What Is Whaling Phishing? Definition, Examples & Prevention


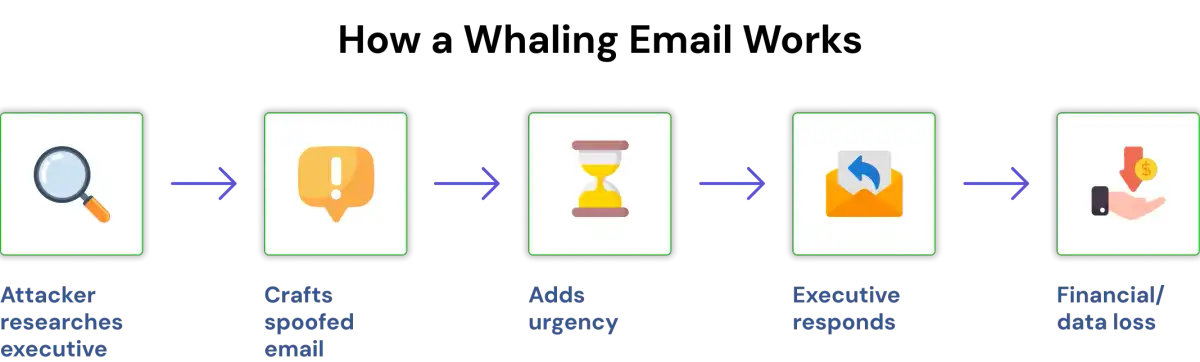
Whaling phishing is a targeted cyberattack in which bad actors assume the false identity of company senior executives, such as CEOs, CFOs, or COOs, to convince them to approve a payment or send private corporate information to the bad actors. Unlike regular phishing emails, whaling phishing emails are specifically crafted, thoroughly researched, and designed to appear completely legitimate. Bad actors will examine a company’s organizational chart to identify its executive officers, examine how executive officers communicate, and monitor the types of business activities a company is conducting to prepare messages that do not raise suspicions of the victim.
Ultimately, whaling phishing vulnerabilities often result in wire transfer fraud, data loss, or business email compromise (BEC). Whaling phishing is one of the most damaging forms of socially engineered cyber attacks in terms of finances.
In this post, we will define what whaling phishing is, provide a description of how whaling works, give real-life examples of whaling attacks, and describe the most effective methods for preventing whaling attacks through awareness-building, authentication processes, identity management, and other controls.
Key Takeaways:
- Whaling phishing targets high-level executives, or "big fish," who have authority over payments or sensitive data.
- Attacks rely on deep research and impersonation, making them harder to detect than normal phishing.
- Whaling attacks often result in BEC, wire fraud, or confidential data theft.
- Prevention requires executive training, MFA, strong email authentication, and identity governance controls.
What is Whaling Phishing?
Whaling refers to the practice of using spear-phishing attack to target high-level executives with personalized messages in an effort to influence them to authorize payments or provide sensitive information.
Also known as "whale phishing" or "executive phishing," whaling is a specific type of social engineering attack against executives, such as the CEO, CFO, COO, and finance head(s). They are referred to as "big fish" due to the level of access that they have to sensitive data, their authority to approve financial transactions, and the ability to have access to key strategic information.
Unlike "traditional" phishing, which typically involves scammers sending mass emails to thousands of employees, many whaling attacks are thorough and tailored to each executive. Many attackers will conduct in-depth research on the public activities that an executive participates in, how they typically communicate via email (to see if they have established patterns), to see any company news that is relevant to that executive and the executive's reporting relationships, and even to identify the writing style of the executive to create highly credible emails.
Most attacks will attempt to do at least one of the following:
- Convince an employee to authorize a wire transfer
- Take confidential financial or strategic information
- Gain unauthorized access to an executive's email account
- Start a BEC (Business Email Compromise)
Many whaling attacks also include a malicious link directing the executive to a spoofed login page or fake vendor portal that looks identical to a legitimate website. Once the credentials are entered or an attachment is downloaded, the attacker captures the information or deploys malware to gain deeper access.
As these messages appear credible and often convey urgency or authority, employees are more likely to trust them, making whaling phishing one of the most convincing and high-impact forms of social engineering.
What Are Whaling Attackers Trying to Achieve?
Whaling attacks are designed to exploit executive authority. Instead of targeting many users, attackers focus on a single high-impact individual and push them to take actions that directly benefit the attacker.
- Financial Fraud- Executives are misled into authorizing wire transfers, invoice payments, and account changes that send company money to accounts controlled by the attacker.
- Sensitive Data Theft- Attacker gains access to sensitive company data such as financial information, customer information, strategic plans, or executive credentials.
- Unauthorized Access to Systems- Executive shares login IDs, approves an account access request, and clicks on a malicious link that opens the door to internal systems.
- Abuse of Decision-Making Power- Leader is manipulated into approving a contract, policy revision, or operational change that creates vulnerability in their organisation's security controls and makes it easier for attackers to compromise their systems.
Because of their ability to build trust and give authority to others, one successful whaling attack can result in immediate significant financial losses for a company's bottom line, as well as ongoing long-term security exposure.
How Whaling Attacks Work
Whaling, also known as executive-level Business Email Compromise (BEC) or CEO fraud, is a highly targeted attack that exploits trust and authority rather than technical flaws. Attackers impersonate trusted individuals or organizations, such as senior executives, legal counsel, vendors, or auditors, and create a sense of urgency to push leaders into acting quickly.
The primary tools of a whaling attack are social engineering techniques, rather than technical exploits. Attackers will spend a significant amount of time researching their potential victim before crafting a believable email and then using both authority and urgency to coerce the executive into taking action quickly. The attack typically runs through the following steps.
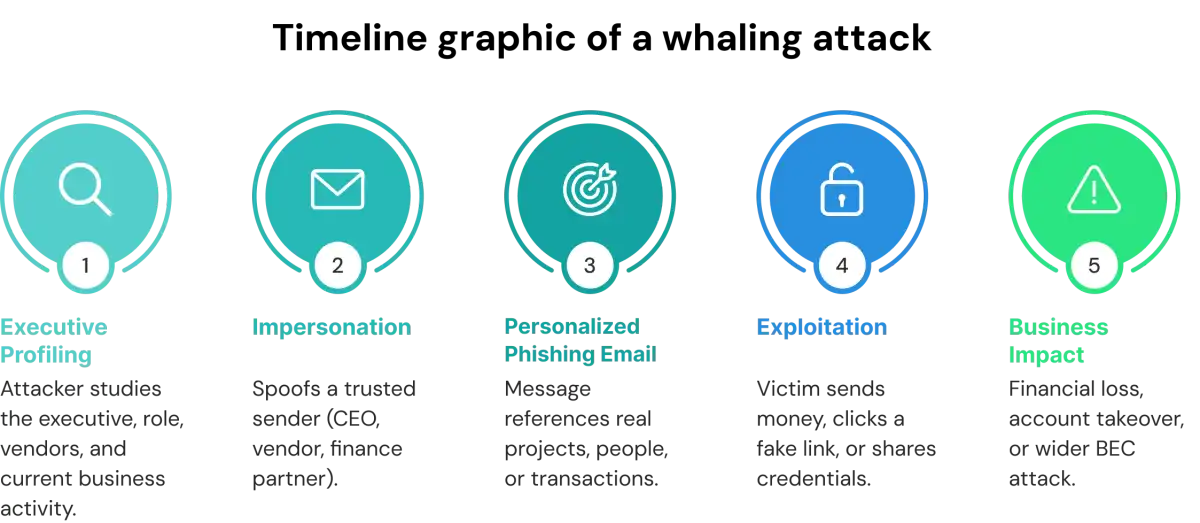
Step 1 – Research & Reconnaissance
The attackers will first gather as much information as possible about the executive and his organisation. This might include:
- The email patterns used by the organisation
- The reporting structure within the organisation (for instance, from CEO to CFO through to the Finance team)
- Publicly available information regarding the organisation (for example, LinkedIn updates, interviews, news stories, and so on)
- Timing of the organisation’s financial planning/finance process (for instance, quarter-end, fundraising rounds, etc.)
The information that is gathered at this stage is key because whaling phishing relies upon a high degree of personalisation; therefore, the attackers need to collect as much information as possible in order to gain credibility with the victim.
Step 2 – Impersonation & Email Spoofing
Once the attackers have gathered enough information about the potential target, they send out an email that impersonates someone that the victim would trust most, typically either the CEO, the CFO, a Legal Counsel, or a Vendor that is highly trusted.
Some of the different tactics include:
- Fake Domains such as company.co instead of company.com, company-finance.net, company-payments.org, or internationalized domains like çompany.com that visually resemble the real domain.
- Display name Spoofing – Although the name appears to be correct, the email has actually not been sent from the same email address.
- Reply-to address manipulation – This tactic is used to collect responses back to the attackers
- Compromised legitimate accounts – In some cases, attackers use a real, hijacked email account belonging to an executive, vendor, or law firm, eliminating the need for spoofing altogether.
These messages are intentionally brief, direct, and mobile-friendly. They often use imperative language (“Need this approved now”) and are increasingly generated or refined with AI to closely mimic the real executive’s tone, phrasing, writing habits, and even common shortcuts or typos.
Step 3 – Creating Urgency
The threats in a whaling email will almost always have time-based or other type of urgency associated with them.
Examples of messages include:
- “Get this wire transfer approved right away.”
- “I need this wire sent before our Board Meeting.”
- “This deal is confidential; do not include anyone else.”
Creating urgency decreases scrutiny, therefore increasing chances of success.
Step 4 – Execution
After the executive responds, the attacker will try to execute the fraud as soon as possible. The way the attack is carried out will depend on the objective of the attack.
Examples of how fraud is executed would be via:
- Wire Transfer Fraud (the most common type of attack)
- Stolen login credentials via a fake login page
- Vendor bank details quietly changed to divert funds
- Gaining access to and sending more BEC attempts via email accounts
The last stage of this attack defines the totality of the Whaling Attack, that is, the highly targeted exploitation for financial gain and/or unauthorised access.
Whaling Phishing Examples
Whaling phishing often takes the form of attackers impersonating trusted internal or external contacts to convince executives to take actions that benefit the attacker. These actions can include authorizing wire transfers, revealing credentials, or disclosing sensitive data. Real-world cases reported to law enforcement agencies like the FBI and the SEC show just how sophisticated and costly these attacks can be. According to the FBI’s 2024 Internet Crime Complaint Center (IC3)report, Business Email Compromise (BEC), the broader category that includes whaling, resulted in approximately $2.77 billion in reported losses in 2024 alone, making it one of the most financially damaging cybercrime types tracked by the agency.
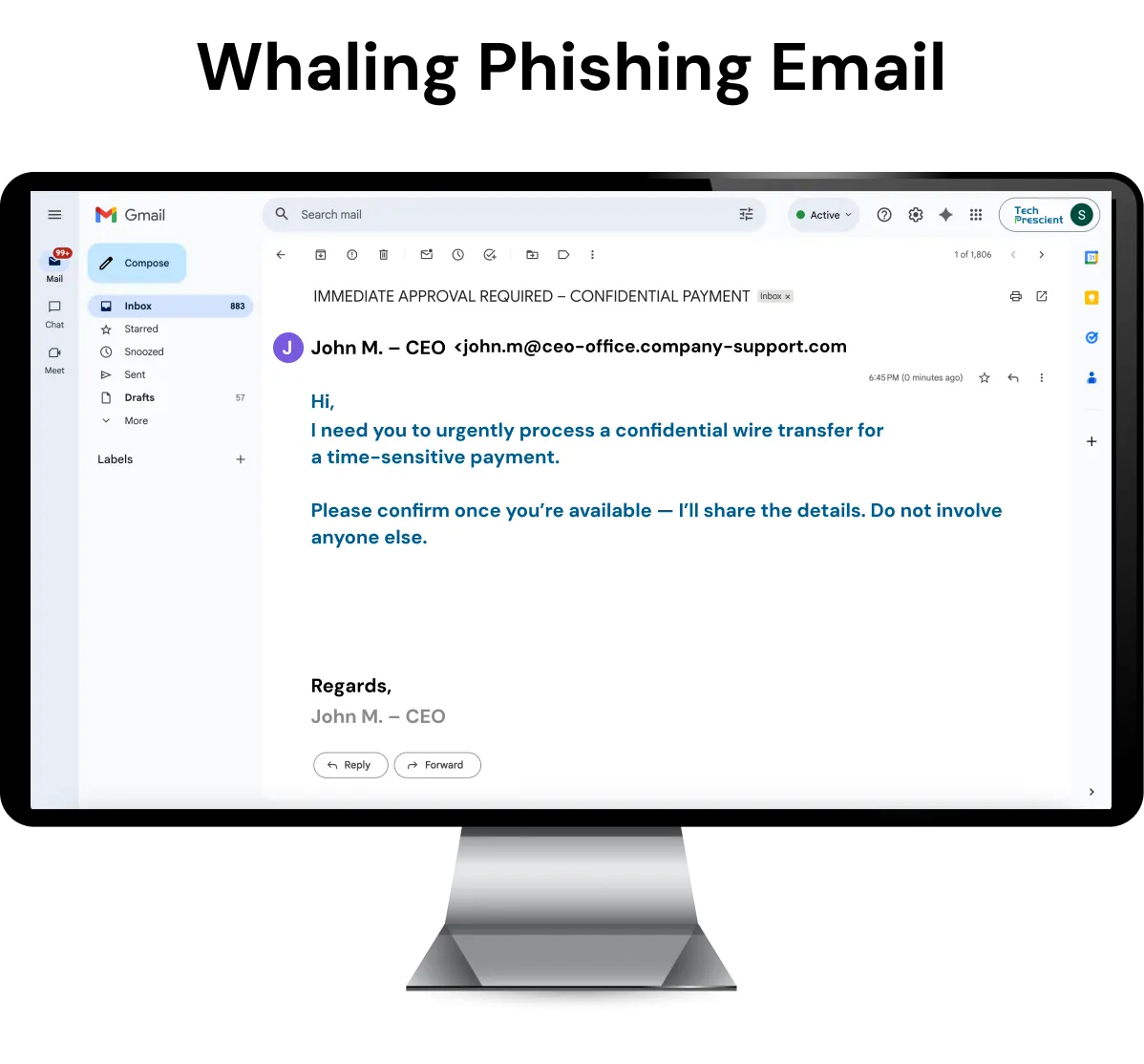
CEO impersonation Fraud (The Most Common scenario)
In the majority of whaling phishing fraud cases, the perpetrators pose as the CEO (of the company) and send an urgent email to the CFO or finance head. The message typically claims that an urgent, confidential payment must be approved immediately for a business acquisition, business transaction, or the settlement of a vendor's invoice.
Because the request appears to come from a senior figure in the company, the recipient may likely skip their typical procedures, indicating that this form of whaling phishing is one of the most common types of attack.
How it typically plays out:
- The perpetrators imitate the CEO's email address or use a virtually identical domain name.
- The email includes a request for urgent/confidential attention.
- The CFO is instructed to wire money and/or provide financial credentials.
Vendor / Client Impersonation
In this type of whaling attack, the bad actor pretends to be a trustworthy supplier or customer that the executive deals with on a regular basis. This is a more advanced version of business email compromise, as it involves sending a:
- Fake invoice
- Request to change bank information and
- Request for an immediate transfer of funds
As executives are often responsible for approving high-dollar invoices, these attacks can cause significant financial damage if not detected.
Credential Theft (with Rare Malware Elements)
Most modern whaling attacks focus on stealing executive credentials rather than deploying malware. Attackers prefer “clean” fraud techniques, often supported by AI-generated content or deepfake cues, because they are harder to detect and leave fewer technical traces. Common tactics include:
- Fake “board meeting agenda” or “confidential M&A update” emails that contain links or documents
- Fraudulent salary revision or executive bonus documents designed to prompt quick action
- Links to spoofed login portals that closely mimic trusted services such as Microsoft 365, Google Workspace, or DocuSign
Attachments are still used, but links to realistic login pages are far more common, as they directly capture credentials without triggering security controls.
Once the executive opens an attachment or enters their credentials into a spoofed portal, they will provide the attacker access to their email account, confidential documents or internal network, thereby magnifying the extent of damage.
Real-world example: In 2020, attackers used a fake Zoom meeting invite to steal executive credentials at an Australian firm, enabling follow-on fraud that resulted in $8.7 million in losses. A textbook example of credential-based whaling in action.
Whaling vs Phishing vs Spear Phishing
All three attacks utilize email to reach victims. However, they vary in size and scope, targeting, and potential damage. Recognizing these variances aids in clarifying many of the most frequently asked questions about phishing, and also gives insight into how whaling phishing fits into the scheme of all the different kinds of phishing attacks.
1. Phishing
Phishing refers to a general mass mailing sent out to thousands of recipients at the same time. Typically, the attacker will try to use simple methods to lure a user into clicking a malicious link or providing credentials. For example, they could use fictitious bank alerts, password reset emails, or package tracking updates as bait. Since phishing is not tailored toward any specific individual, its success rate per email campaign is low; however, the sheer volume of emails sent can offset this low success rate.
A real example of widespread phishing campaigns occurred in early 2025, when over a million phishing-as-a-service attacks were detected globally across organizations, showing how pervasive and automated phishing has become.
2. Spear Phishing
Spear phishing involves highly targeted emails directed towards a specific individual or group. To create the most realistic-looking messages, spear phishers often study the target's job function, company information, and events occurring in the target's life. Thus, the chances of success for spear phishing are much greater than with basic phishing techniques.
An example of this type of highly targeted threat was the $122 million invoice fraud scam, where attackers impersonated a known hardware supplier and sent fake invoices to Google and Facebook, convincing employees to make large payments over several years.
3. Whaling Phishing
Whaling is a form of spear phishing that specifically targets “big fish” at the top of the corporate ladder (executives). Because senior executives have access to restricted budgets and crucial infrastructure, their business impact can be more significant than standard spear phishing or regular phishing approaches. Whale Phishing usually impersonates senior-level executives, important clients, attorneys, authorities, or trusted partners to gain credibility and encourage an executive's approval for something (e.g., funding a project).
In early 2025, an analytics firm in Pune, India, lost ₹2.34 crore (≈ USD 280,000) after attackers posing as the company’s CEO manipulated accounts staff into transferring large sums to fraudulent accounts.
| Attack Type | Target | Typical Characteristics | Impact Level |
|---|---|---|---|
| Phishing | Anyone (mass audience) | Generic messages, no personalization, sent in bulk | Low per-email impact but high volume |
| Spear Phishing | Specific individual or team | Personalized using research, highly convincing | Higher success rate, moderate risk |
| Whaling Phishing | Executives & senior leaders | Executive impersonation, urgent requests, authority misuse | Very high financial & reputational risk |
Who Do Whaling Attacks Target
While whaling attacks target executives, anyone who has authority, the ability to approve payments, or access to sensitive systems may also be at risk. Typically, attackers are searching for people whose decisions or credentials could enable them to directly financially or compromise data.
1. C-Suite Executives (CEOs, CFOs, COOs)
C-Suite executives are trusted and have extensive authority; therefore, they receive emails from a variety of sources, and their emails typically are not questioned before being acted upon by the recipient. Therefore, their email accounts are a prime target for would-be impersonators. Attackers will send whaling emails that ask for wire transfers to be initiated, contracts to be approved, or confidential information to be provided.
2. Finance Leaders & Controllers
Finance directors, controllers, and managers of Accounts Payable/accounts receivable have also been the target of attacks by fraudsters, as these positions typically manage invoices and payments. As a result, fraudsters may send fake invoice approval e-mails, urgent payment update e-mails, and vendor change request e-mails.
3. HR Managers & People Operations
Human resources departments are responsible for managing employee data, payroll, and onboarding (and offboarding) staff; therefore, attackers may be targeting HR personnel to steal employee-sensitive information, salary information, or login credentials under the guise of an internal HR e-mail.
4. Anyone With Approval Power or System Access
In addition to C-Suite executives, numerous other individuals may be victims of whaling. Anyone who can approve purchases or make payments, or can access sensitive systems such as Finance, Procurement, or IT, is also a potential victim and can be considered a target of whaling attacks.
Why Whaling Attacks Are So Dangerous
Whaling attacks are considered some of the most damaging types of cybercrime because they involve all three of the following elements: executive authority, urgency, and privileged access, making them far more convincing and harder to stop.
1. High-Value Financial & Data Losses
Whaling is a type of cyber-attack focused on targeting a small number of individuals with high-value business roles within an organisation. Examples include Senior Executives, Directors, Managers, etc. The ability for whaling to take place means that one successful whaling attack can generate enough funds or confidential data to be passed illegally. The financial amount can represent millions of dollars, and the stolen IP can also include vast amounts of sensitive information about trade secrets, marketing, employees and customers.
2. Harder to Detect & Validate
Whaling emails are targeted, researched and have context. They include references to existing projects, references to senior executives or recent events within your organisation. This level of employment leads employees to be much more wary of questioning or raising flags. The degree of harm poses serious threats to whaling data privacy and security.
3. Often Bypass Technical Filters
Attackers often use ways to bypass email security filters through the use of techniques such as lookalike domains, display-name spoofing, or hijacked inboxes to make emails look legitimate; since there is often no malicious link(s) or attachment(s) in these emails, they often go through email security filters easily, making them more likely to succeed in whaling attacks.
4. Exploit Trust at the Highest Levels
Executives operate under tight deadlines and a sense of urgency, making it more likely that they will approve requests quickly. By exploiting this type of trust relationship and time pressure in a fast-paced working environment, attackers can get around important verification steps.
How to Prevent Whaling Phishing Attacks
An effective strategy for combating whaling must incorporate multiple levels of protection: training for executives, enhanced verification processes for transactions and payments, measures to reduce phishing opportunities through secure communications (such as email authentication protocols like SPF, DKIM, and DMARC), and strong identity governance controls.
1. Strengthen Executive Awareness Training
Because executives are often targeted by criminal organizations, it is important to create a comprehensive executive cyber awareness program focused on educating them about how they can identify warning signs that indicate a whaling attack. Though the training may be limited to annual sessions, it is also critical for executives to receive periodic updates (quarterly, at a minimum) regarding the critical components of their cybersecurity infrastructure that could lead to susceptibility to whaling.
Training should explicitly cover modern tactics such as AI-generated emails, voice deepfakes, and impersonation scenarios, and reinforce a clear “trust but verify” mindset, encouraging executives to pause and confirm sensitive requests through a known phone number or secondary communication channel before acting.
2. Implementing Multi-Factor Authentication (MFA) and Strong Authentication
Phishing-resistant MFA, such as FIDO2 hardware security keys or passkeys, significantly reduces the risk of account takeover, even if an executive’s credentials are exposed. When combined with conditional access policies, organizations can further limit risk by blocking or challenging login attempts from unusual locations, unfamiliar devices, or abnormal behaviour patterns.
This layered approach makes credential-based whaling attacks far less effective by removing reliance on passwords and adding contextual checks before access is granted.
3. Validate All Financial Requests
All financial requests should go through a verification process prior to approval. This is especially important for requests related to wire transfers, updates to vendor records, or changes to invoices. Should these requests be verified before they are processed, it may prevent an executive from incurring a significant financial loss.
4. Email Security/Anti-Spoofing Controls
Beyond basic email authentication standards such as SPF, DKIM, and DMARC, organizations should implement advanced email security controls that can detect anomalies in sender behaviour, writing style, and request patterns. AI-powered email gateways (for example, tools that specialize in behavioural analysis) are particularly effective at identifying whaling attempts that bypass traditional filters.
To strengthen protection further, organizations should enforce a strict DMARC policy (set to reject) to block spoofed emails outright. Together, these controls significantly reduce the likelihood of phishing and whaling emails reaching executive inboxes.
5. Establish Identity Governance Controls
Because of the privileged nature of their access, executives are often targeted by cyber criminals. Enforce these controls through identity governance (IGA):
- Conducting regular access reviews for all executive accounts
- Restricting access based on the principle of least privilege, limiting unnecessary authorized access
- Continuously monitoring all activities associated with the executive accounts to identify and investigate any risk indicators or aberrational access behaviour
- Automating offboarding and access revocation to ensure executive accounts are promptly disabled when roles change or employment ends
- Integrating IGA signals with SIEM tools to generate real-time alerts for risky actions, such as unusual login patterns or bulk data downloads
These IGA controls (established through internal/ IGA-driven audits) will assist in mitigating the adverse impact of misuse and/or the compromise of an executive account.
6. Leverage AI-Based Detection and Rapid Incident Response
Whaling attacks increasingly use AI-generated content, including deepfake voice or video impersonations of executives. Executives should be trained to recognize these tactics and verify sensitive requests, especially those involving payments or access changes. For example, a company in Pune, India reported a $266k loss that happened due to a spoofed CEO call, early this year.
Use User and Entity Behaviour Analytics (UEBA) to monitor executive accounts for unusual activity, such as abnormal login patterns or unexpected transactions.
If an incident is suspected, report it to the FBI’s Internet Crime Complaint Center (IC3) as quickly as possible, ideally within 72 hours, to improve the chances of recovery.

What to Do If You Suspect a Whaling Attack
It is important to quickly respond to all threats. The sooner that your organization can react to a threat, the easier it will be to mitigate losses, minimize financial impact, and pursue legal action against the threat. If you receive an email that you think may be a whaling phishing email, no matter how minor your suspicion, take immediate steps to contain the incident.
1. Report the Email to SOC/IT Immediately
Do not click on any links or respond to the suspicious email. Immediately forward the email to the SOC or your IT department. Notifying your security team as soon as possible gives them time to establish the proper procedures to block the sender, tighten security by updating their filters, and educate and inform others in your organization.
2. Halt All Financial Transfers
If the email involves a wire transfer or other payment instructions, stop the transaction immediately and, if possible, reverse the transaction. Many banks have systems in place that allow them to prevent or reverse a wire transfer if notified by their customers.
3. Reset Accounts and Investigate Logs
If you believe that the suspicious email may have provided the sender with your username and password, modify all account passwords to protect your accounts.
For example, it may be necessary for the SOC to perform the following:
- Review login log files.
- Determine whether there were any unauthorized login attempts.
- Investigate any suspicious login activity related to an executive account.
4. Preserve Evidence for Forensics
Preserve all evidence associated with the phishing email, including the email itself, along with the headers and any attachments, along with all other communications associated with the phishing email. All evidence must remain unchanged and untouched for investigators and law enforcement to trace the origin of the sender.
Final Thoughts
Whaling Phishing is rapidly growing as a highly targeted, high-profile type of cybercrime, which is also quite costly. It targets executives (who typically have the highest authority within organizations). Because of the nature in which the phisher uses an urgent message with a spoofed sender name with a similar context to that person's position to create a believable message, many times one successful whaling attack can result in a significant loss of money and/or other negative ramifications.
To properly protect your organization from whaling attacks, it takes more than just basic filtering of e-mail; it takes a combination of multiple levels of defence:
- Training of Executives to identify high-risk e-mails
- Identity Governance/strong Authentication (for the highest authority)
- Verification process for Financial Transactions
- Advanced E-mail Security Systems to find out about impersonating e-mails before they reach someone in their inbox.
When there are controls in place, detecting whaling attacks becomes easier for an organization, and executing whaling attacks becomes much more difficult for the phisher.
Frequently Asked Questions (FAQs)
1. What is whaling phishing?
Whaling phishing is a targeted cyber attack against executives and decision makers (C-level executives). In a whaling phishing attack, the attacker uses an extremely personalized email utilizing the guise of the CEO, CFO, or someone from a reputable partner organization to trick the victim into sharing sensitive information, authorizing fraudulent payments, and/or allowing access to internal company systems.2. Is whaling a type of phishing?
Yes, whaling phishing is classified as phishing. Whaling is a specialized subset of spear phishing. Phishing is generally "casting a wide net," as in broad-based campaigns. Whereas whaling focuses on high-ranking executives who have the ability to authorize, gain access, and make key decisions.3. What is an example of a whaling attack?
One of the more common examples of whaling phishing is when an attacker impersonates a CEO, sending an urgent message to the finance department requesting a confidential wire transfer. In the message, urgency and authority are used in an attempt to pressure the target to carry out the transfer without appropriately confirming that it's a legitimate request.4. What is the difference between spear phishing and whaling?
Spear phishing can be thought of as coming from someone within the victim organization; whereas whaling is targeted specifically at high-level executives (i.e., “big fish”) who may have authority over budgets, approvals, or confidential information. Due to the high dollar value of the information or funds being offered, this makes whaling significantly more damaging and much less likely to be detected.5. How can companies prevent whaling attacks?
Businesses that want to reduce risk associated with whaling should implement effective executive-focused security awareness training, multi-factor authentication on all executive accounts to mitigate the possibility of compromise through username/password harvesting, deploy effective email authentication methods (such as SPF, DKIM & DMARC) to help prevent spoofing attacks, and enforce robust identity governance policies that place significant limitations on executive access rights. Additionally, all financial requests should include verification workflows to help prevent the processing of fraudulent payment requests.