User Access Review Best Practices for Security & Compliance in 2026

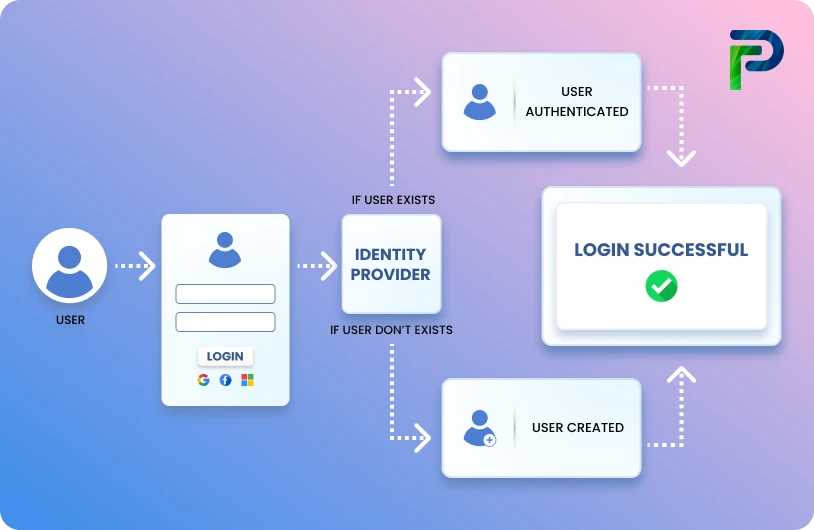
A User Access Review (UAR), also known as user access auditing, is a formal, repeated assessment to verify that users only have the access they need based on their current roles and responsibilities. It is a way to make sure that a user's access does not exceed their job responsibilities in order for organizations to ensure least privilege, as well as ensure stale or excessive permissions are eliminated. UARs apply to employees, contractors, and third-party users and allow IT, security, and compliance varying degrees of visibility and control to protect sensitive access management systems.
In today’s constantly evolving businesses, access management often cannot keep pace with employee roles, responsibilities, or job status. Employees may transfer departments, contract workers leave a project, and third-party engagements may cease, yet access may still remain. If not taken care of, employees may experience privilege creep, orphaned accounts, and non-compliance risk, leading to insider threats and data breaches.
In this blog post, we will explore UARs, detailed process steps for review, best practices, common challenges, streamlining with automation, and the future of access governance in 2025.
Key Takeaways
- Ongoing access opportunities can quietly elevate the risk for both insider threats and unauthorized data exposure.
- Regulatory compliance (SOX, HIPAA, GDPR, ISO 27001, PCI DSS, SOC 2) requires consistent and documented access reviews, so there are procedures in place.
- Enforcing least privilege stops employees and contractors from collecting excessive permissions.
- Automation is an outstanding efficiency improvement, reducing mistakes and suggestions to fix things quickly.
- Addressing high-risk accounts makes sure the most sensitive systems are being protected.
- When you create a document to follow through every step of the process through to completion, you create evidence for any compliance and help overall security standing.
What is a User Access Review?
A User Access Review (UAR) is an established security procedure to confirm that a user’s permissions and privileges allow them to be compliant with their job functions. A UAR ensures that employees, contractors, and partners have the exact level of access that is needed for them to perform their jobs and nothing more. UARs are not a one-time occurrence, but a continuous control that helps strengthen security and compliance as they ensure the principle of least privilege is being validated on an ongoing basis.
The purpose of a User Access Review is to eliminate privilege creep (the accumulation of unnecessary permissions over time). Users often retain access from previous roles, projects, or out-of-date responsibilities when they are not subjected to reviews. In a UAR, managers or administrators evaluate the permissions and privileges assigned to each user in a systematic fashion to see if they are aligned with a user's current job duties and organizational policies. The process enables the user to only have access to information and resources that are necessary for them to perform their job, which minimizes their exposure to sensitive systems and helps to close compliance gaps.
Key Objectives of User Access Reviews:
- Validates “least privilege” access - Verifies that all access rights for each user are reviewed with the principle of least privilege access to reduce risk.
- Verifies compliance with regulatory standards - Standards such as SOX, ISO 27001, HIPAA, GDPR, and industry best practices require continuous periodic access reviews to ensure that unauthorized or unneeded data exposure does not occur.
- Involves IT and security, and accountability leaders - Reviews require considerable cross-functional activity to ensure that all business, security, and compliance requirements are executed.
Why User Access Reviews are Critical?
Organizations expose themselves to multiple risks by not conducting regular User Access Reviews (UARs). Unexamined access rights can lead to compliance failures, privilege creep, and insider threats that can cause financial, legal, and reputational harm.
When people aren’t regularly having their permissions validated, they can hold onto access to systems or data they no longer require. Over a period of time, this can create unnecessary gaps in security and make it increasingly difficult for IT teams to identify and block misuse. The potential fines for regulatory issues and the damage caused by a data breach are costly enough to consider on their own, but can also be catastrophic if overlooked.
The key reasons why UARs are so important are:
-
They stop unauthorized access before it starts
UARs mitigate unauthorized access to sensitive systems or data by allowing only the right users to have the right permissions, which hinders unauthorized access before it can happen. These proactive control measures can significantly lessen breach probability and allow for the enforcement of least privilege across the organization. -
Support regulatory compliance
Many frameworks (SOX, ISO 27001, HIPAA, and GDPR) require organizations to conduct periodic access reviews. Declaring compliance with regulatory frameworks will minimize the risk and potential success a regulator may have if expecting a period review at the time of a suspension of a particular regulation. With continued UARs, organizations are less likely to incur hefty fines, suffer failed audits, and/or lose their certifications altogether. -
Prevent privilege creep
Many employees accumulate unnecessary permissions as they change roles and/or complete projects across departments, leading to privilege creep. UARs can routinely review unneeded permissions and revoke any excess permissions, stopping privilege creep and limiting unnecessary exposure to sensitive resources. -
Reduce insider threats
Not all threats are external. Permissions can be exploited by malicious insiders (or even misguidedly by well-meaning employees), leading to an even worse-case scenario. UARs help mitigate this risk by ensuring users only have access that is warranted by their current defined scope of responsibilities. -
Make audits (much) easier
Audit preparation often requires actual proof that access controls are doing what they are intended to do. Automated, well-documented UARs take the form of audit trail-ready UAR reports, support simple report extraction for IT, compliance, and/or security teams, and limit the time that auditors must spend on the project.
Step-by-Step User Access Review Process
A repeatable process is a key element in a successful user access review. It establishes that each review cycle will follow a consistent process resulting in increased accuracy, consistency, and compliance across the organization. When you set up a user access review workflow, the user access review is no longer a one-off activity, thereby reducing the chances of errors, missed accounts, or unnecessary audits.
Below are the steps you can follow:
Step 1 – Define the Scope and Policy
The initial step is to effectively define the review’s scope, including which systems, applications, and users to include, such as SaaS applications, cloud providers, financial systems, HR systems, third-party connections, on-premises servers, and databases. Clearly defining the scope will help ensure the review does not miss out any major systems or higher risk user groups.
Step 2– Establish the Policy
Once the scope is clear, the next step is to define the rules that will guide the review. A strong policy outlines the frequency of reviews, risk-based prioritization, and criteria for review. Including stakeholders such as IT administrators, managers, and compliance officers early is important.
Step 3 – Gather Access Data from All Systems
After the initial definition phase, the next step is to compile all user access data from all interconnected systems. This should include who has access, what type of access, and when it’s granted, so a complete scope can be developed, and ensure that nothing is overlooked, missed, or unclear. Using tools like Okta or Active Directory can help you automate this process to gather user data for you faster and with less opportunity for error.
Step 4 – Validate Against Existing RBAC Policies
Now that we have gathered the relevant data, it is time to assess this data against the organization’s Role-Based Access Control (RBAC) model. The objective is to determine whether each user or individual truly needs the access they have been assigned. If a user has moved to a new role, switched departments, or isn't using a certain application, any granted permissions should be adjusted or removed. This ensures the access is updated based on the current role and helps with the avoidance of privilege creep, where users continuously accumulate rights without realizing it.
Step 5 – Revoke or Adjust Excess Permissions
Excessive permissions, or privilege creep, can present serious risks. At this stage, reviewers should cancel unnecessary accesses or change permissions to comply with the least privilege principle. This step greatly reduces the chance of insider threats or unnecessarily exposing data.
Step 6– Focus on Privileged Accounts
Privileged accounts (i.e., admin-level or root accounts) have the highest risk if misused. Therefore, these accounts should be heavily scrutinized during reviews by verifying they are still necessary, acceptable to monitor, and assigned to acceptable, trusted actors.
Step 7 – Document All Changes
All decisions, changes, and revocations must be documented to prepare for an audit. This documentation should include timestamps, the name of the reviewer, why the changes were made, and evidence of approval. Documenting properly ensures accountability and shows that the organization has evidence of compliance during audits.
Step 8 – Schedule the Next Review
Finally, user access reviews shouldn't be a one-off review. User access reviews should be done with regularity, quarterly for most systems and monthly for high-risk or privileged accounts. The timelines for the next review should be set in advance to ensure consistency and that there are no gaps in compliance.
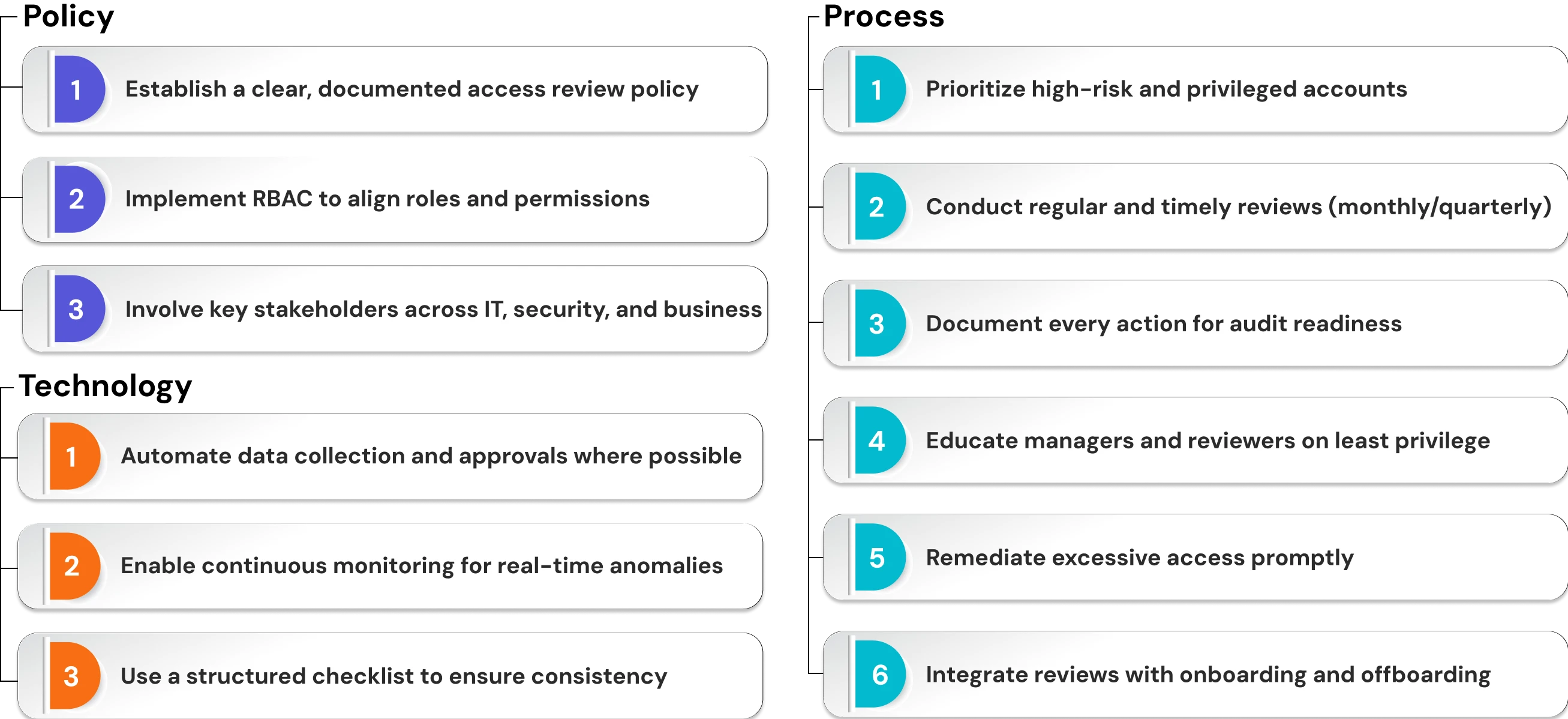
12 Best Practices for User Access Reviews
Best practices ranging from automation to staff training can help users access reviews, turning a tedious compliance activity into a seamless process that can enhance security. By following best practices, user access reviews can be efficient, repeatable, prepared for audits, and reduce the risks associated with privilege creep and insider threats.
1. Establish A Clear Policy
When starting an access review, you should have a clear access review policy that identifies goals, timing, scope, and responsibilities. A written access review policy helps provide consistency, sets expectations for the stakeholders' involvement, and provides accountability for the different phases of the process.
2. Implement Role-Based Access Control
Use Role-Based Access Control (RBAC) so that the access review process is simplified. By aligning access rights to job roles, you will reduce permissions complexity, and it will make it easy to identify a discrepancy. RBAC also allows for the practice of least privilege, which means the user only receives needed access.
3. Automate Where Possible
Manual reviews take time and have a greater risk of human error. Add supporting automation tools or IAM/IGA solutions to collect access information, send reminders, and recognize licensing/access excesses. By automating the review process, you reduce the time and factors contributing to human error, allowing for scalability.
4. Involve Key Stakeholders
Don't leave access reviews 100% with IT. Involve department heads, managers, security teams, and compliance officers. Stakeholders are critical to providing context to user roles and responsibilities and will ensure you are validating existing access against legitimate business needs.
5. Prioritize High-Risk Accounts
Not all accounts are created equally with respect to risk. Consider addressing privileged accounts, admin users, and access to sensitive systems initially. It is better to provide a review opportunity for the riskiest accounts promptly while also providing a broader review of your access universe.
6. Document Everything for Audits
Auditors want to see proof. Keep details of existing access and the changes requested, approval, date, and time of the reviewer, and any notes documenting the review. Documentation is a way to demonstrate compliance, but it also leaves an audit trail, should there be a formal investigation requiring disclosure.
7. Conduct Timely, Regular Reviews
Be consistent. Base review frequency on the risk level of the account. Continued reviews quarterly for standard accounts and monthly for high-risk accounts will help best mitigate privilege creep, identify dormant accounts, and comply with any applicable regulatory guidelines.
8. Continuous Monitoring
User access reviews should not be conducted only at scheduled intervals. Continuous monitoring tools should be utilized to identify suspicious access behaviors, log-in events, or increases in end-user privileges as they happen. This proactive approach will improve security beyond compliance.
9. Educate Personnel
People are the most important aspect of the review process. Train your managers, IT staff, and reviewers on how to evaluate their users' permissions, measure the risk of different permissions, and identify least-privilege. Better-trained people are less likely to make mistakes and are more likely to perform accurate reviews.
10. Promptly Remediate Issues
Identifying excessive permissions is only half of the job. Once excessive permissions are detected, it is imperative to act quickly to remove or adjust the permissions. The longer risk is allowed to remain, the greater the chances of an incident occurring, and the worse the security posture of the organization will become over time.
11. Integrate With Onboarding/Offboarding
Integrate access reviews into employee lifecycle management for consistent provisioning and timely deprovisioning of user accounts during the employee lifecycle. During the onboarding process, access should be provisioned accurately from day 1 (which means granting only what is necessary for the new hire's specific role); during the offboarding process, deprovisioning should occur immediately to close down the new hire's access and remove orphaned accounts from the system. Incorporating UARs into these processes eliminates security gaps that attackers will seek to exploit, and also tightly maintains access, in alignment with user status.
12. Use A Structured Checklist
A structured checklist allows reviewers to maintain consistency and ensure critical steps are not missed. The checklist can include whether to verify least privilege, whether privileged account(s) are validated, whether changes have been documented, and whether proper stakeholders have signed off.
Common Challenges & How to Overcome Them
Even when organizations value user access reviews, it's often the actual reviews that prove challenging. The manual processes, lack of visibility, and misalignment between stakeholders can quickly hinder the efficiency of a UAR program and, even worse, create not only inefficiencies in the review process but also increase the likelihood of missing violations and compliance inadequacies.
Key Challenges:
- Complexity of multi-system environments:
Most enterprises run a mix of on-premises, cloud, and SaaS identity systems, making it difficult to collect consistent access data from all systems, which is labor-intensive and prone to human error. - Manual errors and delays:
Organizations that rely on a spreadsheet-based review for UAR, or sole email approvals by reviewing authorities, often encounter inconsistencies, forgotten tasks, and missed deadlines, jeopardizing security and compliance. - Lack of stakeholder participation:
Without business managers, IT teams, or auditors being aligned, user access reviews can lose value and become "just a checkbox" as opposed to a worthy security control.
Solutions:
- Leverage automation tools:
Automating the entire process from data collection, review notifications, and access certifications greatly reduces human error and can speed up the process. - Improve cross-department communication:
An ongoing and collegial relationship and communication between IT, compliance, and business leaders assures that access reviews are meaningful from both a security and business perspective. - Adopt centralized IAM/IGA platforms:
A central place for identity and permissioning provides a single source of truth, making it easier to become more aware of everything, simplifying reporting, and facilitating audits.
💡 Note: Many organizations struggle with fragmented tools and manual processes for user access reviews. Tech Prescient’s Identity Confluence solves this with automated reviews, continuous compliance, and unified governance, helping you move beyond box-checking to truly proactive identity security.
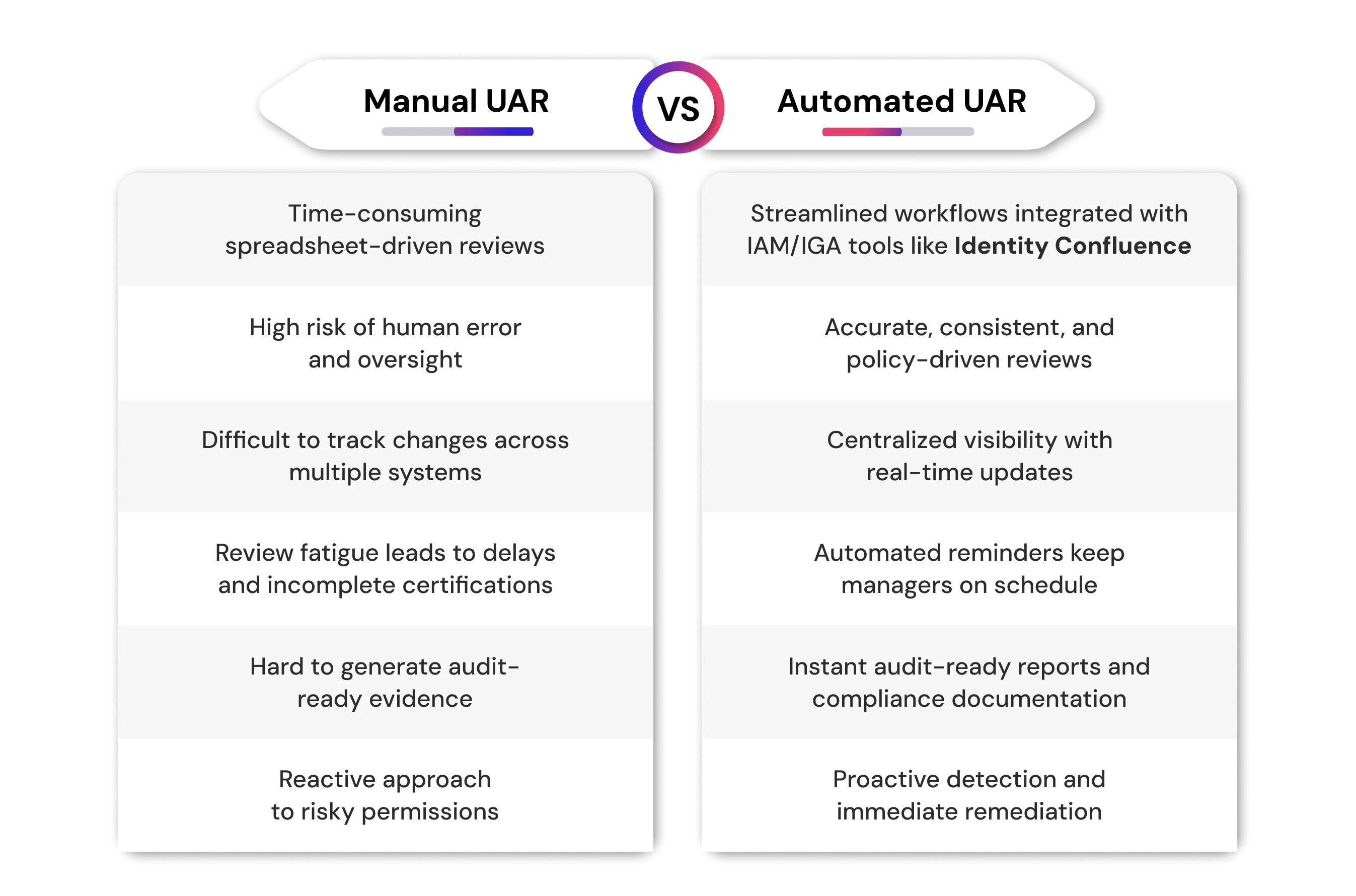
How Automation Improves User Access Reviews
Manual reviews are not feasible in today's rapidly changing and compliance-heavy environment. Automation actively transforms user access reviews by: Increasing review frequency, maximizing human time and effort while minimizing human error, and detecting permissions you would want to remediate in real-time. With less time spent chasing spreadsheets, approvals, & manager feedback, IT teams can return to making informed decisions about the risks they are willing to take, while auditors feel more confident in the integrity of the review process.
The Key Elements to the Benefits of Automation:
-
Integration with IAM/IGA tools like Identity Confluence - Provide access governance with the centralization of identity data across applications, systems, and cloud environments, while keeping there in one place to allow for one source of truth.
-
Generates audit-ready reports - Gathers information automatically to evidence compliance, while increasing the internal and external stakeholders' ability to demonstrate compliance with various things such as SOX, HIPAA, and GDPR.
-
Automates reviewer notifications - Provides review reminders and dashboards to notify managers and reviewers of the deadlines, while helping them to provide timely input and reducing the timeframe between review cycles.
Final Thoughts
User access reviews no longer represent compliance; these reviews represent trust as your organization demonstrates how it protects data and mitigates risk. In an environment characterized by constantly changing regulations, hybrid workplace environments, and a plethora of complex insider and external threats, UARs provide confidence that the right people have the right access at the right time and nothing more.
Organizations that utilize access reviews as a security practice rather than a compliance exercise see clear benefits in terms of fewer risk gaps, better audit/review preparedness, and a more engaged security culture across the organization. When organizations have adequate automation and clarity around policy, UARs move from a manual burden to a proactive control, creating efficiency while establishing confidence and peace of mind.
In short, access reviews are not only about compliance today, but are a way to future-proof your business by proactively identifying tomorrow's risks.
NEXT STEPS
Ready to take your access reviews to the next level?
Identity Confluence helps you automate reviews, generate audit-ready reports, and enforce least-privilege access with ease.
- Get started faster → Explore how automation can simplify your next compliance cycle
- See it in action.
Frequently Asked Questions (FAQs)
1. How to conduct a user access review?
Begin by establishing the scope; you will need to identify which systems, applications, and user groups are being included. You will need to collect access data from all the various custom and maintained systems, including HR records, IAM systems, and cloud applications, and centralize this data. You will then compare each user's permissions with their previous function to identify misaligned access and confirm privilege creep. You will take out or adjust excessive access, as needed; you will also ensure each step is documented in some way for audit purposes.2. How often should user access rights be reviewed?
The frequency of your reviews will depend upon the sensitivity of the data and any applicable regulatory requirements. A quarterly review should provide a balance of security risk and operational workload for most systems. The frequency may be changed when dealing with high-risk accounts (like administrators and privileged users). The easiest way to mitigate risk to the organization is by taking an active approach towards preventing unauthorized access and privilege escalation, which may require monthly or continuous monitoring.3. Who should perform user access reviews?
User access reviews involve various stakeholders and require multiple participants. IT security teams will typically audit the side of the review that will focus on the technical requirements, and system owners can validate the permissions for their area. Managers, or department heads, will confirm that an employee has access that aligns with their job function. Within all of these stakeholders are checks and balances that support accuracy, accountability, and compliance.4. How to audit a user access review?
Keep records of every review that occurs (approvals, changes, removals) and be able to produce an audit-ready report for when, who, and what was reviewed. This is important for regulatory compliance documentation, but also helpful in detecting routine access issues or policy concerns.5. What is a user access review checklist, and why is it important?
A user access review checklist is a prepared structure, helping you follow every important step of a review as you progress. It will typically include items like: Define scope, Gather access data, Validate permissions, Address excess access, and Document actions. It is helpful to use a checklist to ensure consistency, eliminate errors, and provide sound evidence to support audits and compliance reports.5. Can automation improve the effectiveness of user access reviews?
Yes, absolutely. Automation provides significant efficiency and accuracy. For example, there are IGA/IAM tools like Identity Confluence that will automatically collect access data, highlight risky access, and generate an audit-ready report. Automated reminders to managers and other stakeholders not only draw attention to pending remedial actions but also deliver continuous oversight to minimize privilege creep or unauthorized access.