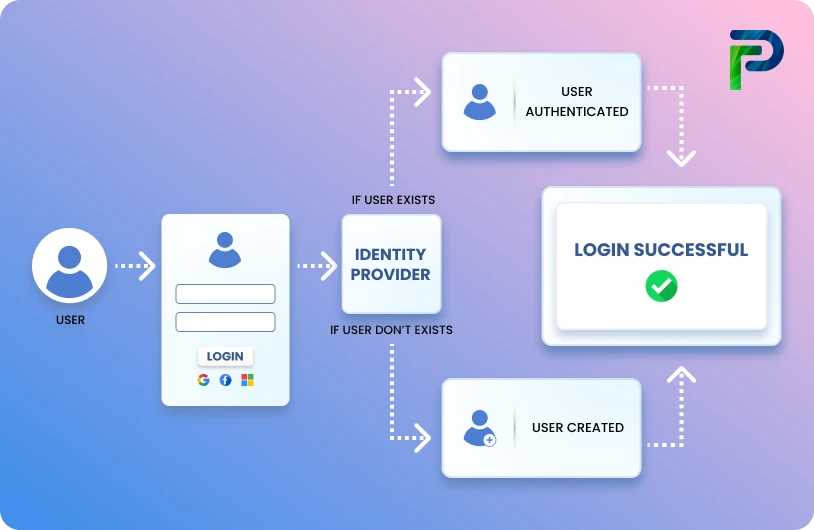
What Is SSPM (SaaS Security Posture Management)?

SaaS Security Posture Management is the practice and set of tools that gives security teams continuous visibility into how SaaS applications are configured, used, and exposed. It helps monitor settings, user access, third-party integrations, and anomalous behavior across your SaaS stack. In many ways, SSPM acts like CSPM did for cloud infrastructure; it makes SaaS risk manageable, not reactive.
Critical business operations in today's organization are powered by SaaS platforms such as Microsoft 365, Salesforce, Workday, and ServiceNow. With over 100 SaaS apps often used in big enterprises, security teams must deal with uneven controls and hidden dangers inside each service. Native admin consoles and point solutions frequently leave gaps, particularly in terms of misconfiguration, overprivileged access, and SaaS-to-SaaS interfaces. SSPM arose to bridge those gaps, providing businesses with a consistent approach to inventorying SaaS usage, enforcing policy, resolving problems, and mitigating vulnerability.
In fact, according to Qualys, in the past year, 28 % of organizations have experienced a cloud- or SaaS-related data breach, meaning more than one in four enterprises were impacted. Moreover, a recent survey by AppOmni found that 31 % of organizations reported SaaS exploits, up five points over last year. These trends underscore why SSPM is not optional; it’s essential. In this blog, we’ll explore what SSPM is, the risks it mitigates, how it works, how it compares with other tools, and what to look for when choosing an SSPM vendor.
Key Takeaways :
- Understanding SaaS Security Posture Management and why it is important for securing SaaS applications.
- Discovering how SSPM protects against misconfigurations, over-privileged access, shadow IT, and compliance violations.
- Exploring how SSPM continuously monitors applications, assesses risks, detects threats, and provides guided remediation.
- Understanding the advantages of SSPM and how it differs from CASB, CSPM, and SIEM.
- Finding out how to choose the right SSPM solution and the role of AI, identity-first security, and Zero Trust in the future.
What Is SSPM?
According to Gartner, SaaS Security Posture Management (SSPM) refers to tools that continuously evaluate risks and maintain the security posture of SaaS applications. In essence, SSPM provides organizations with a dedicated toolset to protect their SaaS ecosystem by spotting misconfigurations, controlling user permissions, and ensuring compliance across the digital landscape. Unlike traditional monitoring, SSPM solutions go further as they proactively help prevent security gaps, protect sensitive data, and minimize risks in real time.
Because SaaS applications are accessed over the internet from virtually any device and are often outside direct IT control, they introduce risks such as misconfigurations, over-privileged access, shadow IT, insecure integrations, and compliance gaps. SSPM solutions detect, alert, and remediate these risks automatically, giving organizations a proactive way to protect their SaaS environment.
What Problems Does SSPM Solve?
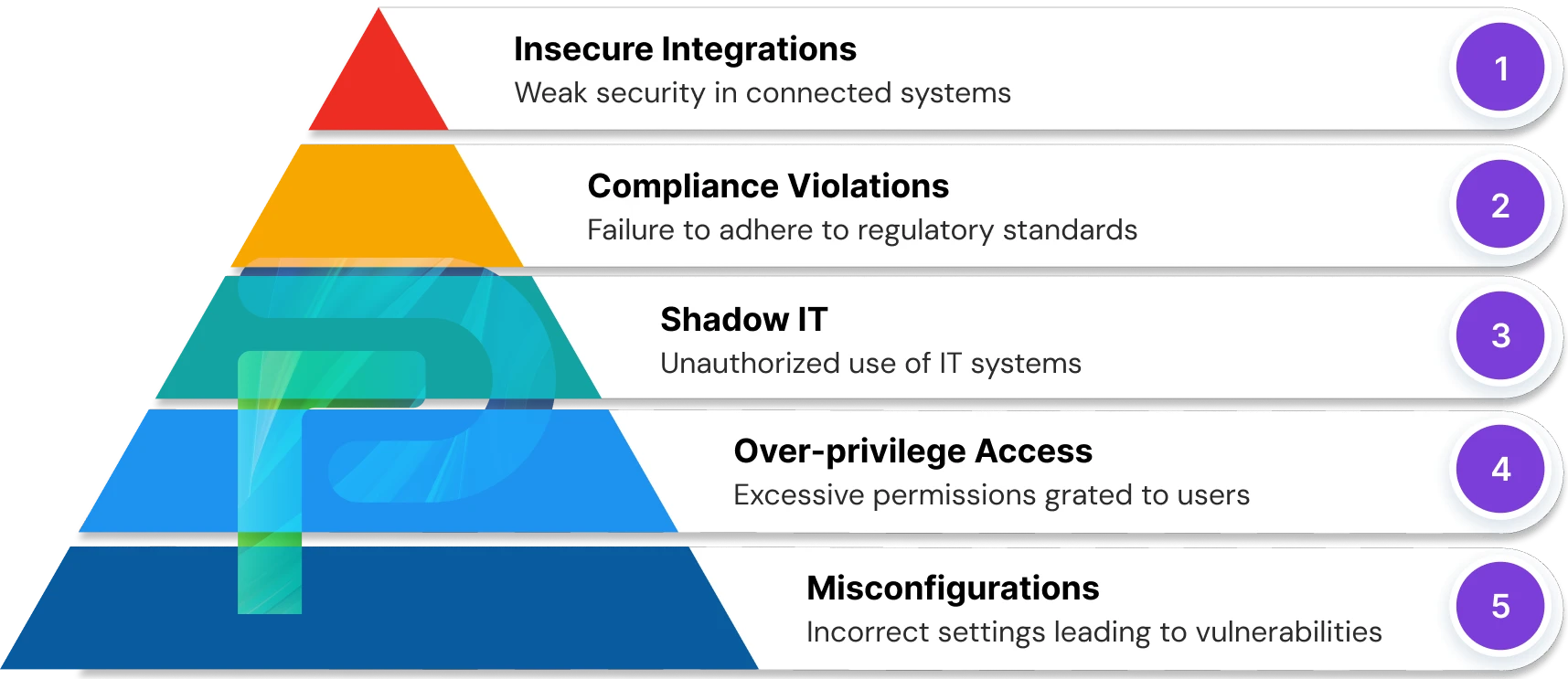
In a modern SaaS environment, security risks can appear quickly and often go unnoticed. SSPM helps close these gaps by focusing on the most common problem areas:
1. Misconfigurations
Misconfigured security settings in SaaS applications can accidentally expose sensitive data. Examples include giving users overly broad access permissions or failing to enable multi-factor authentication. SSPM solutions continuously scan SaaS apps for weak settings and alert security teams so they can correct issues before attackers can exploit them.
2. Over-Privileged Access
Users and third-party apps often receive more permissions than they actually need to perform their work, which increases the risk of insider threats or accidental data leaks. SSPM enforces the principle of least privilege across all SaaS accounts by identifying and correcting excessive permissions, ensuring that only the right people have access to the right data.
3. Compliance Violations
Many organizations must follow strict regulatory standards such as GDPR, HIPAA, or SOC 2 to securely handle sensitive data. However, not all SaaS applications include built-in compliance controls, making it difficult to stay within legal requirements. SSPM evaluates SaaS app configurations against these frameworks, identifies gaps, and helps remediate them before they lead to fines or reputational damage.
4. Shadow IT
Employees sometimes use unapproved SaaS applications that have not been vetted by the IT or security team. These tools may lack proper security features and can go unnoticed in routine audits. SSPM detects these unsanctioned applications within the SaaS environment and brings them to the attention of security teams so they can evaluate or block them as needed.
5. Insecure Integrations
Modern SaaS environments are full of third-party apps, API connections, and SaaS-to-SaaS integrations. If one of these integrations is insecure, it can create a back door into otherwise protected systems. SSPM continuously monitors all these connections, flags risky or unauthorized integrations, and helps organizations control access to keep their data safe.
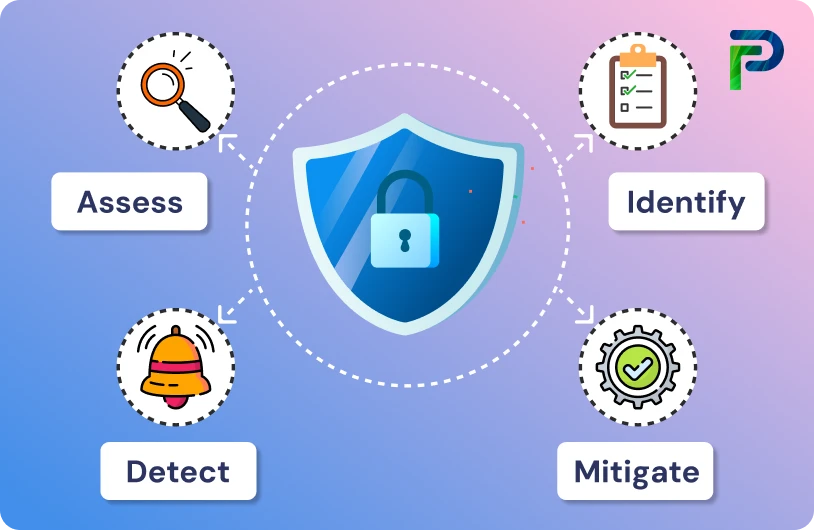
How Does SSPM Work?
SSPM delivers a multi-layered approach to securing SaaS applications. It combines real-time monitoring, risk analysis, automated remediation, and centralized visibility so security teams can stay ahead of misconfigurations, unauthorized changes, and compliance gaps across all cloud-based apps. Here’s how its core functions operate:
1. Continuous Monitoring
SSPM solutions use APIs to track SaaS application settings, configurations, and user activity in real time. This constant visibility helps identify security misconfigurations, excessive privileges, and suspicious behavior as soon as they occur. Any deviations from your organization’s security policies are flagged immediately so teams can respond quickly before risks escalate.
2. Risk Assessment
One of SSPM’s key strengths is benchmarking SaaS app configurations against internal security policies and industry standards. This risk assessment highlights misconfigurations, unauthorized changes, or vulnerabilities within your environment. Many tools also provide automated or guided steps to close these gaps without requiring manual intervention, reducing human error and improving security posture.
3. Threat Detection
Modern SSPM platforms extend beyond configuration checks to include identity threat detection and response (ITDR). By continuously monitoring privileged accounts and integrations, SSPM can spot unusual logins, suspicious privilege escalations, or risky third-party connections, enabling faster containment of threats inside SaaS environments.
4. Guided Remediation
When issues are detected, SSPM not only generates alerts but also provides actionable recommendations or automated fixes. Security teams can customize alerts to prioritize the most critical vulnerabilities, ensuring swift remediation and minimizing exposure time.
5. Visibility and Control
SSPM tools centralize all this information into a single dashboard view. Security teams can visualize trends, track remediation progress, benchmark compliance, and manage the security posture of every SaaS application from one place. This unified visibility simplifies oversight and strengthens control across your organization’s entire SaaS stack.
Benefits of SSPM
SSPM improves compliance, strengthens security, and drives efficiency across the SaaS ecosystem. By providing continuous oversight of configurations, identities, and integrations, SSPM allows organizations to move from reactive checks to a proactive, unified approach to SaaS security.
1. Proactive Security
SSPM helps security teams prevent breaches before they happen by constantly monitoring SaaS configurations, user privileges, and connected apps. It catches misconfigurations such as overly permissive sharing policies, disabled MFA, or risky guest access before they expose sensitive data. This proactive oversight ensures that SaaS environments remain aligned with your organization’s security baselines even as settings change.
2. Reduced Risk
Every new SaaS app, user, or integration increases the attack surface. SSPM limits this risk by centralizing visibility into identities, permissions, and SaaS-to-SaaS connections. It flags over-privileged accounts, orphaned users, and unapproved integrations so you can close potential entry points and reduce opportunities for data loss or privilege escalation.
3. Improved Compliance
Meeting regulatory requirements like HIPAA, GDPR, SOC 2, ISO 27001, or NIST frameworks can be challenging across multiple SaaS apps. SSPM simplifies compliance by continuously evaluating app settings against these standards, generating audit-ready reports, and providing clear evidence of controls. This transforms SaaS compliance from a manual, one-off exercise into a repeatable, automated process.
4. Enhanced Visibility
Modern organizations often use dozens or even hundreds of SaaS apps, some sanctioned, some unsanctioned. SSPM shines a light across the entire SaaS estate, inventorying all apps, third-party integrations, and permissions from a single view. Security teams can finally see which apps are in use, how they’re configured, and where risks may be hiding.
5. Operational Efficiency
SSPM reduces manual work by automating the most time-consuming parts of SaaS security, from configuration checks to compliance evidence gathering. Instead of chasing down screenshots or manually comparing settings across apps, security teams get actionable alerts, guided remediation, and centralized dashboards. This saves time, reduces human error, and allows teams to focus on mitigating real threats rather than tracking down data.
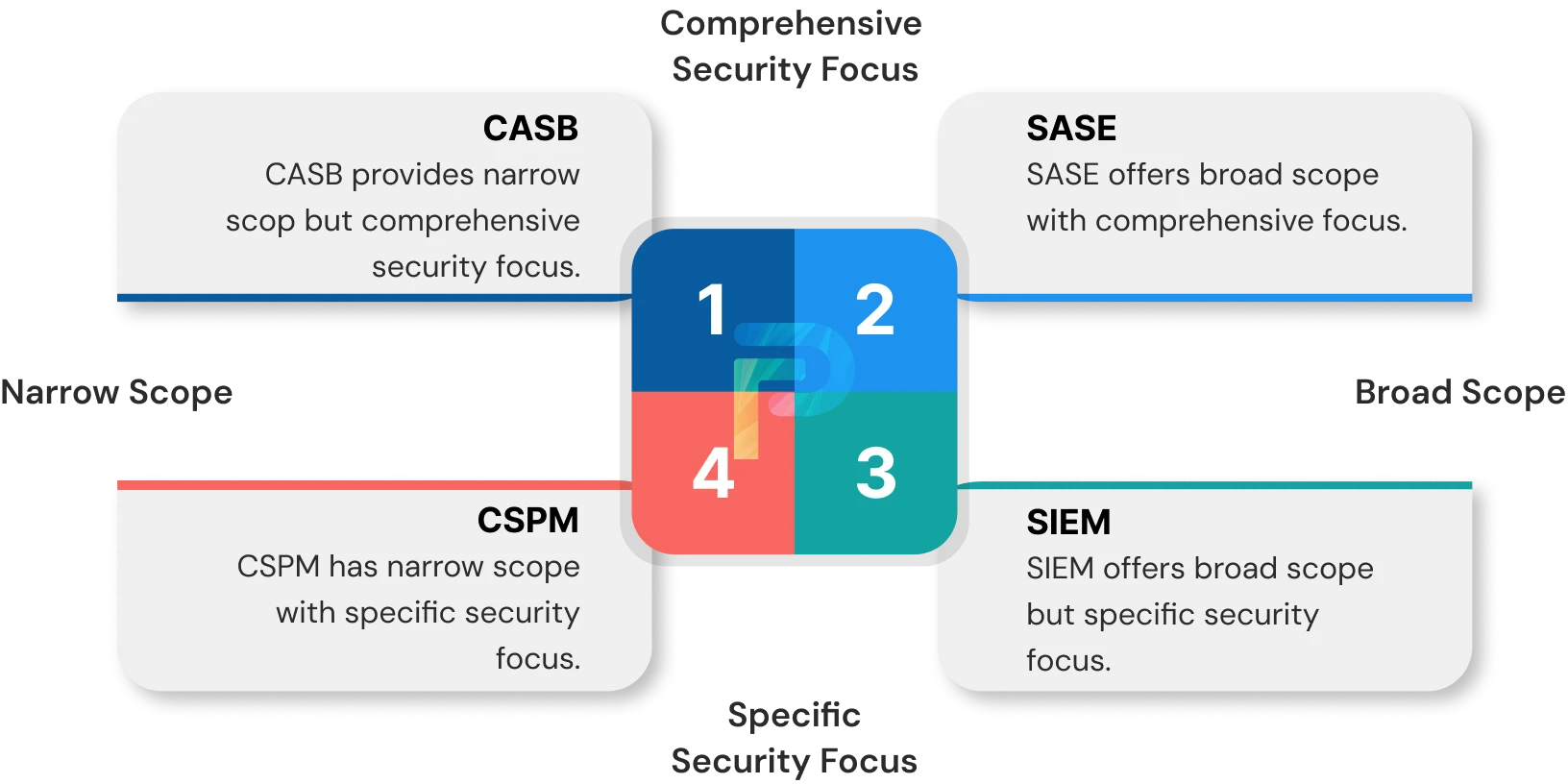
SSPM vs Other Security Tools
SSPM solutions do not replace existing security technologies. They fill a critical gap by providing deep, continuous protection for SaaS platforms themselves. You can think of SSPM as the layer that secures what happens inside SaaS apps, where your users work, where your data resides, and where attackers increasingly focus their efforts.
Below is a breakdown of how SSPM compares to other major security tools.
1. SSPM vs CASB
A Cloud Access Security Broker (CASB) focuses on controlling access to the cloud and securing data as it moves between devices and cloud applications. CASBs are effective at enforcing access controls, monitoring traffic, and protecting data flows.
SaaS Security Posture Management (SSPM) is dedicated to securing SaaS applications and addressing their specific security needs. It helps maintain compliance with security standards by continuously overseeing configurations, user access, and permissions across the organization’s SaaS environment.
2. SSPM vs CSPM
Unlike SSPM, which is limited to SaaS applications, Cloud Security Posture Management (CSPM) takes a broader approach by analyzing entire cloud environments across multiple layers of the computing stack. A CSPM solution scans:
- Infrastructure-as-a-Service (IaaS)
- Platform-as-a-Service (PaaS)
- Software-as-a-Service (SaaS)
- Containers
- Serverless functions
In addition, CSPM platforms often include capabilities beyond those of SSPM, such as:
- Vulnerability detection: Identifying exploitable weaknesses within cloud software.
- Incident response: Automatically responding to and mitigating active security threats.
SSPM focuses exclusively on SaaS applications such as Salesforce, Workday, or Microsoft 365. It ensures these apps’ security settings, access controls, and compliance align with organizational policies. Together, CSPM and SSPM cover both cloud infrastructure and SaaS layers for a complete security posture.
3. SSPM vs SIEM
Similar to SSPM, Security Information and Event Management (SIEM) plays a vital role in an organization’s cybersecurity strategy. While SSPM concentrates on securing SaaS environments, SIEM takes a broader approach by collecting and analyzing data from diverse IT infrastructure sources. This enables it to detect potential threats, anomalies, and signs of unauthorized activity or security incidents.
SSPM cybersecurity also draws on the capabilities of other solutions, including compliance and data security tools, and extends the value of existing technologies like CASBs. Its strength lies in adapting to fast-evolving SaaS environments while addressing the distinct security responsibilities of different stakeholders.
4. SSPM and SASE
A Secure Access Service Edge (SASE) framework integrates networking and security capabilities into a single cloud-based model. Core elements such as CASBs, Secure Web Gateways (SWG), and Zero Trust Network Access (ZTNA) often overlap or interface with SSPM solutions.
SSPM strengthens the SaaS layer inside SASE by ensuring that applications adhere to access controls, compliance policies, and threat protection standards within broader enterprise security goals. It complements rather than replaces other SASE functionalities.
5. SSPM vs CASB vs CSPM vs SIEM - Quick Comparison
| Sr No | Tool | Primary Focus | What It Secures | Strengths | Where SSPM Fits In |
|---|---|---|---|---|---|
| 1 | SSPM (SaaS Security Posture Management) | Continuously monitors and improves the security posture of SaaS applications. | Secures SaaS configurations, permissions, integrations, and compliance settings. | Provides real-time visibility into risks and guided remediation for misconfigurations and over-privileged accounts. | Adds an internal layer of protection by safeguarding what happens inside SaaS apps after access is granted. |
| 2 | CASB (Cloud Access Security Broker) | Controls and secures how users and devices access cloud apps and services. | Protects data movement between end-user devices and cloud applications. | Enforces access policies, monitors cloud traffic, and safeguards data in motion. | Complements CASB by monitoring and securing settings and activity within each SaaS app. |
| 3 | CSPM (Cloud Security Posture Management) | Assesses and improves the security posture of cloud infrastructure platforms. | Secures virtual machines, storage, networking, and serverless components. | Detects and remediates cloud infrastructure misconfigurations and policy violations. | Works alongside CSPM by focusing on SaaS apps, covering what CSPM does not. |
| 4 | SIEM (Security Information and Event Management) | Collects and analyzes logs and events across the IT environment. | Secures servers, endpoints, networks, and applications by identifying anomalies. | Offers centralized threat detection, compliance reporting, and incident response. | Feeds SIEM with SaaS-specific posture data, adding depth and context to its insights. |
Choosing SSPM Tools & Vendors
Selecting the right SSPM tool is not just about checking boxes; it’s about finding a solution that fits your organization’s security needs, compliance requirements, and long-term SaaS growth. The right vendor will give you visibility, control, and confidence in managing your SaaS ecosystem.
Key Features to Look For
-
Automation for Scale: Choose a solution that automates monitoring, risk scoring, and remediation. This reduces dependency on manual effort and ensures your security posture keeps pace with the rapid adoption of SaaS apps.
-
Built-in Compliance Mapping: A good SSPM tool should map security controls to regulatory frameworks such as GDPR, HIPAA, SOC 2, and ISO 27001. This helps your organization stay audit-ready and reduces the stress of meeting compliance standards.
-
Integration with Existing Stack: Look for vendors that support seamless integration with core SaaS platforms like Microsoft 365, Salesforce, Google Workspace, Slack, and also connect with SIEM, CASB, and IGA tools for holistic security.
-
Comprehensive Visibility & Discovery: The tool should not only track sanctioned applications but also discover unsanctioned or “shadow IT” SaaS usage, while monitoring misconfigurations and risky SaaS-to-SaaS integrations.
-
Guided or Automated Remediation: Beyond just flagging risks, the best SSPM solutions provide step-by-step remediation guidance or even automated fixes, so issues can be resolved quickly without overwhelming security teams.
Vendor Examples
Leading SSPM vendors include Adaptive Shield, known for deep integrations, advanced risk detection, and strong compliance features. AppOmni offers detailed visibility and continuous monitoring to help organizations protect sensitive data and maintain SaaS security controls. Zscaler integrates SSPM into its Zero Trust Exchange, combining posture management with access control and threat detection. These vendors highlight different approaches to SaaS security, giving enterprises the flexibility to choose a solution that best fits their scale, compliance needs, and security ecosystem.
Questions to Ask SSPM Vendors
Before finalizing a vendor, it’s important to ask targeted questions that reveal how well the solution aligns with your business needs. For example:
-
Coverage: Which SaaS applications and integrations are supported today, and how often are new ones added?
-
Automation Level: What percentage of remediation tasks can be automated, and what still requires manual intervention?
-
Scalability: Can the solution grow with our SaaS environment and support multiple cloud providers in the future?
-
Compliance Support: How does the platform help us prepare for audits and align with industry regulations?
-
Ecosystem Fit: How well does it integrate with our identity, endpoint, and security monitoring tools?
Asking these questions ensures you’re not only comparing feature checklists but also evaluating how the solution will perform in your real-world environment.
The Future of SSPM in 2025 and Beyond
As SaaS adoption accelerates, SSPM will continue evolving to address more complex threats, regulatory pressures, and identity-driven risks. The future of SSPM lies in deeper intelligence, tighter integrations, and alignment with modern security frameworks like Zero Trust.
1. The Role of AI in SSPM
Artificial intelligence and machine learning are set to transform SSPM by making security predictive rather than reactive. AI-driven engines will analyze large volumes of SaaS activity data to deliver predictive risk scoring, highlight anomalies before they escalate, and detect subtle patterns that indicate insider threats or compromised accounts. This means security teams will move from chasing alerts to proactively mitigating risks with higher accuracy and speed.
2. Integration with IGA and Identity-First Security
Identity will remain the new security perimeter in the SaaS world. SSPM solutions will increasingly integrate with Identity Governance and Administration (IGA) platforms, enabling enterprises to enforce least-privilege access across SaaS environments more effectively. By aligning posture management with identity-first security, organizations can gain granular visibility into who has access to what, when, and why, minimizing insider risks and tightening compliance.
3. Shift Toward Zero Trust SaaS Security Models
The broader security ecosystem is moving toward Zero Trust, and SSPM will play a crucial role in this shift. Instead of assuming any app or user is trustworthy, SSPM will continuously validate configurations, monitor access patterns, and enforce least privilege as part of a Zero Trust SaaS framework. This will help enterprises reduce their attack surface, limit the blast radius of breaches, and ensure SaaS applications remain secure even as the threat landscape evolves.
Final Thoughts
SaaS Security Posture Management (SSPM) is no longer optional; it is essential for safeguarding sensitive data and maintaining compliance across today’s sprawling SaaS ecosystem. By continuously monitoring configurations, detecting risks, and automating remediation, SSPM empowers businesses to stay ahead of misconfigurations, over-privileged access, and shadow IT.
While other tools address parts of the security puzzle, SSPM provides a dedicated layer of protection for SaaS apps, offering visibility, control, and compliance at scale. As AI, Zero Trust, and identity-first security become the new norm, adopting SSPM now sets organizations up for a more secure and resilient future.
To see how Tech Prescient, helps enterprises implement SSPM frameworks with deep expertise and automation-driven solutions -
Frequently Asked Questions (FAQs)
1. What is SSPM in security?
SSPM stands for SaaS Security Posture Management. It refers to tools that continuously monitor your SaaS applications for risks, misconfigurations, and compliance gaps. In simple terms, it helps you keep all your SaaS apps secure and aligned with industry standards.2. How is SSPM different from CASB?
A CASB focuses on securing the data flow between your users and the SaaS applications they access. SSPM, on the other hand, dives inside the apps themselves to secure their configurations, permissions, and posture. Together they complement each other, but they address different parts of SaaS security.3. What is the difference between SSPM and CSPM?
CSPM is designed to manage the security posture of cloud infrastructure like IaaS and PaaS environments. SSPM specifically manages SaaS application configurations and settings. If you are using SaaS apps heavily, SSPM is the tool you need alongside CSPM.4. Do all organizations need SSPM?
If your company uses multiple SaaS apps like Microsoft 365, Salesforce, or Slack, SSPM can make a real difference. It gives you visibility into app risks and ensures compliance across all those platforms. Essentially, the more SaaS apps you rely on, the more you benefit from SSPM.5. What are the top SSPM tools in 2025?
Some of the leading SSPM vendors in 2025 include Adaptive Shield, AppOmni, Wiz, Tech Prescient, and Netskope. These providers offer strong capabilities in monitoring, compliance, and automation to help businesses secure their SaaS environments.