic application in a company's data centre may have only required a single database connection and some app-level credentials. That very same application would (presumably) now have dozens of micro-services, and each micro-service would require credentials to call other services' API, access databases, and authenticate to message queues. One logical application may require hundreds of separate machine identities.
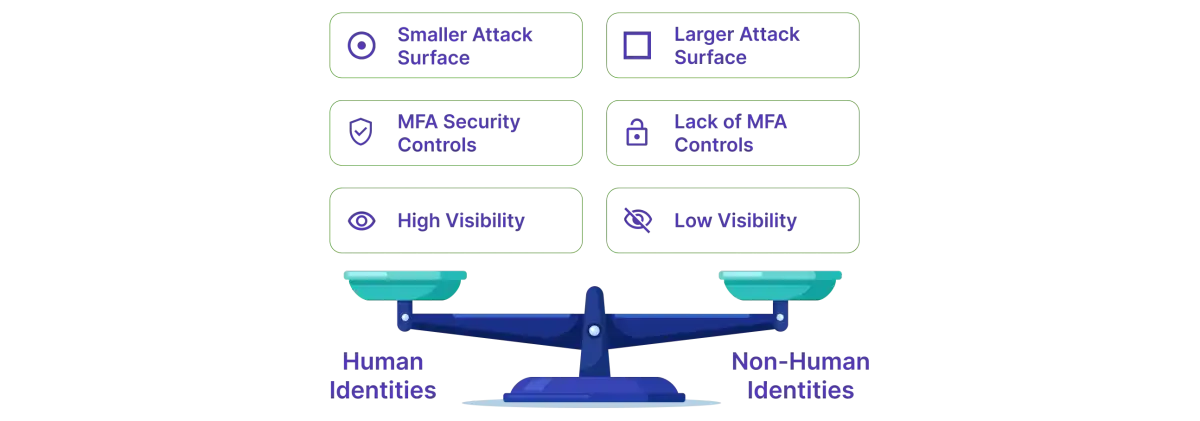
How Non-Human Identities Differ from Human Identities
While both human users and machines need credentials to access systems, the way these identities function reveals fundamental differences that create unique security challenges.
Lifecycle and Ownership
When Jane is employed by your organization as a software engineer, HR provisions her account, assigns role-based permissions, and connects it all to her employee record. When Jane leaves six months later, HR kicks off an automated offboarding process to deactivate her credentials across all systems within mere hours.
Now, think of the service account Jane created during week one in order to connect the customer portal to the database. That credential does not connect to the HR business system. It does not have an expiration date. It is not automatically suspended when Jane leaves. Three years later, the service account is still running, but at this point no one remembers that Jane made it, what it does, or whether or not it is still needed.
Authentication Methods
You access company systems with your username, password, and a code from an authenticator app on your phone. This is known as multi-factor authentication (MFA), a combination of something you have and know. Even if an attacker discovers your password, they will not be able to access your account without having possession of your phone.
However, machines are unable to use phones. If a microservice accesses another microservice, it utilizes API keys or certificates. So the microservice is authenticating with just one credential. If an attacker steals the key, then they have access, with no second factor to stop them.
Scale and Visibility
Your organization likely knows exactly how many employees you have. HR keeps a complete roster. Every employee has a manager who knows what they are responsible for. But how many machine identities do you have in your infrastructure? Most organizations don't know. Research indicates that the typical enterprise has 144 machine identities for every employee. These credentials are created by developers, automatically generated by cloud services, or embedded in self-service containers that are spawned and die in minutes. There is no central list. No clear ownership. And they're all running with little to no visibility.
Permission Patterns
Human access is often consistent. A member of the marketing team may access marketing tools during business hours. A finance staff member will utilize financial systems. It's considered unusual when a marketing person accesses payroll data at 3 AM. In this case, an alert is triggered.
Machine identities will access resources 24/7. For example, a database backup service may run daily at midnight. A monitoring agent checks on systems every 30 seconds. An API may process transactions whenever a customer makes purchases. These activity patterns are difficult to baseline, which often complicates detecting suspicious activity.
The Security Gap
Traditional security solutions were built for human users. They assume that credentials belong to humans who work regular business hours, use MFA, and routinely change their passwords. They operate on a premise of clear ownership, with lifecycle management driven by HR, where the user is always a person.
Machine credentials break all of these assumptions. They run all day, can't use MFA, rarely rotate, and are often not clear who owns it. This is why breaches based on credentials now take an average of 292 days to detect as security teams are not monitoring machine identities like they monitor identity for human accounts.
Understanding these differences is the first step toward properly securing non-human identities. The OWASP Non-Human Identities Top 10 for 2025 framework emerged specifically to address these unique challenges.
Why Non-Human Identities Matter in Cybersecurity
Non-human identities are among the fastest-growing and least visible security threats for modern businesses. They generate an attack surface many times greater than your human workforce, are not subject to the security precautions in place for people, and allow attackers to have similar or greater access to sensitive data and systems.
The Scale of the Problem
Let's do the math: if your organization has 1,000 employees, you are managing 1,000 identities... human identities. The traditional security team is used to this. Yet, if we now add the 144 non-human identities that exist to support every employee, this organization now has 144,000 machine credentials to protect.
These are not just statistics, research is showing this ratio increasing at a rate of 44% per year as organizations move into the cloud with microservices, and adopt the latest automation toolkits. Every new microservice, API integration, IoT device, or automation toolkit adds additional machine credentials to your environment.
For years, security teams have had disparate, sophisticated tools for monitoring human access, such as UX analytics, MFA processes, and regular access reviews, while machine identities continue to run in the dark.
Security teams are often not even able to answer basic questions:
- How many service accounts do I have?
- Which ones have admin access?
- When was the last time the service account was used?
Why Attackers Target Machine Credentials
Verizon's 2025 Data Breach Investigations Report documents credential abuse as the number one initial attack vector across all industries. When attackers successfully compromise an organization, they're increasingly targeting machine credentials rather than human accounts, and for good reason.
-
No Multi-Factor Authentication to Bypass
If an attacker acquires your password, they still have to get around multi-factor authentication (MFA); your phone, a hardware token, or biometric authentication. This creates friction, or an opportunity for detection.
Machine credentials, on the other hand, don't have that protection. An API key is one string. A service account is a password with no second factor. A certificate file has everything you need to log in and authenticate. Steal the credentials, and there are no other barriers; you have complete access. -
Broader Access and Lateral Movement
Most human accounts commonly work with 5-10 applications that are relevant to their job function. A compromised marketing account may have access to the CRM and email system; therefore, there is limited access for the attacker.
Service accounts frequently have access across several systems. For example, one database service account may access customer data, financial records, and operational systems. Compromising just one machine credential can lend an attacker a foothold through your entire infrastructure, what security professionals refer to as "lateral movement". -
Indefinite Validity Periods
Your organization likely requires password changes every 90 days. Human accounts that have been inactive for 30 days are disabled automatically. These policies reduce the opportunity for compromise.
Machine credentials do not typically expire. The Snowflake breach in 2024 included the use of credentials and secrets stolen in 2020, and these secrets were still valid and simply stayed valid for four years. It is reported that 70% of secrets leaked in 2022 were still valid in 2024. Once compromised, you can count on machine credentials to stay compromised until Microsoft manually finds and removes them. -
Minimal Monitoring and Detection
Security Operations Centers (SOCs) keep a watchful eye on human behavior. For example, if your account logs in from Russia and you live in New York, alarms go off immediately. If you log in to systems you don't usually access, security will investigate.
Machine identities run 24/7 in data centers around the world. They access systems around the clock. They make thousands of API calls. It is exponentially harder to tell the difference between malicious activity versus normal autonomous automation. This is one of the reasons why breaches via compromised credentials take, on average, 292 days to discover and contain; because attackers hide in the noise of normal machine-to-machine traffic.
The Business Impact
Beyond the technical risks, compromised non-human identities create significant business consequences:
- Financial losses from breaches continue rising. IBM's 2024 Cost of a Data Breach Report shows the global average breach cost reached $4.88 million, with credential-based attacks being among the costliest to remediate.
- Failing to comply with regulatory frameworks offering limited, or poorly controlled, machine access is a form of regulatory compliance failure. Regulatory frameworks also require periodic access certification and application of least privilege, so when auditors ask, "How do you certify service account access?" and you cannot even provide a list of your service accounts, you have already failed to comply with the compliance requirements before even having a conversation about controls to manage those access points.
- Operational disruption occurs when an organization must change credentials due to a breach. For example, during the emergency credential rotation of the CircleCI incident in August 2023, CircleCI required their entire customer base to rotate over 5,000 credentialed, production systems. This was a huge operational movement for CircleCI and impacted thousands of organizations at the same time, disrupting their operations.
- Reputational harm often amplifies the financial impact. Organizations that suffer breaches because they did not appropriately manage even the most basic principles of credential hygiene have reputational impacts. For example, the company "Snowflake", a SaaS organization publicly identified for leaving credentials from 2020 granted to their organization valid and exposing their data had reputational impact exposure when questioned about reputational maturity.
- There is also a reason why understanding non-human identities matter, but understanding the identifier itself and the level of access assurance controls to apply is what prevents an attack surface expansion risk. The next sections of text will define the major categories of machine identities and viable operational use case strategies to protect them.
Real-World Breaches Caused by Compromised Machine Identities
1. Snowflake Data Breach (2024)
The breach affecting 165+ organizations exposed hundreds of millions of records. AT&T paid a $370,000 ransom for call metadata; Santander exposed 30+ million bank records.
Attack vector: Username and password only, no MFA. Service account credentials from 2020 remained valid for years without rotation.
OWASP Risks: NHI7 (Long-Lived Secrets), NHI4 (Insecure Authentication)
2. CircleCI Breach (2023)
Malware stole session tokens accessing production environments. Attackers exfiltrated customer secrets including API keys, tokens, and environment variables. Forced rotation of 5,000+ production credentials across all customers.
Attack vector: Session tokens bypassed MFA. Overprivileged access to secrets management system.
OWASP Risks: NHI3 (Vulnerable Third-Party NHI), NHI5 (Overprivileged NHI)
3. New York Times GitHub Breach (2024)
An exposed GitHub token enabled access to 270GB across 5,000 repositories, including source code and 4,000+ secrets.
Attack vector: Overly broad token permissions. Five-month detection gap. Only 30 of 5,000 repositories encrypted.
OWASP Risks: NHI2 (Secret Leakage), NHI5 (Overprivileged NHI)
4. Microsoft Midnight Blizzard (2024)
Compromised OAuth tokens provided persistent access to internal systems. The token belonged to a legacy test application never deprovisioned.
Attack vector: Orphaned credentials from abandoned test application remained valid indefinitely.
OWASP Risks: NHI1 (Improper Offboarding), NHI7 (Long-Lived Secrets)
Common Patterns
All reported incidents discussed in this section share the following features: excessive entitlements granted at setup, lack of expiration dates, ownership was never defined, lack of monitoring, and poorly managed life cycles. Attackers made use of valid credentials; no advanced exploits were necessary.
Common Types of Non-Human Identities
- The types of non-human identities refer to distinct categories of machine credentials, each with different authentication mechanisms, use cases, lifecycle patterns, and risk profiles requiring category-specific governance approaches.
1. API Keys: Simple Credentials for Connecting Services and APIs
- API keys are mechanisms for authentication that enable the communication of applications, microservices, and third-party services with one another. An API key is a unique string of identifiers that applications include in requests to authenticate with the service considering the API key. Attackers frequently scan upstream repositories for exposed or hardcoded API keys to exploit to access services and sensitive data in the cloud.
- API keys are the most prevalent machine credential type because they are simple to generate and widely used. Thus, imagine your e-commerce application needs to process a credit card payment. You connect your e-commerce app with Stripe's payment API using an API key that Stripe created for your account. The API key serves to identify your application, and every request your e-commerce application sends to request payment includes the key to prove that your application was authorized to request that payment. You also connect your applications to send SMS notifications with Twilio and to monitor the application using Datadog, using a similar API key that is specific to each service. The security concern is that they are too simple: they are bearer tokens (anyone who has the key can use it). Developers often embed the key in source code during development, include it in configuration files that are deployed with the application, or log the key (although this is not recommended) in error messages.
- Best practices: Externalize all keys to secrets managers like HashiCorp Vault or AWS Secrets Manager, use separate keys per environment with scoped permissions, implement automated monthly or quarterly rotation, and deploy secrets scanning tools like GitGuardian to detect accidentally committed credentials.
2. Service Accounts: Persistent Accounts for Background Processes and Integrations
- A service account is an identity of a named account made specifically for applications, services, daemons, or automated processes that are not people and that provides authentication credentials and access permissions for those noninteractive processes.
- Almost every enterprise system has service accounts. Databases use service accounts to connect applications, monitoring systems use service accounts to query APIs, and backup software uses service accounts to access file systems. Examples include: service accounts for databases managing connection pools, Windows Services using domain accounts, LDAP bind accounts querying Active Directory, and daemon accounts such as "apache" or "mysql" having permissions to file systems. The problem is organizations often reuse the same service account for multiple applications, grant much broader permissions than necessary (such as database owner versus minimum permissions to tables), and do not establish password rotation policies because they do not want to disrupt applications and services. When developers create service accounts and leave the organization, the institution's knowledge about the accounts disappears.
- Best practices would include keeping a complete inventory and documenting the purpose and permissions for service accounts, using automated password rotation – possibly through secrets managers, granting minimum required permissions using roles, using service accounts for each application by environment, and continuously monitoring to identify abnormal activity, which could be a sign that your service account has been compromized.
3. Machine Identities & Certificates: Authentication and Encryption for Devices and Servers
- Machine identities represent cryptographic credentials, primarily X.509 certificates and corresponding private keys, that devices, servers, and other infrastructure components utilize to demonstrate identity in an authentication process and possibly establish encrypted communication.
- Certificates secure TLS/SSL for HTTPS websites and communication between internal services, server identity verification with SSH host keys, code-signing to establish application integrity and provenance, IoT device authentication to the backend, and VPN/IPsec client-to-server authentication. Unlike passwords that can be used indefinitely, certificates have hard expiration dates that will cause outages if not planned for renewal systematically. If an attacker manages to obtain a private key, they can impersonate that machine identity until the private key is revoked. Certificates distribute over countless servers, load balancers, and IoT devices without any comprehensive methodology for tracking, making management all but impossible.
- Best practices: Implement automated discovery to find all certificates across infrastructure, deploy certificate lifecycle automation platforms like Venafi or cert-manager, use short-lived certificates (90 days or less) following the Let's Encrypt model, leverage service mesh automation where technologies like Istio automatically provision and rotate certificates, and store private keys in hardware security modules (HSMs) rather than file systems.
4. Bots & RPA Agents: Automating Repetitive Business or IT Tasks
- RPA (Robotic Process Automation) bots are software applications that use credentials to interact with applications via user interfaces, working continuously to automate frequently performed tasks. Finance bots are responsible for processing invoices and reconciling accounts in institutional ERP applications. HR onboarding bots can automatically create accounts across numerous systems. Support bots can monitor CRM systems for new cases, and IT service desk automation provides incidents such as password resets and account unlocks. If applications do not integrate via API, RPA can carry out data migrations by launching both applications through user interfaces.
- From a security perspective, RPA bots are in a difficult situation: they require actual usernames and passwords with login screens; they accumulate permissions to several different applications to complete workflows; they purposely look like a human (which makes it difficult to decipher); and they are frequently exempt from password expiration and MFA requirements to ensure reliability.
- Best practices may include: every bot should have its own set of credentials with the naming convention making it clear they are bot accounts; store credentials in an enterprise vault instead of in RPA configuration; use the least amount of permissions possible and give bots read-only access wherever available; establish behavioral baselines for each bot and set alerts for variances; completely separate production and nonproduction credentials.
5. Containers & Microservices: Orchestration and Communication in Kubernetes Environments
- Container and microservice identities refer to credentials assigned to containerized workloads that enable the identity of the workload to act with authorization with the orchestration platform (e.g. Kubernetes), communicate with other services, and access other stepped infrastructure, etc. Service accounts in Kubernetes determine the set of API operations that pods can perform; service account tokens (JWT) are the primary source of authentication and are automatically mounted into containers, and workload identities in cloud service providers (like AWS IRSA, GCP Workload Identity, and Azure Pod Identity) allow workloads to assume cloud IAM roles without the static credential. The scale and ephemeral nature of pods pose unique problems because pods create and destroy themselves constantly (sometimes only living for seconds) and require a mechanism to automatically provision credentials. To mitigate these problems, developers sometimes "bake" the credentials into the container image, exposing all the credentials in their images to anyone with access to the container image registry. Kubernetes secrets are only base64 encoded by default, and anyone with access to the api can perform the operation to decode them. Service account tokens never expire by default.
- Some best practices: use external secrets operators to integrate with HashiCorp Vault, AWS Secrets Manager, etc.; use the cloud provider workload identity system for temporary (ephemeral) credentials that expire automatically; use service meshes to automatically provision certificates and mutual TLS with rotation; use service accounts and other tools like audit2rbac to right-size permissions; and use Kubernetes network policies to restrict pod-to-pod communication.
6. Cloud Workloads & Functions: Auto-generated Identities in AWS, Azure, or GCP
- Cloud workload identities are IAM roles, managed identities, and service accounts that cloud platforms assign to compute resources providing those resources with credentials to access cloud services without embedding static keys.
- AWS IAM roles for EC2 instances provide temporary credentials through the instance metadata service that applications query to receive time-limited access keys rotating automatically. AWS Lambda functions execute under IAM roles with SDKs automatically retrieving credentials, Azure managed identities provide OAuth tokens through Instance Metadata Service, and GCP service accounts provide OAuth access tokens through metadata services. This approach is superior because temporary credentials expire (typically after one hour) and refresh automatically, applications don't store credentials in code eliminating accidental repository commits, and every action is logged in CloudTrail/Activity Logs/Cloud Audit Logs with attribution. The biggest risk remains granting more permissions than needed, research shows 99% of cloud service accounts are over-permissioned.
- Best practices: Define precise permissions using specific actions on specific resources rather than wildcards, use IAM policy conditions to restrict usage to specific VPCs or source IPs, enable IMDSv2 to prevent SSRF credential extraction, use cloud provider tools like AWS IAM Access Analyzer to identify unused permissions quarterly, and assign each application its own IAM role rather than sharing.
7. IoT Devices: Unique Identities for Smart, Connected Devices
- IoT device identities are special cryptographic credentials, usually device certificates or hardware-backed keys, associated only with physical devices, allowing the devices to authenticate users and establish secure communications with backend platforms. Examples of IoT devices include industrial sensors that send telemetry, HVAC and access control systems for smart buildings, medical devices like insulin pumps with sensitive health data, telematics systems in connected vehicles, and consumer products like smart thermostats and smart locks. IoT identities present their own challenges: there are always ways to physically access a device (in most cases, public deployment of devices like smart city sensors), cost-sensitive devices may not have good security features with any credentials and may securely store credentials in flash memory, they may need to be deployed for up to 10-15 years and securing credentials for the entire duration of the device's life, and they may have limited CPU/memory/power budgets, which could make sophisticated cryptographic protocols impractical. Lastly, organizations could deploy millions of devices and need to handle the management of credentials at a scale.
- Best practices: Every device should have unique credentials never shared across fleets, use hardware security features like Trusted Platform Modules where available, implement X.509 certificates providing stronger authentication with defined validity periods, provision credentials in secure manufacturing environments or through zero-touch provisioning protocols, chain device certificates to a device CA under organizational control, and maintain comprehensive inventory including unique identifiers, certificate serial numbers, deployment locations, and firmware versions.
| Characteristic | API Keys | Service Accounts | Machine Identities & Certificates | Bots & RPA Agents | Containers & Microservices | Cloud Workloads & Functions | IoT Devices |
|---|---|---|---|---|---|---|---|
| Authentication | Unique string in requests | Named account identity | Cryptographic credentials (X.509 certificates) | Usernames and passwords | Service account tokens (JWT) | IAM roles, managed identities | Device certificates, hardware‑backed keys |
| Use Cases | Connecting services and APIs | Background processes and integrations | Authentication and encryption | Automating repetitive tasks | Orchestration and communication | Accessing cloud services | Authenticating with backend platforms |
| Lifecycle | Manual revocation, indefinite validity | Password rotation challenges | Expiration dates, renewal required | Password expiration exemptions | Ephemeral, automatic provisioning | Temporary, automatic refresh | Long lifecycles, secure rotation needed |
| Security Risks | Bearer tokens, easy compromise | Reuse across applications | Private key extraction, outages | Mimic human behavior | Baked‑in credentials, unencrypted secrets | Over‑permissioning, SSRF attacks | Physical access, weak security |
| Best Practices | Secrets managers, automated rotation | Inventory, minimum permissions, rotation | Automation, short‑lived certificates, HSMs | Unique credentials, credential vaults | External secrets, workload identity | Defined permissions, IAM policy conditions | Unique credentials, hardware security |
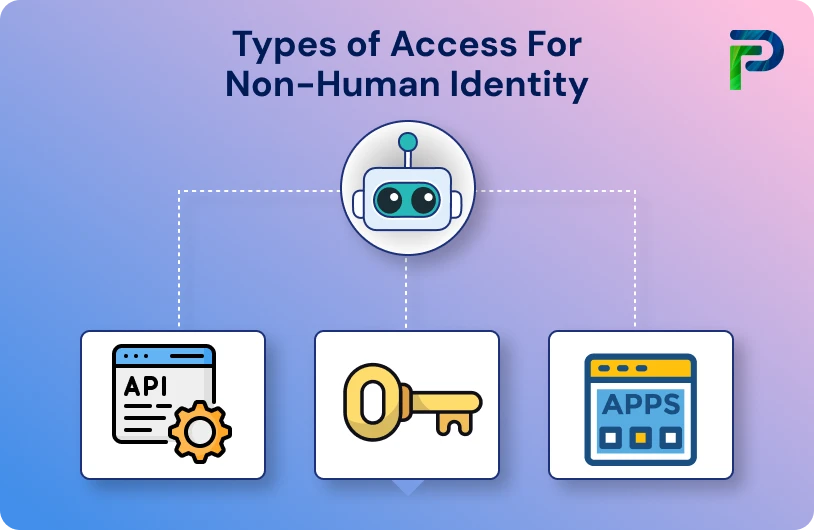
Types of Access for Non-Human Identities
Non-human identities need various access levels depending on their role, where the range could move from highly privileged administrative access to restricted read-only access. By knowing these access levels, organizations can more effectively implement the appropriate security measures and apply the necessary principle of least privilege.
Access levels can be privileged access, which allows for managing infrastructure and security controls to service-to-service API access for communication with microservices, reading or writing to databases and storage access, monitoring access for observability tools, and ephemeral access, which grants access using time-based credentials managed to expire automatically. Each of these access levels has different risk profiles and can have security approaches shaped based on the sensitivity of the operations and the possible blast radius of compromise.
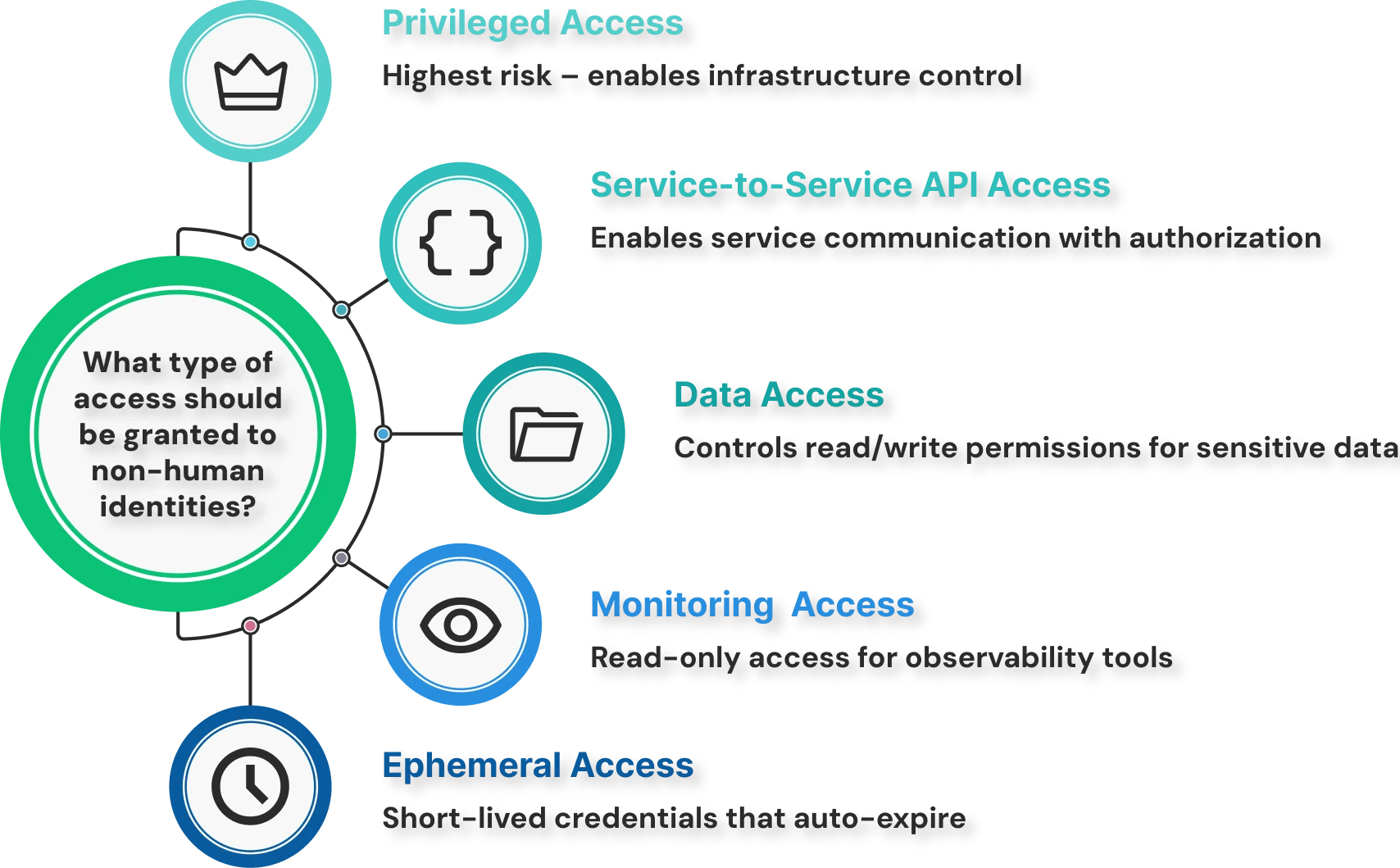
1. Privileged / Administrative Access
Privileged access for non-human identities refers to elevated permissions enabling infrastructure management, security control modification, user provisioning, or other sensitive operations, carrying the highest risk because such access enables attackers to control entire environments.
Governance challenges:
- Developers grant admin access during testing to avoid permission errors
- Some systems only offer "admin" or "regular user" with no middle ground
- A pipeline deploying applications might need permissions across multiple services
Best practices:
- Implement just-in-time (JIT) access where NHIs request temporary privilege for specific tasks
- For emergency access, implement break-glass accounts that are monitored and automatically expire
- Scope privilege as tightly as possible, even when elevated access is necessary
- Create separate identities for different functions, each with only the needed permissions
- Apply heightened monitoring to privileged activity with alerts on unusual operations
2. Service-to-Service API Access
Service-to-service API access refers to permissions enabling applications and microservices to call each other's APIs, typically using OAuth tokens, mutual TLS certificates, or API keys, to exchange data and coordinate workflows.
How it typically works:
- OAuth 2.0 client credentials flow, where services authenticate to obtain access tokens scoped to specific APIs
- Mutual TLS, where both client and server present certificates during the TLS handshake
- API keys per service pair are stored in the secrets managers and retrieved at runtime
- JWT tokens with service identities signed with private keys
Challenges:
In a microservices architecture with 50 services, there could be 2,450 potential service-to-service connections. Services scale dynamically, with new services constantly being deployed. Many implementations focus on authentication but skip authorization.
Best practices:
- Implement authorization alongside authentication using policy engines like Open Policy Agent
- OAuth access tokens should expire after 1 hour or less, with services implementing token refresh logic
- Service meshes like Istio provide mTLS and authorization policies defining allowed communication paths
- When Service A requests a token to call Service B, scope that token to only the specific APIs Service A needs
- Use network policies to restrict which services can network-connect to which others
- Track service-to-service communication patterns and alert on new connections
3. Data Access (Read/Write Scopes)
Data access for non-human identities refers to permissions enabling machines to read from or write to data stores like databases, object storage, or data warehouses, with scope varying from broad to narrow and from read-only to full read-write-delete.
Microsoft's 2023 report shows fewer than 5% of permissions granted to workload identities are actually used, meaning 95% represent unnecessary exposure.
Categories:
- Database access for service accounts with connection credentials
- Object storage access via cloud IAM roles or API keys
- File system access via service accounts with permissions to network file shares
- Data warehouse access for ETL pipelines and analytics services
Why is this particularly sensitive?
Databases contain the information attackers want: customer data, financial records, and intellectual property. Data protection regulations (GDPR, CCPA, HIPAA) require strict access controls and audit trails. Determining precise minimum database permissions requires understanding all code paths.
Best practices:
- Use column and row-level security instead of granting access to entire tables
- Where possible, machine identities should have read-only access
- For periodic jobs, grant data access only during scheduled time windows
- Tag data with sensitivity classifications, then craft policies granting access based on data tags
- Log every data query, read, write, or delete operation, with alerting on unusual patterns
- Use cloud provider tools to analyze actual data access patterns versus granted permissions
- Production data should only be accessible with production credentials
4. Monitoring / Observability Access
Monitoring and observability access for non-human identities refers to read-only permissions enabling monitoring agents, log collectors, metrics scrapers, and security information platforms to gather telemetry data.
Best practices:
- Monitoring agents should never need write access to monitored systems
- Implement data redaction at source to prevent sensitive data from appearing in logs
- Grant monitoring credentials access to only specific metrics or logs needed
- Separate monitoring credentials per environment
- Encrypt monitoring data in transit using TLS
5. Ephemeral / Short-lived Access
Ephemeral access refers to credentials with deliberately limited lifetimes (typically minutes to hours) that automatically expire without manual revocation, reducing risk by minimizing the window during which compromised credentials remain valid.
Modern implementations:
- AWS Security Token Service (STS) temporary credentials are valid for 1 hour
- OAuth access tokens typically expire after 1 hour
- Kubernetes projected service account tokens with configurable time-to-live
- HashiCorp Vault dynamically generates credentials on demand
- Certificate-based authentication with short lifetimes
Benefits:
If credentials are compromised, they expire quickly before attackers can fully leverage them. Forgotten credentials don't persist indefinitely. Regular credential expiration forces continuous validation that access is still authorized. Rotation is automatic, eliminating manual rotation campaigns.
Best practices:
- Use cloud platform workload identities with automatic credential refresh
- Implement OAuth 2.0 with refresh token flows handled by client libraries
- Integrate secrets managers to generate database credentials or API keys on demand with short lifetimes
- Generate credentials when needed rather than pre-provisioning them
- Use ACME protocol (Let's Encrypt), cert-manager (Kubernetes), or certificate management platforms
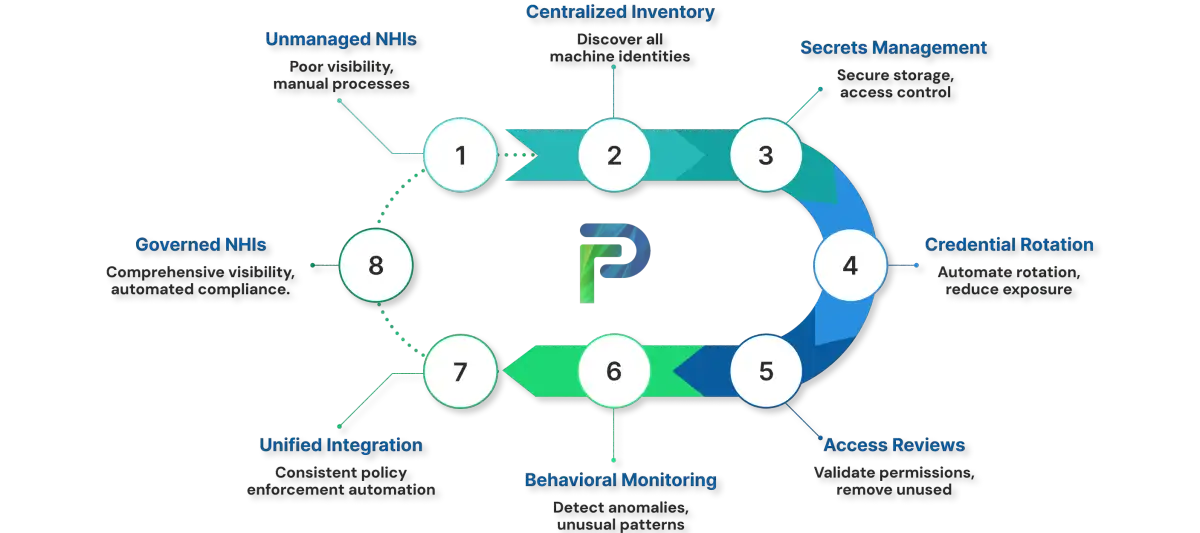
Managing Non-Human Identities Effectively
To manage NHI effectively requires visibility through automated discovery, lifecycle automation which replaces manual processes, governance through access reviews and policy enforcement and continuous monitoring for anomaly detection, orchestrated through consolidated IGA platforms.
Traditional IAM platforms are centred on human lifecycle management and associated with HR departments, interactive authentication utilizing passwords and MFA, and access reviews managed by users. However, all of this fails for machine identities which are created programmatically, and where ownership of the machine is often unclear.
Centralized Inventory & Discovery
You cannot govern what you cannot see. Comprehensive discovery identifies every machine identity across cloud platforms, applications, CI/CD systems, and infrastructure.
Discovery must be continuous. New NHIs appear daily as developers deploy services and infrastructure scales. Automated discovery tools scan cloud provider APIs, query directory services, examine container registries, parse infrastructure-as-code templates, and analyze network traffic.
A complete NHI inventory captures:
- Identity type and authentication method (API key, certificate, IAM role, service account)
- Creation date, creator, and business purpose
- Assigned permissions and resource access
- Usage patterns and last activity timestamp
- Associated applications, services, or infrastructure
- Rotation schedule and expiration date
- Owner and responsible team
Secrets & Credential Management
Secrets management solutions offer secure storage, controlled access, audit logging, and the ability to rotate secrets. Instead of hardcoding the API keys into source code, applications would dynamically fetch secrets from a centralized vault at runtime. HashiCorp Vault, AWS Secrets Manager, Azure Key Vault, and GCP Secret Manager all have encrypted storage, granular access policies, automatic rotation, audit trails, and integration with cloud IAM solutions.
Best practices include:
- Eliminate hardcoded credentials from source code and configuration files
- Use dynamic secrets generated on demand with short lifetimes when possible
- Implement automatic rotation for long-lived credentials
- Enforce least privilege access to secrets themselves
- Enable audit logging with alerting on suspicious patterns
- Integrate secrets retrieval into application initialization workflows
Credential Rotation & Revocation
Credential rotation reduces exposure windows by regularly replacing secrets. Automated rotation eliminates operational burden and human error. Immediate revocation enables rapid response when credentials are compromised.
Modern approaches address rotation through:
- Overlapping validity periods, issuing new credentials before revoking old ones
- Dynamic secret generation creates credentials on demand with short self-expiring lifetimes
- Automated rollout using configuration management to push updates across infrastructure
- Secret references: storing references in code and retrieving current values from managers at runtime
- Graceful degradation, implementing fallback mechanisms when credential refresh fails
Rotation schedules should be risk-based. High-privilege credentials require frequent rotation (daily or weekly). Lower-risk credentials with strong access controls may rotate monthly or quarterly.
Access Reviews & Least Privilege
Periodic access reviews validate that NHIs retain only necessary permissions. Many NHIs accumulate permissions over time that are never removed after issues are resolved.
Microsoft's 2023 report shows fewer than 5% of NHI permissions are actively used, and 80% of workload identities are inactive.
Effective access reviews require:
- Usage analytics identifying which permissions NHIs actually exercise
- Last activity tracking flagging inactive NHIs that haven't authenticated recently
- Permission right-sizing, reducing permissions to the minimum actually used
- Attestation workflows requiring application owners to certify permissions remain appropriate
- Automated revocation removes access when NHIs remain inactive beyond thresholds
The principle of least privilege is challenging for NHIs because determining precise minimum permissions requires understanding application behavior. IGA platforms address this by analyzing actual usage patterns and recommending permission right-sizing.
Behavioral Monitoring & Anomaly Detection
Behavioural analytics detect when NHIs deviate from established patterns: unusual authentication locations, unexpected API calls, abnormal data access volumes, or access outside normal time windows.
Anomaly detection should monitor:
- Authentication patterns (location, timing, frequency, method changes)
- Resource access (new resources accessed, unusual volumes, privilege escalation attempts)
- API usage (new endpoints called, rate limit violations, error rate spikes)
- Data access (sensitive data queries, large exfiltration, unusual query patterns)
- Lateral movement (unexpected service connections or infrastructure access)
The challenge is tuning false positive rates while maintaining detection sensitivity. Applications legitimately scale during peak traffic, deploy to new regions, or interact with new services during feature releases. Security teams must correlate NHI behavior with application deployment cycles and business context.
Integration with IAM/IGA Systems for Unified Control
Mature identity governance requires unified visibility across both human and non-human identities. Organizations cannot maintain separate tools without creating blind spots where attackers operate across identity types.
Modern IGA platforms provide:
- Unified identity inventory aggregating human users, service accounts, API keys, and cloud workload identities
- Cross-identity access reviews enabling certification of both user and machine access
- Policy-based governance applies consistent security controls regardless of identity type
- Lifecycle automation orchestrating NHI provisioning, modification, and deprovisioning
- Compliance reporting demonstrating governance across all identity types
Tech Prescient's Identity Confluence treats non-human identities as first-class entities within identity governance frameworks, providing organizations with comprehensive visibility, consistent policy enforcement, and automated compliance across cloud, on-premise, and hybrid environments.
Industry Frameworks and Compliance Requirements for NHI Security
Organizations need structured approaches to manage non-human identity risks systematically. Industry frameworks provide that roadmap, while regulatory requirements make NHI governance a compliance imperative.
The OWASP Non-Human Identities Top 10 Framework
The OWASP Non-Human Identities Top 10 for 2025 provides a risk-based framework specifically designed for machine identity security. Similar to how the OWASP Top 10 for web applications became the industry standard, the OWASP NHI Top 10 is establishing itself as the definitive reference for prioritizing and mitigating non-human identity risks.
Major vendors including Entro, Astrix Security, Orca Security, GitGuardian, and Saviynt have endorsed the framework, with compliance dashboards now implementing OWASP NHI Top 10 assessments.
The framework addresses 10 critical risk categories:
- Improper Offboarding – Legacy applications and orphaned credentials that remain active indefinitely
- Secret Leakage – Credentials exposed in source code, configuration files, container images, or logs
- Vulnerable Third-Party NHI – Compromised supply chain dependencies and external service credentials
- Insecure Authentication – Weak authentication mechanisms lacking MFA or certificate validation
- Overprivileged NHI – Excessive permissions granted during development and never reduced
- Insecure Cloud Deployments – Misconfigured cloud IAM roles and metadata service exposure
- Long-Lived Secrets – Static credentials with no expiration or rotation schedules
- Environment Isolation – Shared credentials across development, staging, and production
- NHI Reuse – Single service accounts shared across multiple applications
- Human Use of NHI – Developers using service account credentials for interactive access
Organizations should assess their NHI security programmes against these categories to identify gaps and prioritize remediation efforts.
Meeting Regulatory and Compliance Requirements
NHI governance directly supports compliance with major regulatory frameworks:
- SOC 2 Compliance: Common Criteria CC6 (Logical and Physical Access Controls) and CC7 (System Operations) require an organization to restrict logical access through authentication and authorization, monitor system components, and periodically review access rights. Service account management, access certification, and behavioral monitoring directly mitigate these Common Criteria.
- ISO 27001:2022: Annex A.9 (Access Control) specifically addresses privileged access rights, requiring an organization to restrict and control allocation and use of privileged access rights. This includes service accounts and machine identities with elevated permissions. Regular review of user access rights (A.9.2.5) must consist of non-human identities.
- PCI DSS 4.0: Requirements 7 (Restrict Access to Cardholder Data) and 8 (Identify and Authenticate Access) specifically require least-privilege access and unique authentication credentials for all users and systems. Organizations must also document and review all service accounts that have access to cardholder data environments, implement strong authentication and review access on a regular basis.
- GDPR: Article 32 requires appropriate technical and organizational measures to ensure security, including pseudonymization, encryption, and the ability to ensure ongoing confidentiality. Data minimization (Article 5) applies to machine identities; therefore, service accounts should only be able to access personal data required for the specific purpose of the identity.
- HIPAA: The Health Insurance Portability and Accountability Act requires covered entities to implement technical safeguards under the Security Rule, which include unique user identification and automatic logoff . Although HIPAA was written before there were significant service accounts for identity for machines, and although it's not expressly stated, it implies that these safeguards apply to any electronic protected health information (ePHI) access that may not involve an individual identity, like service accounts.
Organizations demonstrating mature NHI governance programs satisfy auditor requirements across all these frameworks while reducing actual security risk.
Best Practices for Securing Non-Human Identities
Proven practices for securing non-human identities (NHIs) comprise established practices for managing NHI security across the phases of prevention, detection, and response across the entire NHI lifecycle, which help to primarily mitigate credential compromise risk and limit the blast radius if a compromise does take place.
To preempt any exploitation, enforce least privilege and a just-in-time (JIT) access model by defaulting to the minimum permissions necessary for that individual action or function and granting JIT access elevation for privileged functions (tasks requiring administrator access) which only grants temporary administrator access when necessary with automatic revocation.
Use short-lived credentials with de-escalating lifetimes or with limited lifetimes, like OAuth tokens, AWS STS temporary credentials, or secrets from a vault. Set short-lived authorization protocols to the minimum acceptable lifetime, preferably hours versus days, and days versus months if feasible.
Automate discovery through identity governance and administration (IGA) or cloud infrastructure entitlement management (CIEM) platforms for continuous discovery of NHIs in cloud environments. CIEM solutions identify overprivileged identities and provide recommendations for right-sizing roles, privileged access, or sharing of privileged sessions when required for investigation or unless stated on an inclusion/exclusion basis.
Rotate keys and certificates automatically via a scheduled rotation, especially for long-lived credentials that are not rotated in line with policies, with an extra layer of protection when keys or certificates have overlapping lifetimes, to maintain uninterrupted application operations. Monitor subsequent rotations, and alert if they fail.
Log and monitor all events from NHIs via security information and event management or orchestrated security tooling, with monitoring a forward of NHI authentications, API requests, logging and/or resource access. Include configuration correlation rules that flag credential abuse patterns from the NXI event fields.
Migrate all credentials to secrets managers (HashiCorp Vault, AWS Secrets Manager, Azure Key Vault) for centralized secrets management. Remove hardcoded credentials from application source code, config files, and container images.
Assign ownership and accountability by assigning every NHI to a team or person. Document the business purpose, permissions, and expected behaviour for each NHI.
Separate environments and credentials by creating a separate identity for development, staging, and production; never use credentials across environments.
Have robust audit logging by turning on detailed logging for NHI authentication, authorization decisions, and resource access. Keep logs as long as required.
Act quickly when you suspect a compromized credential by practicing an incident response playbook for that specific scenario. Practice redeploying credentials or credential revocation. The 2024 Snowflake breach showed that compromised credentials from late 2020 were valid and exploitable; organizations need to identify and revoke compromised credentials within hours, not years.
Future Outlook – Non-Human Identity Governance in 2025 and Beyond
The future of NHI governance involves increasing automation through AI-driven analytics, tighter integration with security operations, contextual access decisions adapting to real-time risk, and recognition as a fundamental pillar of enterprise identity governance.
AI-driven identity analytics will become increasingly sophisticated at establishing behavioral baselines for NHIs and detecting subtle deviations indicating compromise. These models will correlate NHI activity with broader threat intelligence, application deployment patterns, and business context. Rather than simple threshold-based alerts, future systems will understand that a Lambda function typically calls three specific APIs during business hours; any deviation triggers investigation.
Contextual access control will replace static permission policies with context-aware access decisions considering identity, resource, location, time, recent activity, threat intelligence, and environmental risk. Adaptive authentication will dynamically adjust access based on real-time risk assessment. If threat intelligence indicates active exploitation of a specific API vulnerability, systems may automatically require additional verification for NHIs accessing that API until patches are deployed.
Cloud-native governance and CIEM integration will become inseparable as enterprises complete cloud migration. CIEM capabilities will merge with traditional IGA platforms, providing unified governance across on-premises and cloud identities. Organizations will no longer distinguish between "identity governance" and "cloud entitlement management"; they're converging into a single discipline.
Regulatory and compliance evolution will explicitly address non-human identities. Future revisions of SOX, PCI DSS, HIPAA, and GDPR will likely mandate specific controls for machine identity governance, credential rotation, and access certification. Early indicators suggest regulators are recognizing that machine credentials represent a distinct attack surface requiring specialized controls.
Organizations that establish comprehensive NHI governance today position themselves for long-term competitive advantage. As regulatory requirements tighten and cyber insurance premiums reflect NHI risk posture, lagging organizations will face increasing pressure to adopt mature practices. The question is no longer whether to implement NHI governance, but how quickly you can establish it before the next breach.
Conclusion
Non-human identities represent both the backbone and vulnerability of modern digital infrastructure. With organizations managing 144 machine identities per employee and breaches like Snowflake (165 organizations), CircleCI (5,000+ credential rotations), and the New York Times (4,000+ exposed secrets) demonstrating active exploitation, treating NHI governance as a strategic imperative is no longer optional. Organizations need unified platforms providing comprehensive visibility, automated lifecycle management, and continuous monitoring across all machine identities. Those who establish mature NHI programs today will meet evolving regulatory requirements and reduce security risk, while competitors struggle with reactive, fragmented approaches to an accelerating threat.
Ready to secure your non-human identities?
Modern identity governance platforms extend enterprise-grade IGA capabilities to machine identities, providing automated discovery, lifecycle management, access certification, and continuous compliance across cloud, on-premise, and hybrid environments. Transform identity governance from a reactive burden to a proactive security enabler.
Frequently Asked Questions (FAQs)
1. What are examples of non-human identities?
Non-human identities include service accounts, API keys, OAuth tokens, cloud workload identities (AWS IAM roles, Azure managed identities), container credentials, IoT device certificates, and RPA bots. Any digital credential enabling machines or automated processes to authenticate qualifies as a non-human identity.2. Why are non-human identities important?
NHIs enable the automation, integration, and scalability of modern infrastructure. However, they outnumber human identities by up to 144:1 according to Entro Security, often hold excessive permissions, and lack traditional security controls, making them attractive targets for attackers.3. How do you manage non-human identities securely?
Secure NHI management requires comprehensive discovery, centralized secrets management, automated credential rotation, continuous access reviews with least privilege enforcement, and behavioral monitoring. Unified IGA platforms treat NHIs as first-class entities alongside human identities.4. What tools help secure non-human identities?
IGA platforms provide unified governance, CIEM tools identify overprivileged cloud identities, secrets managers (Vault, AWS Secrets Manager) handle credential storage and rotation, and SIEM tools monitor NHI activity for anomalies. Organizations typically need an integrated ecosystem rather than a single tool.5. Are non-human identities part of IAM or IGA?
NHIs span both domains. IAM provides the authentication and authorization mechanisms, while IGA governs lifecycle management, access certification, policy enforcement, and compliance reporting. Modern IGA platforms incorporate machine identities as first-class entities.6. How do non-human identities differ from human identities?
NHIs are created programmatically by developers, authenticate using API keys or certificates rather than passwords, outnumber human identities by orders of magnitude, and often lack clear ownership or expiration policies, unlike human accounts tied to HR systems. They also cannot use multi-factor authentication, requiring different security controls.7. What is the biggest risk with non-human identities?
Overprivileged credentials combined with lack of visibility. Veza's research found 99% of cloud service accounts are over-permissioned, yet fewer than 5% of permissions are used. Compromised NHIs provide broad access without triggering MFA or behavioral analytics designed for human users.8. How often should API keys and service account credentials be rotated?
Rotation frequency should be risk-based: high-privilege credentials weekly or daily, standard service accounts monthly or quarterly. The trend favors ephemeral credentials that expire automatically within hours (AWS STS, OAuth tokens, Vault dynamic secrets), eliminating manual rotation entirely.



