
Just-in-Time (JIT) Provisioning Explained: How It Works & Why It Matters

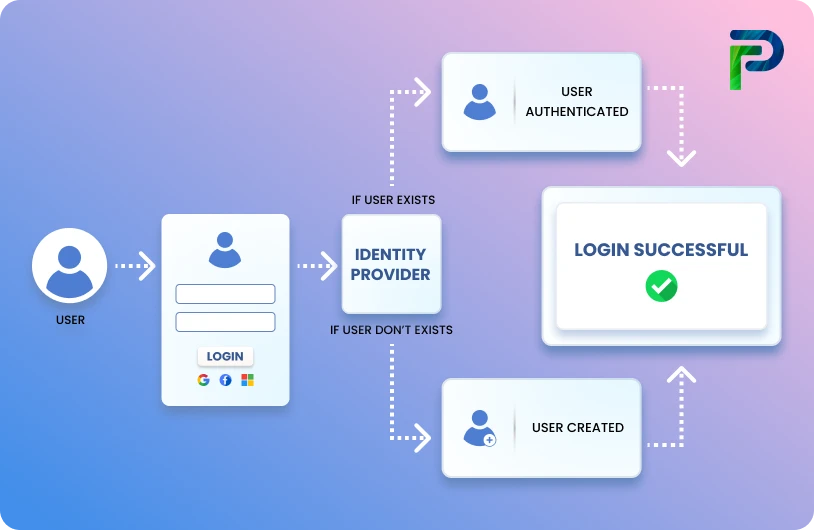
Just-in-Time (JIT) provisioning is a simple and efficient way to create user accounts automatically the moment a user logs in through SSO. Instead of setting up accounts ahead of time for every new hire or contractor, the application creates the user on their very first login using a small set of trusted attributes sent by the Identity Provider (such as Azure AD, Okta, or Google Workspace). This removes the need for IT teams to perform manual account creation and allows the application to generate the user profile immediately.
JIT provisioning works with any standard SSO protocol, such as SAML, OIDC, or OAuth, because the process depends on the identity attributes sent during authentication, not the protocol itself. The only requirement is that the target application must support automatic user creation through JIT; not all SSO-enabled applications do.
In this blog, we’ll discuss how Just-in-Time provisioning functions, its value proposition, how it compares and contrasts with SCIM-based provisioning, and the benefits of JIT provisioning as an integral part of modern IAM/IGA solutions.
Key Takeaways
- Users are dynamically given access to new accounts the first time they log in. No manual account creation is required.
- Through single sign-on (SSO) and automated processes, onboarding and administration have been simplified.
- Compatibility exists for Security Assertion Markup Language (SAML) and OpenID Connect (OIDC), as well as with all current identity provider companies.
- Zero Trust, least privilege, and identity governance are supported and facilitated by eliminating any idle access for users who are not being actively used.
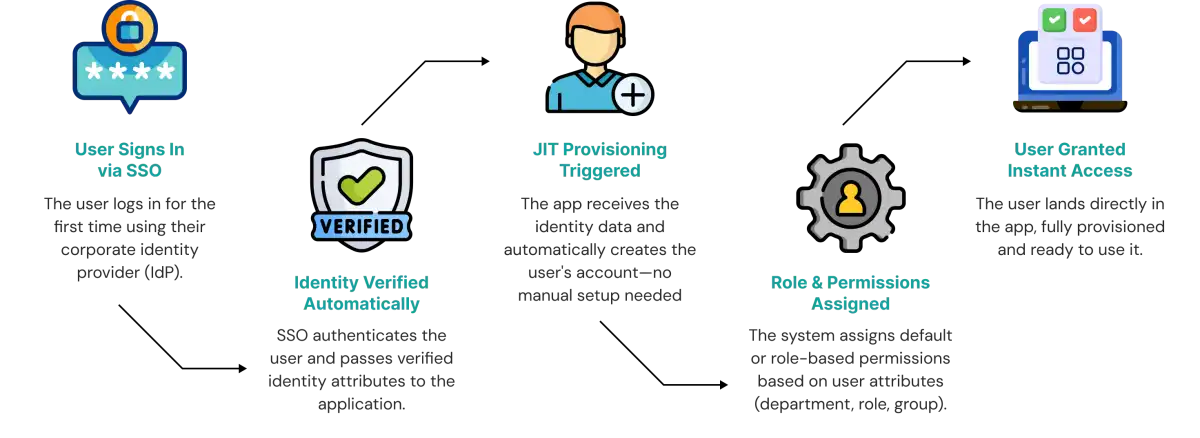
How Does Just-in-Time Provisioning Work?
Just-in-Time (JIT) provisioning creates a user account when a user logs in for the first time via Single Sign-On (SSO). Instead of creating accounts across all applications before first-time logins, identity providers (IdP) send a small, agreed-upon set of trusted user attributes, typically email, name, display name, groups, roles, department, or employee ID, via a SAML assertion or an OIDC ID/access token.
When a new user attempts to log in to the application for the very first time, the application uses these attributes to automatically create their account on the spot. There is no need for an admin to manually provision anything, JIT takes the information passed through SSO and instantly builds the user profile and assigns the right access.
This makes onboarding immediate, removes repetitive admin steps, and ensures users only receive access when they actually need it.
Note: JIT provisioning and SCIM serve different purposes. JIT only creates the account during the first login, triggered by an SSO event. SCIM, on the other hand, handles ongoing lifecycle management; it can create, update, or remove user accounts in applications without requiring the user to log in first.
Step-by-Step Workflow
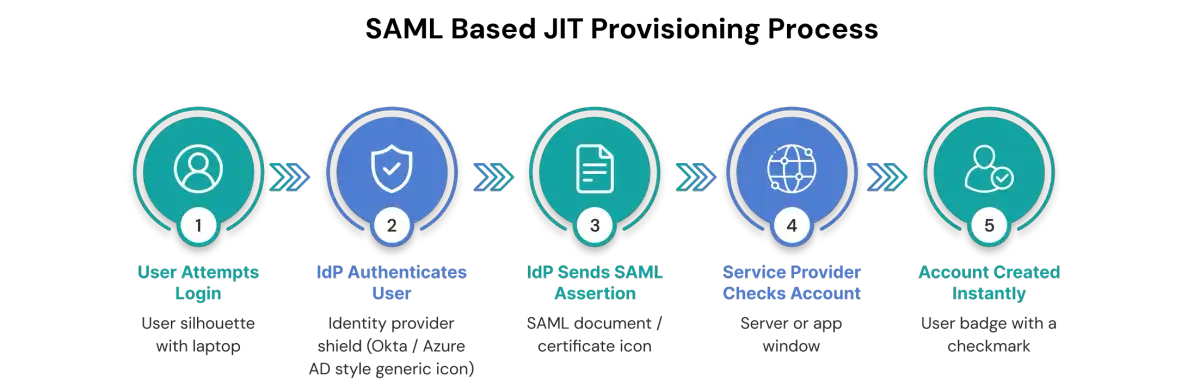
1. SSO connection is configured
The IdP (Azure AD / Entra ID, Okta, Google Workspace, etc.) and the application (SP) are connected using SAML or OIDC.
2. User attempts to log in via SSO
The user selects the option to “Sign in with SSO” and begins to authenticate through the IdP.
3. IdP authenticates the user
The IdP authenticates the user's identity based on the submitted credentials and requires an MFA or Conditional Access Policy to be satisfied as well.
4. IdP sends user attributes
The Identity Provider sends a SAML assertion (in SAML) or an ID/access token (in OIDC) that includes the agreed list of user attributes, usually email, name, display name, and any groups or roles the application expects.
5. Application checks for an existing account
If the application supports JIT provisioning and the attributes in the incoming token align with its required format, it detects that the user doesn't exist and automatically creates the account during that first login.
6. Roles and permissions are assigned automatically
The application then applies the correct access based on its predefined mappings. IdP groups, roles, or other attributes are matched to the application’s internal roles, so the right permissions are assigned immediately without any manual approvals.
Example Use Case
Consider a new employee joining your team. Instead of creating her accounts manually across email, HR, and project management tools, you simply add her to your IdP (e.g., Okta, Azure AD, Google Workspace) and configure SSO for the applications she’ll use. When she clicks Sign in with SSO and logs in for the very first time, the application receives her user attributes through the SAML assertion or OIDC token from the IdP.
If the application is enabled for Just-in-Time provisioning, it automatically creates her account on the spot using those attributes, no pre-creation, tickets, or manual setup required.
Benefits of Just-in-Time Provisioning
Just-in-Time (JIT) Provisioning enables faster onboarding and tighter access controls, while reducing the manual identity work that IT needs to do. This streamlines the account creation process, ensuring users only get access to what they need and reducing overall operational effort.
1. Efficiency & Scalability
JIT allows for efficient and scalable use of hundreds of applications because it removes the time-consuming and manual steps associated with the new user account creation process. It instantly creates a user’s account when they first log into an application. As a result, teams can scale rapidly across many different applications without having to create and manage separate user accounts for every application.
2. Security and Compliance
The Identity Provider (IdP) is the repository that defines the attributes and policies that determine what types of access users receive. Because accounts are provisioned (created) on demand, organizations do not end up with unused or inactive accounts, which enhances Zero Trust by limiting access and requiring continual validation.
3. Cost & Operational Impact
JIT provisioning lets IT teams offload a tedious, never-ending task and reclaim time for higher-value work. By automating user creation through the IdP, admins reduce manual effort, avoid repetitive updates, and cut down on mistakes, like accidentally granting a higher level of access than a user needs. The more of these workflows you automate, the lower your operational overhead and the fewer costly errors you introduce over time.
What’s the Difference Between JIT Provisioning and SSO?
Single Sign-On (SSO) is a process that allows a user to authenticate with a service provider without having to enter multiple passwords or logins for each of the services they access. This allows users to sign in once and then access all of the services they need without needing to remember separate passwords for each service, reducing password fatigue.
On the other hand, Just-in-Time (JIT) provisioning allows a service provider to automatically create a user account the instant the user logs in for the first time.
By providing users the ability to authenticate through SSO and having their accounts automatically created via JIT provisioning, service providers significantly enhance their users' login and onboarding experience. While SSO streamlines the login experience and reduces password fatigue, JIT eliminates the need for IT to create user accounts manually and streamlines the onboarding process.
The main difference between SSO and JIT provisioning is when the two processes take place. SSO will be invoked on every login to verify that the user is who they say they are. JIT provisioning is only invoked when a user tries to sign in, and the application determines that they do not yet have an account and subsequently creates one using the user's identifying attributes sent to the service by the Identity Provider (IdP).
JIT vs SCIM Provisioning: What’s the Difference?
The JIT and SCIM methods for automating identity management have two different automations: SCIM provides continuous synchronization of user data across multiple systems, whereas JIT creates an account upon the user's first successful login. Together, the two solutions provide several levels and types of automation dependent on user access frequency and your desired level of provisioning control.
| Sr. No | Feature | JIT Provisioning | SCIM Provisioning |
|---|---|---|---|
| 1 | Timing | Creates an account at login | Pre-creates or continuously syncs users |
| 2 | Direction | Reactive (on-demand) | Proactive (regular syncs) |
| 3 | Best for | Dynamic, occasional, or flexible access | Large directories, continuous updates |
| 4 | Account Removal | Manual cleanup or access removed at next login | Automated deprovisioning via sync |
| 5 | Setup Complexity | Minimal setup; depends mainly on IdP attributes | Higher setup effort; requires SCIM connectors and mapping |
| 6 | Ideal Use Cases | Lightweight SaaS, infrequent access apps, external users | Core apps, large workforce apps, and apps needing continuous accuracy |
Implementation Guide: Setting Up JIT Provisioning
To allow JIT provisioning, you connect your IdP (for example, Okta or Azure AD) to your target application via SAML or OIDC. During login, the IdP sends the user’s identity attributes to the application so it can create the account automatically without requiring any extra input from the user.
Note: JIT provisioning must be explicitly supported and enabled in the target application; simply supporting SAML or OIDC does not guarantee JIT is available.
1. Prerequisites
To configure JIT provisioning, you need to ensure that the following prerequisites are met:
- Both the IdP and target application must support either SAML 2.0 or OIDC because JIT provisioning uses these protocols to exchange identity information.
- You must have administrative access to both the IdP and the target application, as configuration requires you to perform SSO configuration, enable JIT provisioning, and map attributes between them.
2. Configuration Steps
Once the prerequisites have been met, follow these steps to configure JIT provisioning:
- Identify which attributes the target application needs (typically email, full name, and optionally groups, roles, department, and employee ID). Configure the IdP to include these in the SAML assertion or OIDC ID token..
- In the target application’s admin/SSO settings, enable the option labelled “Just-in-Time Provisioning”, “Automatic User Creation”, or similar (label varies by vendor).
- Create mappings so IdP groups or custom attributes translate to the appropriate application roles/permissions. These mappings determine the user’s access level on first login.
- If the app expects attributes in a particular format (e.g., group IDs vs group names, or a specific role string), add attribute transforms or mapping rules in the IdP or SP so values match the app schema.
- Configure any policy checks (e.g., only allow JIT creation for users from a specific domain or for certain groups) to prevent unwanted account creation.
- Create a test account in the IdP that does not already exist in the application. Log in via SSO and confirm the application automatically: creates the account, sets the expected attributes (name/email), and assigns the correct role/group mapping, without any manual profile creation.
3. Testing and Validation
Once the configuration has been completed, the setup should be tested for proper operation:
- Review the audit log on both the IdP and the application to detect if the provisioning event was triggered appropriately.
- Respect the attribute mapping, confirming that the application received the proper identity information from the IdP.
- Ensure that the access level assigned to the user was correctly validated and that their role or group membership matched the expected permissions for that level.
Note:
Pure JIT provisioning only handles account creation at first login. It does not update user attributes afterwards and does not disable or delete accounts when users leave. For ongoing attribute sync, role updates, and automated offboarding, you should pair JIT with a full SCIM provisioning integration.
Best Practices for Just-in-Time User Provisioning
Securing JIT provisioning, making it scalable, and conforming to legality requires focus on identity quality data, robust access controls, and continuous monitoring.
1. Enforce Attribute Accuracy
JIT uses exclusively the account information provided by the IdP. It is important to ensure that the accuracy of fields such as email, department, job role, and manager is maintained and updated regularly. This ensures that all individuals accessing systems will be granted access based on correct information.
2. Combine JIT with Role-Based Access Control (RBAC)
Using RBAC ensures users get the right access the moment their account is created. Map IdP groups or roles to application-level permissions so access is automatically aligned with job responsibilities. This avoids over-provisioning, keeps permissions consistent across teams, and simplifies future access changes when users switch roles.
3. Integrate with IGA for Governance
While JIT handles the dynamic provisioning aspect of identity and access management, IGA adds the governance component that validates compliance through audits. By integrating JIT with IGA, you will be able to track and monitor all accounts provisioned via JIT; track what entitlements are associated with JIT provisioned accounts; trigger access reviews based on changes to entitlements; and ensure that all JIT provisioning events abide by your organisation's security policy. This is especially important for organisations subject to high regulatory audit requirements.
4. Audit & Logging
JIT-created accounts and access grants must be logged. Audit logs should contain thorough records of the identity's source, any attributes that were provided to the account upon creation, when the account was created, and what permissions the account has been granted. This will provide visibility into how users engage with their accounts, will shorten the time it takes to investigate issues, and will create an easily verifiable audit trail for compliance reasons.
JIT Provisioning in Cybersecurity Context
Providing access through JIT provisioning provides users with access whenever they require the system, rather than maintaining constant privileges over multiple systems. Providing limited access reduces the overall risk to an organisation and creates a secure method for controlling an organisation's user base. This helps organizations avoid standing privileges, reduce risk, and strengthen Zero Trust-based identity controls.
1. Reduces the Attack Surface
With traditional provisioning, users' accounts are often kept active for periods of time where they have no requirement for ongoing system access. With JIT provisioning, a user's account will only be created at the time that the user first logs into the organisation's system and accesses the system based on that user's authenticated identity attributes. As a result, this dramatically reduces both the number of accounts that attackers could try to compromise and also the risk that a malicious actor could access an organisation via cloud and SaaS-type systems. Additionally, it limits the growth of stale or inactive accounts over time.
2. Least Privilege Support for All Users
JIT (Just-in-Time) provisioning provides dynamic user access to resources according to the user's current role and group membership in the Identity Provider (IdP). For example, if the user's team changes, JIT provisioning will immediately update the user's role to match the new team during the next login, eliminating the need for manual updates. Therefore, JIT provisioning maintains a tightly restricted set of permissions for users, thus eliminating or minimizing the risk of privilege creep. Privilege creep is one of the largest contributors to unintentional risk within organizations.
Integration with PAM and IGA for Complete Governance
When Just-in-Time (JIT) provisioning for SaaS and business applications is combined with Privileged Access Management (PAM) for administrator-level access and Identity Governance & Administration (IGA) for lifecycle governance, organizations achieve a more complete and controlled identity security posture. Each solves a different piece of the identity puzzle, but together they close visibility gaps and strengthen overall controls.
-
PAM controls your high-privilege accounts with its own just-in-time privilege elevation technology that is different from SaaS JIT account creation. PAM features time-bound access, recording of sessions, automatic password rotation for continued access after each use, approval workflows prior to granting access, and the ability to provide temporary heightened privileges without needing continuous elevated privileged accounts.
-
IGA utilizes modern tools such as Identity Confluence by Tech Prescient to provide lifecycle governance for identities by monitoring the changes to an identity from provisioning through to its removal. This includes all requests for access through a Secure Content Identity Management platform (SCIM) or other API logs through to identity provider (IdP) sign-in and/or logout logs. With the IGA tool, you can review the access of users who were provided to them via JIT provisioning. You will not automatically receive all governance events from users that are JIT provisioned through an SSO-only scenario, but if you have your logs or SCIM notifications connected to IGA, you will be able to provide a governance audit for JIT provisioned accounts through IGA.
These integrations work together to minimize the gaps in visibility and provide a complete, compliant lifecycle for an identity, from initial login to identity deprovisioning.
Final Thoughts
The implementation of just-in-time (JIT) provisioning is now a key component of modern identity security, allowing organizations to create user accounts only upon successful user verification. As a result, organizations can eliminate time-consuming manual onboarding procedures, diminish unnecessary standing access for users, and guarantee that individuals have the appropriate permissions at the correct time. Additionally, JIT provisioning is a perfect complement to systems that utilize SCIM provisioning and Identity Governance and Administration (IGA) solutions, which help organizations to maintain the integrity of every user's identity, create a cleaner access footprint for all of their employees, and improve their overall Governance across multiple systems.
As more enterprises adopt the Zero Trust Security Model, organizations will use JIT provisioning as a critical part of their implementation, as it will facilitate the creation of dynamic, context-based access and will help organizations to bolster their existing security measures through JIT provisioning, while simultaneously streamlining operational processes and increasing efficiency.
Frequently Asked Questions (FAQs)
1. What is Just-in-Time (JIT) provisioning in IAM?
JIT provisioning refers to the instant creation of a user account when they first log into an application using an identity provider (IdP). The user profile is created using data (attributes) provided by the IdP, such as the user name, email address, and role, rather than having to create a new account in advance.2. How does JIT provisioning work with SAML?
In SAML JIT provisioning, the IdP authenticates the user then sends a SAML assertion with the identity attributes to the service provider (SP), which may then create a user account on the fly if one does not exist, assigning it the appropriate role or permissions as part of the login process.3. What is the difference between SCIM and JIT provisioning?
SCIM provisioning automatically synchronizes users across connected applications by creating, updating, and deleting user accounts on an ongoing basis through the background process. However, JIT provisioning creates a user account only once; therefore, JIT provisioning is used for users who access applications once, while SCIM provisioning is used for continuous access.4. Is JIT provisioning secure?
Yes, it is! Just-in-Time (JIT) Provisioning employs secure authentication protocols such as SAML or OIDC and is fully driven by the Identity Provider (IdP)'s identity verification policy. Since access will only be created when needed AND centrally managed under governance, this will drastically reduce the proliferation of stale or unused accounts and strengthen security as a whole.5. What are the advantages of JIT provisioning?
JIT Provisioning streamlines the onboarding process, reduces the amount of manual provisioning work, and provides each user with just the minimum necessary access at the exact time they require it. JIT Provisioning allows for the elimination of orphaned accounts as well as decreased administrative overhead, and facilitates consistent identity governance across various applications.



