What Is Authorization? Definition, Process, and Examples

Authorization is the process of granting an authenticated user the right to access and use a particular resource. Once authentication confirms who the user is, authorization determines what actions they are permitted to perform within the system. It specifies which data, applications, or processes a user can access, enforcing these permissions through predefined roles, rules, or attributes. This ensures that every identity operates within approved limits, maintaining data security and operational integrity.
Think of it like entering an office building. Everyone may pass through the main entrance after identity verification, but not everyone can enter every room. A manager might have access to all departments, while an employee may only access their own floor. In the same way, authorization controls access within a digital environment by deciding who can view, modify, or manage specific resources.
Even authorized users may pose security vulnerabilities in the absence of appropriate authorization rules. Insider attacks and breaches are frequently made possible by improperly set permissions or overprivileged access. In fact, 74% of data breaches involve a human element such as privilege misuse, stolen credentials or social engineering, according to Infosec Institute.
In this blog, we’ll explore how authorization works, the models behind it, and the best practices that help organizations enforce least privilege without slowing down productivity. Let’s dive in.
Key Takeaways:
-
Authorization defines what users can do after authentication, controlling access based on roles, rules, or attributes.
-
The authorization process verifies user privileges through defined policies before granting or denying access.
-
Key authorization models like RBAC, ABAC, DAC, and MAC determine how permissions are managed across systems.
-
Organizations face challenges like privilege creep, policy complexity, and lack of visibility in authorization management.
-
Modern IAM and IGA solutions integrate authorization to ensure least privilege, compliance, and secure access control.
What Is Authorization in Cybersecurity?
Authorization is the process that determines what an authenticated user is permitted to do within a system. Once authentication verifies who you are, authorization decides what actions you can perform. It specifies the level of access, actions, or privileges granted to a user, application, or device after successful identity verification. In the context of Identity and Access Management (IAM), both authentication and authorization enable system administrators to manage user access to digital resources and assign appropriate privileges. This digital authorization process closely mirrors real-world access control, where permissions are granted based on identity and role.
In cybersecurity, authorization works as a rule-based control layer that ensures users interact only with the data and resources they are allowed to access. It operates through well-defined policies, rules, and contextual attributes such as a user’s department, device type, location, or time of access to enforce permissions dynamically. This ensures that every action taken within a system adheres to security and compliance standards.
To put it simply, authentication answers the question “Who are you?”, while authorization answers “What can you do?” Think of it like air travel: your passport confirms your identity (authentication), while your boarding pass defines where you are allowed to go and the flight you are permitted to board (authorization).
At its core, every secure system uses authorization mechanisms that constantly check and validate permissions. These mechanisms rely on three main components:
-
Rules (Policies): Define who can do what, under which conditions. For instance, only “admins” can modify user data.
-
Contextual Details: Include information like device type, network, or location to make access decisions more precise.
-
Policy Decision Point (Checker): Evaluates the request based on the above rules and context, then grants or denies access.
In essence, authorization in cybersecurity acts as a continuous gatekeeper, ensuring that users, systems, or applications can only perform approved actions.
How the Authorization Process Works
Authorization determines whether an authenticated user can access specific data, applications, or actions within a system. It evaluates user privileges against predefined rules and contextual conditions to ensure only approved operations are performed.
At its foundation, authorization relies on three core elements: permissions, roles, and policies. Permissions define the exact actions a user or system can perform, such as read, write, or delete. Roles group permissions into logical sets that map to job responsibilities, which makes access management scalable. Policies contain the rules and logic that determine when and how roles and permissions apply, specifying the conditions under which access is allowed or denied. These elements work together so the authorization engine can make consistent, auditable access decisions.
Here’s how the authorization process unfolds step by step:
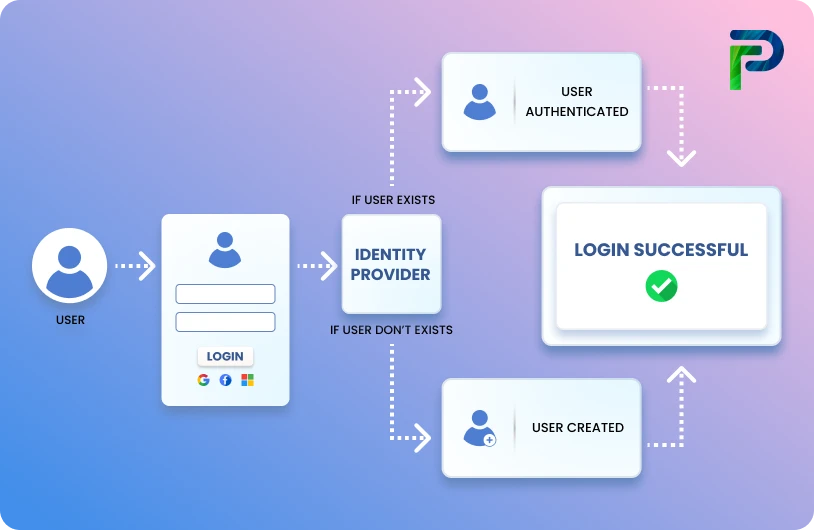
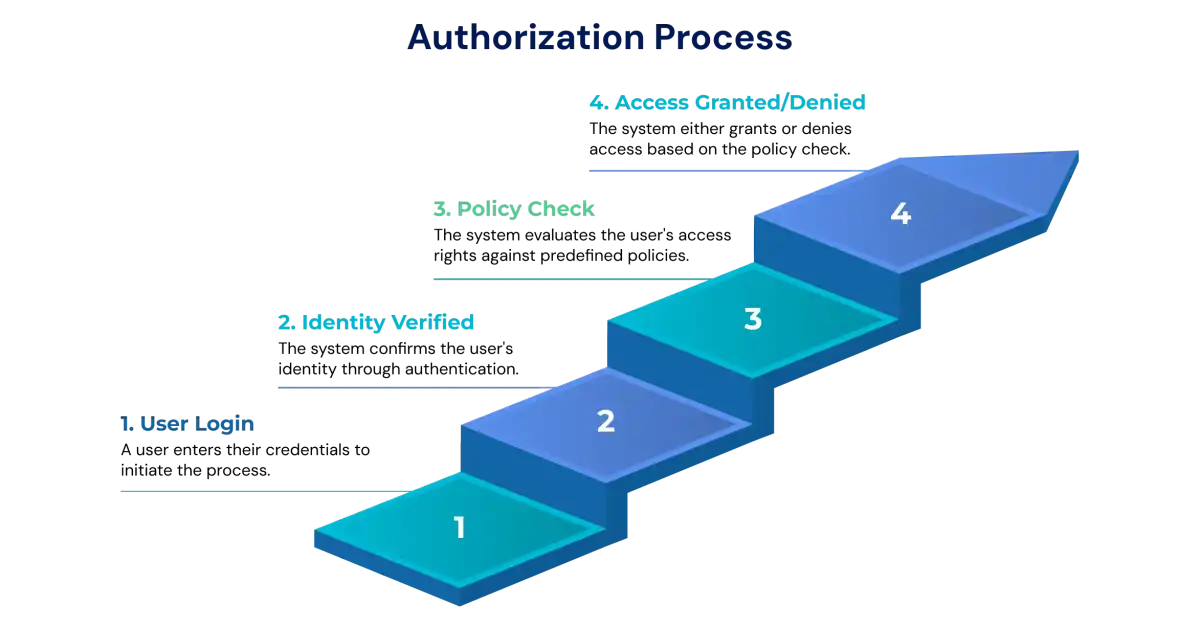
1. User authentication: The process begins when a user proves their identity by signing in with credentials, a one-time code, or multi-factor authentication. Successful authentication establishes a trusted identity and often produces a token or session identifier that represents that identity for subsequent requests.
2. Authorization request: The authenticated user attempts to access a resource or perform an action. The request contains the user identity or token, the target resource, and the desired action, for example, reading a file, calling an API, or modifying a record.
3. Policy retrieval and context collection: The access control engine gathers the relevant policy definitions and any contextual attributes needed to evaluate the request. Context can include the user’s roles and attributes, resource metadata (such as sensitivity or owner), and environmental details like device type, IP address, geolocation, and time of day.
4. Access control evaluation (decision stage): The Policy Decision Point evaluates the request by applying policy logic to the collected attributes, roles, and permissions. This may involve validating tokens (for example, checking JWT claims or OAuth scopes), consulting an attribute store or policy information point for additional facts, and executing policy rules from the policy administration point. The result is a clear allow or deny decision and, where applicable, any obligations or constraints, such as requiring approval or elevated verification.
5. Enforcement (policy enforcement point): The policy enforcement point enforces the decision returned by the decision stage. If the decision is allowed, the system permits the requested action within the defined scope. If the decision is to deny, the system blocks the action and returns a suitable error or status. Enforcement can occur in the application itself, at an API gateway, or via a dedicated authorization service.
6. Token handling and session management: When applicable, the authorization system issues, refreshes, or updates tokens to reflect the granted scopes and permissions. Session state is tracked so subsequent requests can reuse validated tokens without repeating the full evaluation, while still honoring time-limited or revocable permissions.
7. Activity logging and audit: Every access attempt and decision is recorded, including identity details, the requested resource, the decision outcome, timestamp, origin, and justification. These logs support auditing, compliance reporting, and forensic investigations.
8. Continuous review and policy feedback: Authorization is iterative. Periodic access reviews, automated analytics to detect privilege creep, and feedback from audits lead to role adjustments and policy updates. This continuous cycle keeps permissions aligned with business needs and reduces long-term risk.
In modern Identity and Access Management systems, these steps execute in near real time and are integrated with identity stores, token services, and identity governance tools. Centralized policy management, policy-as-code, and consistent enforcement across applications and cloud environments enable organizations to maintain least privilege, preserve auditability, and deliver secure, frictionless access.
Types of Authorization Models
Organizations rely on different authorization models to control who can access which resources. The choice of model depends on how structured the organization is, how dynamic the environment is, and the level of security required.
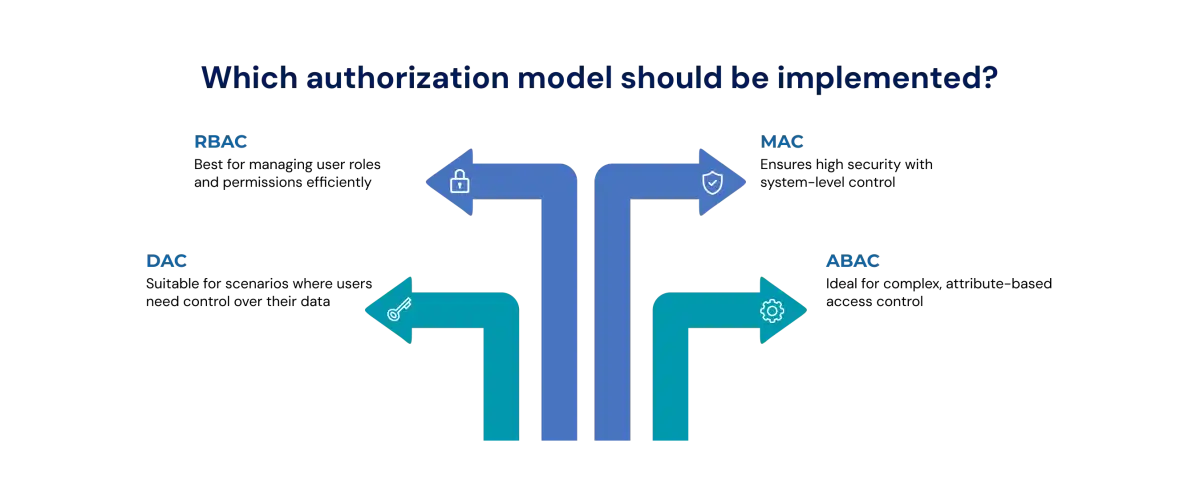
1. Role-Based Access Control (RBAC)
Role-Based Access Control assigns permissions based on the roles defined within an organization. Instead of granting access directly to each user, permissions are grouped into roles such as Admin, Manager, or Employee. A user receives access by being assigned one or more roles. This makes management easier because changes to job responsibilities only require role updates, not individual permission changes. RBAC works best in environments where job functions are clearly defined and do not change frequently.
2. Attribute-Based Access Control (ABAC)
Attribute-Based Access Control uses attributes to determine access permissions. These attributes may be related to the user (department, clearance level), the resource (file classification, owner), or the environment (time of day, device, location). Access decisions are made dynamically by evaluating policies that consider these attributes. This model provides very fine-grained control and aligns well with modern security approaches that require continuous evaluation of trust.
3. Discretionary Access Control (DAC)
Discretionary Access Control allows the owner or creator of a resource to decide who can access it and what actions are permitted. This model is common in personal computing and shared workspaces where individuals frequently create and share files. The flexibility of DAC makes it easy to collaborate, but it also means that organizations must rely on users to assign permissions responsibly. DAC is best suited to smaller environments or systems where individual ownership of data is clear.
4. Mandatory Access Control (MAC)
Mandatory Access Control is enforced by a central authority that assigns security classifications to data and clearance levels to users. Access is only granted when the user’s clearance level matches or exceeds the required classification of the resource. Individual users do not have the ability to override or modify permissions. MAC is typically used in highly secure environments where confidentiality is more important than flexibility, such as government, defense, and classified data systems.
Comparison Table of Advantages and Limitations
| Sr No. | Authorization Model | Advantages | Limitations |
|---|---|---|---|
| 1 | Role-Based Access Control (RBAC) | Easy to manage because permissions are grouped into roles. | Can become difficult to maintain when many roles or exceptions are required. |
| 2 | Attribute-Based Access Control (ABAC) | Provides flexible and fine-grained access control based on multiple attributes. | Policy creation, attribute management, and auditing can be complex. |
| 3 | Discretionary Access Control (DAC) | Resource owners have direct control and the system is simple to understand. | Risk of accidental overexposure of sensitive data if permissions are not carefully managed. |
| 4 | Mandatory Access Control (MAC) | Strong, centralized security ideal for sensitive information environments. | Rigid structure makes it less adaptable to changing roles or requirements. |
Real-World Examples of Authorization
Authorization controls who can access information and perform actions across the tools and systems we use every day. Whether at work, in healthcare, or in cloud applications, authorization ensures that users only access what they are permitted to.
1. Employees With Different System Privileges
In most organizations, employees access internal systems based on their job responsibilities. Role-Based Access Control (RBAC) is commonly used here. For example, an HR manager may be able to view and update all employee records, while a regular employee can only view their own information. By assigning permissions to roles instead of individuals, organizations maintain consistency and reduce administrative effort.
2. Healthcare Providers Accessing Patient Data
Healthcare systems must balance accessibility with strict privacy regulations. Attribute-Based Access Control (ABAC) helps achieve this by considering multiple conditions before allowing access. A doctor may access a patient’s data only if they are assigned to that patient, are using a secure hospital device, and are accessing the data during working hours. This ensures that sensitive medical information is protected while still being available when needed for treatment.
3. Cloud Storage and File Sharing (View Only vs. Edit Access)
Collaboration tools like Google Drive or Microsoft OneDrive often rely on Discretionary Access Control (DAC). The person who creates a file is the resource owner and chooses who can view, comment, or edit. For example, a document owner may grant one teammate edit rights and another teammate view-only access. This allows flexible and user-driven sharing, especially in collaborative work environments.
Common Authorization Challenges
Even with the right access control model, organizations often face difficulties in maintaining secure and efficient authorization. As systems scale and users change roles, managing permissions and policies can become increasingly complex.
1. Privilege Creep and Overprovisioning
Privilege creep occurs when users gradually accumulate more permissions than they actually need. This usually happens when employees switch departments or take on temporary responsibilities but continue to retain old access rights. Over time, this creates unnecessary risk because users may access sensitive systems or data they no longer require.
To address this, organizations should enforce the principle of least privilege, conduct regular access reviews, and remove outdated permissions promptly. Automated deprovisioning can also help ensure access is revoked when roles or employment status change.
2. Managing Policies Across Multiple Clouds
Modern organizations often operate across hybrid or multi-cloud environments. Each cloud platform may use different authorization models, identity frameworks, and policy formats. This makes it challenging to maintain consistent access rules across systems.
Centralizing authorization with a unified policy management layer helps ensure consistent enforcement. Platforms that support centralized policy enforcement and continuous authorization can evaluate access in real time, regardless of where resources reside.
3. Lack of Automation or Visibility
Manual provisioning and deprovisioning of access is slow, error-prone, and difficult to scale. Without automation, teams struggle to maintain an accurate record of who can access what. This lack of visibility increases the risk of misconfigurations and unauthorized access.
Integrating authorization workflows with HR systems and identity platforms enables Just-in-Time (JIT) access, automatic permission updates, and clear tracking of access changes.
4. Compliance and Audit Gaps
Many industries require proof of who accessed data, when they accessed it, and what actions they performed. Without centralized logs or audit trails, organizations may find it difficult to demonstrate compliance or detect suspicious activity.
Implementing centralized logging and tamper-resistant audit trails allows teams to trace every access event. This improves both regulatory compliance and incident response readiness.
Best Practices for Modern Authorization
Modern authorization is not just about granting access, but controlling it intelligently. As organizations scale, permissions must adapt without introducing complexity or risk. The best practices below help maintain security while ensuring users can work efficiently.
1. Principle of Least Privilege (PoLP)
The principle of least privilege ensures that users are granted only the access needed to perform their responsibilities. By restricting permissions to the minimum necessary, organizations limit the potential impact if an account is compromised. This helps contain security risks and supports operational efficiency.
2. Just-in-Time (JIT) Access
Instead of providing ongoing, broad access levels, Just-in-Time access delivers temporary permissions only when required. Once the task is complete, access is automatically revoked. This minimizes long-term exposure of sensitive systems and reduces the chance of privilege abuse.
3. Role Mining and Access Reviews
Over time, roles and responsibilities change, which can lead to unnecessary or outdated permissions. Regularly reviewing access, along with role mining to identify overlapping or unused privileges, allows organizations to stay aligned with the Principle of Least Privilege and prevent privilege creep.
4. Continuous Authorization and Auditing
Rather than relying on static, one-time approvals, continuous authorization evaluates access based on real-time context such as location, behavior, and activity. Combined with ongoing audits, this helps detect anomalies, enforce compliance requirements, and maintain visibility into who accessed what and when.
5. Centralized Policy Enforcement
Authorization policies should be defined and managed in one place, even if applications and environments are distributed. A centralized and decoupled policy enforcement approach ensures consistency, reduces configuration errors, and simplifies the management of access rules across cloud, on-premises, and hybrid infrastructures.
Authorization in Action: IAM and IGA Context
Authorization is at the heart of any modern identity and access management (IAM) architecture. While IAM frameworks define who can access which resources and what actions they are permitted to perform, authorization is the mechanism that enforces those rules in real time. When integrated properly, it ensures that every access request aligns with the user’s identity, role, and context. This operational layer enables organizations to control access at scale, across applications, services, and environments, and serves as a key pillar of a comprehensive IAM strategy.
Beyond simply granting or denying access, identity governance and administration (IGA) provides the oversight needed to ensure access policies stay aligned with business goals, compliance standards, and risk control. IGA manages the review, certification, and adjustment of user entitlements throughout the entire user lifecycle including onboarding, role changes, and offboarding. In this way, authorization becomes not just a technical enforcement step in IAM but also a governed and auditable process through IGA. Together, IAM addresses the mechanics of access, while IGA ensures the access remains appropriate, traceable, and compliant.
Final Thoughts
Authorization is the backbone of secure digital access, defining who gets to do what once identity is verified. It transforms authentication into meaningful trust by ensuring users only access what they are permitted to, maintaining data integrity, compliance, and security across every interaction.
As organizations scale across hybrid and multi-cloud environments, managing authorization efficiently becomes critical. By adopting modern models like RBAC and ABAC, enforcing the principle of least privilege, and integrating authorization within IAM and IGA frameworks, businesses can achieve both agility and control.
To see how Tech Prescient, helps enterprises build intelligent, policy-driven authorization systems that enhance security and user experience,
Frequently Asked Questions (FAQs)
1. What is authorization in simple terms?
Authorization is the process that decides what actions a verified user can perform within a system. Once authentication confirms who you are, authorization sets the boundaries of what you can access or do based on your role or permissions. It is essentially the gatekeeper for your digital privileges.2. How is authorization different from authentication?
Authentication is about proving your identity, like logging in with a username and password. Authorization comes next as it decides what you are allowed to do once you are inside. In short, authentication asks “Who are you?” and authorization asks “What can you do?”3. What are the main types of authorization?
There are four key access control models: RBAC (Role-Based Access Control), ABAC (Attribute-Based Access Control), DAC (Discretionary Access Control), and MAC (Mandatory Access Control). Each model defines permissions differently based on roles, attributes, ownership, or central policies.4. What is an example of authorization in real life?
Think of an HR system where a manager can view all employee records, but staff members can only see their own details. That is authorization in action where permissions based on job roles ensure everyone accesses only what they need.5. Why is authorization important in cybersecurity?
Authorization protects sensitive information by preventing unauthorized access and limiting privileges to what is necessary. It enforces the Principle of Least Privilege and helps organizations stay compliant with data security standards. In essence, it keeps systems both secure and accountable.