Use Cases of Identity Governance and Administration (IGA)


Managing who can access what in your organization shouldn't require an army of IT staff and months of spreadsheet tracking. Yet that's exactly where most enterprises find themselves today. Every new hire, role change, or contractor engagement creates a cascade of access decisions across dozens of systems. Manual processes break under this weight.
Identity Governance and Administration (IGA) provides the automation and intelligence to manage access at scale. Whether you're onboarding 50 new employees or preparing for a compliance audit, IGA platforms transform Identity and Access Management(IAM) from reactive firefighting into proactive governance. This guide explores ten practical use cases from 2025 deployments that solve real operational problems your organization faces today.
Key Takeaways
- IGA transforms reactive identity management into proactive governance
- Ten proven use cases solve your most pressing operational challenges
- Strategic implementation beats big-bang deployment
- Different stakeholders solve different problems with IGA
What Are IGA Use Cases and Why Do They Matter?
IGA use cases are specific scenarios where identity governance solves tangible business challenges. Think of them as practical applications rather than theoretical concepts. Each use case addresses a pain point you're likely experiencing: slow onboarding, failed audits, security gaps, or operational bottlenecks.
Organizations with mature IGA programmes see 50-70% lower compliance costs and achieve 3–5x returns, driven by operational efficiency and reduced risk, according to Gartner and Forrester (2025).
But let's talk about what this actually means for your day-to-day operations.
For Compliance Teams: Auditors ask who accessed financial systems last quarter. Instead of spending weeks pulling logs from different systems and cross-referencing spreadsheets, you click a button and generate the report instantly.
For IT Directors: A new marketing manager joins on Monday morning. Without IGA, your team spends the day creating accounts, assigning permissions, and handling access tickets. With IGA, the HRIS entry triggers automatic provisioning, and the manager starts work immediately with all necessary access.
For Security Teams: An employee leaves on Friday afternoon. Without IGA, their accounts might sit dormant for weeks until someone remembers to disable them. With IGA, the HRIS termination triggers immediate deprovisioning across every system.
For HR Operations: Role changes don't require email chains coordinating with IT to update permissions. The HRIS update automatically adjusts access to match the new position.
In 2025, most of the IGA platforms add AI-powered intelligence that predicts access risks, suggests role optimizations, and detects anomalies before they escalate into security incidents.
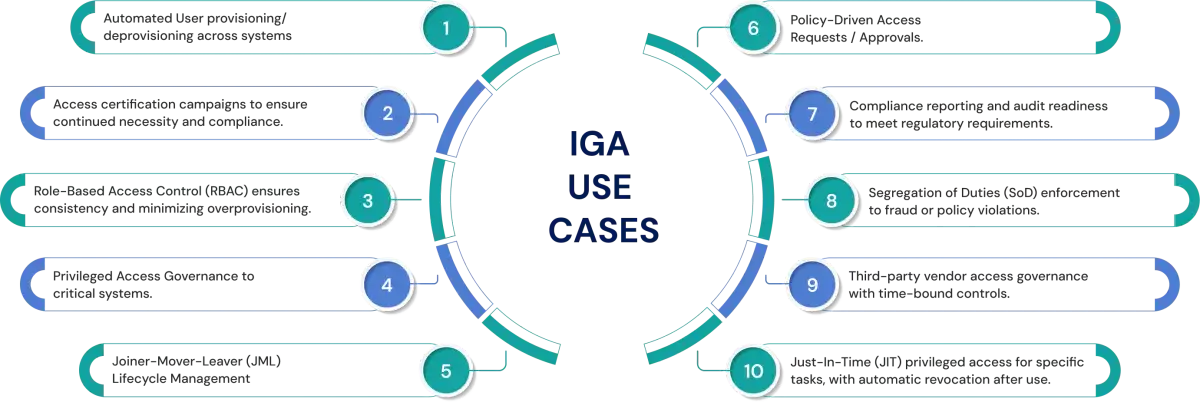
Top Use Cases of Identity Governance and Administration
Identity Governance and Administration is not a single feature. It’s a collection of tightly connected use cases that together control who gets access, when they get it, and why. Below are the most common and high-impact IGA use cases organizations rely on to improve security, reduce manual work, and stay audit-ready.
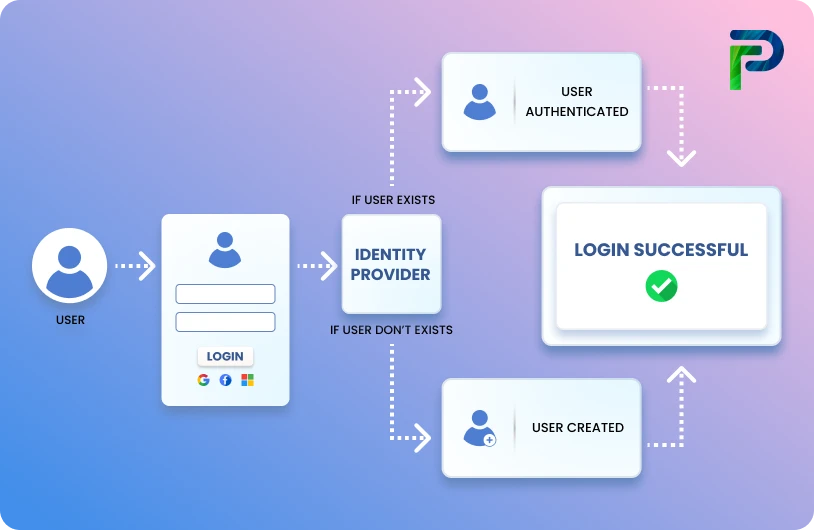
1. Automated User Provisioning and Deprovisioning
The Problem: New employees wait days for system access because IT manually processes each account creation. When employees leave, their accounts often remain active for weeks, creating security vulnerabilities.
How IGA Solves It: The IGA platform connects to your HRIS (like Workday or BambooHR). When HR adds a new employee, the system automatically creates accounts across all connected applications. When HR marks someone as terminated, access is removed from all systems, usually within seconds or a few minutes.
Benefit: Secure onboarding and offboarding without manual coordination.
Example: Your HR team adds a new sales representative to Workday on Friday. By Monday morning, they have email, CRM access, document storage permissions, and collaboration tool accounts ready to go. No IT tickets required.
When they leave six months later, the HRIS status change triggers instant deprovisioning. Their email forwards to their manager, files are transferred to the team, and all system access terminates within minutes.
What Identity Confluence Provides: Pre-built connectors to 50+ applications, including cloud and on-premises systems. HRIS integration with major platforms. Automated workflows for both provisioning and deprovisioning.
2. Access Certification Campaigns
The Problem: Compliance frameworks like SOX and HIPAA require quarterly access reviews. Managers receive spreadsheets with hundreds of user permissions they don't understand. Reviews take weeks. Evidence collection for auditors is a nightmare.
How IGA Solves It: Access certification campaigns automate the entire process. The system shows managers their team members with current access across all systems. Managers click to approve or revoke. The platform documents everything with timestamps and creates audit-ready reports.
Benefit: Audit readiness plus compliance without the spreadsheet chaos.
Example: Every quarter, your finance system requires access review. The IGA platform sends each manager a simple review showing their direct reports' financial system access. Managers see who has access, when they last used it, and whether it's appropriate for their role. They approve or deny with one click. The system automatically revokes denied access and generates the compliance report auditors need.
What Identity Confluence Provides: Automated certification campaigns with customizable schedules. Manager-friendly review interfaces that translate technical permissions into plain language. Complete audit trails with evidence packaging.
3. Role-Based Access Control (RBAC)
The Problem: Managing individual permissions across multiple applications is administrative chaos. Users accumulate permissions over time. New hires require extensive manual configuration. IT can't keep up.
How IGA Solves It: RBAC defines standard roles based on job function. "Sales Representative" gets a specific set of permissions across all systems. Assign someone the role, and they automatically receive all necessary access. Change roles, and permissions update automatically.
Benefit: Consistent access per department and role with minimal IT involvement.
Example: Your company has 50 sales representatives. Instead of manually configuring CRM access, document permissions, and tool access for each person, you create a "Sales Representative" role once. Assign new sales hires to this role, and they instantly receive all necessary permissions. If someone moves to sales management, you change their role, and the system adjusts their access automatically.
What Identity Confluence Provides: Visual role designer for creating and managing roles. Role mining that analyzes existing access patterns to suggest optimal role structures. Automated permission assignment based on role membership.
4. Privileged Access Governance
The Problem: Administrative accounts with elevated privileges are prime targets for attackers. Permanent admin rights create persistent security risks. But you need admin access for legitimate operational tasks.
How IGA Solves It: Privileged access governance enforces approval requirements and time limits on elevated access. Users request admin rights with business justification. If approved, they receive temporary credentials that automatically expire after the task completes.
Benefit: Control and monitor admin-level access without blocking legitimate work.
Example: A database administrator needs elevated access to troubleshoot a production issue. They submit a request explaining the problem. Their manager approves. The system grants 4-hour database admin access. All actions are logged. At the 4-hour mark, credentials automatically expire. The audit log shows exactly what they did during that window.
What Identity Confluence Provides:
- Structured request and approval flows for privileged access
- Temporary credential access with automatic expiry controls
- Privileged session tracking and recording, natively or through integrations
- End-to-end audit logs with compliance-ready evidence
5. Joiner-Mover-Leaver (JML) Lifecycle Management
The Problem: Employee lifecycle events trigger complex access changes. New hires need onboarding. Role changes require permission adjustments. Departures need immediate access revocation. Coordinating this across HR, IT, and managers is error-prone.
How IGA Solves It: JML automation synchronizes your HRIS with all connected systems. The identity lifecycle adjusts automatically as employees join, change roles, or leave. HR makes one change in their system, and access updates everywhere.
Benefit: Automatically adapts access as users change roles without manual coordination.
Example: An IT manager accepts a promotion to operations director. HR updates their title and department in the HRIS. The IGA platform detects this change and initiates an access review. It identifies which permissions to keep (email, core tools), which to add (operations dashboards, facilities systems), and which to remove (IT admin tools now managed by their replacement). The system routes approval to their new manager, then automatically implements the changes across all systems.
What Identity Confluence Provides: Real-time HRIS synchronization. Automated access recalculation for role changes. Intelligent access suggestions based on peer analysis. Complete lifecycle documentation.
Example: An IT Manager is promoted to Operations Director. HR updates their role in Workday. Identity Confluence automatically:
- Detects the role change in real time
- Compares access with peers in the same role
- Recommends what to add (operations dashboards, facilities systems)
- Recommends what to remove (legacy IT admin tools)
- Sends a fast-track approval to the new manager
- Applies approved changes across all systems within minutes
What Identity Confluence Delivers
- Real-time HRIS sync with platforms like Workday and BambooHR
- Automatic access recalculation for every joiner, mover, and leaver event
- AI-driven peer-based access recommendations
- Complete, tamper-proof JML records and audit trails
6. Policy-Driven Access Requests and Approvals
The Problem: Every access request becomes an IT ticket. Users don't know what to request. IT doesn't know what's appropriate. Managers lack context to approve intelligently. Everything moves slowly.
How IGA Solves It: Self-service access catalog shows users what they can request based on their role. Low-risk requests auto-approve based on policies. Higher-risk requests route to appropriate approvers with context. Users get access faster, and IT handles fewer tickets.
Benefit: Faster access with fewer IT tickets.
Example: A sales team member needs CRM access. They log into the self-service portal and see "Sales CRM" as an available request. The system knows this is appropriate for their role and auto-approves instantly. The CRM access provisions automatically. No IT ticket or manager approval needed. But when they request financial system access, the system recognizes this as unusual for their role and routes it to their manager for review.
What Identity Confluence Provides:
- User-role-specific self-service access catalogue
- For auto-approval rules (birthright, SoD, compliance), an intelligent policy engine
- Workflows for multi-level approval of sensitive or unusual requests
- Complete records and audit trails for each request and choice
7. Compliance Reporting and Audit Readiness
The Problem: Preparing for audits takes months. You pull logs from dozens of systems, correlate access data with approval records, and format everything for auditors. It's manual, time-consuming, and error-prone.
How IGA Solves It: Compliance reporting collects evidence continuously from all connected systems. Pre-built templates map to compliance frameworks like SOX, HIPAA, and GDPR. Click to generate audit reports showing who has access to what, when it was granted, who approved it, and when it was last reviewed.
Benefit: Generate real-time reports for SOX, GDPR, HIPAA, and other frameworks.
Example: Your external auditors arrive for the annual SOX audit. They ask for evidence of financial system access controls. Instead of scrambling to collect data, you log into the IGA platform and generate the SOX compliance report. It shows all users with financial system access, their roles, when access was granted, quarterly certification records with manager attestations, and automatic deprovisioning of terminated employees. The report takes 5 minutes to generate.
What Identity Confluence Provides:
- Pre-configured templates for SOX, HIPAA, GDPR, PCI-DSS, and ISO 27001
- Real-time compliance dashboards for ongoing monitoring
- One-click audit report generation
- Complete evidence packages with timestamps, approvals, and export-ready formats
8. Segregation of Duties (SoD) Enforcement
The Problem: Certain access combinations enable fraud. Someone who can both create vendors and approve payments could create fake vendors and authorize fraudulent payments. Manually detecting these toxic combinations across multiple systems is nearly impossible.
How IGA Solves It: SoD enforcement uses predefined rules to detect conflicting permissions. When someone's access would create a conflict, the system blocks it and requires a security review. Continuous monitoring identifies existing violations for remediation.
Benefit: Enforces policy-level access boundaries, reduces risk of internal fraud, and simplifies audits with automatic SoD violation reports.
Example: In your finance department, the system includes an SoD rule stating that users cannot have both "Vendor Creation" and "Payment Approval" permissions in the ERP system. When you try to assign the Accounts Payable role to someone who already has the Vendor Management role, the system blocks the assignment and alerts security. This prevents the toxic combination before it creates an audit finding or enables fraud.
What Identity Confluence Provides: Pre-built SoD rule library for common scenarios. Cross-system conflict detection. Preventive controls that block dangerous combinations. Exception management with business justification tracking.
9. Third-Party Vendor Access Governance
The Problem: Contractors, consultants, and vendors need temporary access to your systems. Their accounts often remain active long after contracts end. You lack visibility into what external users are accessing.
How IGA Solves It: Third-party access governance ties vendor access to contract dates. Access provisions when contracts start and automatically revoke when they end. You track exactly what external users access and for how long.
Benefit: Ensures time-bound, least-privilege access, prevents long-term orphan accounts, and tracks usage for accountability.
Example: A marketing agency contractor needs access to your analytics platform for a 30-day campaign project. You grant access when the contract starts, setting the expiration date to match the contract end. The contractor accesses only the analytics tool, nothing else. After 30 days, access automatically revokes. The system generates a report showing exactly what they accessed during those 30 days for your records.
What Identity Confluence Provides: Contract-based access expiration. Time-bound access grants with automatic revocation. Vendor activity monitoring and reporting. Integration with contract management systems.
10. Just-In-Time (JIT) Privileged Access
The Problem: Permanent admin rights create 24/7 security risks. But you need admin access for legitimate operational tasks like troubleshooting, maintenance, and emergency response.
How IGA Solves It: Just-in-time privileged access eliminates permanent admin accounts. Users request elevated access when needed. If approved, they receive temporary admin credentials that automatically expire after task completion. Every privileged session is monitored and recorded.
Benefit: Eliminates standing admin rights, reduces attack surface, and enables session monitoring and recording.
Example: A DevOps engineer needs root access to a production server to apply a critical security patch. They submit a request explaining the need. Their manager approves. The system grants 2-hour root access. The engineer applies the patch. All commands are logged. At the 2-hour mark, the credentials automatically expire. The security team has a complete record of what happened during that privileged session.
What Identity Confluence Provides: Approval workflows for JIT access requests. Temporary credential provisioning with automatic expiration. Session recording and command logging. Risk-based access decisions with policy enforcement.
Real-World Application: Use Case in Action
A regional healthcare provider with 3,500 employees faced mounting HIPAA compliance challenges. Manual provisioning delayed new clinical staff from accessing patient systems for 3 days. Access reviews consumed 6 weeks every quarter, with managers struggling with spreadsheets. Auditors consistently flagged incomplete documentation of who accessed protected health information.
They implemented IGA, focusing on three priorities: automated provisioning, access certification, and compliance reporting.
Phase 1: Automated Provisioning (Weeks 1-4)
Connected the IGA platform to their HRIS and clinical systems. Defined birthright access for each role (nurses, physicians, and administrative staff). Created automated workflows for onboarding and offboarding.
Result: New hire access provisioning dropped from 3 days to 2 hours. Terminated employee access is now revoked within minutes of the HRIS status change.
Phase 2: Access Certification (Weeks 5-8)
Launched quarterly certification campaigns for all systems containing protected health information. Managers review their team's access through a simple web interface showing who has access to what and when they last used it.
Result: Quarterly certification now completes in 9 days instead of 6 weeks. The system identified and remediated 284 instances of inappropriate access to patient data. All certification decisions are documented with timestamps for HIPAA audit requirements.
Phase 3: Compliance Reporting (Weeks 9-12)
Configured pre-built HIPAA report templates. Set up real-time compliance dashboards showing access patterns, certification status, and policy violations.
Result: Audit preparation time dropped from 6 weeks to 3 days. External auditors received complete evidence packages documenting access controls. Zero audit findings in the first post-implementation review.
Measurable Outcomes After 90 Days:
- New hire productivity gained: 2.5 days per employee
- IT ticket volume: Reduced 68%
- Audit preparation time: 96% reduction
- Compliance confidence: Zero HIPAA findings
How to Identify the Right IGA Use Cases for Your Organization
Don't try to implement all ten use cases at once. Start with your biggest pain point, prove value, then expand.
Audit Current Access Challenges
Ask your teams these questions:
- IT Operations: How many hours per week do you spend processing access requests? How long does new hire provisioning take? How many orphaned accounts exist from former employees?
- Compliance: How long does audit preparation take? How many audit findings relate to access controls? Can you prove who accessed sensitive data last quarter?
- Security: How many accounts have permanent admin rights? Can you identify all users with access to your most sensitive systems? How quickly can you revoke access in an emergency?
- Business Units: How often do users complain about access delays? How long after a promotion do permissions actually update?
The answers reveal where IGA delivers immediate value.
Prioritize High-Risk Areas
Match use cases to your organization's profile:
- Regulated Industries (Healthcare, Finance): Start with access certification, compliance reporting, and SoD enforcement. Audit requirements make these mandatory.
- Rapidly Growing Companies: Focus on automated provisioning, RBAC, and JML lifecycle management. Manual processes break as headcount increases.
- Security-Focused Organizations: Implement privileged access governance, JIT access, and vendor access governance to reduce attack surface.
- Complex IT Environments: Deploy RBAC, policy-driven access requests, and SoD enforcement to manage permission sprawl across many applications.
Align Use Cases to Roles (HR, IT, Compliance)
Different stakeholders care about different outcomes:
- CISOs: Want privileged access governance, SoD enforcement, and JIT access to reduce security risk.
- IT Directors: Need automated provisioning, RBAC, and JML lifecycle management to reduce operational burden.
- Compliance Managers: Require access certification, compliance reporting, and policy-driven approvals for audit readiness.
- HRIS Leads: Benefit from JML automation, automated provisioning, and vendor access governance for seamless employee lifecycle management.
Choose Tools That Support Automation and SoD
Evaluate IGA platforms on these capabilities:
Integration: Does it connect to your HRIS (Workday, SAP, BambooHR)? Can it manage both cloud and on-premises applications? Does it support your critical systems?
Automation: Can workflows run without manual intervention? Does deprovisioning happen automatically? Can certification campaigns schedule themselves?
SoD Support: Does it include pre-built SoD rules? Can it detect conflicts across multiple systems? Does it prevent toxic combinations proactively?
Scalability: Can it handle your current user count and application portfolio? Will it scale as you grow?
Usability: Is the self-service portal intuitive? Can managers certify access without technical training?
Not sure where to begin? Start with your most painful problem. Quick wins build momentum for broader implementation.
Implementing Use Cases with Identity Confluence
Identity Confluence addresses all ten use cases through a unified platform designed for rapid deployment and measurable results.
Core Capabilities:
Pre-built connectors for 100+ applications spanning cloud, on-premises, and hybrid environments. HRIS integration with Workday, SAP SuccessFactors, BambooHR, and ADP. Support for SCIM, SAML, and OAuth standards. Bidirectional synchronization maintains identity consistency across systems.
Automated provisioning and deprovisioning synchronized with your HRIS. Role-based access control with visual role designer and role mining. Access certification campaigns with automated workflows and audit-ready evidence. Policy-driven access requests with self-service catalogue and approval routing.
Compliance reporting with pre-configured templates for SOX, HIPAA, GDPR, PCI-DSS, and ISO 27001. Segregation of duties enforcement with pre-built conflict rules. Privileged access governance with time-limited credentials and session monitoring. Just-in-time access with approval workflows and automatic expiration.
Frequently Asked Questions (FAQs)
1. What is the difference between IGA and IAM?
IAM (Identity and Access Management) covers authentication (proving who you are) and authorization (what you can access). IGA is the governance layer ensuring access is appropriate, auditable, and compliant. IAM handles login mechanics; IGA ensures those logins should exist.2. How long does IGA implementation take?
Quick wins with a single use case take 6-8 weeks. Standard enterprise implementation with multiple use cases typically requires 4-6 months. Complex global deployments need 9-12 months. Phased approaches deliver value faster than attempting everything at once.3. Can IGA integrate with our existing systems?
Modern IGA platforms support standard protocols (SCIM, SAML, LDAP) and include pre-built connectors for common systems. Custom integrations handle proprietary applications. Most enterprises integrate their critical systems within the first 4-6 weeks.4. What are common IGA implementation challenges?
Three main challenges: integration complexity with hundreds of applications, change management as users and managers adopt new processes, and role design that balances granularity with manageability. Phased rollouts, executive sponsorship, and role mining tools address these challenges.5. How does IGA help with compliance?
IGA automates evidence collection that auditors require. Instead of manually gathering access data across systems, you generate compliance reports showing who has access, when it was granted, who approved it, and when it was last reviewed. Audit preparation drops from months to days.